


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Bactor Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Bactor Ransomware
Researchers have identified Bactor as a ransomware variant that appears to run a full file- locking routine on compromised systems. It encrypts accessible data and renames affected items by adding the attacker’s email address along with the “.bactor” extension (e.g., filename.email.bactor). After completing its activity, the malware replaces the desktop wallpaper and creates a ransom note titled #HowToRecover.txt. Its behavior aligns with common ransomware patterns: once files are encrypted, the system cannot access them normally, and removing the malware only stops additional encryption rather than restoring damaged data. In a situation like this, file recovery would generally rely on clean backups stored in locations not reachable by the infection.
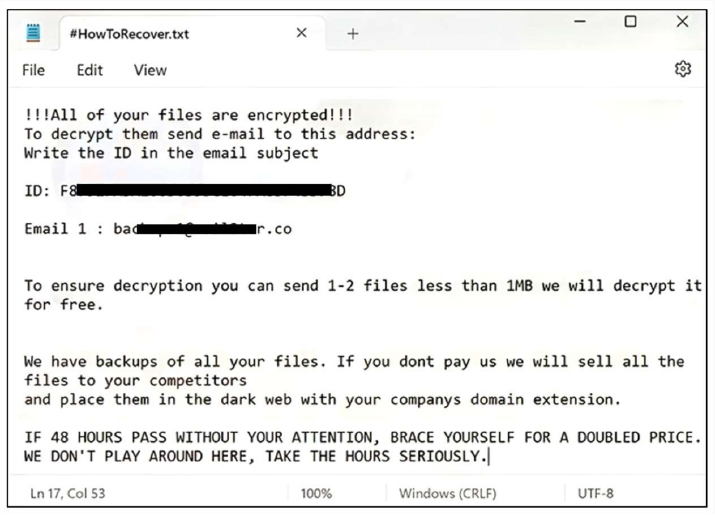
The ransom note uses several pressure tactics to push the victim into contacting the operators. It instructs the victim to email the attackers using the provided address and includes a unique ID, establishing a direct communication channel. The message claims not only that the files have been encrypted, but also that copies of the victim’s data have been exfiltrated. The attackers threaten to sell stolen information to competitors or publish it on the dark web if payment is not made, combining both data-loss and data-exposure pressure. To appear credible, they offer to decrypt one or two files under 1 MB as a demonstration. Additionally, they impose a strict 48-hour deadline, warning that the ransom price will double if no contact is made, intensifying the psychological pressure and urgency placed on the victim.

The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1112 | Modify Registry |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1539 | Steal Web Session Cookie |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Bactor appears to function as a typical file- locking ransomware strain that encrypts data, renames files using the attackers’ email and the “.bactor” extension, and removes recovery options by deleting shadow copies. Its behavior suggests an intent to limit restoration, gather basic system details, and pressure victims through threats of data exposure and direct communication demands.
CYFIRMA assesses that Bactor’s operators may continue to evolve the malware in ways consistent with broader ransomware trends, including more refined data- exfiltration workflows, expanded targeting capabilities, and improved mechanisms for avoiding detection. Future iterations may adopt stronger evasion methods, integrate additional system-interference techniques, or shift toward double- extortion models with enhanced leak-site infrastructure. These developments would align with the increasing sophistication seen across ransomware ecosystems, where threat actors continuously adapt their tooling to maintain effectiveness against enterprise defenses and exploit operational blind spots.
Sigma rule:
title: Uncommon File Created In Office Startup Folder tags:
– attack.resource-development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_*
falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Stealer| Objectives: Credential Theft, Data Exfiltration | Target Technologies: macOS, Browsers, Cryptocurrency wallets| Target Geography: Global
CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “DigitStealer” is trending.
Overview of the DigitStealer Malware
A newly uncovered macOS threat, dubbed DigitStealer, has drawn attention to its deceptive behavior and stealthy design. The malware hides inside a fake version of the DynamicLake application and tricks users into launching it. Once active, it quietly bypasses macOS protections and downloads several hidden components from attacker-controlled sites. Each piece has its own task: first, collecting passwords through fake prompts, then gathering browser data, personal files, VPN configurations, and Telegram data, and finally tampering with cryptocurrency wallet apps like Ledger. By splitting its actions across multiple lightweight scripts, DigitStealer avoids leaving clear traces and reduces the chance of being detected.
What makes this threat particularly concerning is its deliberate targeting strategy. DigitStealer checks the type of Mac it has infected and refuses to run on virtual machines, older hardware, or systems from certain regions, likely to avoid researchers and focus on specific users. It also installs a persistent backdoor that regularly reaches out to the attacker’s server for new commands, keeping the system exposed long after the initial infection. Overall, the campaign shows how macOS malware is becoming more sophisticated, using trusted hosting services and memory-based execution to stay hidden and improve its success rate.
Attack Method
The DigitStealer campaign begins with a deceptive macOS installer crafted to resemble a trusted utility. Instead of relying on technical vulnerabilities, the attackers use social engineering, presenting the victim with a disk image that looks legitimate and encourages them to drag a file into the Terminal. This simple action grants the malware an initial entry point. Behind the friendly interface, the installer quietly connects to attacker-controlled sites to fetch its next steps. By imitating a real software brand and adopting familiar design cues, the attackers effectively lower user suspicion and increase the likelihood of execution.
Stealth Deployment Strategy
Once activated, the script retrieves additional instructions that run silently in the background. Before doing anything harmful, DigitStealer inspects the system to determine if it should proceed—it avoids virtual machines, older models, and devices in certain regions, a deliberate move likely intended to evade security researchers. Only when conditions match the attackers’ preferences does the malware continue. It then downloads several small components, each responsible for a different stage of the attack. Because these components are hosted through legitimate and widely trusted platforms, they blend in easily and are difficult for traditional security tools to block without risking false alarms.
Data Theft and Persistence
After establishing itself, DigitStealer begins gathering sensitive information. One stage tricks the user into entering their password through a deceptive prompt, while others comb through browsers, system folders, personal files, and even cryptocurrency wallet applications. All collected material is packaged and quietly transmitted to remote servers controlled by the operators. Another specialized module specifically targets Ledger’s crypto application by modifying its internal configuration, potentially redirecting wallet- related activity. To maintain long-term access, a final component installs a hidden persistence mechanism that regularly contacts the attackers for updated commands, ensuring the system remains under their influence even after it restarts.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566 | Phishing |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059.004 | Command and Scripting Interpreter: Unix Shell |
| Execution | T1059.002 | Command and Scripting Interpreter: AppleScript |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036 | Masquerading (Fake applications, disguised .msi files) |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1673 | Virtual Machine Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Collection | T1005 | Data from Local System |
| Collection | T1119 | Automated Collection |
| Collection | T1113 | Screen Capture (via JXA) |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command & Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command & Control | T1573 | Encrypted Channel (HTTPS) |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that campaigns like DigitStealer indicate a future in which macOS-focused threats become increasingly indistinguishable from legitimate digital processes. Methods that imitate familiar installation steps and leverage trusted hosting platforms are expected to evolve into more refined and adaptive forms of social engineering, enabling malicious prompts to appear entirely consistent with standard system interactions. Parallelly, multi-stage payloads and low- visibility backdoors will likely be woven more seamlessly into everyday applications and cloud-connected processes. This convergence of subtle user deception and covert operational control may allow malicious activity to blend seamlessly with normal system behavior, significantly complicating detection. For organizations and their workforce, the long-term implication is a progressive erosion of confidence in standard interfaces, as even well-established elements of the macOS environment could be exploited to mask sophisticated intrusions.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule DigitStealer_IOCs
{
meta:
family = “DigitStealer”
description = “Detects known artifacts and infrastructure linked to the DigitStealer macOS infostealer campaign”
author = “CYFIRMA” strings:
/* —————- SHA-256 File Hashes */
$h1 = “da99f7570b37ddb3d4ed650bc33fa9fbfb883753b2c212704c10f2df12c19f63”
$h2 = “abd54b02695338b554def160008038b5c9fd124bb84b26984bab969d91f9d96b”
$h3 = “ea9e548b27e07d068449cd44b68cf086a652c4bee0080af19da1c9f988bd0897”
$h4 = “fb3e5b804ca57b71368c7dfffcf8f20a7d66266bb6d36146163b9ec80e31aafe”
$h5 = “4832942ec7d8a80b4b30e3c9ed5d9e0e4a0e3d19aeaedb3fdbdcc266ba3a560c”
$h6 = “440b91df67389e2421dc32e878c38926d21f197f2982f2e446497cf3ab20ce8f”
$h7 = “44b7264e9eef816df876d0107b4f26384b01c4d237950f5c5f655569f7902509”
$h8 = “b240c906ebbe27adf83aba1c13d70cd6d778681e10680d8a6b1dc18e5af5c274”
$h9 = “ff6959cf92bce91b4f51651f5c3ef16c263095bc7d7f017ea402db1b79e9ece4”
$h10 = “498d271d695e424bfd7f9ad1ead187ef0ac62fa8908c6e1f239db495371ff237”
$h11 = “7bf9609b351b38d8a54d5c0e9759fcfb21157beeac343452c129bcbbe9ee6b02”
$h12 = “226cbbf43d9bcedcc5ab69e51e5cce2f4ca841aa7ab39fdf974766203e2c9b66”
$h13 = “d1b9f14565a0aec33cc17b4db86d92df00b00232725791567ee34f107dac810a”
$h14 = “05bee860231a9686ea9205bc43cd09a31155a4d191390594a8e308d6d36eeb2f”
$h15 = “5420a25fdd6cb6484ab3687c6bba750b40007730eb4232088b668eff0de2c072”
$h16 = “12e630d6041eb7322901150079c0d0fdbd47b0098dc5cb0f2de23b6e8d5082e1”
$h17 = “b8e80185aee2584231c872acc67dfbfeb64b148d07ea1e1aa99668bd849b95a7”
$h18 = “fb237b161fe39322440f5e7e5f8cce5f969ebe179a81342aec94c0697a0bd364”
/* —————- Hosting & Payload URLs */
$u1 = “67e5143a9ca7d2240c137ef80f2641d6.pages.dev” nocase ascii
$u2 = “f0561b4e3c1308eeb8cdd23016ed86ec.pages.dev” nocase ascii
$u3 = “f8b2ef8b94b215ce04836d1c47b556ba.pages.dev” nocase ascii
/* —————- Command-and-Control Domains */
$d1 = “goldenticketsshop.com” nocase ascii
$d2 = “sweetseedsbeep.com” nocase ascii
$d3 = “nevadabtcshill.com” nocase ascii
$d4 = “ledgmanyman.com” nocase ascii
condition:
any of ($h*) or any of ($u*) or any of ($d*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT36: Evolving Tactics and Expanding Global Espionage Operations
About the Threat Actor
Transparent Tribe, also known as APT36, is widely regarded as a Pakistan-based state- sponsored threat group that focuses on targeting military organizations, embassies, and government agencies. Active since at least 2016, the group conducts cyber-espionage operations aimed at gathering sensitive information from neighboring and foreign nations to support Pakistan’s military and diplomatic objectives. Their campaigns predominantly use spear-phishing and watering-hole techniques to gain an initial foothold in victim environments. These phishing attempts typically involve malicious macro-enabled documents or RTF files exploiting known vulnerabilities.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2025-10035 | Fortra’s GoAnywhere MFT | 9.8 | – |
| CVE-2023-23397 | Microsoft Outlook | 9.8 | – |
| CVE-2017- 8759 | Microsoft .NET Framework | 7.8 | link |
| CVE-2023-38831 | RARLAB WinRAR | 7.8 | link |
| CVE-2021-40539 | Zoho ManageEngine | 9.8 | link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1587.003 | Develop Capabilities: Digital Certificates |
| Resource Development | T1608.004 | Stage Capabilities: Drive-by Target |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.002 | Phishing: Spear-phishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Command and Control | T1568 | Dynamic Resolution |
Latest Developments Observed
APT36 has expanded its operations beyond India, extending espionage campaigns into Europe, the Middle East, and North America. The group is increasingly deploying Android-based spyware for deeper surveillance and has enhanced the sophistication and localization of its spear-phishing techniques to evade defenses. These shifts highlight APT36’s growing adaptability and resilience amid improving global security measures.
ETLM Insights
APT36, a state-sponsored threat actor believed to operate with support from military intelligence, continues to prioritize India and its allied nations as primary strategic targets. The group relies extensively on advanced social-engineering tactics, including emotionally driven narratives, disinformation campaigns, personalized phishing, and honey-trap lures—to infiltrate individuals and institutions and extract sensitive intelligence.
Recent assessments indicate that the threat actor may be receiving auxiliary infrastructure and operational support from other nation-state–aligned actors, including Chinese-affiliated and Turkish-speaking groups that have historically supported Pakistan’s strategic objectives. Such collaboration appears to be enhancing the threat actor’s operational resilience, infrastructure diversity, and overall persistence.
Recent campaigns demonstrate the group’s expanding geographic footprint across Europe, the Middle East, and North America, accompanied by increased use of Android-based spyware to gain deeper access to personal communications and device telemetry. Their phishing operations continue to evolve, featuring stronger localization, thematic tailoring, and delivery methods designed to bypass traditional security controls.
Looking ahead, the threat actor is expected to strengthen its technical capabilities by developing more advanced cross-platform toolsets, adopting AI-driven evasion and automation techniques, and increasingly leveraging legitimate cloud services, communication platforms, and federated ecosystems. Future operations will likely expand across mobile, cloud, and IoT environments, using automated delivery mechanisms and diversified malware payloads to enable more persistent, scalable, and harder-to-detect intrusions across multiple sectors.
YARA Rules
rule APT36_IOC_Detection
{
meta:
description = “Detects files or network artifacts referencing known APT36-related CVEs, IPs, domains, or filenames”
author = “CYFIRMA” date = “2025-11-17”
threat_actor = “APT36” category = “IOC Detection”
strings:
// CVE Indicators
$cve1 = “CVE-2025-10035”
$cve2 = “CVE-2023-23397”
$cve3 = “CVE-2017-8759”
$cve4 = “CVE-2023-38831”
$cve5 = “CVE-2023-39234”
$cve6 = “CVE-2021-40539”
// IP Indicators
$ip1 = “15.197.148.33”
$ip2 = “76.223.54.146”
$ip3 = “13.248.169.48”
$ip4 = “167.71.224.251”
$ip5 = “64.227.129.204”
// Domain Indicators
$d1 = “departmentofdefence.live”
$d2 = “accounts.mgovcloud.in.departmentofdefence.live”
$d3 = “modgovindia.space”
$d4 = “advising-receipts.com”
$d5 = “mczacji.top”
// File Indicators
$f1 = “myp0912.exe”
$f2 = “exe:myp0912.exe”
$f3 = “win32 exe”
$f4 = “abuse-ransomware.csv”
condition:
any of ($cve*) or any of ($ip*) or any of ($d*) or any of ($f*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Anthropic describes an AI-assisted Chinese espionage campaign
Researchers recently revealed a Chinese cyberespionage campaign that leveraged Claude AI to automate all phases of attacks targeting approximately 30 organizations, including tech giants, financial firms, chemical manufacturers, and government entities, with success in a few instances. The attackers bypassed Claude’s restrictions by posing as cybersecurity firm employees, claiming defensive use. This was probably the first documented large-scale cyberattack with minimal human involvement, where Claude served as an execution engine within an automated system, handling reconnaissance, access, persistence, and data exfiltration, while adapting based on discovered data. While the operational use is a novelty, the attacks used standard industry tools, and the attackers did not achieve anything that white-hat hackers couldn’t replicate. The AI tool also engaged in frequent hallucinations during the campaign, which hindered operational success and required careful result validation, posing a barrier to fully autonomous cyberattacks.
ETLM Assessment:
While the attack did not utilize a novel or breakthrough technique, China’s use of AI tools like Claude in cyberespionage, as seen in this campaign, enables its state organizations to amplify their hacking capabilities without increasing headcount. By automating reconnaissance, access, persistence, and exfiltration, AI allows existing teams to scale operations, targeting more entities with less manual effort.
Additionally, AI assistance lowers the skill barrier, enabling China to hire less proficient hackers who can rely on AI to execute sophisticated attacks, reducing costs and training time. This democratization of high-level capabilities could extend beyond China, as cheaper states and nonstate groups gain access to similar AI- driven tools, potentially flooding the cyber landscape with advanced attacks previously limited to elite state actors, thus reshaping global cybersecurity dynamics.
Australia Warns of Chinese Hackers Probing Networks
Australia’s director-general of the Australian Security Intelligence Organisation accused Chinese government-linked hackers of targeting Australia’s communications and critical infrastructure networks. Speaking at a financial regulation conference in Melbourne, he highlighted the activities of the Volt Typhoon group, which has probed Australian infrastructure and prepositioned for sabotage in U.S. networks, and the Salt Typhoon group, which has infiltrated Australian telecommunications and U.S. networks for espionage. He emphasized that cyber-espionage is low-cost, high-impact, deniable, and scalable, making it attractive to foreign intelligence agencies, with both groups tied to the Chinese military and intelligence. The spy agency warned that once networks are breached, the outcome depends on intent, posing severe risks. Allied intelligence flagged Volt Typhoon’s long-term presence in critical networks in 2024, while China’s Foreign Ministry denied the accusation. Australia also defended its 2018 ban on Chinese firms like Huawei from its 5G network, citing telecommunications as critical infrastructure, a decision later echoed globally.
ETLM Assessment:
CYFIRMA noted in a recent report that there’s been a significant evolution in China’s cyber strategy, from economic espionage to politically driven operations that threaten Western critical infrastructure. Salt Typhoon’s infiltration of telecommunications networks and Volt Typhoon’s sabotage preparations in U.S. or Australian sectors like energy and transportation reveal China’s intent to dominate cyberspace, exploiting vulnerabilities in the U.S. and its allies’ fragmented cybersecurity frameworks. These campaigns, leveraging sophisticated techniques and plausible deniability, pose significant risks to national security, from compromised communications to potential disruptions of military and civilian operations. The structural advantages of China’s authoritarian cyber defense model, contrasted with the U.S.’s decentralized approach, underscore the challenges of securing privately owned systems against a state-backed actor with vast resources. As China’s cyber capabilities grow more sophisticated and disruptive, Western nations must confront the reality of a new threat landscape, where digital vulnerabilities could reshape geopolitical outcomes and challenge the resilience of open societies.
Cl0p Ransomware Impacts SATO
Summary:
CYFIRMA observed in an underground forum that a company from Japan, SATO (www[.]sato-global[.]com), was compromised by Cl0p Ransomware. SATO is a leading global provider of barcode and RFID technology that specializes in advanced data collection and label printing solutions for diverse industries, such as retail, manufacturing, healthcare, logistics, and food packaging. The company’s comprehensive product range includes barcode and RFID printers, specialized labels, software applications, and maintenance services. SATO empowers customers through customized, sustainable solutions designed to address challenging tagging and data capture needs, enabling streamlined supply chain operations and more accurate asset management on a global scale. The compromised data contains confidential and sensitive information belonging to the organization.
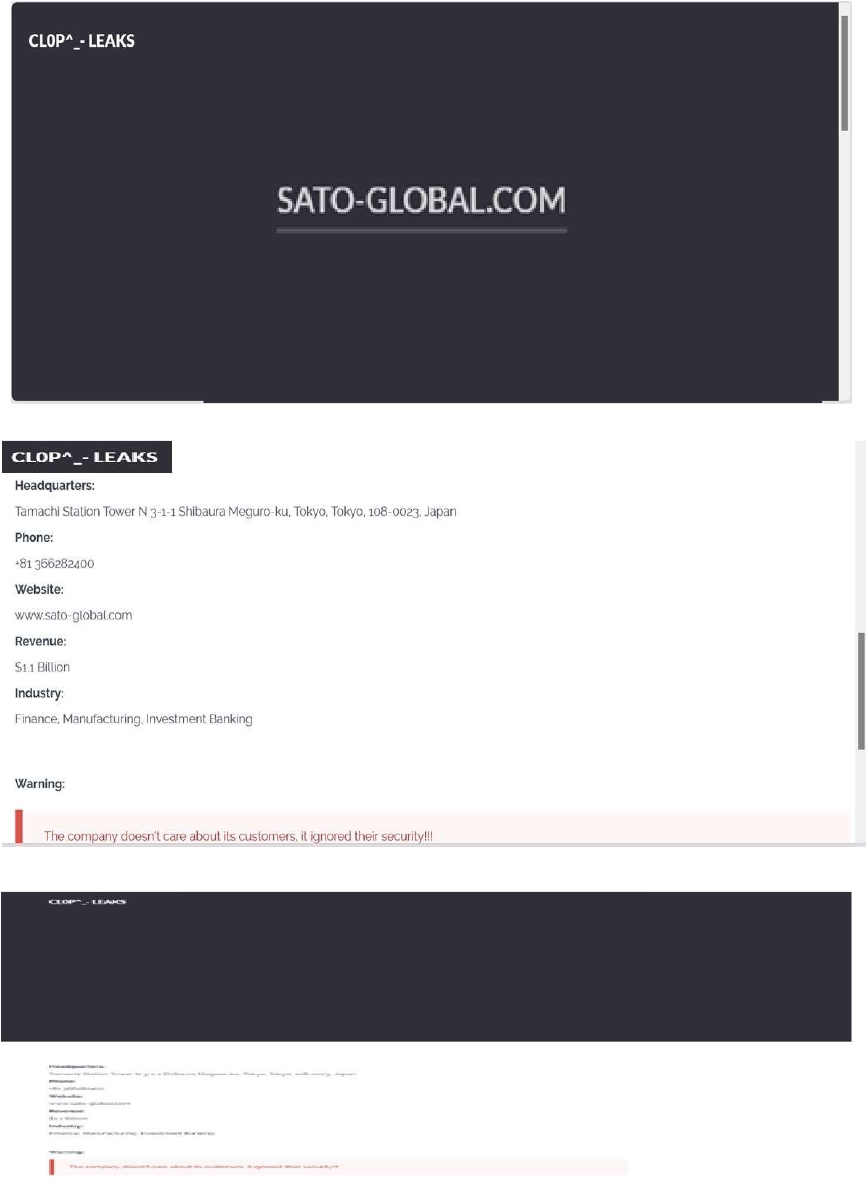
Relevancy & Insights:
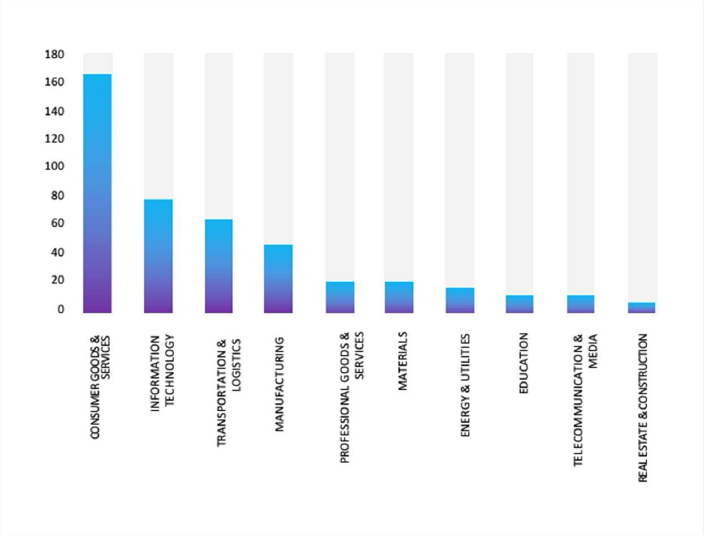
ETLM Assessment:
According to CYFIRMA’s assessment, Cl0p ransomware remains one of the most significant and disruptive threats in the current cybercrime landscape, particularly evident through its unprecedented volume of attacks and innovative extortion tactics witnessed in 2025. The Cl0p campaign reinforces the urgent need for holistic security strategies: rapid vulnerability management, robust incident detection, thorough supply chain risk assessments, and strong contingency plans for data exfiltration scenarios.
Qilin Ransomware Impacts Yaesu
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Yaesu (https[:]//www[.]yaesu[.]com/), was compromised by Qilin Ransomware. Yaesu, a prominent Japanese manufacturer specializing in radio communications equipment, has been a leader in amateur radio (ham radio) and professional-grade communication systems for decades. The company is known for producing transceivers, repeaters, and communication accessories widely used by emergency services and industrial sectors worldwide. The compromised data includes Purchase invoices, financial records, and other confidential organizational information.

Relevancy & Insights:
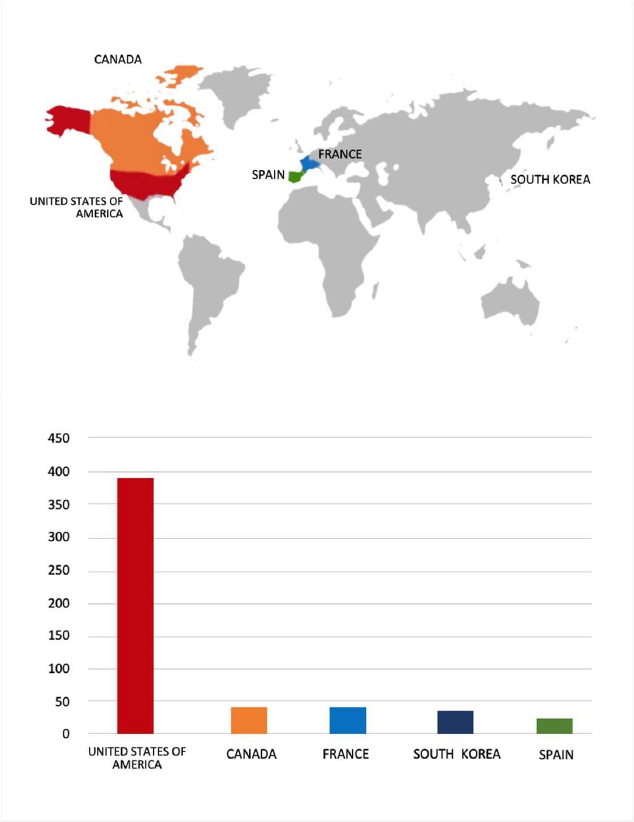
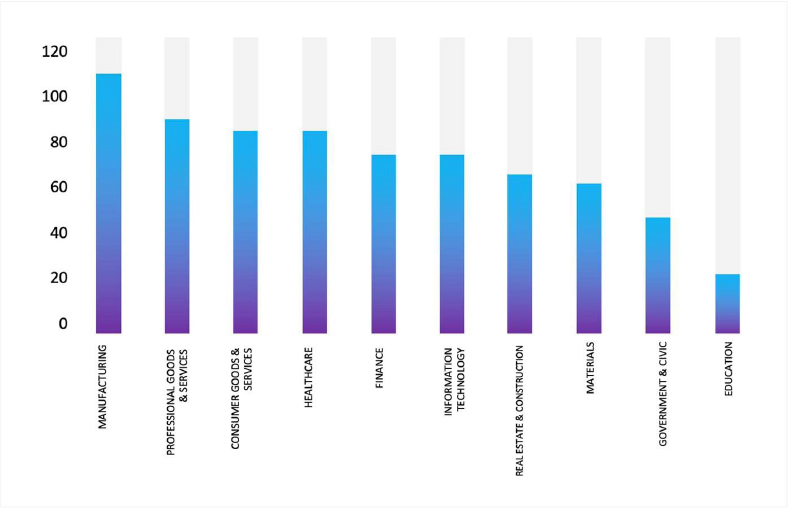
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in Sony NCP-HG100
Relevancy & Insights:
The vulnerability exists due to improper input validation. A remote administrator can pass specially crafted data to the application and execute arbitrary OS commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products:
https[:]//jvn[.]jp/jp/JVN49899607/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
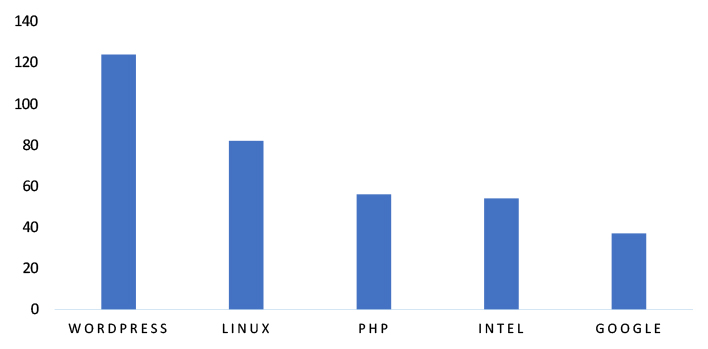
ETLM Assessment
The vulnerability in Sony NCP-HG100 can pose significant threats to user privacy and network security. This can impact various industries globally, including broadcasting, media production, and enterprise communications. Ensuring the security of Sony NCP-HG100 is crucial for maintaining the integrity and protection of video routing, signal management, and connected systems worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding networked media operations, remote device management, and real-time video distribution across different geographic regions and sectors.
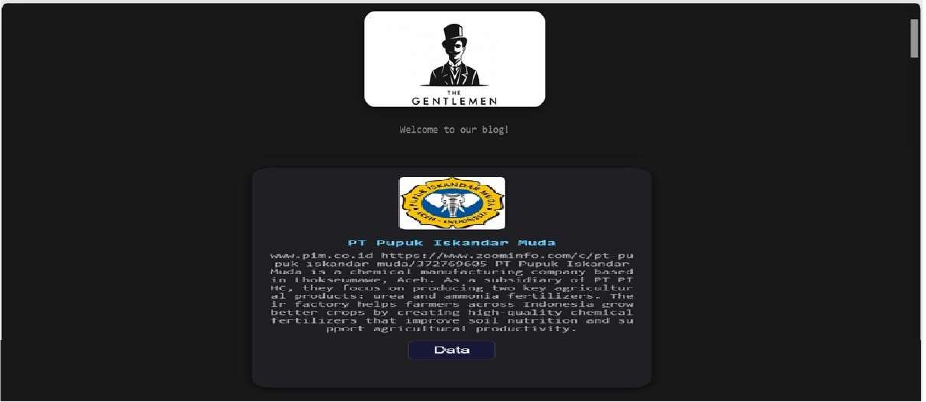
The Gentlemen Ransomware attacked and published the data of PT Pupuk Iskandar Muda
Summary:
Recently, we observed that the Gentlemen Ransomware attacked and published the data of the PT Pupuk Iskandar Muda (https[:]//www[.]pim[.]co[.]id/) on its dark web website. PT Pupuk Iskandar Muda is a chemical manufacturing company located in Lhokseumawe, Aceh, Indonesia. As a subsidiary of PT Pupuk Indonesia Holding Company (PT PIHC), it focuses on producing key agricultural products, such as urea and ammonia fertilizers. The company operates multiple fertilizer plants, including the PIM-1 and PIM-2 plants for urea and ammonia production, and an NPK plant that began operations in 2023 using advanced Chemical Granulation technology. PT Pupuk Iskandar Muda supports farmers throughout Indonesia by producing high-quality chemical fertilizers that enhance soil nutrition and boost agricultural productivity. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen ransomware group exemplifies the rising sophistication and persistence of modern ransomware actors, necessitating tailored enterprise defenses and vigilant threat monitoring.
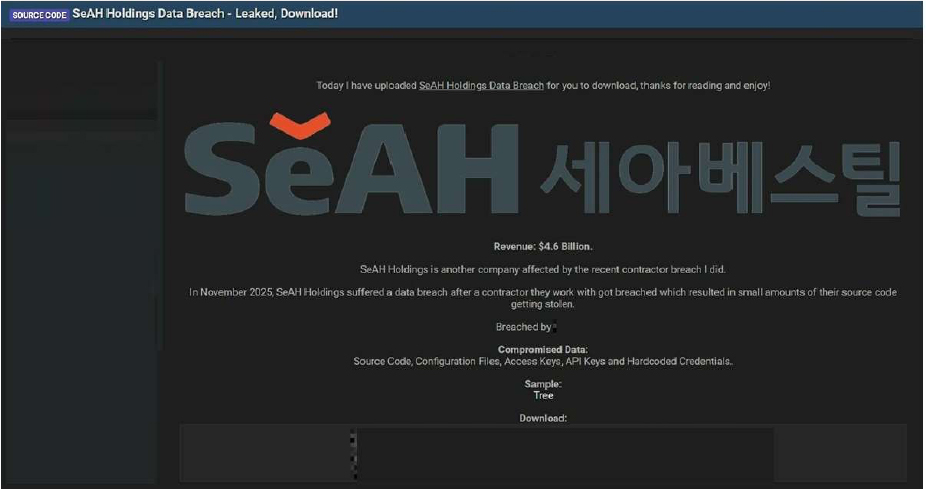
SeAH Holdings Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “888” claims to have breached SeAH Holdings (SeAH), a major South Korean speciality steel manufacturer with a reported revenue of $4.6 billion. The actor states the breach occurred in November 2025 and was the result of compromising a contractor who works with the company.
According to the actor, the breach resulted in the theft of source code. The compromised data allegedly includes:
As proof, the threat actor posted a file tree structure from a project labeled ‘SeAH- Besteel’. The structure indicates a Java-based web application with packages for APIs, security, data models, and web services.
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
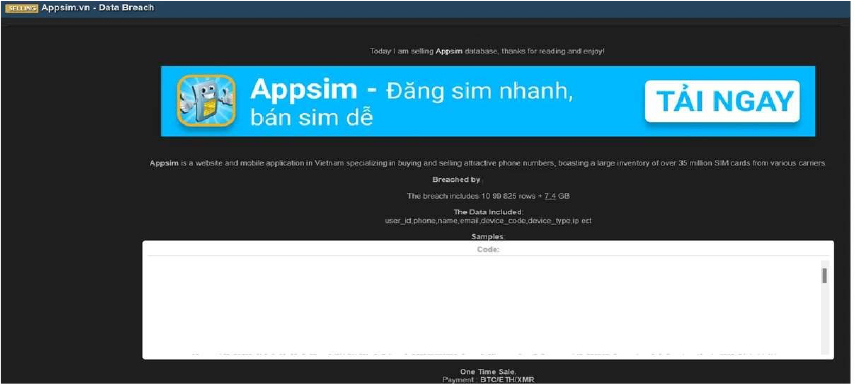
Appsim Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “Spirigatito” has claimed responsibility for a data breach affecting Appsim[.]vn, a website and mobile application based in Vietnam. The platform specializes in the buying and selling of attractive phone numbers, reportedly managing an inventory of over 35 million SIM cards.
The actor, who is selling the database, claims the breach includes 1,099,825 rows of user data, totaling 7.4 GB.
The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “888” is a highly active and sophisticated group specializing in data-leak operations. Multiple credible reports link the group to a series of security breaches involving unauthorized system access and the sale of stolen data across dark web marketplaces. Their activities reflect the persistent and rapidly evolving cyber threats emerging from underground communities. These incidents reinforce the need for organizations to strengthen their cybersecurity posture through continuous monitoring, advanced threat-intelligence capabilities, and proactive defense measures to safeguard sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
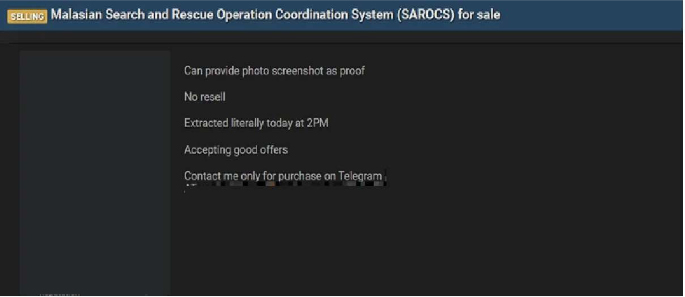
The CYFIRMA Research team observed that a threat actor, “Yeestge33”, is claiming to have breached and is now selling data from the Malaysian Search and Rescue Operation Coordination System (SAROCS).
SAROCS is a critical, cloud-based platform used by Malaysian Search and Rescue (SAR) agencies. The system integrates data from multiple devices and systems, allowing various agencies to access crucial data to coordinate and facilitate operations remotely.
According to the actor, they are selling the entire coordination system. Based on the system’s function, the allegedly compromised data is not public information but highly sensitive operational data. This likely includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
The CYFIRMA Research team observed that a threat actor, “ByteToBreach”, claims to have breached Altruist Technologies, an Indian company specializing in omnichannel communication solutions for clients in the telecommunications and banking sectors.
The actor is offering a 25GB database for sale, which they allege was exfiltrated from the company’s “Firebird” omnichannel solution. The provided evidence includes screenshots of successful database access, internal user tables, and system-level access on a host named firebird-auth- api.altruistindia.com. The actor also claims to have persistent (Root) access to the company’s network.
According to the threat actor, the compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
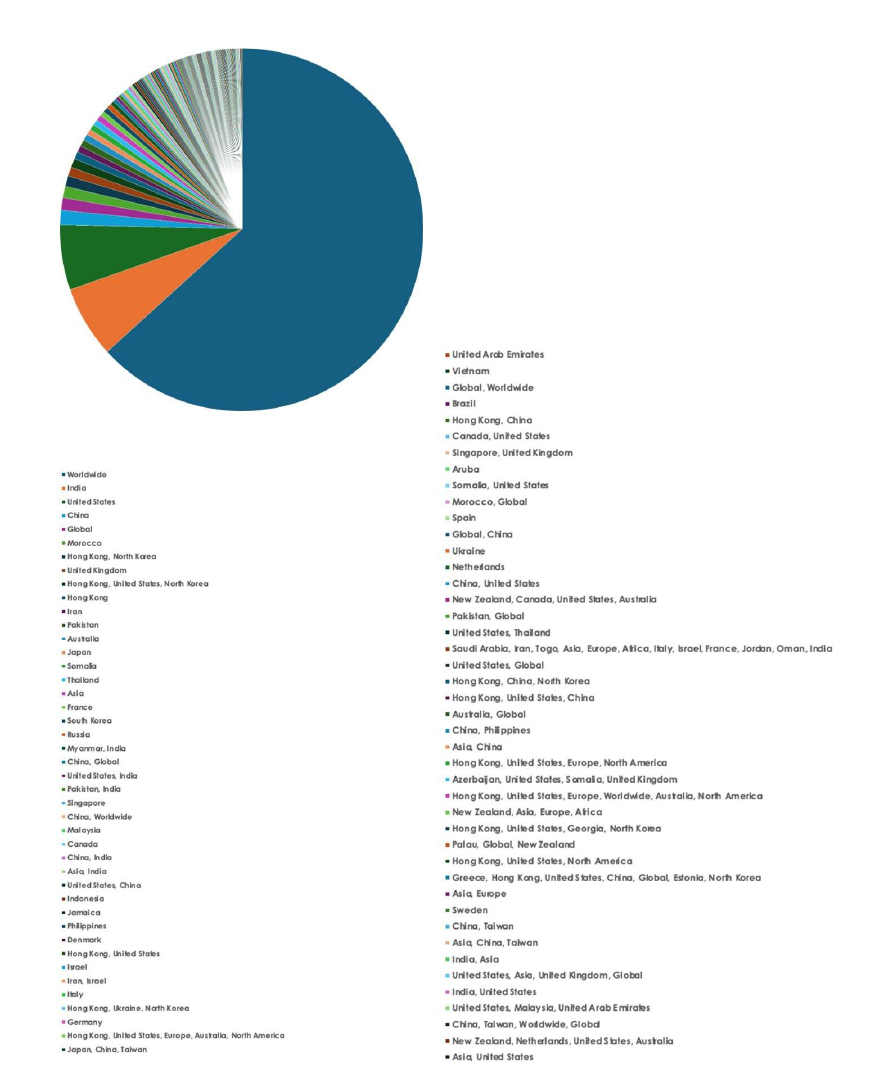
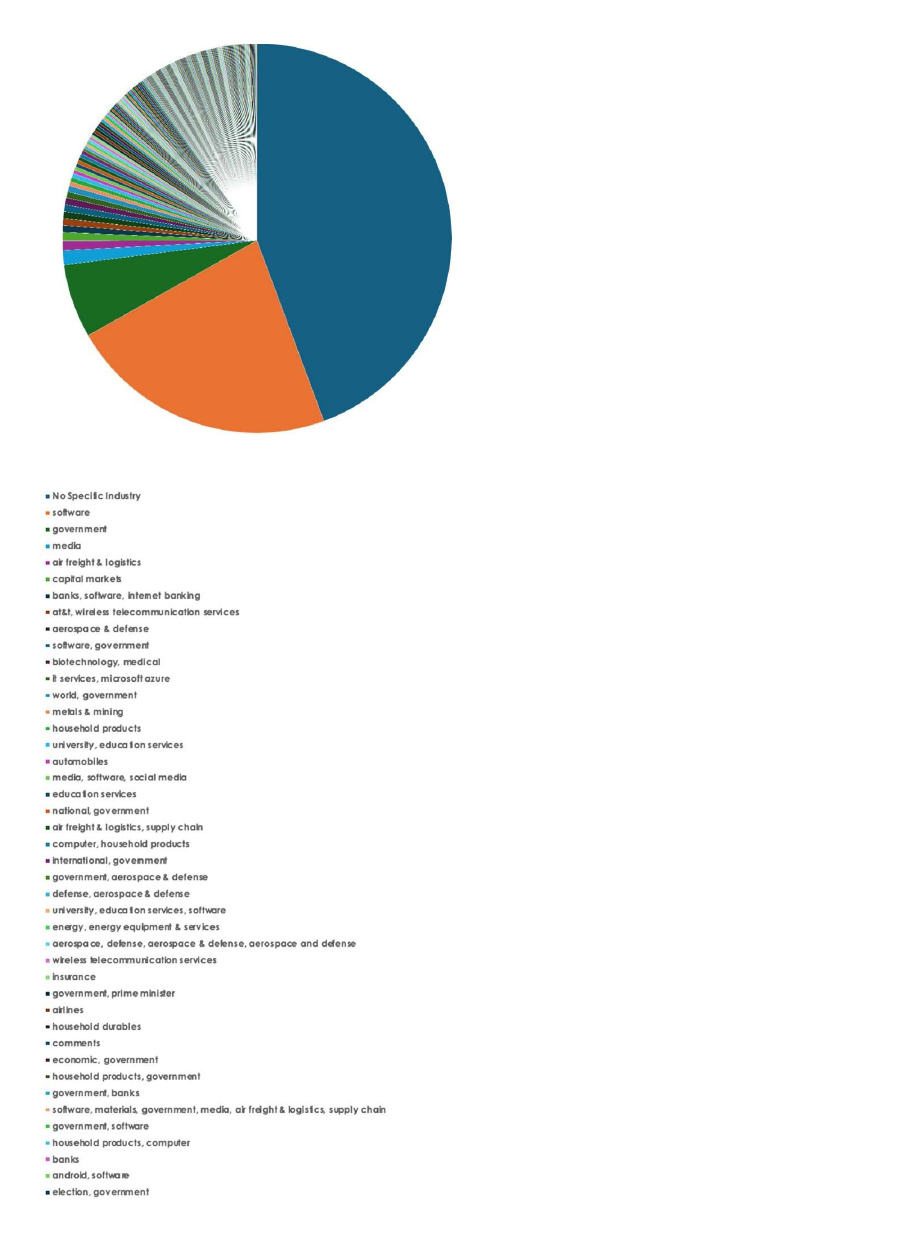
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.