


Between January and October 2025, Rwanda’s government infrastructure experienced a series of coordinated cyber incidents involving data leaks, credential theft, and website defacements. The earliest indicators appeared in February–March with the resurfacing of .gov.rw archives on dark web and Telegram channels linked to Babuk Locker affiliates. In May, the Rwandan Ministry of Health was targeted twice, first by Vasa Locker affiliates claiming a 52 GB data theft, and later by a dark web actor “koko” selling a 53 GB package for $2,500. Additional incidents included defacements of naeb.gov.rw and minagri.gov.rw subdomains in January, and a Telegram-based DDoS solicitation against the National Bank of Rwanda in May. By August–October, stealer logs from Acreed, Rhamadanthys, and Vidar revealed credential compromises across critical domains, such as irembo.gov.rw, rra.gov.rw, and mifotra.gov.rw, confirming widespread infiltration of government networks.
The authenticity of the breaches below remains unverified at the time of reporting, as the claim originates solely from threat actors.
On 23 September 2025, a threat actor using the alias “koko” advertised a 53 GB data dump, allegedly from the Government of Rwanda Ministry of Health, on a dark web forum (Seller’s Place). The package, tied to hmis.moh.gov.rw, reportedly contains documents, CVs, emails, and SQL files and is being sold for $2,500, a compromise that could expose sensitive health records, personnel information, and operational data if verified.
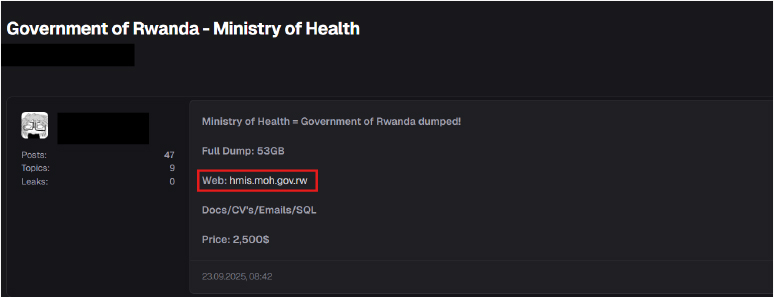
On 25 May 2025, a Telegram post by user “Deleted Account” publicly called for a distributed-denial-of-service (DDoS) against the National Bank of Rwanda website (www.bnr[.]rw / https://www.bnr[.]rw/), stating: “Yo y’all hop in ddos this website I’m attacking it rn.” The message potentially constitutes an open solicitation and admission of an ongoing attack against the bank’s online infrastructure.
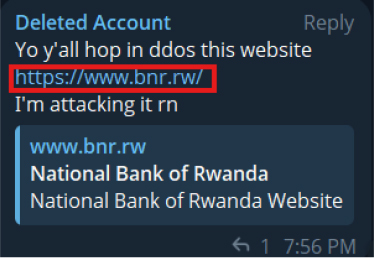
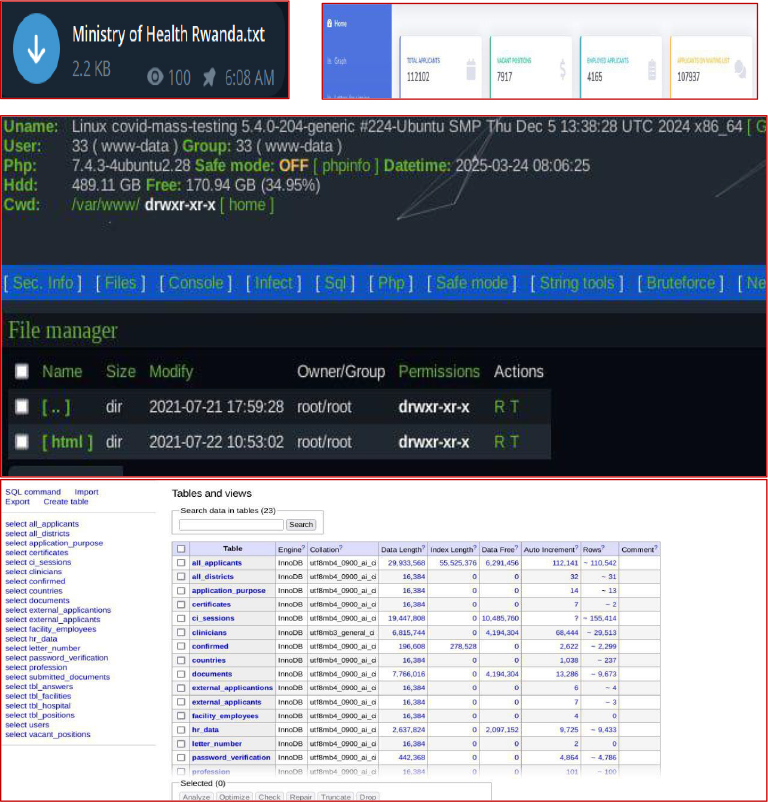
On 4 May 2025, a post surfaced on Telegram, allegedly made by the Vasa Locker Affiliate (Babuk Locker 2.0), claiming responsibility for breaching the Rwandan Ministry of Health (moh.gov.rw). The actor stated that approximately 52GB of data had been exfiltrated from multiple Ministry websites, including the Rwanda Health Workforce Management System. The post included a message asserting full access to ministry systems and data theft.
The same claim was reshared on Raidforums on 4 May 2025 under the Discussion section, amplifying the visibility of the incident across cybercriminal communities.
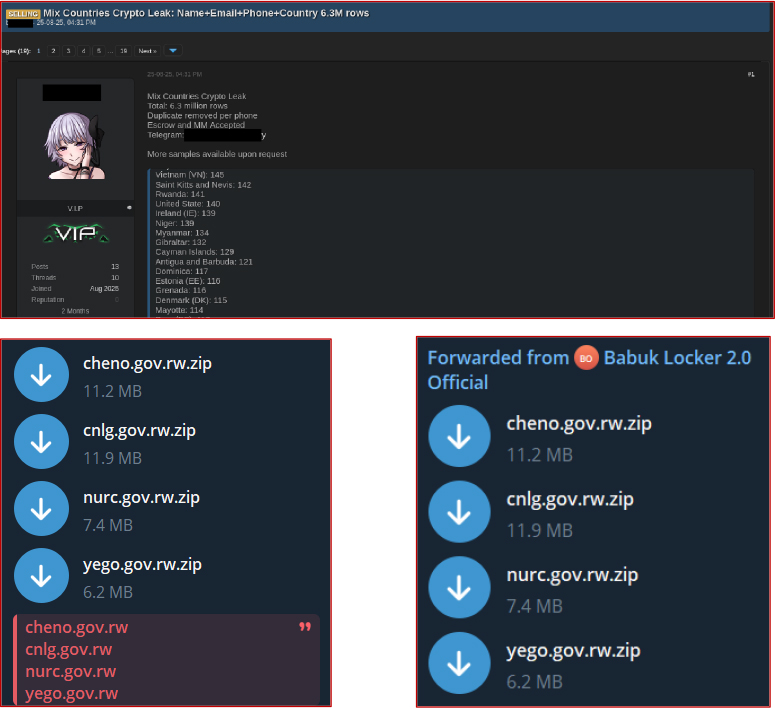
Between February and March 2025, several archive files associated with Rwandan government domains cheno.gov.rw.zip, cnlg.gov.rw.zip, nurc.gov.rw.zip, and yego.gov.rw.zip were observed circulating on cybercriminal platforms.
Rwanda government data leak timeline & summary:
The content resurfacing in February–March 2025 traces back to a documented 2023 breach. Threat actors and ransomware-affiliated channels appear to have repackaged and re-amplified the older dataset to maintain visibility and monetize the leak. The consistent reposting across Telegram ransomware channels and underground forums indicates a coordinated campaign leveraging historical data from Rwandan government systems, with Babuk Locker 2.0 and its affiliate networks playing a key role in the propagation.
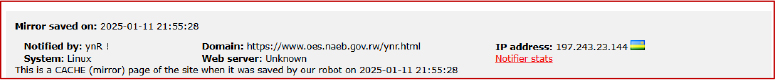
On 11 January 2025 at 21:55:28, a mirror cache of https://www.oes.naeb.gov.rw/ynr.html was saved and notified by ynR, showing evidence of a possible defacement; the record lists the host IP as 197.243.23.144 (Rwanda), system Linux, and identifies the page as a cached snapshot of the site in its compromised state, indicating unauthorized modification of a NAEB (Government of Rwanda) subdomain.
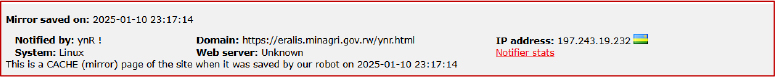
On 10 January 2025 at 23:17:14, a mirror cache of https://eralis.minagri.gov.rw/ynr.html was saved and notified by ynR, indicating a possible defacement of the Ministry of Agriculture and Animal Resources (MINAGRI) subdomain; the snapshot lists the IP address 197.243.19.232 (Rwanda), running on a Linux system, serving as evidence of unauthorized modification to a Rwandan government website.
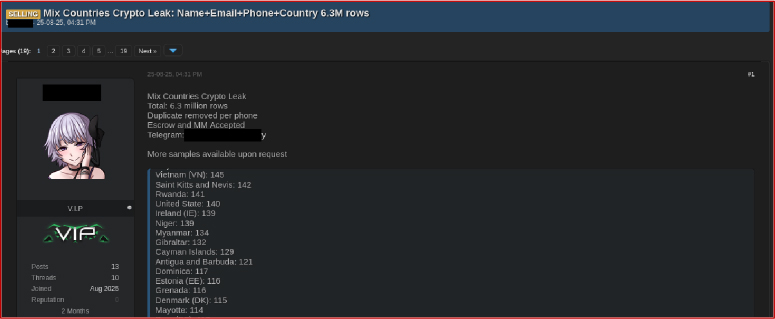
On 25 August 2025, a post appeared on a dark web forum by a user identified as hulky (V.I.P), advertising a database titled “Mix Countries Crypto Leak.” The dataset reportedly contained 6.3 million records of names, emails, phone numbers, and countries, with 141 entries associated with Rwanda. The seller claimed to have removed duplicates and offered the data for sale with escrow and middleman options, providing a Telegram contact for further inquiries and sample verification.
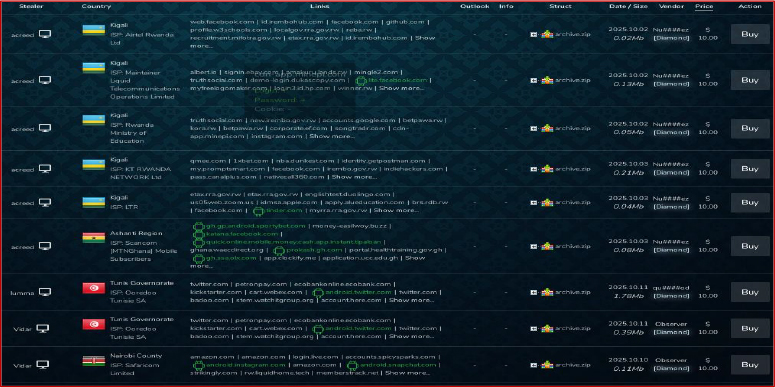
Between February and March 2025, initial leaks of several Rwandan government archive files, including cheno.gov.rw.zip and cnlg.gov.rw.zip, were observed circulating on cybercrime platforms. By August 2025, stealer logs from malware families, such as Acreed, Rhamadanthys, and Vidar, began revealing credentials associated with the Rwandan government and telecom networks, indicating a shift from data leakage to active credential compromise. In October 2025, broader exposure was confirmed as multiple .gov.rw domains across public sector systems were identified with compromised credentials, underscoring a sustained and escalating threat to Rwanda’s government infrastructure.
The 2025 cyber activity against Rwanda indicates a sustained campaign targeting both public services and national infrastructure, blending hacktivism, credential theft, and criminal monetization. Repeated resurfacing of historic leaks and new stealer data suggests poor credential rotation and ongoing exposure. Strengthening identity management, monitoring Telegram and dark web channels, and enhancing incident coordination across ministries are critical to limiting further exploitation.