


Tanzania’s cyber threat landscape has escalated in 2025, reflecting its growing digital transformation, expanding telecom sector, and increasing reliance on online platforms for governance, commerce, and public services.
Ransomware remains the most disruptive threat, with both established and emerging groups exploiting weak defences across government, finance, and telecom sectors. Underground forums have also seen a steady flow of Tanzanian data leaks, compromised credentials, and unauthorized access sales, creating ready-made entry points for ransomware operators, fraudsters, and espionage actors.
Hacktivism has emerged as a visible risk. In May 2025, several government-linked social media accounts were compromised, leading to the posting of offensive content and forcing temporary restrictions on the X platform. While technically less sophisticated, such campaigns undermine public trust and highlight the exposure of critical communication channels.
The convergence of ransomware, the dark web’s commercialization of access, and hacktivist campaigns highlights Tanzania’s growing appeal to cyber adversaries. Without significant investment in resilience, coordinated monitoring, and skilled workforce readiness, organizations risk operational disruption, financial loss, and reputational damage.
In 2025, Tanzania recorded two confirmed ransomware victims, attributed to Arcusmedia and Nightspire.
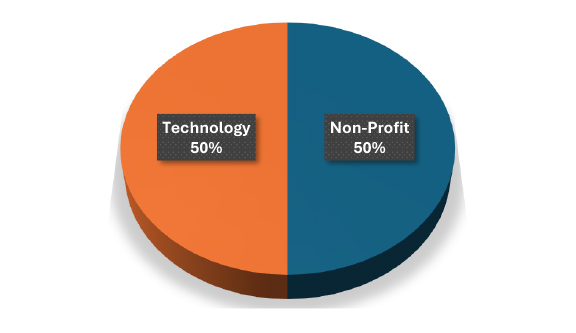
While the number of observed incidents is low, the presence of both established and emerging groups in the Tanzanian threat landscape illustrates the opportunistic nature of ransomware actors. Attackers are scanning broadly across regions and industries, looking for vulnerable targets regardless of size or sector.
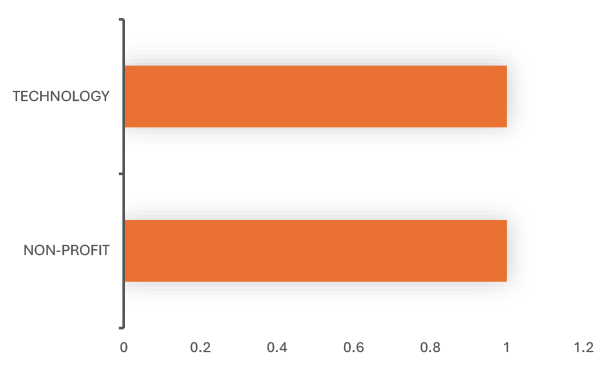
Non-Profit – Demonstrates that social-impact and humanitarian organizations are not exempt from financially motivated attacks, despite limited resources.
Information Technology – Attacks against IT service providers are particularly concerning, as they can cascade into multiple client environments and amplify the overall impact.
Although ransomware activity in Tanzania appears lower than in larger economies, such as South Africa, the diversity of victims indicates that attackers are sector-agnostic. The risk remains significant, especially if ransomware groups begin to target Tanzanian critical infrastructure, finance, or government entities in future campaigns.
Web defacement emerged as a notable trend in Tanzania during 2025, with 10 confirmed incidents observed. Most of these incidents targeted government websites, highlighting the risk of adversaries using symbolic attacks to undermine public trust and highlight perceived political or social grievances.
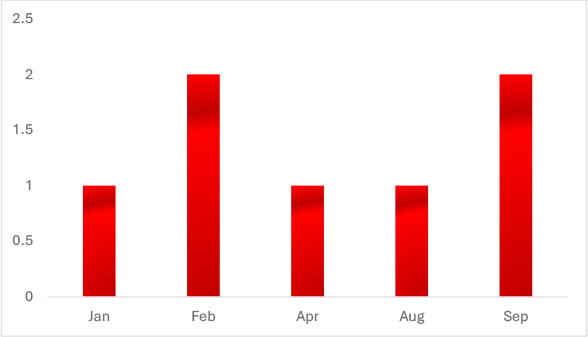
While technically less sophisticated than ransomware or data theft, defacement incidents have a high reputational impact. Hacktivists or opportunistic attackers often use them to:
The concentration of incidents on government domains indicates adversaries are prioritizing visibility and symbolism over financial gains. This trend emphasizes the need for stronger web application security, continuous monitoring of public-facing assets, and faster incident response processes to restore services and protect public trust.
In May 2025, multiple official X (formerly Twitter) accounts belonging to Tanzanian government agencies and private institutions were compromised by hackers. Among the most prominent was the official Tanzania Police account, which was used to post sexually explicit material and spread false claims of the President’s death.
The incident caused significant reputational damage and disrupted public communications. In response, authorities restricted nationwide access to X while investigations were initiated.
Such hacktivist-style account takeovers undermine public trust, amplify disinformation, and highlight systemic weaknesses in the security of official communication channels. This episode demonstrates how adversaries can leverage compromised social media accounts to achieve high visibility with minimal technical effort.
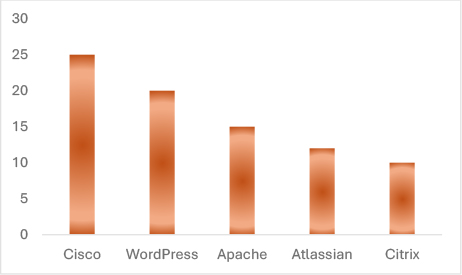
Recent analysis highlights Tanzanian exposure to global vulnerability trends:
These vulnerabilities provide fertile ground for adversaries to gain initial access and pivot into broader ransomware or espionage campaigns.
On September 24, 2025, a threat actor allegedly leaked the source code associated with an IT integrator and managed service provider in Tanzania. The threat actor did not disclose the source of the breach or how it was exploited.
Tanzania’s cyber threat environment is becoming increasingly complex, with ransomware remaining a primary driver of financial loss and operational disruption. The circulation of leaked data and unauthorized access on underground marketplaces further amplifies this risk by granting adversaries direct entry points into sensitive systems.
The compromise of government-linked social media accounts in May 2025 illustrates the growing role of hacktivism and disinformation, which threaten public trust and exploit political contexts. At the same time, the ongoing exploitation of commonly used platforms and unpatched vulnerabilities continues to expose both public- and private-sector organizations to opportunistic and targeted attacks.
Without timely investment in cyber resilience, real-time monitoring, and workforce capacity-building, Tanzania will remain a priority target for cybercriminals and hacktivist groups.
Strategic
Operational
Tactical