


CVE-2025-6541 is a critical Remote Command Injection vulnerability in TP-Link Omada Gateway devices, caused by improper input validation in the web management interface that allows attackers to execute arbitrary operating-system commands.
CYFIRMA research has reviewed public advisories and confirms that this flaw, along with related vulnerabilities (including CVE-2025-6542), could be exploited to compromise device integrity, exfiltrate sensitive network credentials, and pivot laterally within enterprise networks. Attackers can leverage web UI access, command injection payloads, and malicious configuration parameters to gain elevated privileges and persistence.
CVE-2025-6541 is a critical vulnerability affecting TP-Link Omada Gateway devices, widely deployed in enterprise and small and medium-sized businesses (SMB) networks for routing, VPN, and network management. This flaw, classified as a Remote Command Injection vulnerability, allows attackers to execute arbitrary operating-system commands by exploiting improper input validation in the device’s web management interface. Given the significant role of Omada Gateways in network operations, compromise of these devices poses a severe risk to organizations’ infrastructure and data security.
The vulnerability arises from the unsafe handling of user-supplied parameters in web requests, which can be manipulated to bypass command restrictions and inject malicious payloads. Exploitation can lead to full device compromise, exposure of sensitive configuration and credential data, and potential lateral movement within internal networks. The presence of these flaws underscores the urgency for immediate patching, access restriction, and continuous monitoring to prevent unauthorized control of critical network infrastructure.
Remote Command Injection Vulnerability: CVE-2025-6541 is a critical command injection flaw in TP-Link Omada Gateway devices, allowing attackers to execute arbitrary operating-system commands via the web management interface.
Improper Input Validation: The vulnerability arises from unsafe handling of user-supplied parameters, enabling attackers to bypass command restrictions and manipulate device operations.
Potential for Unauthenticated Exploitation: Some related vulnerabilities (e.g., CVE-2025-6542) reduce the exploitation barrier, allowing remote attackers to gain control without authentication.
Severe Risk to Network Infrastructure: Omada Gateways are widely deployed in enterprise and SMB networks; exploitation can compromise routing, VPNs, credentials, and internal network security.
Immediate Mitigation Required: Organizations must upgrade affected devices to the latest firmware, restrict web management access to trusted networks, enforce strong admin credentials, disable unnecessary services, and continuously monitor for exploitation attempts.
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers, cybersecurity vendors, and the open-source community in identifying, analyzing, and mitigating the CVE-2025-6541 vulnerability. Their contributions have been instrumental in raising awareness and ensuring timely security patches to protect organizations from potential exploitation.
Vulnerability Type: Remote Command Injection (RCE) via Web Management Interface
CVE ID: CVE-2025-6541
Application: TP-Link Omada Gateway
Impact: Attackers can execute arbitrary OS commands on the device, potentially compromising configurations, credentials, and enabling lateral movement within internal networks.
Severity: Critical
Affected Versions: Multiple Omada Gateway models prior to October 2025 patched firmware builds (e.g., ER707-M2 < 1.3.1 Build 20251009 Rel.67687, ER8411 < 1.3.3 Build 20251013 Rel.44647, ER605 V2 < 2.2.3 Build 20251008 Rel.12231, ER7206 < 1.4.3 Build 20251009 Rel.53521)
Patch Available: Yes
CVE-2025-6541 is a critical Remote Command Injection vulnerability affecting TP-Link Omada Gateway devices. The flaw stems from improper input validation within the web management interface, which allows attackers to inject and execute arbitrary operating-system commands on affected devices.
By sending specially crafted web requests with manipulated parameters, attackers can bypass command restrictions, alter device configurations, and execute malicious payloads. This vulnerability is particularly severe because Omada Gateways serve as central routing, VPN, and network management devices in enterprise and SMB environments. Successful exploitation can lead to full device compromise, exposure of administrative credentials, modification of network settings, and potential lateral movement within connected networks. Some related vulnerabilities further lower the attack barrier by enabling unauthenticated remote command execution (RCE), increasing the risk of exploitation from external sources. The flaw underscores the critical need for immediate firmware updates, network access restrictions, and continuous monitoring to safeguard critical network infrastructure.
Remote Command Execution: CVE-2025-6541 allows attackers to execute arbitrary operating-system commands on the gateway, potentially leading to complete device compromise.
Unauthorized Access: Exploiting vulnerabilities enables attackers to bypass input restrictions and gain control over critical network management functions.
Privilege Escalation: Attackers can leverage command execution to escalate privileges on the device, potentially gaining root-level access.
Data Theft & Integrity Risks: Unauthorized access can expose administrative credentials, configuration data, VPN settings, and other sensitive information, with the risk of manipulation or exfiltration.
Operational Disruptions: Compromise may disrupt network routing, VPN connectivity, and overall device functionality, causing service interruptions and operational impact.
High Risk Due to Ease of Exploitation: Related vulnerabilities, including unauthenticated RCE (CVE-2025-6542), increase the likelihood of exploitation, making it a critical concern for organizations relying on Omada Gateways.
This vulnerability affects multiple TP-Link Omada Gateway models prior to the October 2025 patched firmware builds, including but not limited to:
Is there already an exploit tool to attack this vulnerability?
As of current public reporting, there are no widely published, confirmed exploit toolkits or public PoC scripts specifically attributed to CVE‑2025‑6541.
Has this vulnerability already been used in an attack?
TP‑Link’s advisory and several news outlets state there is currently no evidence of active exploitation of Omada gateway flaws in the wild. Vendor guidance treats the flaws as high‑risk and urges immediate remediation because related issues (including an unauthenticated RCE) significantly increase exposure if left unpatched.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Public reporting and open‑source monitoring show discussion across mainstream social platforms and security blogs, but there is no verified public intelligence indicating wide‑scale Dark Web trade or exploit sales specific to CVE‑2025‑6541 currently. That said, when high‑impact gateway vulnerabilities appear, chatter can migrate quickly to underground forums—so targeted dark‑web monitoring is recommended.
What is the attack complexity level?
The attack complexity for CVE‑2025‑6541 is classified as LOW. Exploiting this vulnerability does require significant technical expertise, making it accessible to both advanced threat actors and lower-skilled cybercriminals.
Historical Trends and Known Exploits
Network appliance RCEs and command‑injection flaws are high‑value targets: past router/gateway vulnerabilities have frequently been weaponized for persistent footholds, credential theft, and lateral movement. Given that TP‑Link patched four related Omada issues (two enabling arbitrary command execution, one unauthenticated), the overall threat posture is elevated — especially because unauthenticated variants (CVE‑2025‑6542) lower the barrier for attackers. Even though there is no confirmed active exploitation of CVE‑2025‑6541 at this moment, historical patterns imply rapid weaponization if PoCs appear or scans reveal exposed management interfaces.
Organizations should immediately patch affected systems, monitor suspicious activity, and implement strict access controls to mitigate the risk.
How Does CVE-2025-6541 Work?
Example:
Suppose there is a form to set a DNS server:
When this input is processed, the resulting shell command might look like:
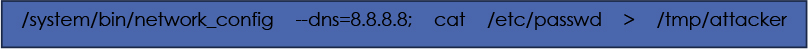
With no input sanitization, the second command (cat /etc/passwd > /tmp/attacker) is executed with the same privileges as the admin process—potentially exposing sensitive files or compromising the entire device.
To reduce the risks associated with CVE-2025-6541, organizations should implement the following measures:
Target Geography
CVE-2025-6541 has a global impact, affecting organizations and individuals deploying TP-Link Omada Gateway devices across North America, Europe, Asia, and other regions. Enterprises, SMBs, and service providers that rely on these gateways for routing, VPN, and network management are all potentially at risk. Given the wide deployment in offices, branch networks, and remote sites, the vulnerability represents a high-priority concern for organizations with exposed management interfaces.
Target Industry
This vulnerability poses a significant threat to industries that depend on secure and reliable network infrastructure:
Adversaries likely target sectors handling sensitive data or critical operations, increasing risks of compromise, credential theft, and disruption.
Target Technology
The vulnerability affects multiple Omada Gateway models prior to the October 2025 firmware patches. Exploitation allows remote command execution via the web management interface, potentially compromising routing configurations, VPN credentials, and network security. Organizations with interconnected networks, cloud-managed sites, or publicly exposed management interfaces face heightened exposure, emphasizing the importance of rapid patching and access restrictions.
Currently, threat actors are not actively discussing this vulnerability. However, the CYFIRMA Research team continues to monitor for any new developments or discussions. In the past, threat actors have exploited and sold the RCE vulnerability, as shown in the image below.
The case of CVE-2025-6541 underscores the critical risks associated with improper input validation and insufficient access controls in widely deployed enterprise network devices. This vulnerability highlights the importance of proactive security measures, including timely firmware updates, restricted administrative access, and continuous monitoring of web-management interfaces.
TP-Link Omada Gateways, serving as central routing and VPN devices, are high-value targets for attackers seeking to gain network footholds or exfiltrate sensitive data. This incident demonstrates that even core network infrastructure can be vulnerable to exploitation if security hygiene is not rigorously maintained. Regular security assessments, network segmentation, threat intelligence monitoring, and incident response planning remain essential for organizations to defend against emerging threats and reduce the likelihood of operational disruptions or compromise.