


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found White Lock Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
White Lock Ransomware
Researchers have identified a new ransomware strain known as White Lock, which functions by encrypting user data and appending the .fbin extension to affected files. Once the encryption process is complete, the malware generates a ransom note in a file titled “c0ntact.txt”, where instructions to the victim are provided. The encryption mechanism ensures that files cannot be accessed without the corresponding decryption key held by the attackers, effectively locking the victim out of their own data.
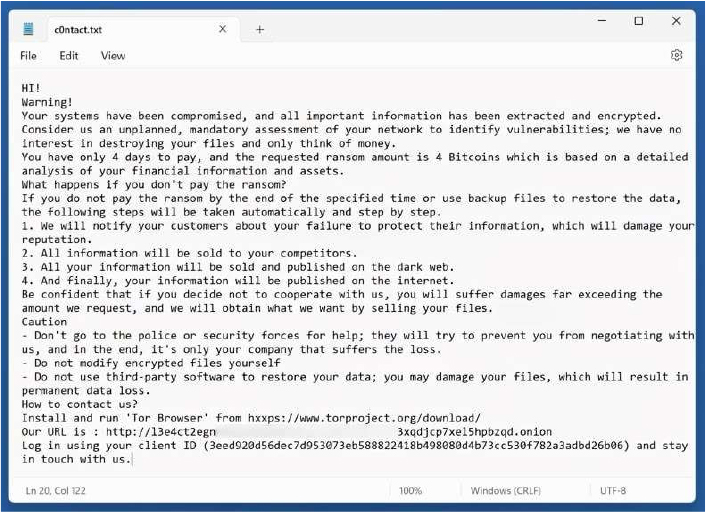
The ransom notes contained in c0ntact.txt informs the victim that their network has been compromised, with both encryption and data exfiltration carried out during the attack. It states that the attackers demand 4 Bitcoin as payment, giving the victim a four-day deadline. The message outlines a sequence of consequences if the ransom is not met notifying customers of the breach, selling the stolen data to competitors, publishing it on the dark web, and eventually releasing it openly online. The note also includes explicit warnings against contacting law enforcement, using third-party recovery tools, or attempting manual decryption, claiming that such actions could result in permanent data loss. Victims are directed to use the Tor Browser to access a provided onion URL, where they are instructed to log in with a client ID to initiate communication with the attackers.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1518 | Software Discovery |
| Commandand Control | T1071 | Application Layer Protocol |
| Commandand Control | T1090 | Proxy |
| Commandand Control | T1571 | Non-Standard Port |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1529 | System Shutdown/Reboot |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that White Lock represents an advanced threat blending strategic extortion with operational sophistication. Beyond immediate encryption, its design reflects potential for rapid adaptation, targeting multiple vectors within corporate networks while exploiting gaps in backup strategies and access controls. The malware’s architecture suggests future iterations could incorporate automated lateral movement, enhanced evasion of detection, and streamlined exfiltration pipelines, making containment more challenging and amplifying operational disruption for victims. White Lock as a high-stakes extortion actor that deliberately prioritizes large, enterprise-level victims to maximize payout potential. Its operational profile combining theft with crippling disruption indicates an appetite for high-value targets and negotiable demands far above consumer- or SMB-focused campaigns.
From a strategic perspective, White Lock highlights the increasing convergence of cybercrime and organizational risk management. Its evolution could push ransomware toward service-oriented models, where attack orchestration and leak management become highly scalable. Organizations should therefore prioritize proactive detection frameworks, continuous threat hunting, and resilient recovery planning to counter both present threats and the likely trajectory of similar, more sophisticated malware campaigns.
Sigma rule:
title: Potentially Suspicious Desktop Background Change Via Registry tags:
– attack.defense-evasion
– attack.impact
– attack.t1112
– attack.t1491.001 logsource:
product: windows category: registry_set
detection: selection_keys:
TargetObject|contains:
– ‘Control Panel\Desktop’
– ‘CurrentVersion\Policies\ActiveDesktop’
– ‘CurrentVersion\Policies\System’ selection_values_1:
TargetObject|endswith: ‘NoChangingWallpaper’
Details: ‘DWORD (0x00000001)’ # Prevent changing desktop background selection_values_2:
TargetObject|endswith: ‘\Wallpaper’ selection_values_3:
TargetObject|endswith: ‘\WallpaperStyle’
Details: ‘2’ # Stretch filter_main_svchost:
# Note: Excluding GPO changes Image|endswith: ‘\svchost.exe’
condition: selection_keys and 1 of selection_values_* and not 1 of filter_main_* falsepositives:
– Administrative scripts that change the desktop background to a company logo or other image.
level: medium (Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Data theft, Financial Fraud | Target Technology: Android OS| Target Industry: Finance sector (banking & crypto services) | Target Geographies: Australia, Malaysia, Singapore, Canada, South Africa, United Kingdom
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Datzbro” is trending.
Overview of Datzbro Malware
Researchers newly discovered an Android Trojan dubbed Datzbro, a device-takeover malware embedded within a deceptive campaign that exploited seniors through fake Facebook groups promoting “active senior trips” and similar social events. The threat gained global traction after its Command-and-Control builder was leaked online, allowing cybercriminals worldwide to weaponize it freely. Analysis revealed numerous Facebook groups filled with AI-generated posts and images, all posing as genuine communities for seniors in regions such as Australia, Malaysia, Singapore, Canada, South Africa, and the UK. Despite targeting diverse audiences, the uniform content and design across these groups indicates a single coordinated operation, highlighting how cybercriminals are shifting tactics to exploit emotional trust and social connection, turning familiar online spaces into tools for large-scale digital manipulation.
Technical Analysis
The campaign used AI-generated posts in fake Facebook groups to engage seniors, promoting “active senior trips” and similar activities. These posts successfully attracted the target audience, prompting fraudsters to contact interested users via Messenger or WhatsApp and direct them to download a “community” app. In some cases, victims were even asked to pay a sign-up fee, resulting in phishing attempts and theft of card details.
While links for iOS were inactive placeholders, clicking the Google Play button triggered the download of a malicious APK. Researchers observed instances where Datzbro was installed directly on devices, as well as cases where a dropper, such as Zombinder, was used to bypass Android 13+ restrictions, demonstrating the threat actors’ adaptability in reaching their targets.
Once installed, Datzbro provides attackers with extensive remote-control capabilities, allowing access to files, photos, audio, and video. Fraudulent activity is concealed through a “black overlay” feature, which hides any malicious actions from the user while still giving the operator full control of the device.
Additionally, Datzbro focuses on financial exploitation, logging accessibility events related to banking and crypto apps and prompting victims to enter PINs, passwords, and other sensitive credentials. This combination of social engineering and technical capabilities highlights the malware’s dual focus on device takeover and financial theft, making it a significant threat to users worldwide.
Origins and Global Reach
Analysis of Datzbro reveals its roots in China, with debug and logging strings in Chinese and some samples named “最强远控.apk” (“The most powerful remote control”), suggesting the developers’ origin. Unlike typical banking Trojans, Datzbro uses a desktop-
based command-and-control application, which was later leaked online and became accessible to cybercriminals globally. Early campaigns targeted Chinese-speaking users, showing that the malware evolved from a regional threat into one with international distribution and impact.
Following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| Initial Access | T1660 | Phishing |
| Privilege Escalation | T1626 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1655 | Masquerading |
| Credential Access | T1417.001 | Input Capture: Keylogging |
| Credential Access | T1517 | Access Notifications |
| Discovery | T1421 | System Network Connections Discovery |
| Discovery | T1424 | Process Discovery |
| Discovery | T1426 | System Information Discovery |
| Discovery | T1430 | Location Tracking |
| Collection | T1517 | Access Notifications |
| Collection | T1429 | Audio Capture |
| Collection | T1513 | Screen Capture |
| Collection | T1512 | Video Capture |
| Collection | T1636.003 | Protected User Data: Contact List |
| Collection | T1636.004 | Protected User Data: SMS Messages |
| Command and Control | T1437 | Application Layer Protocol |
| Command and Control | T1509 | Non-Standard Port |
| Command and Control | T1521 | Encrypted Channel |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that campaigns like Datzbro could increasingly affect not just organizations and employees but also everyday users and digital ecosystems at large. As AI-generated content becomes more convincing and malware tools more widely accessible, ordinary users may face higher risks of account compromise, identity theft, and financial fraud even during casual online interactions. Social platforms and online communities could be exploited more frequently as vectors for trust-based manipulation, while cross-border distribution of such malware may challenge law enforcement and cybersecurity coordination. Over time, these trends suggest a growing environment where digital trust is harder to maintain, and the consequences of falling victims extend beyond individuals to families, social networks, and broader online infrastructures.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Datzbro_Indicators
{
meta:
description = “Detects Datzbro malware indicators” author = “CYFIRMA”
malware_family = ” Datzbro”
strings:
// SHA256 File Hashes
$sha256_1 = “a57d70b2873d9a3672eda76733c5b2fb96dca502958064fab742cfc074bf0feb”
$sha256_2 = “453b0a62e414e9b40185c63842546fc96e8e1ab3f77d3230b02988dd8834c555”
$sha256_3 = “ed2313bfebe03ff29a7c802ddd471583cc8da76bf5cb9f418ae7d999d6a0b9fb”
$sha256_4 = “fac119c569ba7dd19df9154f22f928cf3f0b0165bbe7d6b11a77215bdfc2a11a”
condition:
any of ($sha256*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
The Sandworm Playbook: How APT44 Wages Cyber War
About the Threat Actor
The advanced persistent threat group APT44, also known as Sandworm, is believed to be responsible for the Petya ransomware attack in Ukraine. Their activities were first observed in December 2016, when they targeted Ukrainian financial institutions and critical infrastructure. According to dark web sources, the group also operates under the names TeleBots & Electrum, and is believed to be funded by the Russian government. They maintain close ties with the BlackEnergy group, which was behind the infamous 2015 power outages in Ukraine.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2025- 0282 | Ivanti Connect Secure | 9.0 | – |
| CVE-2020- 1472 | Microsoft Windows domain controllers | 10.0 | Link1, link2 |
| CVE-2022-30190 | MSDT | 7.8 | link |
| CVE-2021-27065 | Microsoft Exchange Server | 7.8 | link1, link2 |
| CVE-2024- 7344 | Howyar UEFI Application | 8.2 | – |
| CVE-2023-38831 | RARLAB WinRAR | 7.8 | link |
| CVE-2017-11882 | Microsoft Office | 7.8 | link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1592.002 | Gather Victim Host Information: Software |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning |
| Reconnaissance | T1589.002 | Gather Victim Identity Informati on: Email Addresses |
| Reconnaissance | T1589.003 | Gather Victim Identity Information: Employee Names |
| Reconnaissance | T1590.001 | Gather Victim Network Information: Domain Properties |
| Reconnaissance | T1591.002 | Gather Victim Org Information: Business Relationships |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1593 | Search Open Websites/Domains |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583 | Acquire Infrastructure |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1586.001 | Compromise Accounts: Social Media Accounts |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1584.005 | Compromise Infrastructure: Botnet |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.006 | Obtain Capabilities: Vulnerabilities |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1195 | Supply Chain Compromise |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1078.002 | Valid Accounts: Domain Accounts |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1106 | Native API |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1072 | Software Deployment Tools |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1554 | Compromise Host Software Binary |
| Persistence | T1136 | Create Account |
| Persistence | T1136.002 | Create Account: Domain Account |
| Persistence | T1543.002 | Create or Modify System Process: Systemd Service |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1133 | External Remote Services |
| Persistence | T1112 | Modify Registry |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1505.001 | Server Software Component: SQL Stored Procedures |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1078.002 | Valid Accounts: Domain Accounts |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1543.002 | Create or Modify System Process: Systemd Service |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1078 | Valid Accounts |
| Privilege Escalation | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1484.001 | Domain or Tenant Policy Modification: Group Policy Modification |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.002 | Impair Defenses: Disable Windows Event Logging |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1036.010 | Masquerading: Masquerade Account Name |
| Defense Evasion | T1027.010 | Obfuscated Files or Information: Command Obfuscation |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1055 | Process Injection |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1087.003 | Account Discovery: Email Account |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1072 | Software Deployment Tools |
| Lateral Movement | T1570 | Lateral Tool Transfer |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Collection | T1213 | Data from Information Repositories |
| Collection | T1005 | Data from Local System |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1572 | Protocol Tunneling |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1090 | Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1491.002 | Defacement: External Defacement |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1499 | Endpoint Denial of Service |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1489 | Service Stop |
Latest Developments Observed
The threat actor is carrying out a campaign, BadPilot, on a global scale, targeting energy, oil and gas, telecommunications, shipping, arms manufacturing, and government entities. The threat actor is potentially discovering and compromising numerous Internet-facing systems, exploiting vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709), Fortinet FortiClient EMS security software (CVE-2023-48788), predominantly affecting Ukraine, Europe, and specific verticals in Central and South Asia, and the Middle East.
ETLM Insights
Sandworm is an advanced persistent threat (APT) group, widely attributed to Russia’s General Staff Main Intelligence Directorate (GRU). The group is well-established and has had extensive time to develop, test, and refine its tactics, techniques, and procedures.
It is known for conducting long-duration, highly coordinated attack campaigns, with a consistent emphasis on destructive operations rather than traditional objectives, such as data theft or financial gain. This focus underscores the group’s role as a strategic, state- sponsored actor intent on disruption, destabilization, and long-term intelligence collection supporting Russian strategic objectives.
YARA Rules
rule APT_Multi_IOC_Match
{
meta:
author = “CYFIRMA”
description = “Detects presence of IOCs related to multiple CVEs, IPs, and suspicious files/domains”
date = “2025-10-07”
reference = “Generated from threat intelligence input”
strings:
// IP Addresses (as text)
$ip1 = “208.91.197.27”
$ip2 = “172.67.174.99”
$ip3 = “172.67.174.93”
$ip4 = “104.21.64.14”
$ip5 = “127.0.0.1”
// Domains
$domain1 = “mariamchurch.com”
$domain2 = “techzenspace.com”
$domain3 = “dattolocal.net”
// CVEs
$cve1 = “CVE-2025-0282”
$cve2 = “CVE-2020-1472”
$cve3 = “CVE-2022-30190”
$cve4 = “CVE-2021-27065”
$cve5 = “CVE-2024-7344”
$cve6 = “CVE-2023-38831”
$cve7 = “CVE-2017-11882”
// Suspicious file indicators
$file1 = “hrm3jvh9v.dll”
$file2 = “multi-user.target”
condition:
any of ($ip*) or
any of ($domain*) or any of ($cve*) or any of ($file*)
}
Recommendations Strategic
Management
Tactical
Chinese Hackers Breached Foreign Ministers
A Chinese-aligned hacking group, dubbed Phantom Taurus, has been targeting foreign ministries, embassies, and telecom providers across Africa, the Middle East, and Asia for about two-and-a-half years. The group aims to steal sensitive geopolitical and military intelligence, often timing attacks with major global or regional events. Phantom Taurus uses advanced tactics, including a new malware suite called NET-STAR, alongside known Chinese malware like China Chopper, to conduct covert operations and maintain long- term access to critical targets. The group has shifted from targeting emails to extracting entire databases, focusing on technology providers to governments to access diplomatic and defense-related information. NET-STAR, designed to target Microsoft’s Internet Information Services web servers, employs sophisticated evasion techniques, making it hard to detect by disabling security monitoring features.
ETLM Assessment:
Phantom Taurus shares infrastructure with other Chinese hacking groups like APT27, Winnti, and Mustang Panda, but stands out for its evolved tactics and custom tools. Chinese APT groups have long targeted foreign ministries and embassies in a variety of ways over the last decade. In addition to longstanding attacks on U.S. diplomats, Chinese groups have been accused of attacking governments and embassies in Sweden, France, the U.K., Ukraine, Hungary, Singapore, the Czech Republic, Japan, Lithuania, multiple Southeast Asian countries, and several Pacific islands.
The Killsec Ransomware Impacts WalletKu Indompet Indonesia
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia, WalletKu Indompet Indonesia (http [:] //www.walletku.com/), was compromised by Killsec Ransomware. Walletku is a digital financial service application created to facilitate online transactions, with a focus on micro, small, and medium enterprises (MSMEs) that often lack access to bank accounts or face difficulties conducting daily transactions via mobile devices. Developed by PT Walletku Indompet Indonesia and headquartered in Jakarta, Walletku stands as one of the pioneering digital wallet platforms in Indonesia, specifically catering to users without traditional banking access. The application offers a variety of services, including bill payments, prepaid phone credit sales, travel ticket purchases, and more, empowering small businesses and individuals to efficiently manage their financial activities digitally. The compromised data includes personally identifiable information (PII), financial records, confidential documents, and other sensitive information belonging to the organization.
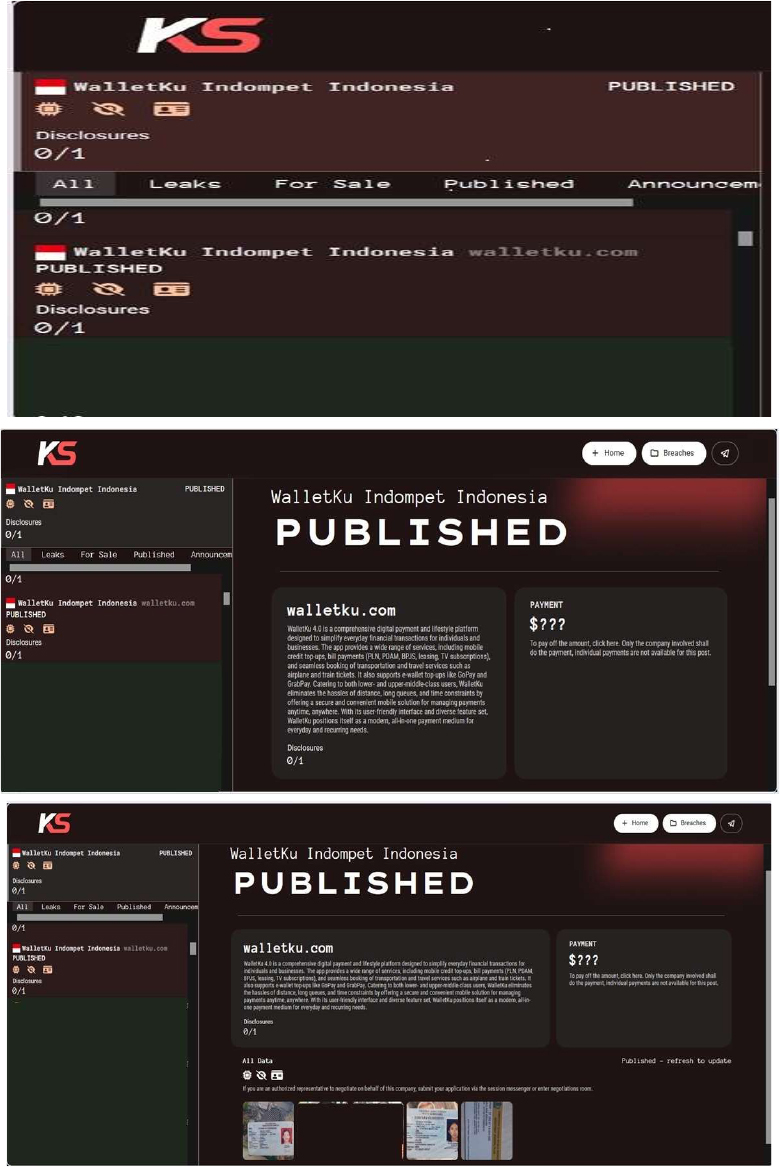
Relevancy & Insights:
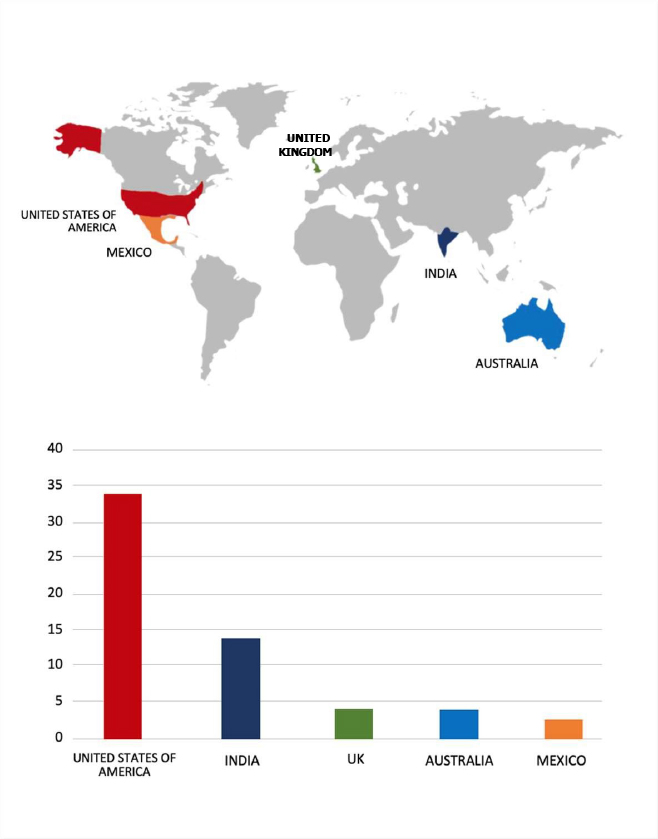
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Medusa Ransomware Impacts Future Generali
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India, Future Generali(https[:]//online[.]futuregenerali[.]in/), was compromised by Medusa Ransomware. Future Generali India is a joint venture between the global Generali Group and Indian partners, offering both life and general insurance. The company provides a wide range of products, including motor, health, travel, savings, and protection plans. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
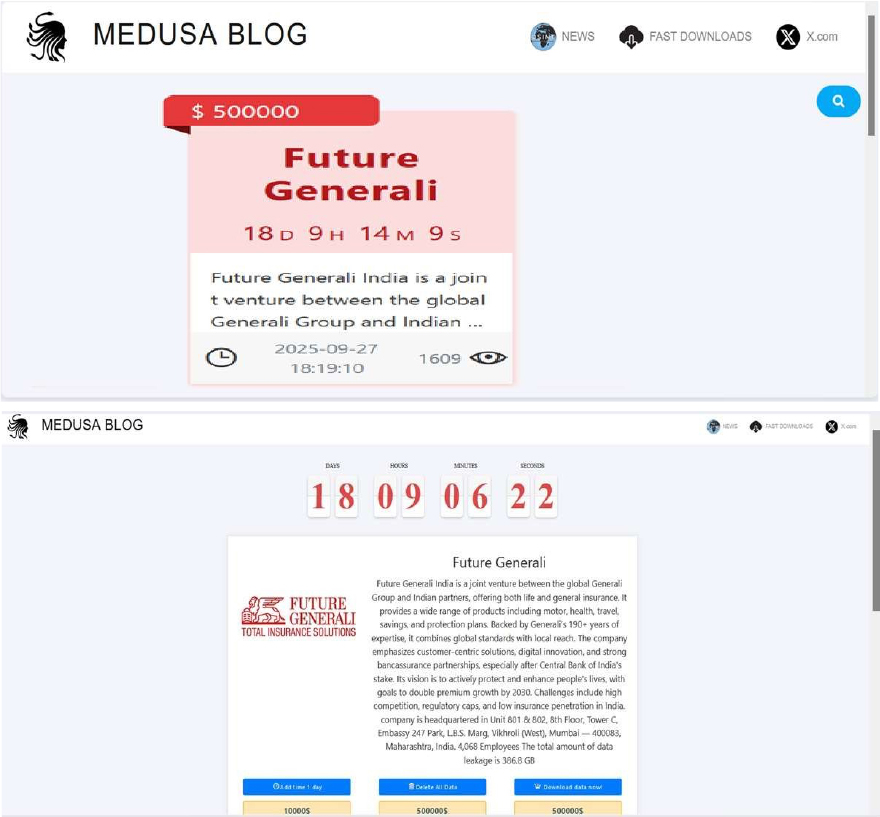
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Medusa Ransomware continues to pose a significant threat across various sectors. The group’s sophisticated tactics and aggressive demands highlight the need for organizations to enhance their cybersecurity measures, including regular updates, employee training on phishing recognition, and robust incident response plans to mitigate risks associated with ransomware attacks.
Vulnerability in Logback
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied input when parsing the configuration file. A remote attacker can trick the victim into using a specially crafted configuration file and execute arbitrary code on the system.
Impact:
Successful exploitation of the vulnerability requires the presence of the Janino library and Spring Framework on the user’s class path.
Affected Products:
https://logback.qos.ch/news.html#1.5.19
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
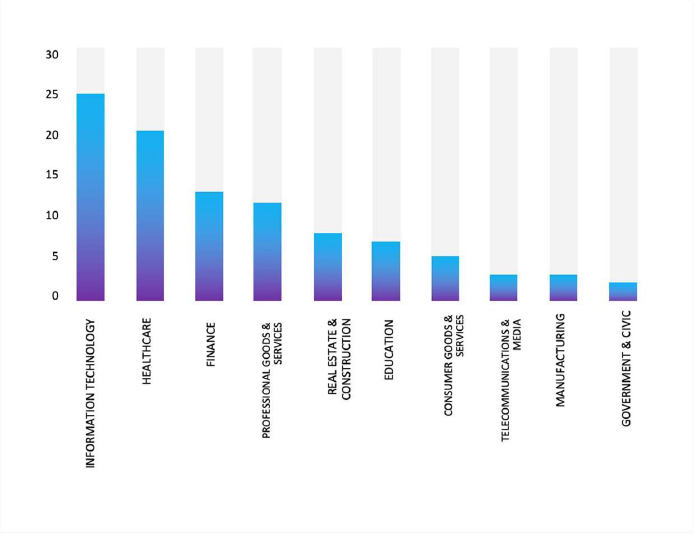
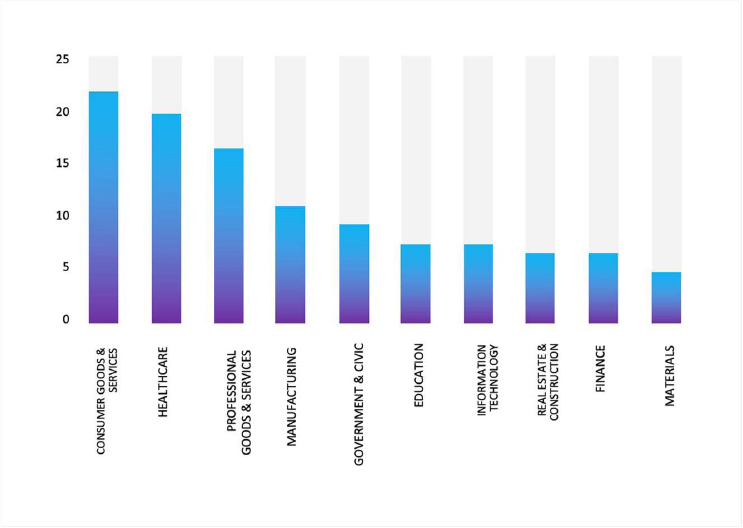
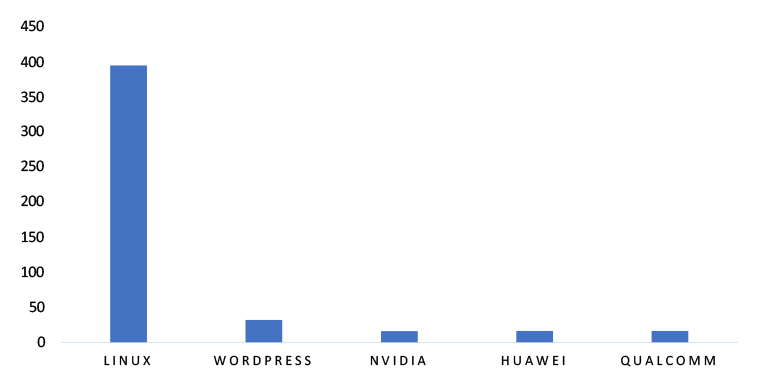
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Logback is an open-source logging framework for Java applications, intended as the successor to Log4j. It is designed for high performance and flexibility, offering advanced filtering, configuration through XML or Groovy, and seamless integration with the SLF4J (Simple Logging Facade for Java) API.
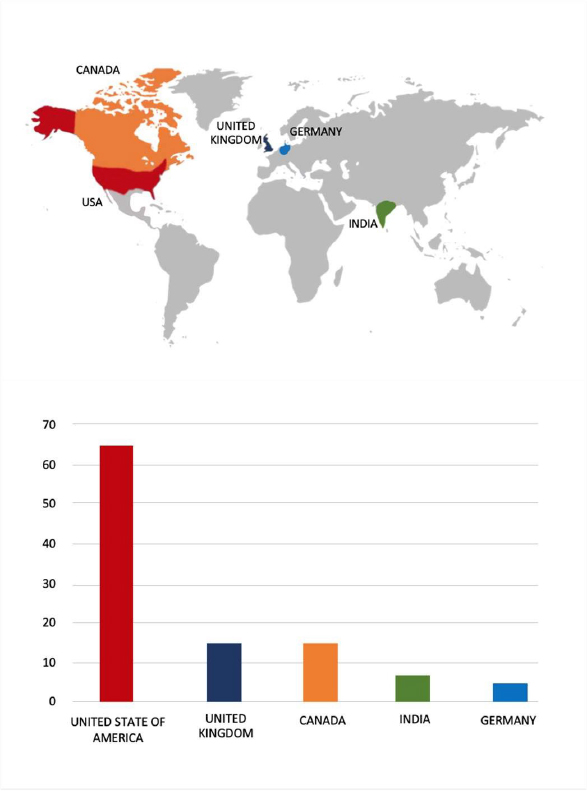
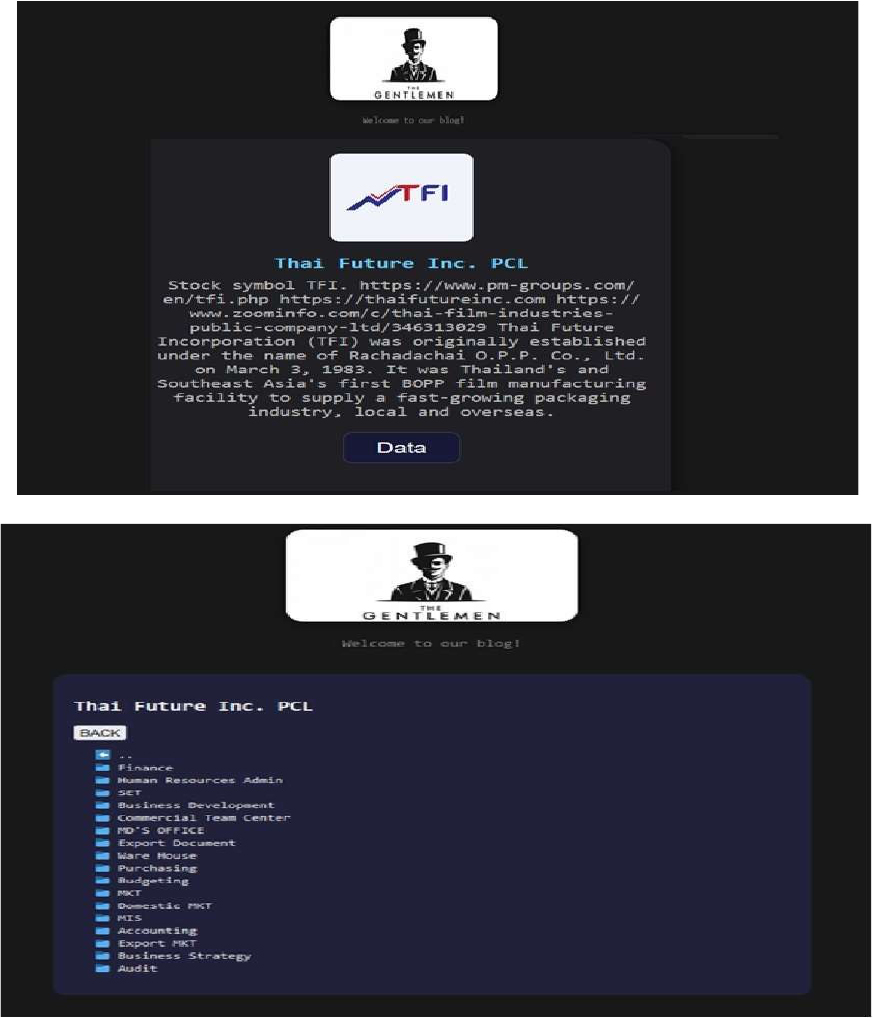
The Gentlemen Ransomware attacked and published the data of Thai Future Incorporation Public Company Limited
Summary:
Recently, the Gentlemen Ransomware was observed attacking and publishing the data of Thai Future Incorporation Public Company Limited (https[:]//thaifutureinc[.]com/) on its dark web website. Thai Future Incorporation Public Company Limited, formerly known as Thai Film Industries Public Company Limited, is a Thailand-based company engaged in the manufacturing and distribution of packaging films. Their product range includes biaxially oriented polypropylene (BOPP) films, cast polypropylene (CPP) films, and metallized films.
These films are used in various applications, such as flexible packaging, publishing, flower wraps, adhesive tapes, labels, textile bags, overwraps, fresh produce packaging, and biodegradable products. The company operates across Thailand, Asia, Europe, America, and other regions. Thai Future Incorporation PCL is recognized as the world’s leading manufacturer of BOPP films and is a pioneer in the film industry within Southeast Asia.
The data leak resulting from the ransomware attack encompasses information from various departments including Finance, Human Resources & Administration, Stock Exchange of Thailand (SET), Business Development, Commercial Team Center, Managing Director’s Office, Export Documentation, Warehouse, Purchasing, Budgeting, Marketing, Domestic Marketing, Management Information Systems (MIS), Accounting, Export Marketing, Business Strategy, and Audit.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen ransomware group exemplifies the rising sophistication and persistence of modern ransomware actors, necessitating tailored enterprise defenses and vigilant threat monitoring.
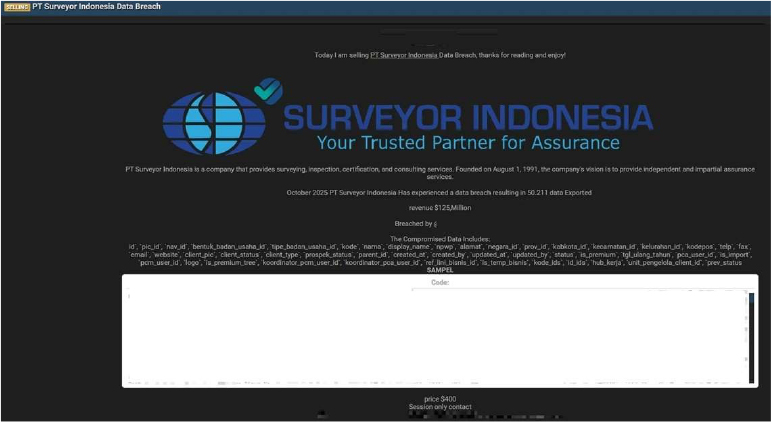
PT Surveyor Indonesia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor, “ KaruHunters”, claims to have breached and is selling data from PT Surveyor Indonesia, a state-owned enterprise that provides surveying, inspection, certification, and consulting services. The company, founded in 1991, provides independent assurance services across various sectors.
The actor posted the alleged data breach on a dark web forum, claiming to have exported 50,211 records from the company’s systems.
According to the actor, the compromised data includes a wide range of client and corporate information. The database headers listed in the breach notification suggest the following types of information were exposed:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Kiple Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “888” claims to have breached Kiple, a Malaysian company specializing in digital payment solutions. According to a post on a dark web forum, the incident occurred in October 2025, resulting in the theft of the company’s source code. Kiple, a Greenpacket company, provides services including e-wallets, Visa prepaid cards, and e-wages for salary disbursements, and is a partner of Visa and Alibaba Cloud. The leak appears to encompass a wide range of the company’s internal and external-facing projects.
The actor claims to have stolen and leaked the company’s entire source code, posting a link to a 3.71 GB archive. Analysis of the leaked file structure suggests the compromised source code includes numerous projects and systems. According to the actor, the data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “KaruHunters” is a highly active and sophisticated group specializing in data leaks. Numerous credible sources attribute multiple security breaches to this group, involving unauthorized access to systems and the illicit sale of stolen data on dark web marketplaces. KaruHunters’ operations highlight the persistent and evolving nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to enhance their cybersecurity posture through continuous monitoring, leveraging advanced threat intelligence, and adopting proactive defense strategies to protect sensitive data and vital infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor is selling network access to a leading software development company based in Vietnam. The company is reported to have an annual revenue of $17 million.
According to the actor, the offered access includes sensitive corporate systems. The allegedly compromised access includes:
The authenticity of this access sale remains unverified at the time of reporting, as the claim originates solely from the threat actor.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
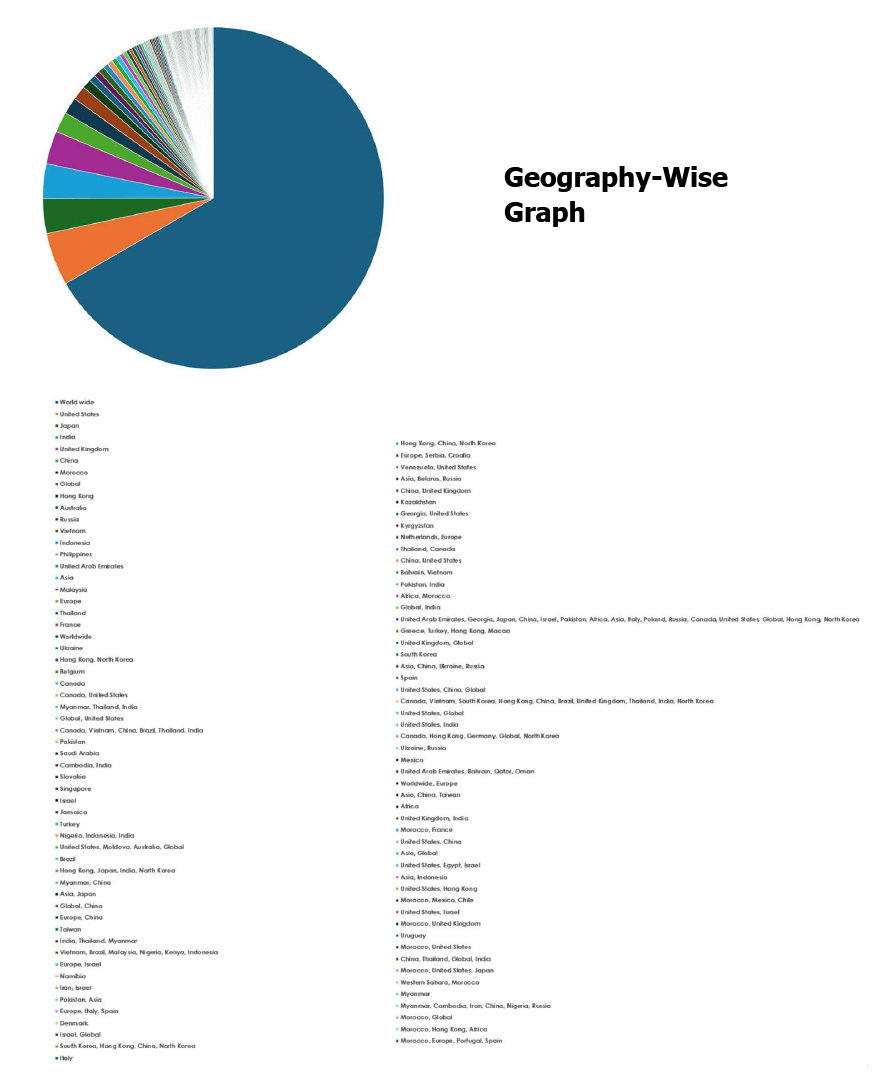
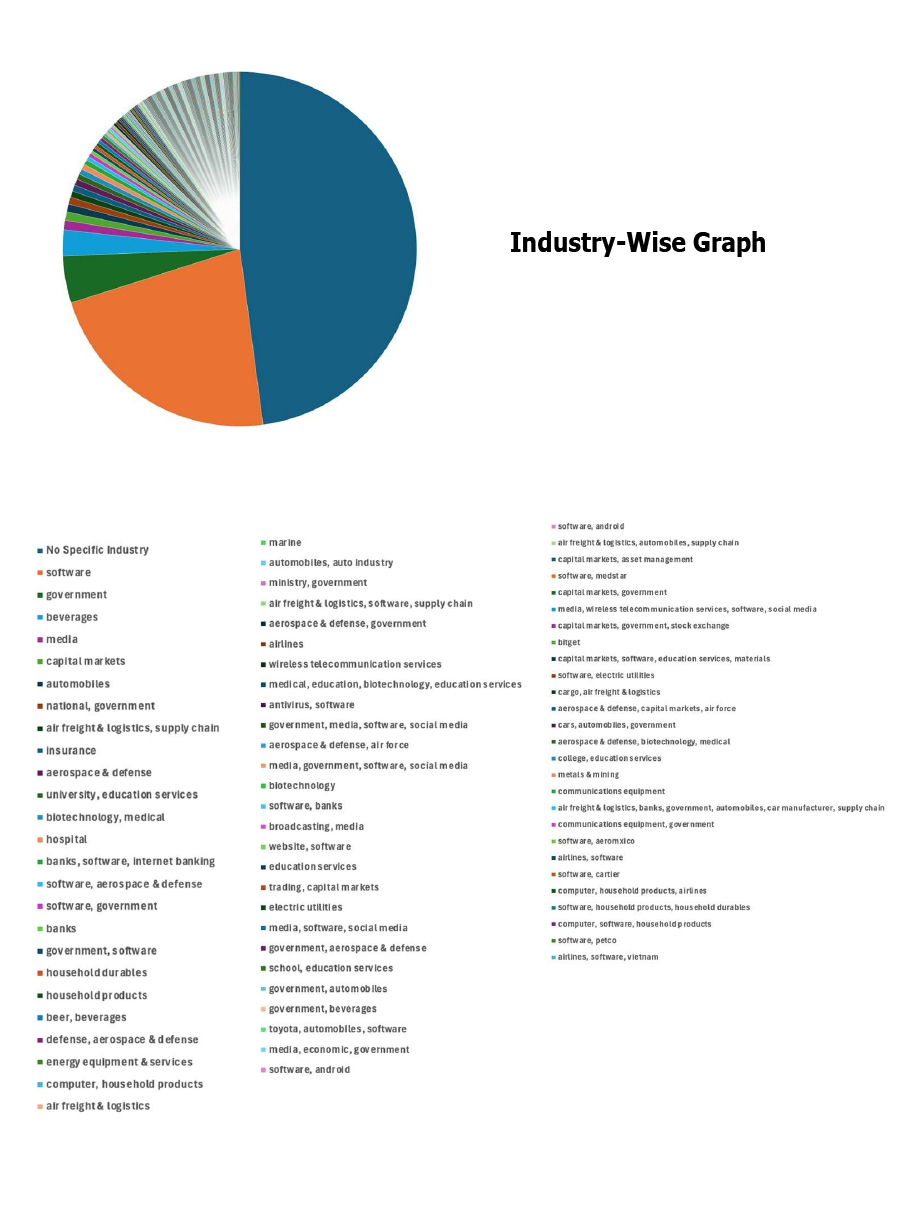
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.