


In 2025, Saudi Arabia witnessed a notable rise in cybercriminal activity, particularly within the dark web landscape. Threat actors increasingly targeted key sectors, including government institutions, financial services, transportation, shipping, and healthcare, leading to a series of high-impact data breaches. Compromised data ranged from personally identifiable information (PII) and financial records to internal government documents and sensitive corporate information. Hacktivist groups, such as Keymos, were also active, launching DDoS attacks that disrupted online services. Additionally, ransomware incidents saw a sharp increase, with groups like KillSecurity, Everest Ransom, and Qilin Ransomware conducting significant attacks against Saudi-based organizations. This evolving threat environment highlights the critical need for stronger cybersecurity frameworks, improved regulatory enforcement, and advanced threat intelligence capabilities to safeguard national digital assets.
Note: The authenticity of the breaches below remains unverified at the time of reporting, as the claims originate solely from the threat actor.
On 13 September 2025, a threat actor operating under the alias “privilege” leaked a database containing 1,845 user records from a delivery and shipping management platform serving the MENA region. The compromised dataset includes information on both customers and internal system users, exposing details such as full names, verified email addresses, bcrypt-hashed passwords, avatars, client IDs, and activity timestamps. A logistics provider with operations in Jordan, Iraq, and Saudi Arabia has been particularly impacted, with the leaked records containing Arabic names alongside international emails.
In May 2024, Riyadh Airport (Saudi Arabia) suffered a data breach impacting 864 employees. A threat actor uploaded the stolen database on a cybercrime forum on 1 June 2024. The compromised data includes employee numbers, full names, corporate email addresses, and mobile numbers. The leak exposes personally identifiable information (PII) of airport staff, increasing risks of phishing, targeted attacks, and identity misuse.
On 22 August 2024, a threat actor leaked a database allegedly belonging to a government department. The breach reportedly contains thousands of personal records, stored in SQL format with UTF-8 Arabic names. The leaked data appears to include patient information, clinical notes, illness types, medical history, and personal identifiers, posing a significant risk to privacy.
On September 9, 2025, a threat actor advertised the sale of a breached Saudi Arabian recruitment database on a well-known underground forum. The database reportedly contains approximately 150,000 records of job applicants and employees, exposing a wide range of sensitive personal information. This includes passport numbers, CV file paths, full names, email addresses, phone numbers, dates of birth, addresses, candidate details, job preferences, health conditions, marital status, emergency contacts, and more. According to the post, the data was extracted directly from the source system and left in its original format to ensure authenticity. The actor offered to provide additional samples upon request and claimed escrow services were available to facilitate secure transactions. A sample was shared via Pastebin, and communication was directed to a Telegram handle. The full dataset was being sold for $290, indicating a low-cost, high-risk breach with potentially severe privacy and national security implications for affected individuals in Saudi Arabia.
On May 20, 2024, a threat actor posted on an underground forum claiming to have access to a breached database from the Saudi Arabian pharmaceutical health field website. The leaked data, in SQL format, reportedly contains over 7 million records from the year 2023. A sample dump shared in the post reveals the inclusion of extensive personal and transactional information, such as full names, phone numbers, cities, towns, addresses, payment methods, and transaction details. Alarmingly, the dataset also contains sensitive medical-related information like height, weight, gender, blood type, pregnancy, and breastfeeding status. Other metadata, including user login attempts, last login, and discount usage, further amplifies the privacy risk. The full content is hidden behind a paywall requiring forum points, a common mechanism for monetizing stolen data in underground communities. This breach poses a significant threat to individual privacy and could be exploited for fraud, identity theft, or other malicious purposes.
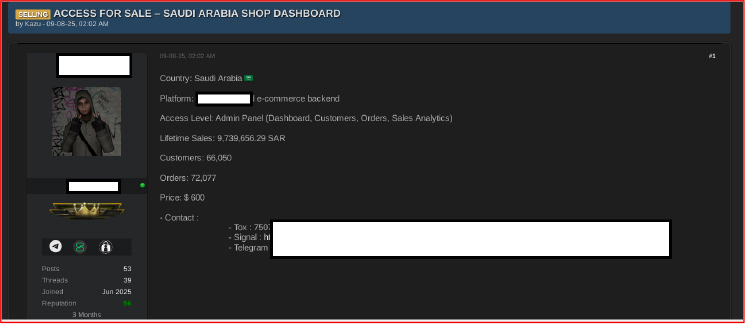
The listing below offers admin panel access to an e-commerce backend for a shop in Saudi Arabia. Posted by a seller on an underground forum on September 8, 2025, it provides full control over essential platform functions, such as dashboard management, customer information, order tracking, and sales analytics. The shop boasts lifetime sales of around 9.7 million SAR, with more than 66,000 customers and 72,000 orders. The asking price for this access is $600. Potential buyers can reach the seller via secure messaging apps like Tox, Signal, and Telegram, with all contact details included. The seller has a solid reputation on the forum, with a score of 56 and a history of 53 posts and 39 threads. The listing is up-to-date as of September 2025, and the seller has been a member since June 2025.
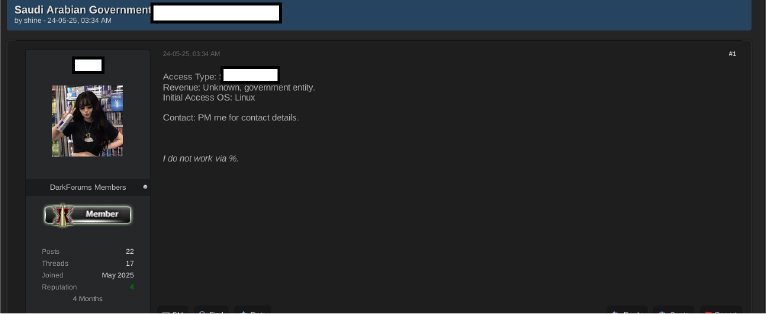
The post below was made by a user on May 24, 2025, and offers access to a server associated with a Saudi Arabian government entity. The access is granted via SSH using a key, with the server running on a Linux operating system. Although the revenue details are unknown, the target is identified as a government entity. The seller asks interested buyers to contact them through private message for further information and specifies that they do not engage in percentage-based deals. The poster has been a forum member since May 2025, with 22 posts, 17 threads, and a reputation score of 4. This listing suggests unauthorized access to a critical government system, indicating a significant security breach.
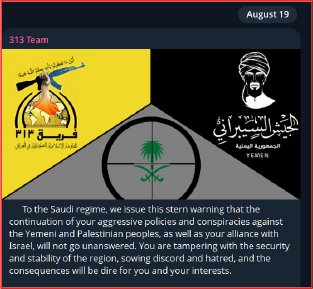
On August 19, 2025, the hacktivist group 313 Team issued a statement condemning the Saudi government’s policies and warning that failure to take action against Israel would result in severe cyberattacks. The group also claimed to be collaborating with other pro-Palestine and pro-Iranian hacktivist organizations, including the Yemen Cyber Army. This alliance suggests a potential escalation, where coordinated efforts among multiple hacktivist factions could significantly increase the scale and impact of cyberattacks targeting Saudi infrastructure and government-affiliated entities.
On August 17, 2025, a newly established channel called Cyber Unity started releasing what it claims are sensitive documents related to weaponry, including files that suggest Saudi Arabia’s involvement. The leaked materials, comprising PDFs and images, allege connections between both the CIA and Saudi Arabia. If these documents prove to be genuine, they could carry significant geopolitical and security consequences by revealing classified defense information and implicating Saudi Arabia in cooperation with U.S. intelligence. However, the authenticity of these leaks has yet to be confirmed, leaving open the possibility that this may be part of a wider disinformation effort aimed at undermining Saudi Arabia’s reputation.
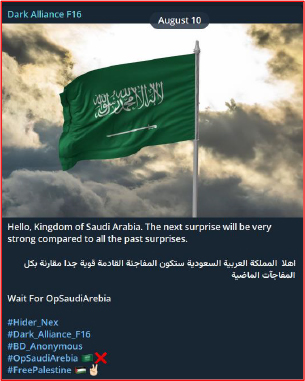
On August 10, 2025, threat actors associated with #Hider_Nex, #Dark_Alliance_F16, #BD_Anonymous, and #OpSaudiArabia posted a warning about an impending cyberattack targeting the Kingdom of Saudi Arabia. The message, released in both English and Arabic, declared that the upcoming “surprise” would be far more powerful than any previous attacks. The statement also expressed strong pro-Palestinian sentiments, using the hashtag #FreePalestine to emphasize their cause.
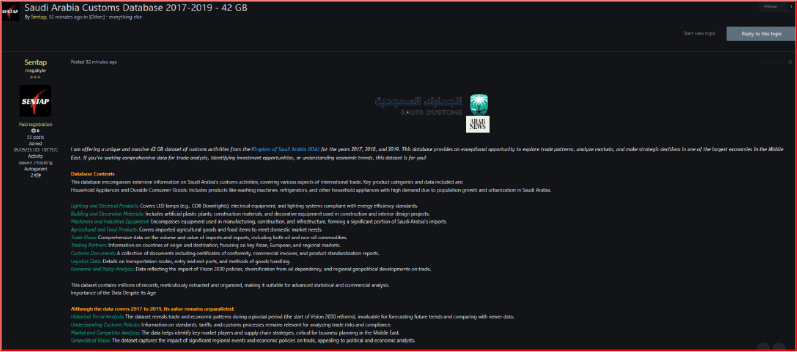
On August 6, 2025, a threat actor operating under the alias “Sentap” advertised on several underground forums a 42 GB dataset purportedly containing Saudi Arabia’s customs records from 2017 to 2019. The dataset reportedly includes comprehensive details on imports, exports, trading partners, certificates, and tariffs. This information was marketed to researchers, investors, and analysts focusing on Middle Eastern economic activities and trade patterns, with an asking price of $700.
On August 3, 2025, the group Shadow Cyber Unit leaked numerous login credentials for Saudi government-operated systems. The compromised accounts included access to the Noor System, Ministry of Education Projects (MIP), and various platforms under the Ministry of Human Resources and Social Development, among others. The leaks also contained links associated with Saudi government entities.
On July 30, 2025, a user known as “Supreme1” on DarkForum offered for sale root-level account privileges, including firewall and shell access, to a private cybersecurity firm headquartered in Saudi Arabia.
On July 25, 2025, the hacktivist group Keymous launched a DDoS attack targeting a private Bank website, causing it to become unresponsive.
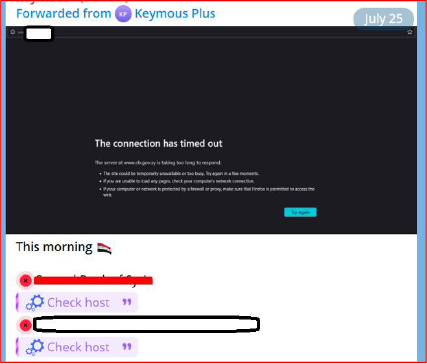
On July 21, 2025, a discussion resurfaced on a leak forum concerning a breach of a Saudi government entity. The original post, made on June 17, 2025, by a user named “chengyi,” claimed to include 1.4 million personal records (~600 MB) that were old but recently leaked. On July 21, another user responded, requesting a Telegram contact, suggesting a possible off-platform exchange of data.
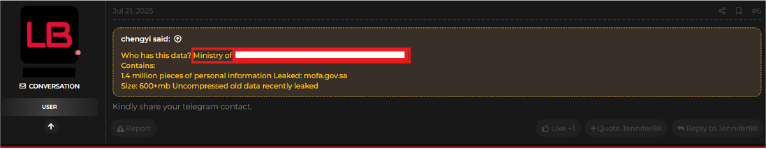
On July 7, 2025, a listing on a Chinese cybercrime forum advertised the initial release of alleged advanced account data from a Saudi Bank, claiming to include details of 690,000 high-value accounts with substantial balances. The dataset, priced at USD 420, was said to have been acquired through “self-infiltration” and was offered with automatic delivery and guaranteed uniqueness. Payments were accepted in USDT (ERC20/TRC20) or ETH. The post also referenced a different bank, suggesting either that multiple banks were targeted or there was a possible translation error.
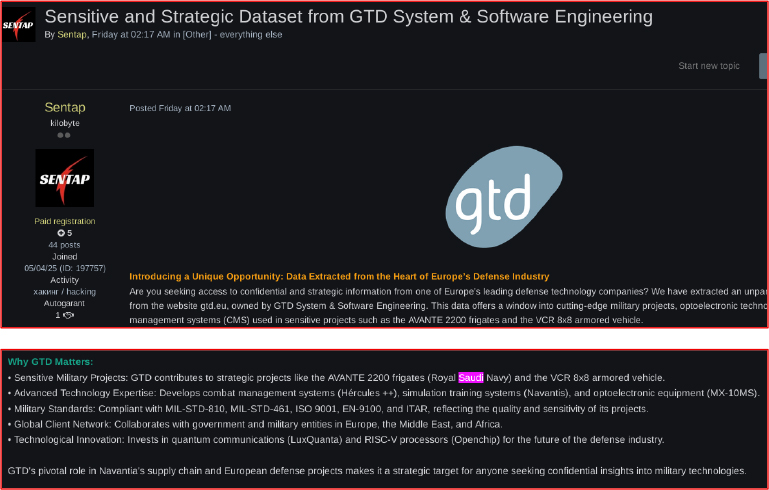
On June 13, 2025, a user named “sentap” posted on an exploit Forum offering a database from a private organization. This is especially notable for Saudi Arabia’s government entities, as the threat actor claimed the organization is involved in key projects, such as the AVANTE 2200 frigates for the Royal Saudi Navy. The leak poses significant risks by potentially exposing sensitive and classified information.
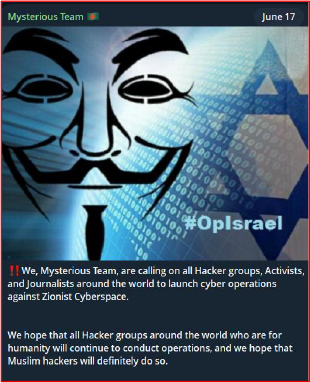
On June 17, 2025, a Bangladeshi hacktivist group known as Mysterious Team announced via their Telegram channel their intention to target Saudi Arabia, the United States, the United Kingdom, and other countries perceived as not taking action against Israel. This development is significant, as hacktivist groups can rapidly mobilize and carry out attacks like DDoS assaults or website defacements, with Saudi Arabia being a likely focus of such activities.
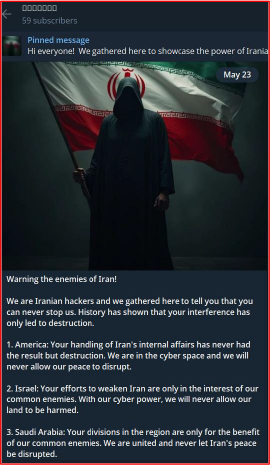
On May 23, 2025, an Iranian hacktivist group issued a warning against Saudi Arabia, the United States, and other nations, stating they would launch attacks if these countries intervened against Iran.
The dark web continues to serve as a major underground marketplace, where hackers and threat actors exchange information and trade illicit data. Analysis of dark web activity shows an increasing focus on targeting enterprises within Saudi Arabia. The CYFIRMA research team identified numerous posts from various threat actors aimed at Saudi-based organizations, with most involving the sale of customer databases and unauthorized access to corporate networks. Government institutions, healthcare, shipping, and financial services are the most frequently targeted sectors in Saudi Arabia, followed closely by transportation and additional healthcare-related industries. These patterns highlight the growing cyber risks faced by critical sectors in the Kingdom and emphasize the urgent need for enhanced cybersecurity measures to defend against evolving threats.
On September 19, 2025, a Saudi-based medical center was listed by the ransomware group KillSecurity as a victim. Based in Riyadh, the medical center specializes in advanced medical services, including diagnostics, lab testing, and aesthetic procedures. According to KillSecurity, the attackers claim to have exfiltrated a range of sensitive data, including medical records, biopsy reports, patient invoices, lab results, and internal financial documents, such as asset depreciation files. A ransom deadline was set for September 24, 2025. The incident highlights ongoing ransomware activity targeting healthcare providers in the GCC region, raising concerns over patient privacy, regulatory compliance, and the operational resilience of medical institutions.
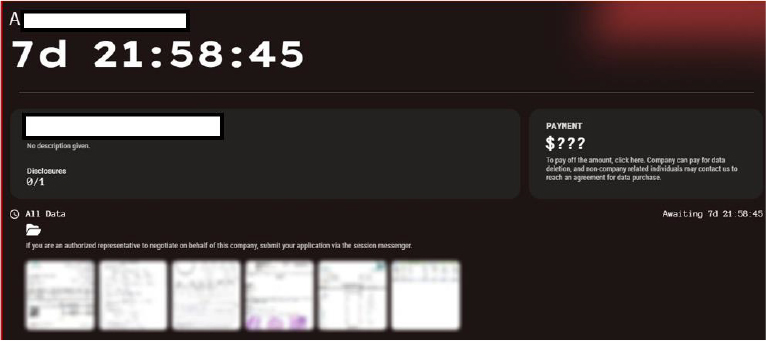
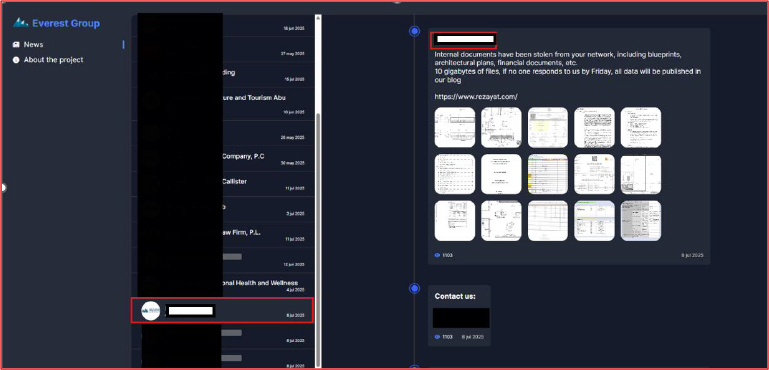
On July 17, 2025, the Everest ransomware group claimed responsibility for breaching a Saudi-based conglomerate involved in engineering, energy, construction, and logistics. The group alleges the theft of 10 GB of internal data, including blueprints, architectural plans, and financial documents. Everest has issued a public extortion threat, warning that if the company fails to make contact by Friday, the stolen data will be fully published on their leak site. The countdown timer and threat indicate active pressure tactics against a critical Saudi enterprise with strategic infrastructure exposure.
On July 3, 2025, the Qilin ransomware group claimed responsibility for a major cyberattack on a multinational retail company with significant operations in Saudi Arabia. The attackers reportedly stole over 3.1 million files totaling 816.8 GB, including sensitive employee and customer data, contracts, source code, and financial records. While Qilin noted the attack is unrelated to a previous Phobos ransomware incident, the breach poses serious risks to Saudi Arabia’s retail sector, including operational disruption, and data privacy concerns under the Kingdom’s Personal Data Protection Law (PDPL).
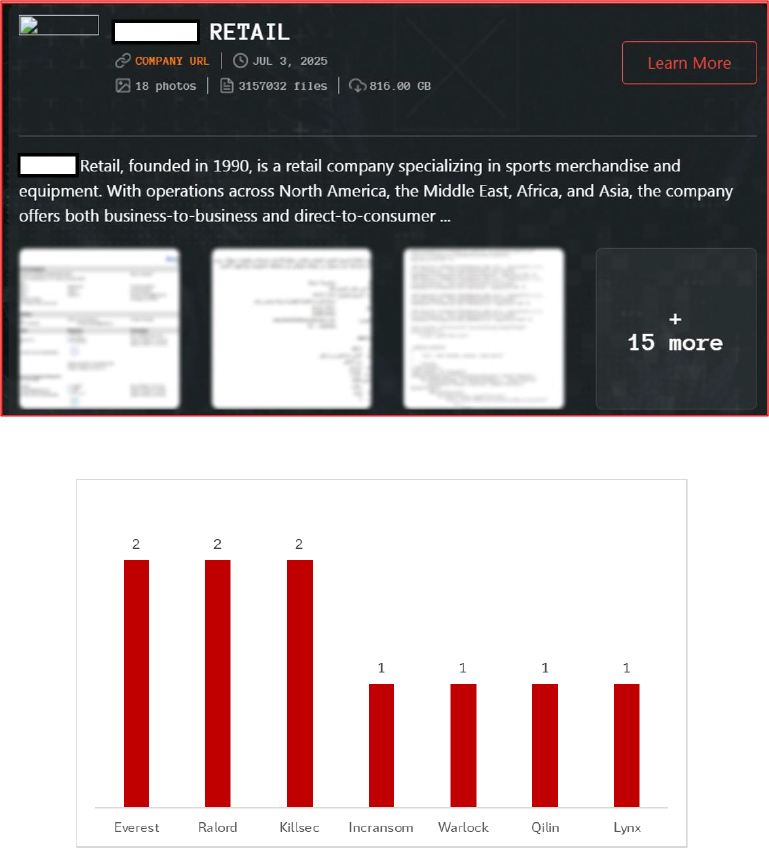
In 2025, ransomware activity across Saudi Arabia was largely dominated by the Everest group, which accounted for the highest volume of attacks, positioning it as the most active ransomware operator of the year. Groups like Ralord and Kilsec also launched significant campaigns, particularly targeting Saudi entities. Additional threat actors—including Incransom, Warlock, Qilin, and Lynx—were less prolific but remained consistent contributors, reflecting a diverse and persistent ransomware ecosystem in the region.
The Saudi Arabia threat landscape in 2025 faced a significant escalation in cyber threats, driven by dark web activity, hacktivism, and targeted ransomware attacks. Critical sectors, including government, healthcare, and finance, were heavily impacted, exposing sensitive data and disrupting operations. The evolving threat landscape highlights the urgent need for enhanced cybersecurity infrastructure, proactive threat intelligence, and robust regulatory compliance to protect national interests and ensure digital resilience amid increasing global and regional cyber risks.
Strengthen Cybersecurity Infrastructure
Enhance Threat Intelligence and Monitoring
Improve Data Protection and Regulatory Compliance
Employee Awareness and Training