

Hafnium is a Chinese state-sponsored advanced persistent threat (APT) group, also referred to as Silk Typhoon, and is known for sophisticated cyber espionage targeting critical sectors worldwide. The group operates under the sponsorship of China’s Ministry of State Security (MSS) and utilizes both advanced attack techniques and layered relationships with contracted technology firms for operational support.
Alias:
MURKY PANDA, Silk Typhoon
Motivation:
Espionage
Target Technologies:
Microsoft SharePoint, Citrix Netscaler, Cloud Infrastructure, Commvault Web Server, Office Suites Software, Operating System, Web Application.
Tools Used:
Covenant, Impacket, PsExec, Nishang, PowerCat, Archive Utilities, China Chopper, ASPXSpy.
Malware used by the Hafnium:
Tarrask, PlugX, and Whitebird.
Targeted Countries:
The United States of America, the United Kingdom, Australia, Japan, Vietnam, Cañada, and Mexico.
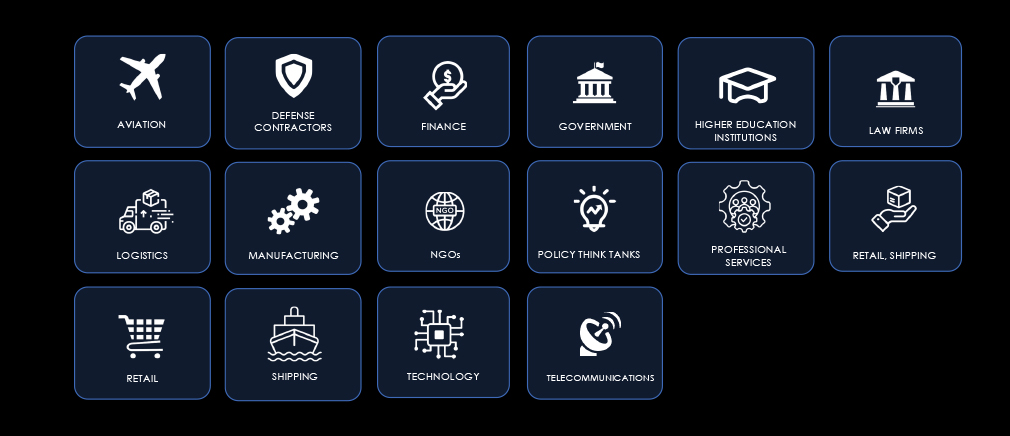
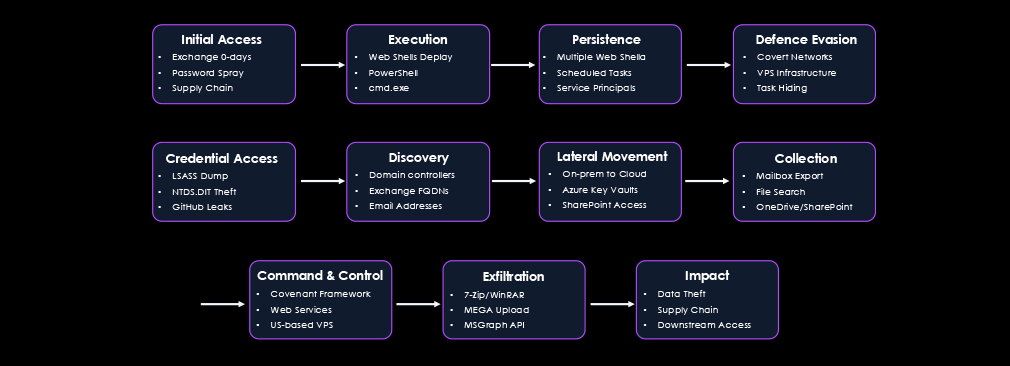
Recent Campaign Highlights
Trends and Tactics
Sector Focus
| Tactic | ID | Technique |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1592.004 | Gather Victim Host Information: Client Configurations |
| Reconnaissance | T1590 | Gather Victim Network Information |
| Reconnaissance | T1590.005 | Gather Victim Network Information: IP Addresses |
| Reconnaissance | T1593.003 | Search Open Websites/Domains: Code Repositories |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1583.005 | Acquire Infrastructure: Botnet |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1584.005 | Compromise Infrastructure: Botnet |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Persistence | T1136.002 | Create Account: Domain Account |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1078.003 | Valid Accounts: Local Accounts |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078.003 | Valid Accounts: Local Accounts |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1078.003 | Valid Accounts: Local Accounts |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Defense Evasion | T1078.003 | Valid Accounts: Local Accounts |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1555.006 | Credentials from Password Stores: Cloud Secrets Management Stores |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1016.001 | System Network Configuration Discovery: Internet Connection Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1119 | Automated Collection |
| Collection | T1530 | Data from Cloud Storage |
| Collection | T1213.002 | Data from Information Repositories: SharePoint |
| Collection | T1005 | Data from Local System |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |