Published On : 2025-10-03
Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type:
Ransomware
Target Technologies:
Windows, Linux.
Target Geographies:
China, United States, Taiwan, Brazil, Turkey.
Target Industries:
Manufacturing, Consumer Services, Software/IT, Finance, Government.
Introduction:
CYFIRMA Research and Advisory Team has found LOCKBIT 5.0 Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
LOCKBIT 5.0 Ransomware:
Researchers have discovered a new ransomware strain called LOCKBIT 5.0. This ransomware Encrypts victims’ files, renaming them appends a random extension to filenames (e.g., “.db9785905a3cad2c”), and creates a ransom note (“ReadMeForDecrypt.txt”)

Source: Surface Web
The ransom note states the victim has been attacked and must pay, or stolen data will be leaked via a Tor site. It warns against contacting law enforcement, modifying encrypted files, or revealing the ransom purpose when buying cryptocurrency. Instructions are given for using Tor, brokers, and cold wallets, while the attackers claim their “reputation” ensures payment leads to decryption. Technically, LockBit 5.0 features a cleaner affiliate interface, customizable encryption options, and randomized 16-character file extensions without markers, complicating recovery. It disables Windows Event Tracing via EtwEventWrite patching, avoids execution in Russian environments, and includes Linux and ESXi variants the latter enabling mass encryption of virtual machines on VMware hosts.
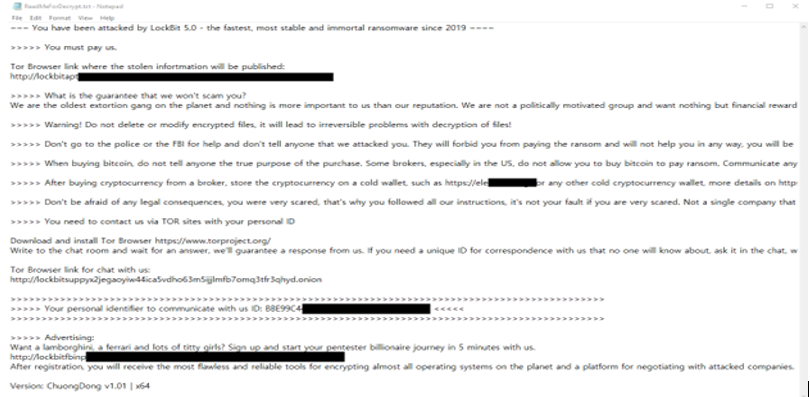
The appearance of LOCKBIT 5.0 ‘s ransom note (“ReadMeForDecrypt.TXT “) (Source: Surface Web)
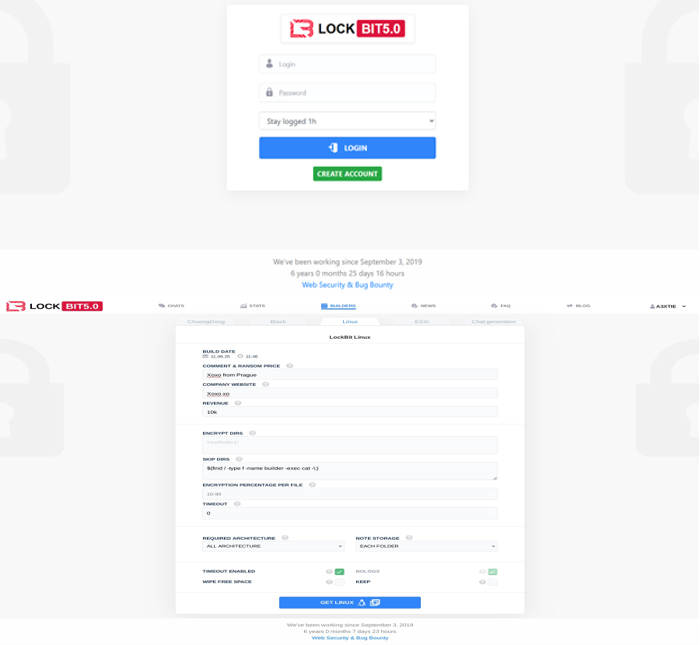
LockBit’s 5.0 builder panel
Following are the TTPs based on the MITRE Attack Framework.
| Tactic |
Technique ID |
Technique Name |
| Initial Access |
T1091 |
Replication Through Removable Media |
| Privilege Escalation |
T1055 |
Process Injection |
| Privilege Escalation |
T1055.012 |
Process Injection: Process Hollowing |
| Privilege Escalation |
T1548 |
Abuse Elevation Control Mechanism |
| Defense Evasion |
T1027 |
Obfuscated Files or Information |
| Defense Evasion |
T1027.002 |
Obfuscated Files or Information: Software Packing |
| Defense Evasion |
T1036 |
Masquerading |
| Defense Evasion |
T1055 |
Process Injection |
| Defense Evasion |
T1055.012 |
Process Injection: Process Hollowing |
| Defense Evasion |
T1070 |
Indicator Removal |
| Defense Evasion |
T1070.004 |
Indicator Removal: File Deletion |
| Defense Evasion |
T1497 |
Virtualization/Sandbox Evasion |
| Defense Evasion |
T1497.003 |
Virtualization/Sandbox Evasion: Time Based Evasion |
| Defense Evasion |
T1548 |
Abuse Elevation Control Mechanism |
| Defense Evasion |
T1562 |
Impair Defenses |
| Defense Evasion |
T1562.001 |
Impair Defenses: Disable or Modify Tools |
| Defense Evasion |
T1564 |
Hide Artifacts |
| Defense Evasion |
T1564.003 |
Hide Artifacts: Hidden Window |
| Defense Evasion |
T1564.004 |
Hide Artifacts: NTFS File Attributes |
| Defense Evasion |
T1622 |
Debugger Evasion |
| Credential Access |
T1003 |
OS Credential Dumping |
| Credential Access |
T1552 |
Unsecured Credentials |
| Credential Access |
T1552.001 |
Unsecured Credentials: Credentials In Files |
| Discovery |
T1057 |
Process Discovery |
| Discovery |
T1082 |
System Information Discovery |
| Discovery |
T1083 |
File and Directory Discovery |
| Discovery |
T1120 |
Peripheral Device Discovery |
| Discovery |
T1497 |
Virtualization/Sandbox Evasion |
| Discovery |
T1497.003 |
Virtualization/Sandbox Evasion: Time Based Evasion |
| Discovery |
T1518 |
Software Discovery |
| Discovery |
T1518.001 |
Software Discovery: Security Software Discovery |
| Discovery |
T1622 |
Debugger Evasion |
| Lateral Movement |
T1091 |
Replication Through Removable Media |
| Collection |
T1005 |
Data from Local System |
| Collection |
T1114 |
Email Collection |
| Collection |
T1119 |
Automated Collection |
| Command and Control |
T1071 |
Application Layer Protocol |
| Command and Control |
T1090 |
Proxy |
| Impact |
T1485 |
Data Destruction |
Relevancy and Insights:
- The ransomware primarily targets Windows OS, which is utilised by enterprise in a variety of industries.
- USB Bus Checks: The ransomware is actively monitoring and checking the USB bus for connected devices. This behaviour suggests that the ransomware may be attempting to propagate itself by spreading through removable media, such as USB drives. It could be searching for specific files or vulnerabilities on connected devices to further spread its malicious payload.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. This technique is used by the ransomware to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- Persistence: The ransomware exhibits persistence mechanisms to ensure its survival and ongoing malicious activities within the compromised environment. This could involve creating autostart entries or modifying system settings to maintain a foothold and facilitate future attacks.
ETLM Assessment:
CYFIRMA’s assessment indicates that the LOCKBIT 5.0 ransomware group is a direct evolution of prior LockBit variants, demonstrating clear indicators of rapid refinement and expanded capabilities. Evidence from observed artifacts (randomized 16-character file extensions, ReadMeForDecrypt.txt ransom note), confirmed IOCs, and TTPs such as EtwEventWrite API patching to disable Windows Event Tracing, geolocation/locale checks, and mass encryption of ESXi virtualized environments strongly support this trajectory. With these capabilities already operational, it is highly likely LOCKBIT 5.0 will expand into double- or triple-extortion, adopt dedicated leak sites, and further mature into a Ransomware-as-a-Service ecosystem positioning it as a scalable, persistent global threat.
Sigma Rule
title: System File Execution Location Anomaly
tags:
– attack.defense-evasion
– attack.t1036
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith:
– ‘\atbroker.exe’
– ‘\audiodg.exe’
– ‘\bcdedit.exe’
– ‘\bitsadmin.exe’
– ‘\certreq.exe’
– ‘\certutil.exe’
– ‘\cmstp.exe’
– ‘\conhost.exe’
– ‘\consent.exe’
– ‘\cscript.exe’
– ‘\csrss.exe’
– ‘\dashost.exe’
– ‘\defrag.exe’
– ‘\dfrgui.exe’ # Was seen used by Lazarus Group – https://asec.ahnlab.com/en/39828/
– ‘\dism.exe’
– ‘\dllhost.exe’
– ‘\dllhst3g.exe’
– ‘\dwm.exe’
– ‘\eventvwr.exe’
– ‘\logonui.exe’
– ‘\LsaIso.exe’
– ‘\lsass.exe’
– ‘\lsm.exe’
– ‘\msiexec.exe’
– ‘\ntoskrnl.exe’
– ‘\powershell_ise.exe’
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\regsvr32.exe’
– ‘\rundll32.exe’
– ‘\runonce.exe’
– ‘\RuntimeBroker.exe’
– ‘\schtasks.exe’
– ‘\services.exe’
– ‘\sihost.exe’
– ‘\smartscreen.exe’
– ‘\smss.exe’
– ‘\spoolsv.exe’
– ‘\svchost.exe’
– ‘\taskhost.exe’
– ‘\taskhostw.exe’
– ‘\Taskmgr.exe’
– ‘\userinit.exe’
– ‘\wininit.exe’
– ‘\winlogon.exe’
– ‘\winver.exe’
– ‘\wlanext.exe’
– ‘\wscript.exe’
– ‘\wsl.exe’
– ‘\wsmprovhost.exe’ # Was seen used by Lazarus Group – https://asec.ahnlab.com/en/39828/
filter_main_generic:
Image|startswith:
– ‘C:\$WINDOWS.~BT\’
– ‘C:\$WinREAgent\’
– ‘C:\Windows\SoftwareDistribution\’
– ‘C:\Windows\System32\’
– ‘C:\Windows\SystemTemp\’
– ‘C:\Windows\SysWOW64\’
– ‘C:\Windows\uus\’
– ‘C:\Windows\WinSxS\’
filter_optional_system32:
Image|contains: ‘\SystemRoot\System32\’
filter_main_powershell:
Image:
– ‘C:\Program Files\PowerShell\7\pwsh.exe’
– ‘C:\Program Files\PowerShell\7-preview\pwsh.exe’
filter_main_wsl_windowsapps:
Image|startswith:’C:\Program Files\WindowsApps\MicrosoftCorporationII.WindowsSubsystemForLinux’
Image|endswith: ‘\wsl.exe’
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Unknown
level: high
(Source: Surface Web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise control of your security systems
STRATEGIC RECOMMENDATION
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATION
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATION
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rules for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week
Type: Information Stealer
Objective: Data Theft, Data Exfiltration
Target Technologies: Windows OS, Web Browsers, Email and FTP Clients, VPN
Target Industry: Manufacturing
Active Malware of the Week
This week “DarkCloud” is trending.
Overview of DarkCloud Malware
Researchers identified a spear-phishing campaign targeting customers in the manufacturing sector, in which a financial-themed email sent to their Zendesk support address attempted to deliver DarkCloud, an information-stealing malware. DarkCloud is being promoted via a website and on Telegram, presenting itself as legitimate software while actually advertising malicious capabilities. Originally circulated on underground forums, DarkCloud has evolved with updates that enhance stealth and data theft, targeting applications such as web browsers, email and FTP clients, and VPN software. The malware can capture sensitive information, including browser credentials, keystrokes, files, email data, clipboard contents, and cryptocurrency wallets, which are then exfiltrated to attacker-controlled channels, such as Telegram, FTP, email, or web panels.
Technical Analysis
Initially, the malware was distributed through a phishing email that used a convincing banking-themed notice and carried a ZIP attachment labeled as a Swift message; the archive unpacked an executable that turned out to be an older DarkCloud build. The campaign used a realistic financial pretext to trick support channels, and the sample in this case matched a prior release of the malware. Notably, the DarkCloud builder requires the legacy Visual Basic 6 IDE to compile its payload locally; an unusual design choice has historically opened the door to unauthorized copies and “forks” of the tool, increasing the chance the code will spread and be misused by a wider set of actors.
Functionally, DarkCloud is an all-purpose data harvester. It is designed to quietly collect a wide range of sensitive material — from browser-stored credentials, cookies, and keystrokes to email contacts, documents, and clipboard content — and it specifically seeks cryptocurrency wallet data and other financial artifacts. The malware uses a VBScript object to regex-match stolen credit card numbers and tag each card by type (for example, Amex). It also includes a generic file-collection feature that sweeps common user folders and document types, expanding its reach beyond simple credential theft.
To avoid detection and analysis, DarkCloud runs a series of environment checks before it proceeds. It scans for common analysis tools and processes typically used by security researchers, checks system resources and disk size to detect lightweight sandboxes, and probes for virtualization drivers and platform models associated with common VM solutions. If those checks raise alarms, the malware may exit quietly rather than reveal its behavior. It can also register itself for persistence using RunOnce-style registry entries, so it will reappear after a reboot.
Finally, exfiltration is flexible and configurable: Operators can configure exfiltration over multiple channels — email (including encrypted SMTP), Telegram, FTP, or web-based control panels — and captured data is packaged in structured formats so it can be easily consumed by the operator. Taken together, these traits make DarkCloud a practical, adaptable threat that is likely to keep appearing in targeted financial and support-channel campaigns as copies and new variants proliferate.
Following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic |
Technique ID |
Technique Name |
| Initial Access |
T1566.001 |
Phishing: Spear phishing Attachment |
| Execution |
T1106 |
Native API |
| Execution |
T1129 |
Shared Modules |
| Privilege Escalation |
T1055 |
Process Injection |
| Defense Evasion |
T1027.002 |
Obfuscated Files or Information: Software Packing |
| Defense Evasion |
T1055 |
Process Injection |
| Defense Evasion |
T1070.006 |
Indicator Removal: Timestomp |
| Defense Evasion |
T1497 |
Virtualization/Sandbox Evasion |
| Defense Evasion |
T1562.001 |
Impair Defenses: Disable or Modify Tools |
| Credential Access |
T1003 |
OS Credential Dumping |
| Credential Access |
T1552.001 |
Unsecured Credentials: Credentials in Files |
| Credential Access |
T1555 |
Credentials from Password Stores |
| Credential Access |
T1555.003 |
Credentials from Password Stores: Credentials from Web Browsers |
| Discovery |
T1082 |
System Information Discovery |
| Discovery |
T1497 |
Virtualization/Sandbox Evasion |
| Collection |
T1005 |
Data from Local System |
| Collection |
T1114 |
Email Collection |
| Command and Control |
T1071 |
Application Layer Protocol |
INSIGHTS
- DarkCloud exemplifies how malware is evolving from one-off attacks into organized, commercialized offerings. It is openly promoted through Telegram and websites. This approach makes it easier for low-skilled operators to access sophisticated tools without building them from scratch. Updates, features, and even user guidance resemble professional software development cycles. The commercialization of malware also encourages the creation of multiple versions or editions to attract different buyers. Overall, it reflects a structured underground economy where cybercrime operates much like a traditional business.
- The malware’s modular design and local compilation process allow multiple operators to create variants from the same base tool. These forks may use different lures, payloads, or delivery methods, creating the illusion of separate campaigns. This diversity complicates attribution, as investigators can see multiple superficially unrelated attacks that trace back to the same toolkit. The ability to adapt quickly also ensures that defensive measures may be bypassed repeatedly. In effect, DarkCloud acts as a shared platform in the underground ecosystem, providing flexibility to its operators. It highlights the challenges in tracking and analyzing modern malware operations.
- DarkCloud’s capabilities go beyond simple credential theft, impacting organizational operations and incident response. The variety of data it can harvest — from passwords to documents and financial artifacts — increases the complexity of triage. Each exfiltration channel introduces new reporting and coordination challenges. Even small breaches can become resource-intensive because the toolkit affects multiple departments simultaneously. This broad impact demonstrates how modern malware influences both technical and organizational processes.
ETLM ASSESSMENT
- From the ETLM perspective, CYFIRMA anticipates that malware like DarkCloud is likely to blur the lines between everyday digital activity and cybercrime, as its adaptability allows it to be repurposed for a variety of malicious goals. Individuals may see a rise in personal data misuse, from financial fraud to identity theft, as stolen information circulates more freely across underground markets. Communities could also feel the effects indirectly, with disruptions in customer support systems, financial services, and online platforms that rely on trust and reliability. As more variants emerge, people might notice an increase in convincing scams and fraudulent messages that exploit both personal and institutional vulnerabilities. Even small-scale breaches may ripple outward, affecting not just direct victims but also wider networks of contacts and service providers. Over time, this could normalize digital uncertainty, where users approach online interactions with heightened suspicion, reshaping how trust is managed in everyday digital life.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule DarkCloud_Indicators
{
meta:
description = “Detects DarkCloud malware indicators”
author = “CYFIRMA”
malware_family = “DarkCloud”
strings:
// SHA256 File Hashes
$sha256_1 = “e013fb82188cb7ea231183197e12c189b4637e7d92e277793d607405e16da1e2”
$sha256_2 = “6a3b4e62a8262a0bf527ad8ea27eb19a0fcb48a76d6fc2868785362e40491432”
// Domains
$domain_1 = “mail.apexpharmabd.com”
condition:
any of ($sha256*) or
any of ($domain*)
}
STRATEGIC RECOMMENDATION
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audits of workstations, servers, laptops, and mobile devices to identify unauthorized/ restricted software.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Configure the organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATION
- Incorporate a written software policy that educates employees on good practices in relation to software and the potential implications of downloading and using restricted software.
- Security Awareness training should be mandated for all company employees. The training should ensure that employees:
- Avoid downloading and executing files from unverified sources.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
TACTICAL RECOMMENDATION
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Exert caution when opening email attachments or clicking on embedded links supplied via email communications.
- Add the Yara rules for threat detection and monitoring, which will help to detect anomalies in log events and identify and monitor suspicious activities.
Weekly Intelligence Trends/Advisory
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks,Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Killsec Ransomware, Qilin Ransomware | Malware – DarkCloud
- Killsec Ransomware – One of the ransomware groups.
- Qilin Ransomware – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Behaviour –Most of these malware use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
2. Threat Actor in Focus
Inside the Threat: ShinyHunters collaboration LAPSUS$ and Scattered Spider
- Threat Actor: ShinyHunters collaboration with LAPSUS$ and Scattered Spider
- Attack Type: Connection Proxy, Credential Dumping, Living of the land, Ransomware Attacks, Social Engineering Attack, Exploitation of Vulnerabilities
- Objective: Information theft, Financial Gains
- Suspected Target Technology: SAP, Office Suites Software, Operating System, Web Application
- Suspected Target Geography: US, Germany, India, Australia
- Suspected Target Industries: Airline, Automotives, Diversified Financials, E-Commerce, IT Services, Retail, Software, telecommunications
- Business Impact: Financial Loss, Data Theft, Operational Disruption, Reputational Damage
About the Threat Actor
- ShinyHunters is a criminal black-hat hacker group active since at least 2020, known for executing large-scale data breaches targeting major corporations and online services. The group exfiltrates sensitive data, including user credentials and corporate information, which is then sold or leaked on dark web forums. Since emerging, ShinyHunters has gained notoriety for its bold tactics and high-impact operations. Recent intelligence suggests a possible collaboration between ShinyHunters, LAPSUS$, and Scattered Spider—three highly sophisticated threat actors—creating an adaptive cybercrime ecosystem. This alliance represents a growing advanced persistent threat (APT) to enterprises worldwide, combining social engineering, extortion, and persistent access techniques.
Details on Exploited Vulnerabilities
| CVE ID |
Affected Products |
CVSS Score |
Exploit Links |
| CVE-2025-31324 |
SAP |
9.8 |
———– |
| CVE-2024-6387 |
OpenSSH’s server |
8.1 |
link1, link2 |
TTPs based on MITRE ATT&CK Framework
| Tactic |
ID |
Technique |
| Initial Access |
T1566.004 |
Phishing: Spearphishing Voice |
| Execution |
T1204.002 |
User Execution: Malicious File |
| Execution |
T1059 |
Command and Scripting Interpreter |
| Persistence |
T1098 |
Account Manipulation |
| Persistence |
T1078 |
Valid Accounts |
| Persistence |
T1556.006 |
Modify Authentication Process: Multi-Factor Authentication |
| Privilege Escalation |
T1098 |
Account Manipulation |
| Defense Evasion |
T1027.009 |
Obfuscated Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion |
T1578 |
Modify Cloud Compute Infrastructure |
| Credential Access |
T1555 |
Credentials from Password Stores |
| Discovery |
T1082 |
System Information Discovery |
| Discovery |
T1083 |
File and Directory Discovery |
| Discovery |
T1087 |
Account Discovery |
| Collection |
T1005 |
Data from Local System |
| Exfiltration |
T1030 |
Data Transfer Size Limits |
| Exfiltration |
T1020 |
Automated Exfiltration |
| Command and Control |
T1071 |
Application Layer Protocol |
| Impact |
T1657 |
Financial Theft |
Latest Developments Observed
The threat actor is suspected of compromising the Salesloft platform to obtain OAuth and refresh tokens from its Drift chat agent integration with Salesforce, enabling lateral movement into customer environments and subsequent data exfiltration. The campaign appears primarily focused on credential theft, with particular emphasis on sensitive assets such as AWS access keys, passwords, and Snowflake access tokens. This theft of Salesloft tokens coincides with a broader wave of Salesforce-related data breaches attributed to the ShinyHunters group, which has also been linked to potential overlaps with the threat actor known as Scattered Spider.
ETLM Insights
ShinyHunters, a highly adaptive cyber threat group with established ties to LAPSUS$ and Scattered Spider, continues to represent a sophisticated Advanced Persistent Threat (APT) to global enterprises.
Recent intelligence highlights notable connections, tactical overlaps, and direct collaboration among these groups. Indicators of this alignment include shared TTPs, overlapping memberships, joint public communication channels, and coordinated attacks against high-profile organizations.
Of particular concern is their collaboration around coordinated threat campaigns, staged data leak disclosures, and the promotion of a new Ransomware-as-a-Service (RaaS) platform, branded as shinysp1d3r.
YARA Rules
rule ShinyHunters_CVE_Domain_Indicators
{
meta:
author = “CYFIRMA”
date = “2025-09-30”
description = “Detects presence of CVE-2025-31324, CVE-2024-6387, and domains havenly.com or promo.com”
tags = “shinyhunters, cve, domain, indicator”
strings:
$cve1 = “CVE-2025-31324”
$cve2 = “CVE-2024-6387”
$domain1 = “havenly.com”
$domain2 = “promo.com”
condition:
any of ($cve*, $domain*)
}
Recommendations
Strategic Recommendations
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Deploy Zero Trust Policy that leverages tools like security information management, advanced security analytics platforms, security user behaviour analytics, and other analytics systems to help the organization’s security personnel observe in real-time what is happening within their networks so they can orient defences more intelligently.
- Block exploit-like behaviour. Monitor endpoints memory to find behavioural patterns that are typically exploited, including unusual process handle requests. These patterns are features of most exploits, whether known or new. This will be able to provide effective protection against zero-day/critical exploits and more, by identifying such patterns.
Management Recommendations
- Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyze conversation history to detect anomalies, as well as computer vision to analyze suspect links within emails.
- Invest in user education and implement standard operating procedures for the handling of financial and sensitive data transactions commonly targeted by impersonation attacks. Reinforce this training with context-aware banners and in-line prompts to help educate users.
- Develop a cyber threat remediation program and encourage employee training to detect anomalies proactively.
Tactical Recommendations
- For better protection coverage against email attacks (like spear phishing, business email compromise, or credential phishing attacks), organizations should augment built-in email security with layers that take a materially different approach to threat detection.
- Protect accounts with multi-factor authentication. Exert caution when opening email attachments or clicking on embedded links supplied via email communications, SMS, or messaging.
- Apply security measures to detect unauthorized activities, protect sensitive production, and process control systems from cyberattacks.
- Add the YARA rule for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
3. Major Geopolitical Developments in Cybersecurity
Chinese hackers are breaching global critical infrastructure
- RedNovember, a Chinese state-sponsored threat group, conducted a global cyber-espionage campaign between June 2024 and July 2025. Throughout this period, the group targeted defense contractors, government agencies, and private corporations by rapidly exploiting vulnerabilities in VPN appliances and firewall devices—often faster than patches could be deployed. Researchers confirmed successful intrusions into at least two U.S. defense contractors, more than thirty government agencies in Panama, and various organizations across Europe, Asia, and South America. The affected entities included aerospace manufacturers, law firms, and other high-value targets, underscoring the campaign’s strategic focus on sensitive and confidential information.
ETLM Assessment:
- This APT group has repeatedly demonstrated a high level of technical proficiency and operational speed, particularly in its ability to identify and weaponize zero-day vulnerabilities in widely used network infrastructure before security patches are available. Their targeting of VPNs and firewalls suggests a focus on gaining persistent access to internal networks without detection. RedNovember appears to operate with clear geopolitical intent, selecting targets that align with China’s strategic interests—such as defense innovation, legal intelligence, and foreign government operations. The campaign also reveals the group’s global reach and adaptability, successfully compromising entities in diverse regions and industries. This level of coordination and breadth of impact indicates that RedNovember is likely a well-resourced unit within China’s broader cyber apparatus, capable of sustained, covert operations over long periods.
Iranian hackers targeting Western Europe
- Researchers have released a report detailing an Iranian cyber-espionage campaign targeting defense, telecommunications, and aviation sectors in Western Europe—specifically in Denmark, Sweden, and Portugal. The threat actor, identified as Nimbus Manticore (also known as UNC1549 or Smoke Sandstorm), is posing as HR recruiters to deliver spearphishing emails aimed at job seekers. These emails redirect recipients to phishing websites that deploy a new version of the Minibike malware, which researchers have dubbed “MiniJunk.” According to the report, this latest variant demonstrates a notable advancement in the actor’s capabilities, including the use of a previously undocumented technique that manipulates process execution parameters to load DLLs from alternate paths.
ETLM Assessment:
- This campaign highlights a growing sophistication in Iranian cyber operations, particularly those attributed to advanced persistent threat (APT) groups like Nimbus Manticore. Known for targeting critical infrastructure and high-value sectors, Nimbus Manticore has previously been linked to cyber-espionage activities aligned with Iran’s strategic interests. The group’s use of social engineering—disguising themselves as recruiters to exploit job seekers—is a calculated method to bypass traditional security defenses and gain initial access to targeted systems. The deployment of the newly evolved “MiniJunk” malware indicates ongoing development and investment in custom tooling, enabling stealthier and more flexible operations. The use of novel techniques, such as loading DLLs from alternate paths, suggests a deeper understanding of Windows internals and an effort to evade detection mechanisms. This attack not only signals a continued focus on European targets but also underscores the need for increased vigilance against APTs leveraging social engineering and advanced malware to infiltrate sensitive sectors.
4. Rise in Malware/Ransomware and Phishing
The Killsec Ransomware Impacts Allure Clinics
- Attack Type: Ransomware
- Target Industry: Healthcare
- Target Geography: Saudi Arabia
- Ransomware: Killsec Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
- From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia, Allure Clinics (https[:]//www[.]allureclinics[.]com/), was compromised by Killsec Ransomware. Allure Clinics is a major provider of cosmetic and aesthetic medical services headquartered in Riyadh, Saudi Arabia. The clinic is recognized for its comprehensive range of advanced treatments in dermatology, laser therapy, hair restoration, non-surgical cosmetic procedures, and wellness, all delivered by a team of highly qualified Saudi consultants. The compromised data consists of service invoices, patient personal details, medical histories, diagnoses, treatment plans, laboratory reports, test results, prescription and medication records, along with other highly sensitive information.
The following screenshot was observed published on the dark web:
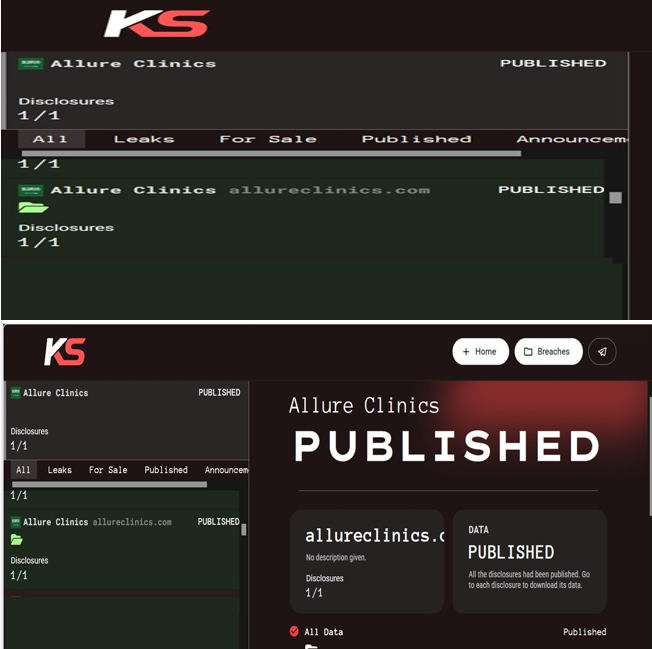
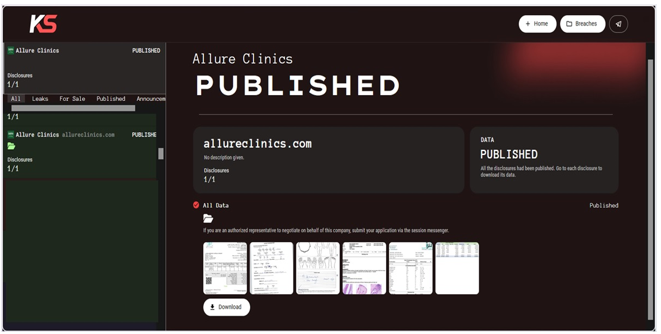
Source: Darkweb
Relevancy & Insights:
- KillSec is a ransomware group that has gained notoriety for its ransomware-as-a-service (RaaS) model and a series of high-profile attacks.
- KillSec Ransomware employs various sophisticated methods to infiltrate systems, including phishing attacks, exploiting known vulnerabilities, and using custom malware to maintain persistence within compromised networks.
- The KillSec Ransomware group primarily targets countries like the United States of America, India, Australia, Brazil, and Mexico.
- The KillSec Ransomware group primarily targets industries, such as Information Technology, Healthcare, Professional Goods & Services, Finance, and Real Estate & Construction.
- Based on the KillSec Ransomware victims list from 1st Jan 2025 to 01 st October 2025, the top 5 Target Countries are as follows:
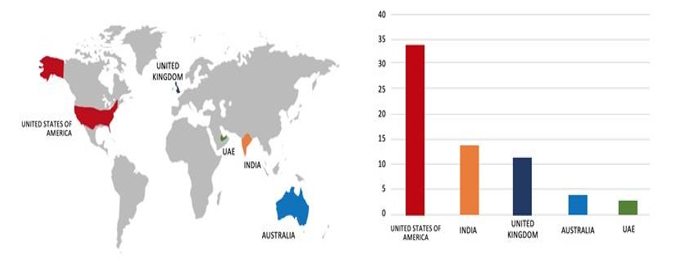
- The Top 10 Industries most affected by the KillSec Ransomware victims list from 1st Jan 2025 to 01 st October 2025 are as follows:
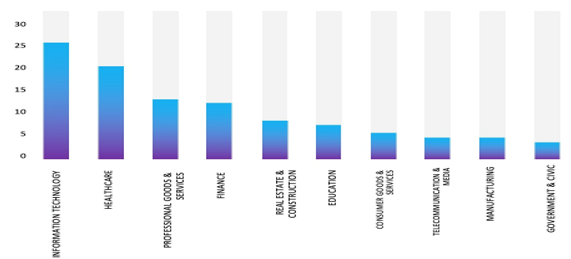
ETLM Assessment:
- The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Qilin Ransomware Impacts Chinup Technology Co., Ltd
- Attack Type: Ransomware
- Target Industry: Industrial Machinery & Equipment Manufacturing
- Target Geography: Taiwan
- Ransomware: Qilin Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan, Chinup Technology Co., Ltd (www[.]chinup[.]com[.]tw) was compromised by Qilin Ransomware. Chinup Technology Co., Ltd specializes in manufacturing Cutting Presses, Die Cutting Machines, Automated Cutting Systems, and Card Processing Machinery. The company expanded its expertise to include solar module manufacturing equipment. The compromised data consists of design drawings of the company’s proprietary technical systems, customer and employee records, as well as the company’s financial information.

Source : Darkweb
Relevancy & Insights:
- The Qilin Ransomware group primarily targets countries such as the United States of America, Canada, South Korea, France, and the United Kingdom.
The Qilin Ransomware group primarily targets industries, including Manufacturing, Professional Goods & Services, Healthcare, Finance, and Information Technology.
Based on the Qilin Ransomware victims list from 1st Jan 2025 to 01st October 2025, the top 5 Target Countries are as follows:
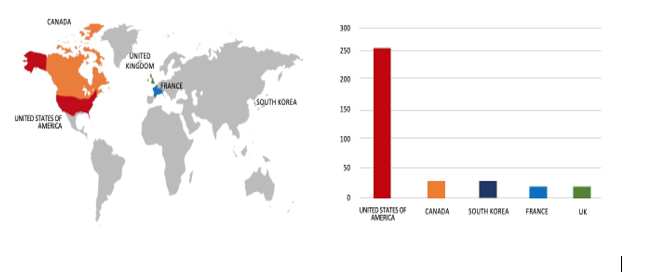
- The Top 10 Industries most affected by the Qilin Ransomware victims list from 1st Jan 2025 to 01st October 2025 are as follows:
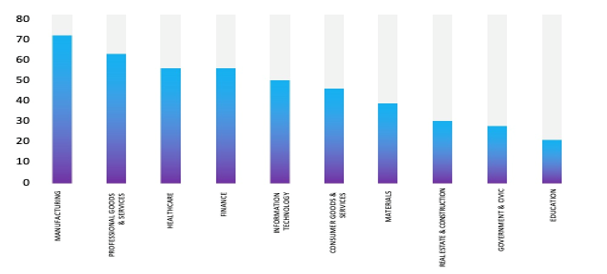
ETLM Assessment:
- According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
5. Vulnerabilities and Exploits
Vulnerability in Libtiff
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Universal components
- Vulnerability: CVE-2025-9900
- CVSS Base Score: 8.8 Source
- Vulnerability Type: Memory corruption
- Summary: The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Relevancy & Insights:
- The vulnerability exists due to a boundary error when processing image files. A remote attacker can create a specially crafted image file, trick the victim into opening it, trigger memory corruption and execute arbitrary code on the target system.
Impact:
- Successful exploitation of this vulnerability may result in complete compromise of vulnerable system.
Affected Products:
https[:]//github[.]com/SexyShoelessGodofWar/LibTiff-4.7.0-Write-What-Where?tab=readme-ov-file
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
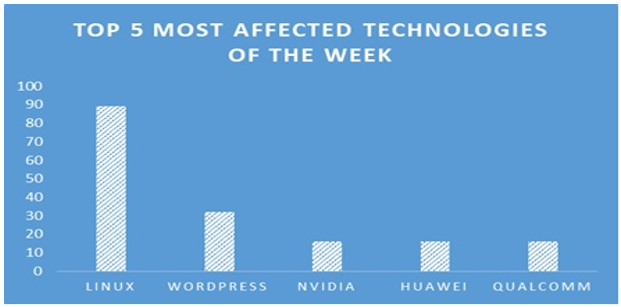
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
- Libtiff is an open-source library for reading and writing Tagged Image File Format (TIFF) files. It provides support for a wide variety of TIFF features, including different compression schemes, color spaces, and image types, and is commonly used in image processing applications and software that requires manipulation of TIFF images.
6. Latest Cyber-Attacks, Incidents, and Breaches
Black Shrantac Ransomware attacked and published the data of Klinglnberg India Pvt Ltd
- Threat Actor: Black Shrantac Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Industrial Machinery & Equipment / Machine Tool Manufacturing
- Target Geography: India
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
- Recently, Black Shrantac Ransomware was observed attacking and publishing the data of Klinglnberg India Pvt Ltd (https[:]//klingelnberg[.]com/) on its dark web website. Klingelnberg India Pvt. Ltd., the Indian subsidiary of the global Klingelnberg Group, is a renowned leader in gear manufacturing and precision measuring technologies. The data leak resulting from the ransomware attack includes financial information such as production costs, bills, invoices, statements, and payrolls; HR data including employee details, contracts, driver’s licenses, and Social Security numbers; comprehensive legal and executive records; and complete product development procedures and R&D results. The total volume of compromised data is estimated to be approximately 2 TB.
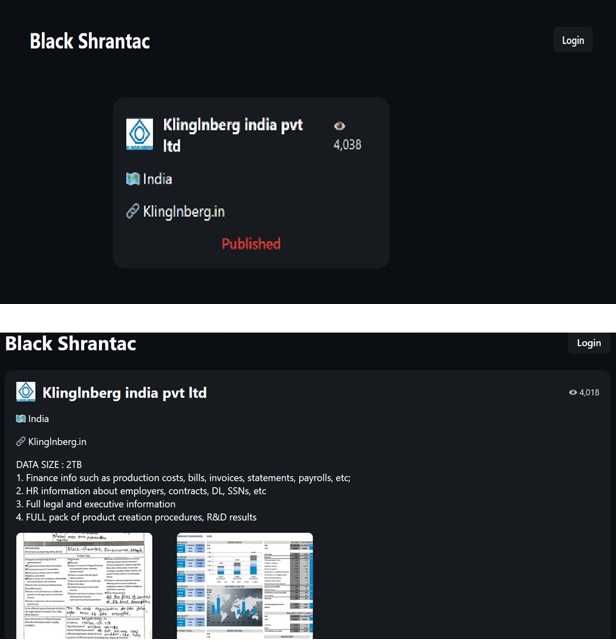
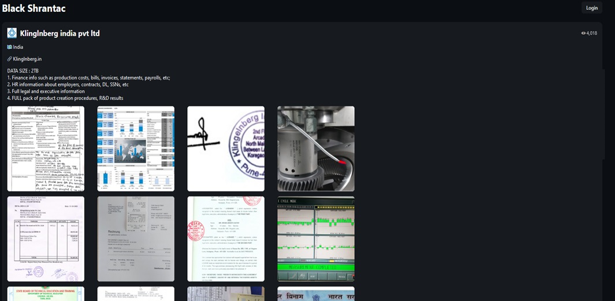
Source: Darkweb
Relevancy & Insights:
- Black Shrantac is a recently identified ransomware group first observed in September 2025, operating primarily as a data broker and extortion outfit. The group targets organizations, exfiltrating sensitive data and leveraging public pressure—often via a dedicated. onion (Tor) site—to coerce ransom payments.
ETLM Assessment:
- According to CYFIRMA’s assessment, Black Shrantac Ransomware exemplifies the latest trend of fast-forming, adaptable data extortion groups that maintain an aggressive web presence to pressure victims using both threat and demonstration of data exposure.
7. Data Leaks
Akulaku’s Data Advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Fintech
- Target Geography: Indonesia, the Philippines, Vietnam, and Malaysia
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed that a threat actor “CLOBELSECTEAM” claims to have breached and leaked the data of Akulaku, a major fintech company operating in Southeast Asia, with a primary focus on Indonesia, the Philippines, Vietnam, and Malaysia. The platform is known for its digital credit services and online shopping installments.
According to the actor, the compromised database contains approximately 32.6 million user records. The allegedly exfiltrated data includes the following information:
- Email addresses
- Phone numbers
- Passwords
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
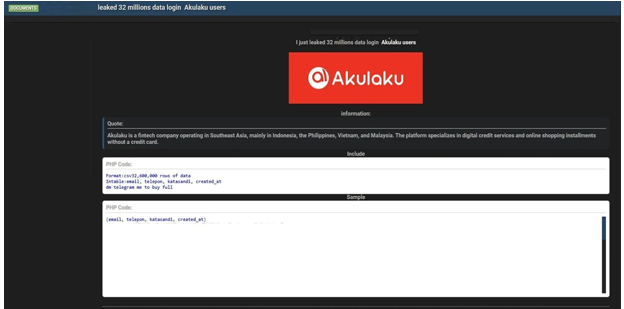
Source: Underground Forums
Singburi Hospital Data Advertised on a Leak Site
- Attack Type: Data leak
- Target Industry: Government
- Target Geography: Thailand
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed that a threat actor “RobotMan” has posted a database for sale, allegedly containing the personnel information from Singburi Hospital. Singburi Hospital is a government hospital in Thailand, operating under the Singburi Provincial Public Health Office, Office of the Permanent Secretary, Ministry of Public Health.
The actor claims the database contains 300,000 records in total.
According to the threat actor, the compromised data includes a wide range of personally identifiable information (PII). The allegedly exfiltrated data fields include:
- Citizen IDs
- Prefixes and full names (first and last)
- Dates of birth
- Father’s names
- Mother’s names
- Home phone numbers
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
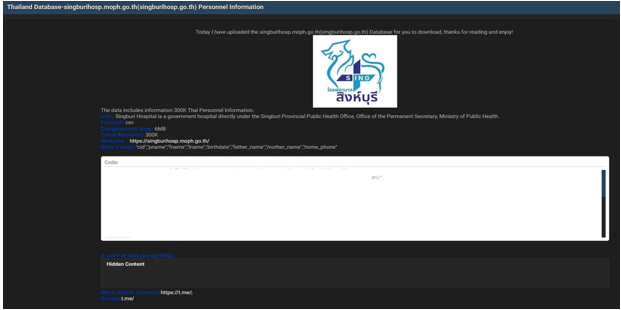
Source: Underground Forums
Relevancy & Insights:
- Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
- The threat actor known as “RobotMan” has recently emerged as a highly active group focused on data leaks. Credible sources link this group to numerous security breaches involving unauthorized access to systems and attempts to sell stolen data on dark web marketplaces. RobotMan’s activities exemplify the evolving and persistent cyber threats originating from underground forums. These incidents highlight the urgent need for organizations to strengthen their cybersecurity defenses with continuous monitoring, advanced threat intelligence, and proactive strategies to safeguard sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by
- Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
- Ensure proper database configuration to mitigate the risk of database-related attacks.
- Establish robust password management policies, incorporating multi-factor authentication and role-based access, to fortify credential security and prevent unauthorized access.
8. Other Observations
The CYFIRMA Research team observed that a threat actor claims to have breached the Land Transportation Office (LTO), a key government agency in the Philippines responsible for all land transportation, including driver licensing and vehicle registration.
The actor, who framed the breach as an act of hacktivism against alleged government corruption, has leaked databases allegedly belonging to the agency.
According to the actor, the compromised data includes a wide range of sensitive information. The allegedly exfiltrated files contain:
- Account details
- Email addresses
- Financial and insurance data
- Login sessions and PIN codes
- Bank transaction records
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
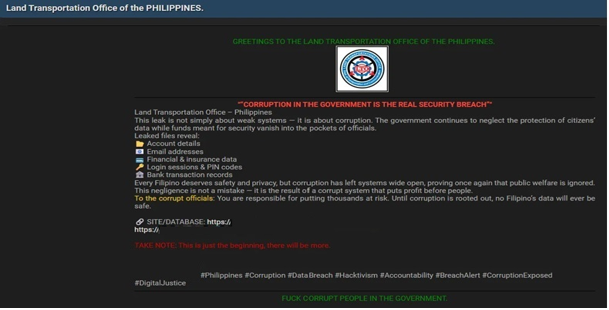
Source: Underground Forums
STRATEGIC RECOMMENDATION
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATION
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and, are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATION
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.




















