


The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the transportation & logistics industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the transportation & logistics industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the transportation & logistics organizations.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes a thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
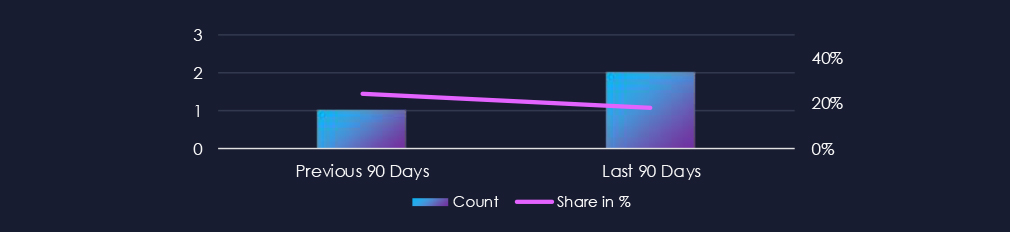
The transportation & logistics industry featured in 5 out of the 14 observed campaigns over the past 90 days, which is a presence in 36% of all campaigns. That is an increase from one previous 90 days, and also in the overall share from 8% (1 out of 12).
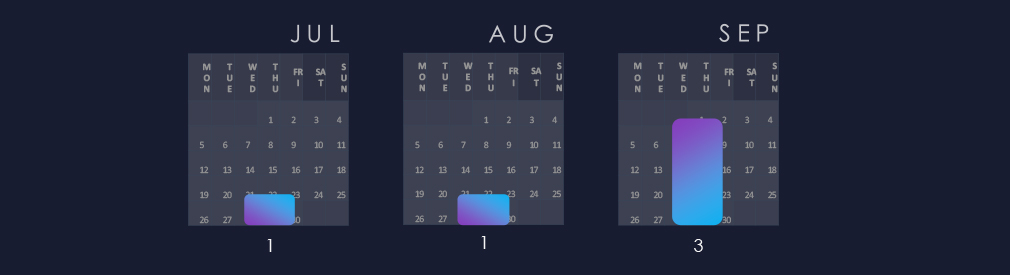
Campaigns were observed across the last 3 months, with a sudden spike during September.
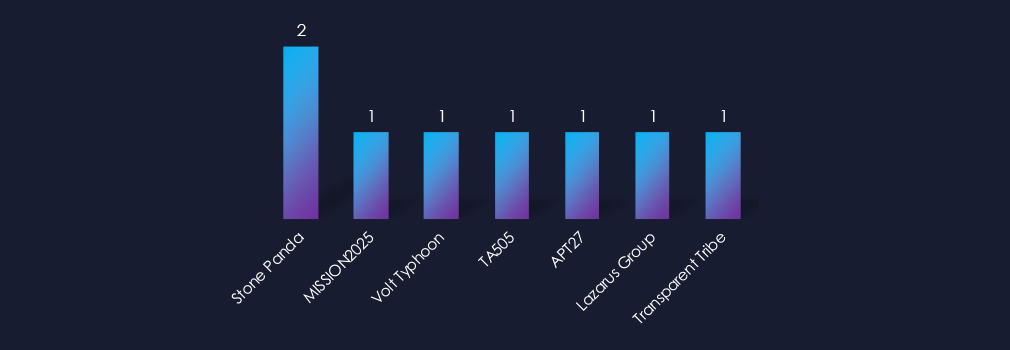
Observed activity involved multiple well-known actors, with campaigns linked to Chinese Stone Panda (2 campaigns), MISSION2025, Volt Typhoon, APT27, Russian TA505, North Korean Lazarus Group, and Pakistani Transparent Tribe.
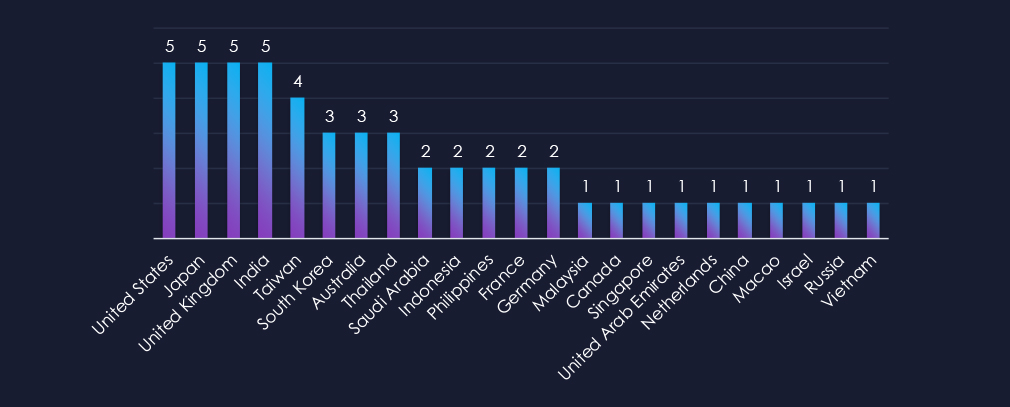
The United States, Japan, the United Kingdom, and India reported victims in all five campaigns. Taiwan reported victims in four campaigns, followed by South Korea, Australia, and Thailand, which reported victims in three campaigns.
Overall, the number of countries indicates a wide reach for relatively few observed campaigns, highlighting the global nature of the transportation & logistics industry.
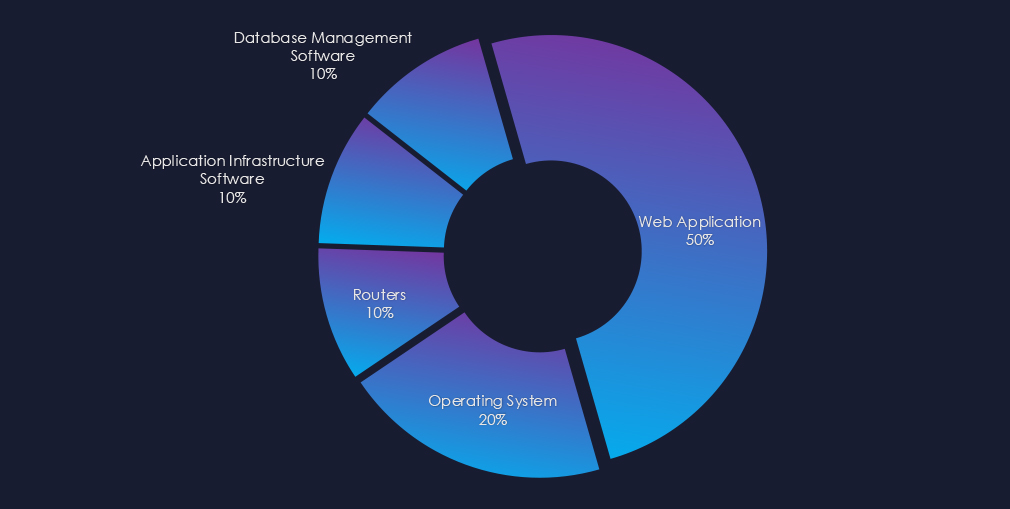
Campaigns targeted mostly web applications and operating systems. Some also used routers, applications, or database software as attack vectors.

Over the past 90 days, the transportation & logistics industry has been significantly impacted by advanced persistent threat (APT) campaigns. 5 out of 14 observed APT campaigns recorded victims in this industry. That is a 36% presence in observed campaigns.
This is an increase from the previous 90-day period, during which 1 campaign targeted this industry.
Monthly Trends
The observed campaigns were active during July and August, with a sudden spike during September.
Key Threat Actors
4 out of 7 identified suspected threat actors were from China, one Russian cybercrime syndicate, the notorious North Korean Lazarus Group, and the Pakistani Transparent tribe were also identified.
Geographical Impact
In total, 23 countries recorded victims in observed campaigns. The US, UK, India, and Japan recorded victims in all 5 campaigns.
Targeted Technologies
Web Applications were the most targeted technology, followed by Operating Systems. Routers, applications, and database software were also attacked.
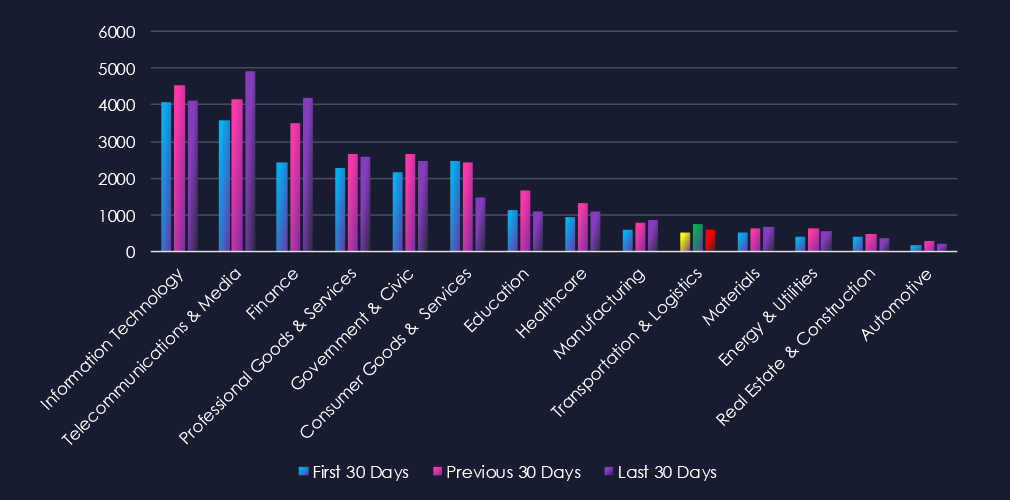
Over the past three months, CYFIRMA’s telemetry has identified 1,876 mentions of the transportation & logistics industry out of a total of 73,374 industry mentions. This is from a total of 300k+ posts across various underground and dark web channels and forums.
The transportation & logistics industry placed 10th out of 14 industries in the last 90 days, with a share of 2.56% of all detected industry-linked chatter.
Below is a breakdown by 30-day periods of all mentions.
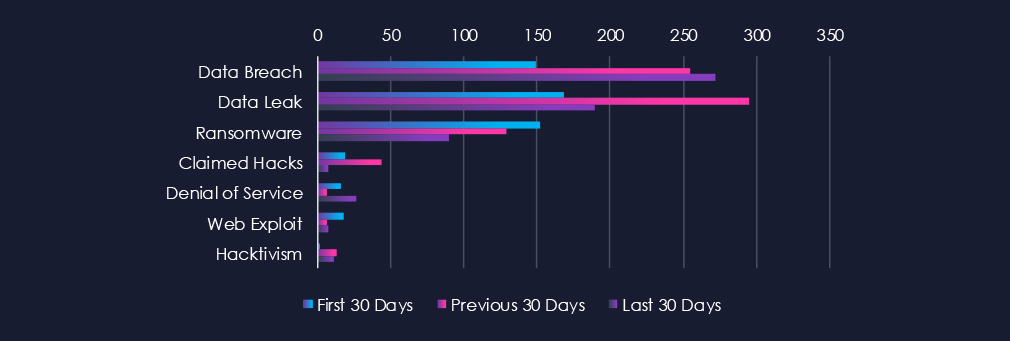
Data Leaks and Data Breaches are the most common category of recorded chatter for this industry. Ransomware chatter declined after early spike.
Remarkably recent European airports incident shows itself only in the minor Denial of Service chatter category, but shows no major chatter spike in overall numbers.

In total, the transportation & logistics industry comprises 2.56% of all detected industry underground and dark web chatter in the last 90 days, and ranks 10th out of 14 industries.
Below are observed key trends across 90 days:
Data Breach
149 → 255 → 272, Strong and consistent growth. Indicates that logistics firms and transportation providers are facing sustained compromise attempts, likely due to their role in supply chain operations and critical infrastructure.
Data Leak
168 → 295 → 190, Spiked in the middle period before dropping back, though still higher than the starting point. Suggests ongoing exfiltration of logistics data such as shipping records, tracking information, and customer details.
Ransomware
152 → 129 → 90, Gradual decline across the periods. While still a notable risk, ransomware chatter is tapering, possibly as attackers pivot to data theft and breaches instead of purely disruptive operations.
Claimed Hacks
19 → 44 → 7, Sharp spike in the middle period followed by a steep drop. Likely reflects a wave of publicly claimed intrusions that has since slowed.
Denial of Service (DoS)
16 → 6 → 27, After a lull, DoS-related chatter surged in the latest period. This is correlated to recent European airport incidents.
Web Exploit
18 → 6 → 7, Dropped significantly after the first period and has remained low. Indicates reduced focus on web-facing vulnerabilities in logistics-specific platforms.
Hacktivism
2 → 13 → 11, A marked increase compared to the first period, though slightly down in the latest window, suggesting growing interest from ideologically motivated groups.
Over the past three months, CYFIRMA’s telemetry has identified 169 mentions of the transportation & logistics industry out of a total of 2.855 industry mentions. This is from over 10k CVEs reported and updated in the last 90 days.
The transportation & logistics industry ranked 5th out of 14 industries in the last 90 days, with a share of 5.92% of all detected industry-linked vulnerabilities.
Below is a breakdown by 30-day periods of all mentions.
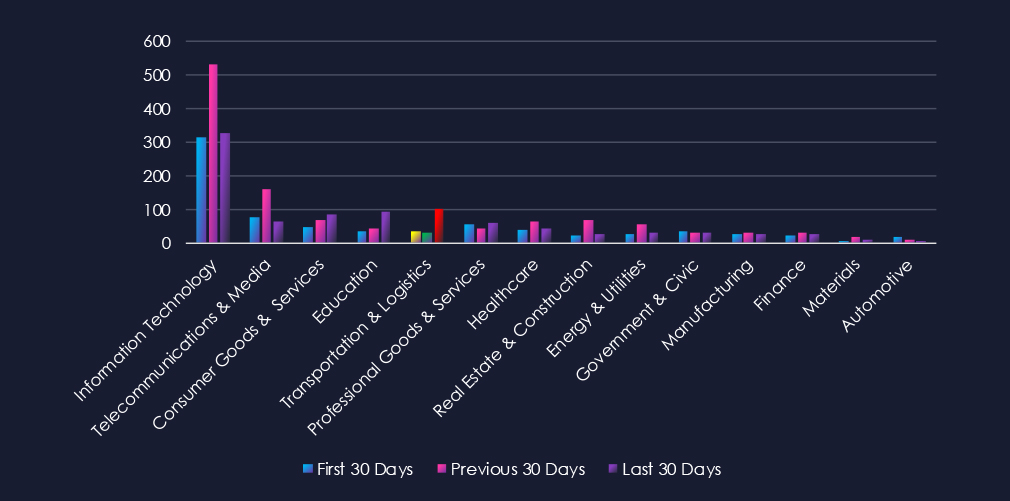
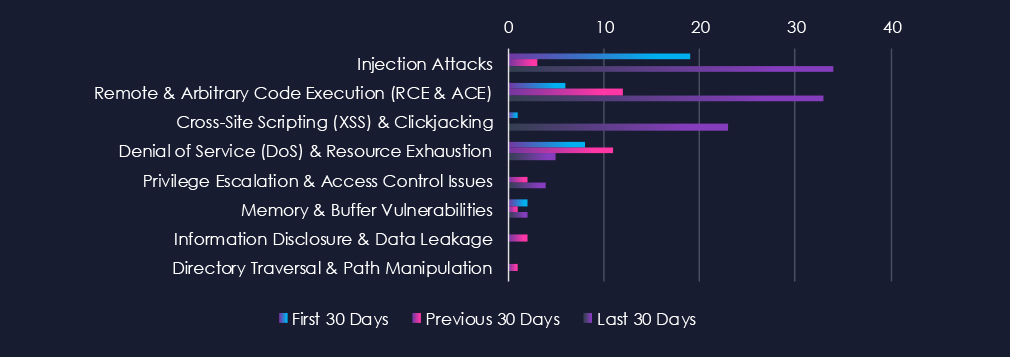
In the last 30 days, there has been a major spike in reported CVEs for this industry. Many of them are due to the downfall from recent European airport incidents and supply-chain scrutiny. Injection Attacks, Remote & Arbitrary Code Execution (RCE & ACE), and XSS7 Clickjacking were the most prevalent categories in the latest CVEs.

In total, the transportation & logistics industry comprises 5.92% of all detected industry-linked vulnerabilities in the last 90 days. And ranking 5th out of 14 industries.
Below are observed key trends across 90 days.
Injection Attacks
19 → 3 → 34, Sharp spike in the latest period after low reporting in the middle window. This surge likely reflects intensified researcher/vendor focus on web and application security following heightened scrutiny of transportation systems in the wake of recent incidents.
Remote & Arbitrary Code Execution (RCE & ACE)
6 → 12 → 33, Strong upward trend, peaking in the most recent 30 days. Suggests that more high-severity flaws have been disclosed in critical transportation-related platforms, with a likely connection to deeper security reviews and emergency patch cycles post-incident.
Cross-Site Scripting (XSS) & Clickjacking
1 → 0 → 23, Minimal activity early, but a sudden spike in the last 30 days. Indicates newly disclosed weaknesses in web-facing portals such as booking systems, cargo tracking, or airport services.
Denial of Service (DoS) & Resource Exhaustion
8 → 11 → 5, Initially steady, but down in the latest period. While still a concern, the focus of recent disclosures appears to have shifted to injection and RCE rather than service disruption flaws.
Privilege Escalation & Access Control Issues
0 → 2 → 4, Gradual rise, reflecting increased reporting of authentication and role mismanagement issues. May point to closer review of access controls in aviation and logistics IT systems following recent events.
Memory & Buffer Vulnerabilities
2 → 1 → 2, Low and stable across periods. Indicates some ongoing disclosures, likely in embedded or legacy systems, but not a dominant issue relative to injection and RCE.
Information Disclosure & Data Leakage
0 → 2 → 0, Minor and inconsistent reporting, suggesting this category is not currently a major focus of disclosures in the sector.
Directory Traversal & Path Manipulation
0 → 1 → 0, Isolated reporting only, with no sustained trend.
In the past 90 days, CYFIRMA has identified 48 verified ransomware victims in the transportation & logistics industry. This accounts for 3.2% of the overall total of 1,505 ransomware victims during the same period, placing the transportation & logistics industry 12th out of 14 industries.
Furthermore, a quarterly comparison reveals a major decrease in interest in transportation & logistics organizations of -27.3% from 66 to 48 victims. The overall share also dropped from 4.5% to 3.2% of all victims.
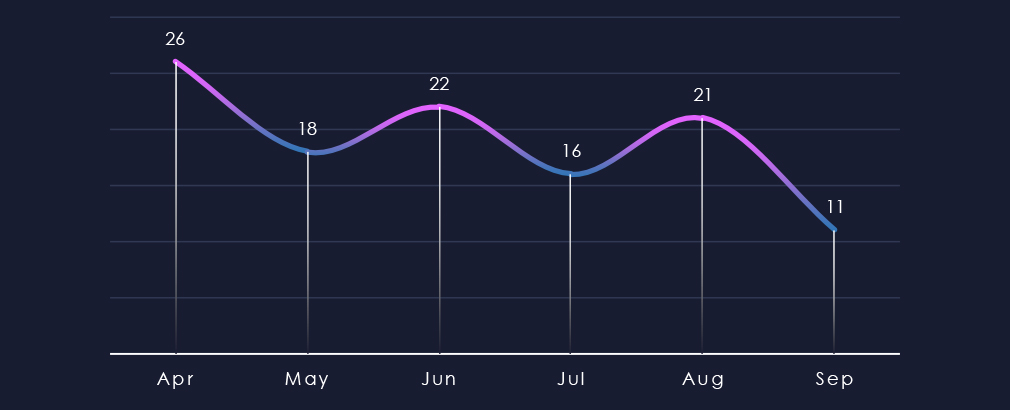
Over the past 180 days, we have not observed any significant spike like the major February victims dump earlier this year. Activity has been sustained and mildly declining over the past 6 months.
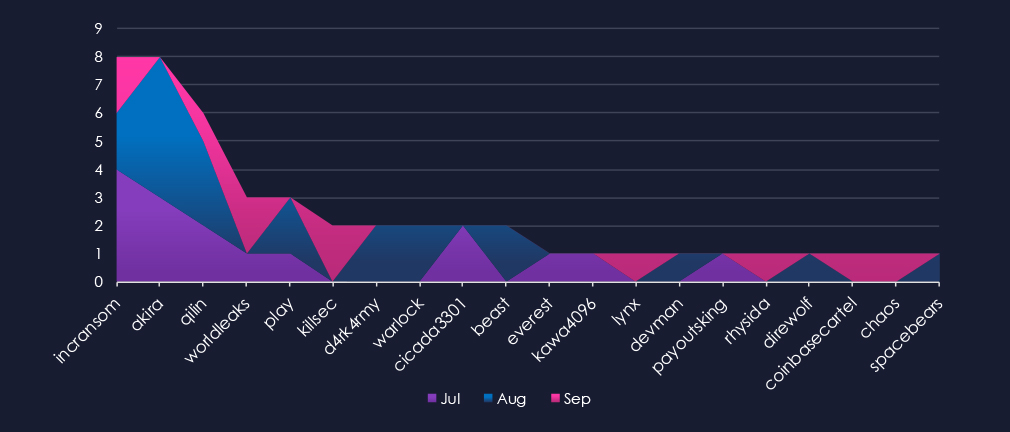
A breakdown of monthly activity per gang provides insights into which gangs were active each month. For example, the most active gang, IncRansom, was active across months, with most victims in July; the other most active gang, Akira, was active only in July and August, recording most victims during August.
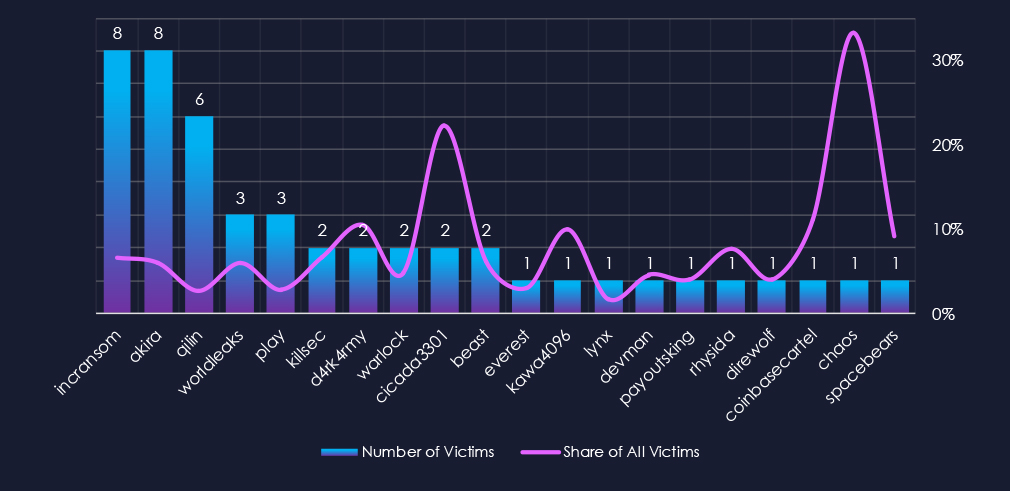
Out of the 76 gangs, 20 recorded victims in this industry in the last 90 days (26% participation). Incransom and Akira had the highest number of victims (8).
The share of victims for most gangs in this industry is low. Only 2 of the top 10 gangs recorded 10% or more of the victims in this industry, while 3 have below 5%.
Among the top 10 gangs, D4rk4rmy (10.5%) and Cicada3301 (22%) recorded high shares in this industry, however, they recorded overall low numbers of victims.
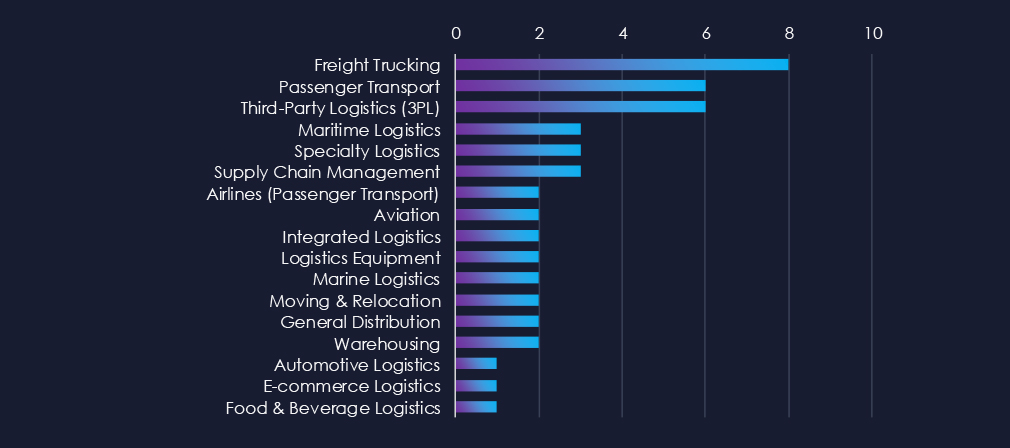
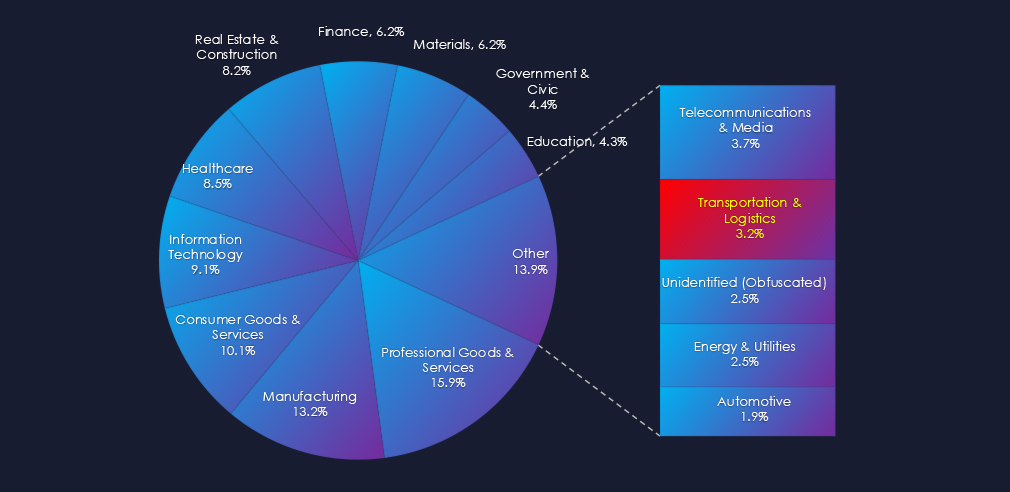
Freight trucking is the most frequent victim of ransomware in this industry. Third-party logistics and passenger transport follow in second and third place.
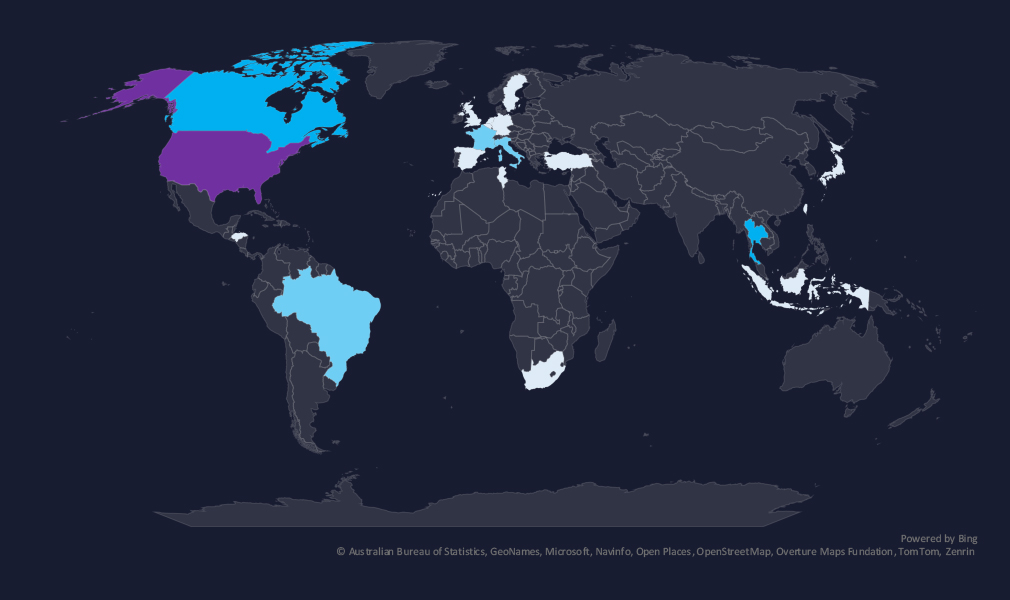
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
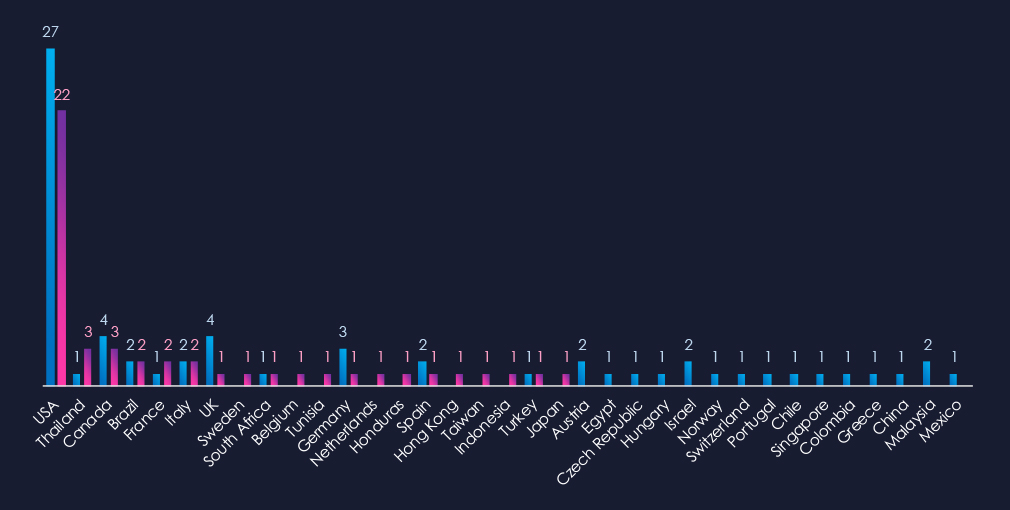
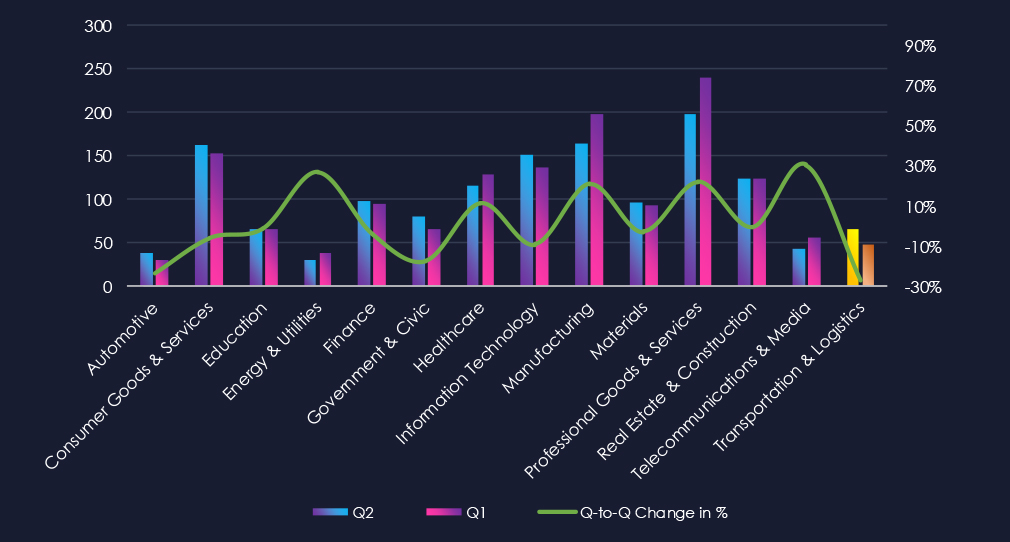
The chart shows quarter-to-quarter changes in targeted countries. Data is sorted by the last 90 days and compared to the previous 90 days, marked in blue.
In the last 90 days, the USA recorded 22 victims, representing 46% of all victims. Thailand and Canada follow in the top three. Thailand recorded the highest increase, whereas many countries like the UK, Germany, and Malaysia recorded a decline in victims in this industry.

The transportation & logistics industry placed 12th out of 14 monitored industries, recording 48 victims in the last 90 days, a major decrease of -27% from 66 victims in the previous 90-day period.
Overall share also dropped from 4.5% to 3.2% of all ransomware victims.
Monthly Activity Trends
Monthly activity showed mild oscillation between months, but overall sustained number with a very mild declining trend ending with a major dip to half of the monthly average in September.
Ransomware Gangs
A total of 20 out of 76 active ransomware groups targeted this industry in the past 90 days – 26% participation:
Incransom, Akira: The most active with 8 victims, 6.6% (8 out of 121) and 6.0% (8 out of 133) share victims. respectively
Da4rk4rmy, Cicada3301: Highest shares of 10.5% (2 out of 19) and 22% (2 out of 9) victims among the top 10 gangs.
Geographic Distribution
The geographic distribution of ransomware victims is spread across the globe due to the nature of this industry. The USA (222) accounted for 46% of all victims, followed by Thailand (3) and Canada (3). Notably, most countries recorded a decline in victims.
In total, 20 countries recorded ransomware victims in this industry in the last 90 days, five fewer than 25 in the previous period.
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
APT Campaigns (Moderate): The transportation & logistics sector faced moderate exposure to APT activity over the past 90 days, with 5 of 14 observed campaigns targeting it (36%). This is a marked increase from the previous period, when only one campaign was recorded. Activity peaked in September, following steady operations through July and August. Key threat actors included four Chinese groups, a Russian cybercrime syndicate, North Korea’s Lazarus Group, and Pakistan’s Transparent Tribe. Victims were spread across 23 countries, with the US, UK, India, and Japan present in every campaign. Web applications were the most frequently exploited, alongside operating systems, routers, and database software.
Underground & Dark Web Chatter (Low): Chatter levels remained low, with the sector accounting for 2.56% of observed mentions (10th out of 14). Data breaches grew steadily (149 → 272), while data leaks spiked mid-period before dropping, but stayed elevated. Ransomware chatter declined across the window, indicating a shift away from purely disruptive operations toward breaches and theft. Claimed hacks briefly surged but fell sharply, suggesting reduced willingness to publicize intrusions. DoS mentions rose again, tied to EU airport incidents, while hacktivism increased compared to earlier baselines. Web exploit mentions remained low, showing less focus on platform vulnerabilities.
Vulnerabilities (Moderate): The industry ranked 5th for reported vulnerabilities (5.92%), reflecting moderate exposure. The most notable shift was a sharp rise in injection (19 → 34) and RCE flaws (6 → 33) in the latest period, highlighting intensified research and disclosure linked to transport IT and OT systems. XSS and clickjacking also spiked (0 → 23), pointing to weaknesses in web-facing portals such as cargo tracking and booking systems. DoS vulnerabilities fell, while privilege escalation steadily increased, reflecting access control scrutiny post the recent European airports incident. Memory, data leakage, and directory traversal flaws were reported only sporadically.
Ransomware (Low): Ransomware risk was comparatively low, with the sector ranking 12th overall. Victims dropped by 27% to 48, representing 3.2% of all cases. Activity fluctuated month to month but ended with a sharp decline in September. Twenty groups were active, led by Incransom and Akira (8 victims each), while smaller gangs such as Da4rk4rmy and Cicada3301 showed high proportional focus on logistics targets. Victims were spread globally, though the US remained the largest cluster, followed by Thailand and Canada. Overall, 20 countries were impacted, down from 25 in the prior period.