CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type:
Ransomware
Target Technologies:
Windows
Introduction
CYFIRMA Research and Advisory Team has found Obscura Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Theft Ransomware
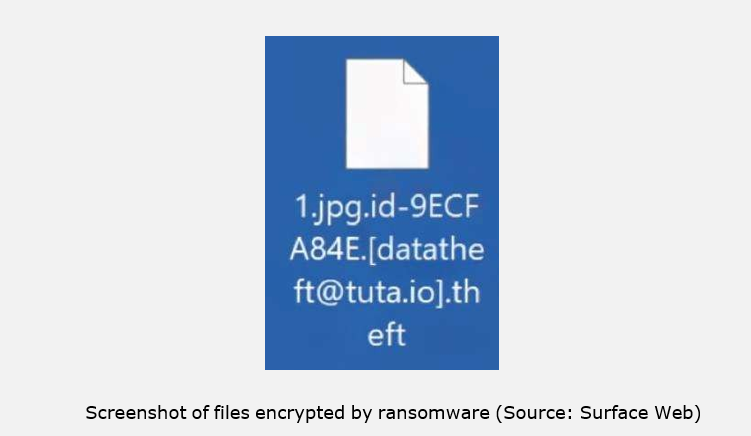
Researchers identified a new variant of the Dharma ransomware family known as Theft, which is designed to encrypt local and network-shared files while avoiding critical system components to keep infected devices operable. Once executed, the ransomware appends encrypted files with a unique victim ID, the attacker’s email address, and the “.theft” extension. During the encryption process, active processes linked to opened files such as databases or document editors are terminated to prevent access conflicts. The malware ensures persistence by copying itself into the %LOCALAPPDATA% directory, configuring Run registry keys for auto-execution, and deleting Volume Shadow Copies to block native recovery options. Additionally, it collects geolocation data that may influence its execution behavior, such as targeting specific regions.
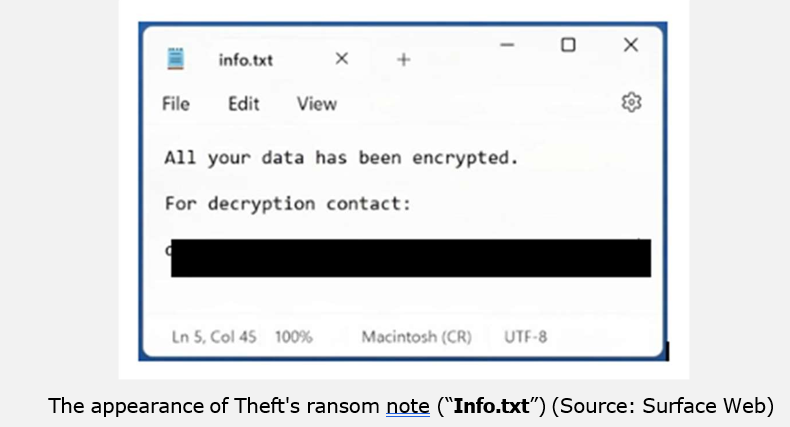
After encryption, Theft generates two ransom demands: a pop-up message and a text file named info.txt placed in all affected folders. The pop-up provides detailed instructions, offering to decrypt up to three files (smaller than 3 MB and non-critical) as proof of decryption capability, while warning against renaming files or using third- party tools.
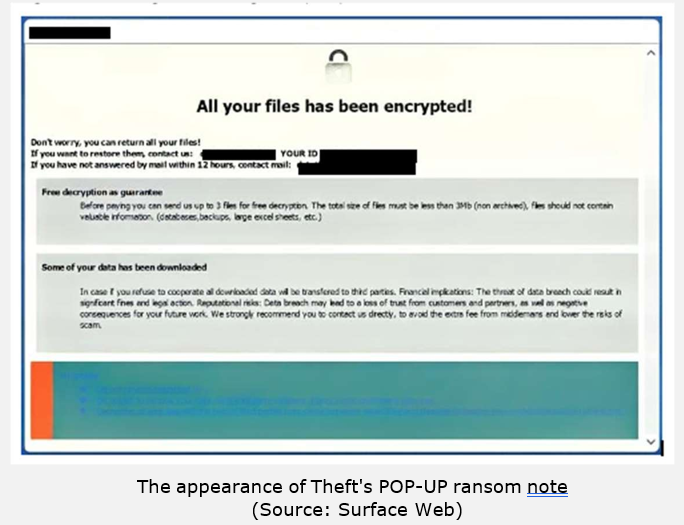
It also introduces a double extortion element, claiming that sensitive business- related data has been exfiltrated and will be leaked if payment is not made. The ransom note directs victims to contact the attackers through email, emphasizing that attempts to involve intermediaries may increase costs or expose victims to scams.
The following are the TTPs based on the MITRE Attack Framework
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of Teft identifies it as a Dharma family ransomware that encrypts local and network-shared files, appends a victim ID and attacker contact to filenames (.theft), kills processes locking targets, deletes Volume Shadow Copies, and establishes persistence by copying itself to %LOCALAPPDATA% and adding Run registry entries.During execution it may terminate applications that hold files open to ensure successful encryption and drops info.txt plus a pop-up ransom message that offers limited free decryption as proof and claims data exfiltration for coercion.Technically, the sample is modular enough to be altered: its cryptographic routine, file- targeting rules, and persistence mechanisms can be swapped or extended (e.g., scheduled tasks, service installation, or WMI/event subscription). Evasion can be hardened by adding richer anti-analysis checks, in-memory loading, packing, or polymorphism; lateral movement and exfiltration capabilities can be bolted on via credential theft, SMB propagation, or encrypted uploads to attacker-controlled endpoints. These kinds of changes would broaden impact and complicated detection, shifting indicators from single artifacts (extension, Run keys) to a combination of endpoint and network telemetry.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
category: process_creation product: windowsdetection: selection1_img:
CommandLine|contains|all:- ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”- ‘delete’ selection2_img:
CommandLine|contains|all:
CommandLine|contains|all:
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
IOCs:Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Trending Malware of the Week [New]Type: Information Stealer | Objectives: Stealing Sensitive Information, Data Exfiltration |Target Technologies: Windows OS, Web Browsers | Target Geography: GlobalCYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
Thisweek,“RavenStealer”istrending.
Overview of Raven Stealer Malware
Raven Stealer is a lightweight, modern information-stealing malware designed for stealth and efficiency. Built to harvest credentials, cookies, autofill data, and other browser-stored information, it exfiltrates stolen details in real time, often using Telegram as a communication channel and a promotional outlet via dedicated channels. Its distribution often takes place through underground forums and cracked software bundles, making it accessible to a wide range of operators, including those with limited technical skills. What sets Raven Stealer apart is its streamlined design and modular build, allowing attackers to configure it easily and deploy it quickly. By targeting Chromium-based browsers such as Chrome and Edge, it focuses on the most widely used platforms, ensuring maximum impact. With the ability to bypass basic antivirus detection and deliver stolen data instantly, Raven Stealer has established itself as a persistent and commercially attractive threat within the cybercrime ecosystem.
Technical Analysis
Attackers spread this malware through underground forums and pirated or trojanized software bundles, luring victims into executing compromised installers. Once launched, Raven Stealer moves quickly into action with minimal user interaction, relying on its builder to embed payloads and operator credentials directly into the executable. Each build is uniquely named with a randomly generated filename, helping it evade simple signature-based detection and ensuring campaigns remain flexible.The builder’s interface allows operators to input Telegram Chat IDs and Bot Tokens, which are then stored in the resource section of the binary. At runtime, the malware decrypts its embedded payload in memory and often injects it into a Chromium process, enabling it to run under the guise of legitimate software. From there, it focuses on extracting sensitive data from Chromium- based browsers — including passwords, cookies, autofill details, and payment data — and organizes them into dedicated folders under the user’s AppData directory.All collected artifacts, including a desktop screenshot, are compressed into a single archive and transmitted through Telegram’s API for remote access. Even in cases where transmission fails due to invalid tokens, the process highlights how Raven Stealer combines resource embedding, in- memory execution, and streamlined configuration to maintain stealth and make credential theft accessible to a wide range of operators.The following are the TTPs based on the MITRE Attack Framework for Enterprise
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Raven Stealer is likely to accelerate the commoditization of sophisticated cyber tools, making advanced information-stealing capabilities increasingly accessible to a wider range of threat actors. Future variants may adopt even more seamless integration with popular communication and collaboration platforms, enabling faster and more covert data exfiltration across diverse environments. As its framework becomes more modular and adaptable, the overall cyber threat landscape may see an increase in scale, frequency, and diversity of attacks, affecting digital ecosystems globally and pushing defenders to contend with more persistent and automated threats.
IOCs:Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Raven_Stealer_Indicators{
meta:description = “Detects Raven Stealer malware indicators” author = “CYFIRMA”malware_family = “Raven Stealer”strings:// SHA256 File Hashes$sha256_1 = “2b24885942253784e0f6617b26f5e6a05b8ad45f092d2856473439fa6e095ce4″$sha256_2 = “65ca89993f2ee21b95362e151a7cfc50b87183bf0e9c5b753c5e5e17b46f8c24″condition:any of ($sha256*)}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
Please refer to the trending malware advisory for details on the following:
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart
from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.2. Threat Actor in Focus
Inside Kimsuky: RGB-Aligned Cyber Threat Actor Targeting US and SouthKorea
About the Threat Actor
Kimsuky, an advanced persistent threat (APT) group active since at least 2012, is suspected to be operating out of North Korea in direct support of the regime’s strategic objectives. The group’s intelligence collection priorities are closely aligned with the mission of the Reconnaissance General Bureau (RGB), North Korea’s primary foreign intelligence agency. Kimsuky possesses moderately sophisticated technical capabilities and is known for employing highly targeted social engineering tactics, especially against the South Korean and U.S.-based government agencies, academics, and think tanks focused on geopolitical issues related to the Korean Peninsula. In addition to its espionage operations, Kimsuky engages in cybercriminal activities to generate revenue, helping to finance its overarching mission of acquiring strategic intelligence.
Details on Exploited Vulnerabilities
| Tactic | Technique ID | Technique Name | |
| Execution | T1106 | Native API | |
| Execution | T1129 | Shared Modules | |
| Persistence | T1112 | Modify Registry | |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup
Folder |
|
| Privilege Escalation | T1055 | Process Injection | |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup
Folder |
|
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing | |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads | |
| Defense Evasion | T1036 | Masquerading | |
| Defense Evasion | T1055 | Process Injection | |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion | |
| Defense Evasion | T1112 | Modify Registry | |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | |
| Defense Evasion | T1202 | Indirect Command Execution | |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion | |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories | |
| Discovery | T1057 | Process Discovery | |
| Discovery | T1082 | System Information Discovery | |
| Discovery | T1083 | File and Directory Discovery | |
| Discovery | T1497 | Virtualization/Sandbox Evasion | |
| Collection | T1074 | Data Staged | |
| Command and Control | T1071 | Application Layer Protocol | |
| Command and Control | T1105 | Ingress Tool Transfer | |
| Impact | T1485 | Data Destruction | |
| Impact | T1486 | Data Encrypted for Impact | |
| Tactic | Technique ID | Technique Name | |
| Execution | T1059 | Command and Scripting Interpreter | |
| Execution | T1106 | Native API | |
| Execution | T1129 | Shared Modules | |
| Privilege Escalation | T1055 | Process Injection | |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing | |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools | |
| Defense Evasion | T1036 | Masquerading | |
| Defense Evasion | T1055 | Process Injection | |
| Defense Evasion | T1070 | Indicator Removal | |
| Defense Evasion | T1202 | Indirect Command Execution | |
| Discovery | T1057 | Process Discovery | |
| Discovery | T1082 | System Information Discovery | |
| Discovery | T1083 | File and Directory Discovery | |
| Discovery | T1518 | Software Discovery | |
| Discovery | T1614 | System Location Discovery | |
| Collection | T1005 | Data from Local System | |
| Collection | T1185 | Browser Session Hijacking | |
| Command and Control | T1071 | Application Layer Protocol | |
| Command and Control | T1102 | Web Service | |
| Command and Control | T1105 | Ingress Tool Transfer | |
| Command and Control | T1573 | Encrypted Channel | |
| CVE ID | Affected Products | CVSS Score | Exploit Links |
|
CVE-2017-11882 |
Microsoft Office |
7.8 |
link |
|
CVE-2019-0708 |
Remote Desktop Services |
9.8 |
link1, link2, link3, link4, link5 |
| Tactic | ID | Technique | |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email
Addresses |
|
| Reconnaissance | T1589.003 | Gather Victim Identity Information: Employee
Names |
|
| Reconnaissance | T1591 | Gather Victim Org Information | |
| Reconnaissance | T1598 | Phishing for Information | |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link | |
| Reconnaissance | T1596 | Search Open Technical Databases | |
| Reconnaissance | T1593 | Search Open Websites/Domains | |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media | |
| Reconnaissance | T1593.002 | Search Open Websites/Domains: Search
Engines |
|
| Reconnaissance | T1594 | Search Victim-Owned Websites | |
| Resource Development | T1583 | Acquire Infrastructure | |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | |
| Resource Development | T1583.004 | Acquire Infrastructure: Server | |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services | |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts | |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains | |
| Resource Development | T1587 | Develop Capabilities | |
| Resource Development | T1587.001 | Develop Capabilities: Malware | |
| Resource Development | T1585 | Establish Accounts | |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts | |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts | |
| Resource Development | T1588.002 | Obtain Capabilities: Tool | |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates | |
| Resource Development | T1588.005 | Obtain Capabilities: Exploits | |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware | |
| Initial Access | T1133 | External Remote Services | |
| Initial Access | T1190 | Exploit Public-Facing Application | |
| Initial Access | T1566 | Phishing | |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment | |
| Initial Access | T1566.002 | Phishing: Spear phishing Link | |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts | |
| Execution | T1059.001 | Command and Scripting Interpreter:
PowerShell |
|
| Execution | T1059.003 | Command and Scripting Interpreter: Windows
Command Shell |
|
| Execution | T1059.005 | Command and Scripting Interpreter: Visual
Basic |
|
| Execution | T1059.006 | Command and Scripting Interpreter: Python | |
| Execution | T1059.007 | Command and Scripting Interpreter:
JavaScript |
|
|
Execution |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
|
Execution |
T1204.001 |
User Execution: Malicious Link |
|
|
Execution |
T1204.002 |
User Execution: Malicious File |
|
|
Persistence |
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | |
|
Persistence |
T1098.007 |
Account Manipulation: Additional Local or Domain Groups | |
|
Persistence |
T1136.001 |
Create Account: Local Account |
|
|
Persistence |
T1543.003 |
Create or Modify System Process: Windows Service | |
|
Persistence |
T1546.001 |
Event Triggered Execution: Change Default File Association | |
|
Persistence |
T1078.003 |
Valid Accounts: Local Accounts |
|
|
Persistence |
T1505.003 |
Server Software Component: Web Shell |
|
|
Persistence |
T1205 |
Traffic Signaling |
|
|
Persistence |
T1176.001 |
Software Extensions: Browser Extensions |
|
|
Persistence |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
|
Persistence |
T1112 |
Modify Registry |
|
|
Persistence |
T1133 |
External Remote Services |
|
|
Privilege Escalation |
T1098.007 |
Account Manipulation: Additional Local or Domain Groups | |
|
Privilege Escalation |
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | |
| Privilege Escalation |
T1543.003 |
Create or Modify System Process: Windows Service | |
|
Privilege Escalation |
T1546.001 |
Event Triggered Execution: Change Default File Association | |
|
Privilege Escalation |
T1055 |
Process Injection |
|
|
Privilege Escalation |
T1055.012 |
Process Injection: Process Hollowing |
|
|
Privilege Escalation |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
|
Privilege Escalation |
T1078.003 |
Valid Accounts: Local Accounts |
|
|
Defense Evasion |
T1140 |
Deobfuscate/Decode Files or Information |
|
|
Defense Evasion |
T1564.002 |
Hide Artifacts: Hidden Users |
|
|
Defense Evasion |
T1564.003 |
Hide Artifacts: Hidden Window |
|
|
Defense Evasion |
T1562.001 |
Impair Defenses: Disable or Modify Tools |
|
|
Defense Evasion |
T1562.004 |
Impair Defenses: Disable or Modify System Firewall | |
|
Defense Evasion |
T1656 |
Impersonation |
|
|
Defense Evasion |
T1070.004 |
Indicator Removal: File Deletion |
|
|
Defense Evasion |
T1070.006 |
Indicator Removal: Timestomp |
|
|
Defense Evasion |
T1036.004 |
Masquerading: Masquerade Task or Service |
|
|
Defense Evasion |
T1036.005 |
Masquerading: Match Legitimate Resource Name or Location | |
|
Defense Evasion |
T1112 |
Modify Registry |
|
|
Defense Evasion |
T1027 |
Obfuscated Files or Information |
|
|
Defense Evasion |
T1027.002 |
Obfuscated Files or Information: Software Packing | |
|
Defense Evasion |
T1055 |
Process Injection |
|
|
Defense Evasion |
T1055.012 |
Process Injection: Process Hollowing |
|
|
Defense Evasion |
T1620 |
Reflective Code Loading |
|
|
Defense Evasion |
T1553.002 |
Subvert Trust Controls: Code Signing |
|
|
Defense Evasion |
T1218.005 |
System Binary Proxy Execution: Mshta |
|
| Defense Evasion |
T1218.010 |
System Binary Proxy Execution: Regsvr32 |
|
|
Defense Evasion |
T1218.011 |
System Binary Proxy Execution: Rundll32 |
|
|
Defense Evasion |
T1205 |
Traffic Signaling |
|
|
Defense Evasion |
T1550.002 |
Use Alternate Authentication Material: Pass the Hash | |
|
Defense Evasion |
T1078.003 |
Valid Accounts: Local Accounts |
|
|
Credential Access |
T1557 |
Adversary-in-the-Middle |
|
|
Credential Access |
T1555.003 |
Credentials from Password Stores: Credentials from Web Browsers | |
|
Credential Access |
T1003.001 |
OS Credential Dumping: LSASS Memory |
|
|
Credential Access |
T1056.001 |
Input Capture: Keylogging |
|
|
Credential Access |
T1111 |
Multi-Factor Authentication Interception |
|
|
Credential Access |
T1040 |
Network Sniffing |
|
|
Credential Access |
T1539 |
Steal Web Session Cookie |
|
|
Credential Access |
T1552.001 |
Unsecured Credentials: Credentials In Files |
|
|
Discovery |
T1518.001 |
Software Discovery: Security Software Discovery | |
|
Discovery |
T1040 |
Network Sniffing |
|
|
Discovery |
T1083 |
File and Directory Discovery |
|
|
Discovery |
T1057 |
Process Discovery |
|
|
Discovery |
T1012 |
Query Registry | |
|
Discovery |
T1082 |
System Information Discovery |
|
|
Discovery |
T1016 |
System Network Configuration Discovery |
|
|
Discovery |
T1007 |
System Service Discovery |
|
|
Lateral Movement |
T1534 |
Internal Spear phishing |
|
|
Lateral Movement |
T1021.001 |
Remote Services: Remote Desktop Protocol |
|
|
Lateral Movement |
T1550.002 |
Use Alternate Authentication Material: Pass the Hash | |
| Collection |
T1560.001 |
Archive Collected Data: Archive via Utility |
|
|
Collection |
T1557 |
Adversary-in-the-Middle |
|
|
Collection |
T1560.001 |
Archive Collected Data: Archive via Utility |
|
|
Collection |
T1560.003 |
Archive Collected Data: Archive via Custom Method | |
|
Collection |
T1185 |
Browser Session Hijacking |
|
|
Collection |
T1005 |
Data from Local System |
|
|
Collection |
T1074.001 |
Data Staged: Local Data Staging |
|
|
Collection |
T1114.002 |
Email Collection: Remote Email Collection |
|
|
Collection |
T1114.003 |
Email Collection: Email Forwarding Rule |
|
|
Collection |
T1056.001 |
Input Capture: Keylogging |
|
|
Collection |
T1113 |
Screen Capture |
|
|
Command and Control |
T1071.001 |
Application Layer Protocol: Web Protocols |
|
|
Command and Control |
T1071.002 |
Application Layer Protocol: File Transfer Protocols |
|
|
Command and Control |
T1071.003 |
Application Layer Protocol: Mail Protocols |
|
|
Command and Control |
T1219.002 |
Remote Access Tools: Remote Desktop Software |
|
|
Command and Control |
T1105 |
Ingress Tool Transfer |
|
|
Command and Control |
T1205 |
Traffic Signaling |
|
|
Command and Control |
T1102.001 |
Web Service: Dead Drop Resolver |
|
|
Command and Control |
T1102.002 |
Web Service: Bidirectional Communication |
|
|
Exfiltration |
T1041 |
Exfiltration Over C2 Channel |
|
|
Exfiltration |
T1567.002 |
Exfiltration Over Web Service: Exfiltration to Cloud Storage |
|
|
Impact |
T1657 |
Financial Theft
|
Latest Developments Observed
The threat actor is suspected of weaponizing ChatGPT to fabricate government identification documents in a phishing campaign targeting South Korean officials. By generating high-resolution images of official credentials, the attackers were able to disguise malware-laden messages as legitimate government communications with the intent of exfiltrating sensitive data.
ETLM Insights
Kimsuky is a North Korea-linked espionage group engaged in long-term intelligence collection and cyber operations targeting government, defense, financial, and critical infrastructure sectors to assist their intelligence agencies and government in their strategies. The threat actor’s critical threat level, combined with artificial intelligence (AI) adoption and advanced technologies, increases the sophistication of their cyberattacks. The adoption of the latest technologies and AI allows the threat group the following:
These evolutions will likely support North Korea’s strategic objectives, gathering intelligence, bypassing sanctions, and destabilizing adversaries, while maintaining stealth and persistence across a broader global attack surface. Organizations need to have predictive, intelligence-led defense and proactive strategies to alert them in advance on to such threats.
YARA Rules
rule Kimsuky_APT_Indicators
{
meta:
description = “Detects potential Kimsuky APT activity based on known IPs, domains, and exploit indicators”
author = “CYFIRMA” date = “2025-09-19”
threat_actor = “Kimsuky”
reference = “CVE-2017-11882, CVE-2019-0708”
strings:
// IP Addresses
$ip1 = “152.32.138.167”
$ip2 = “27.255.80.162”
$ip3 = “212.224.107.244”
$ip4 = “27.255.81.118”
// Domains
$domain1 = “www.vic.apollo-star7.kro.kr”
$domain2 = “bitjoker2024.000webhostapp.com”
$domain3 = “nidlogin.apollo.r-e.kr”
// Exploit-related strings (CVE-2017-11882 and CVE-2019-0708)
$eqnedit = “Equation.3” wide ascii // often used in CVE-2017-11882
$rdp_check1 = “termdd.sys” ascii // RDP-related driver
$rdp_check2 = “TSMSISrv.dll” ascii // part of terminal services
condition:
any of ($ip*) or
any of ($domain*) or 2 of ($rdp_check*) or
$eqnedit
}
Recommendations Strategic
Management
Tactical
European Airports in Chaos Following a Major Cyberattack
Significant European airports were thrown into chaos over the weekend, with thousands of passengers experiencing delays and cancellations as a result of a significant cyberattack. Airlines flying out of Heathrow, Brussels, and Berlin were forced to manually check passengers in after the attack damaged check-in and boarding systems, resulting in hours-long waits on Saturday. Cancellations at Brussels airport warned that disruptions in Europe’s air travel might continue into Monday.
The cyber-attack disrupted a check-in and baggage system. Airlines were forced to return to slower manual check-ins on Friday night following the attack on Collins Aerospace, which provides check-in counter technology to several airlines. On Sunday afternoon, Brussels Airport said it had “no indication yet” when the system would be operational again and requested that half of the departing flights scheduled for Monday be cancelled. The airport stated that Collins was “not yet able to deliver a new secure version of the check-in system” and verified a cyber-attack had occurred.
Heathrow stated on Sunday that efforts to remedy the situation were underway. It did not specify whether the problem was caused by a cyberattack. It apologized to those who had experienced delays but emphasized that “the vast majority of flights have continued to operate,” advising travellers to check their flight status before heading to the airport and arrive on time. Approximately half of the airlines operating from Heathrow were back online by Sunday, including British Airways, which had been using a backup system since Saturday.
ETLM Assessment:
RTX, which owns the software company Collins Aerospace, stated that it was “aware of a cyber-related disruption” to its system in “select airports” and planned to rectify the problem as soon as possible. It identified the compromised system as its Muse software, which allows multiple airlines to utilize the same check-in booths and boarding gates at an airport instead of having their own. The corporation has yet to reveal what went wrong or how long the outage will persist but stated on Sunday that it will “provide details as soon as they are available”. The incident highlights systemic vulnerabilities in service providers, supply chain attacks supporting critical airport functions, and underscores the need for proactive cyber defenses, continuous threat monitoring, and cross-border coordination to mitigate risks posed by these threat actors.
The Killsec Ransomware Impacts HappyTenant
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE), HappyTenant (https[:]//happytenant[.]io/), was compromised by Killsec Ransomware.
HappyTenant is a cloud-based property management platform designed to simplify and automate key tasks for landlords, property managers, and tenants, with a broad market focus on the UAE and growing international reach. The compromised data includes confidential and sensitive information belonging to the organization.
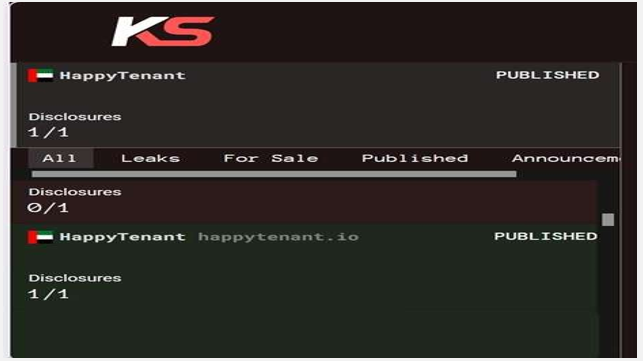

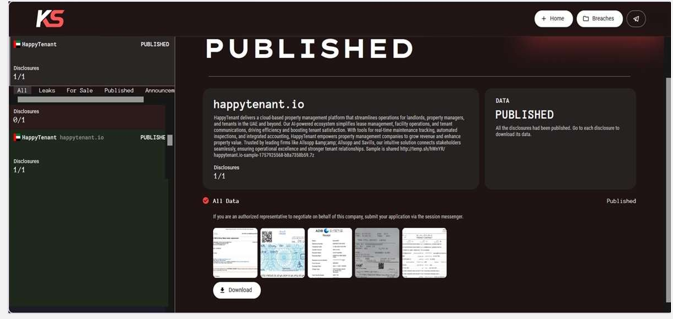
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
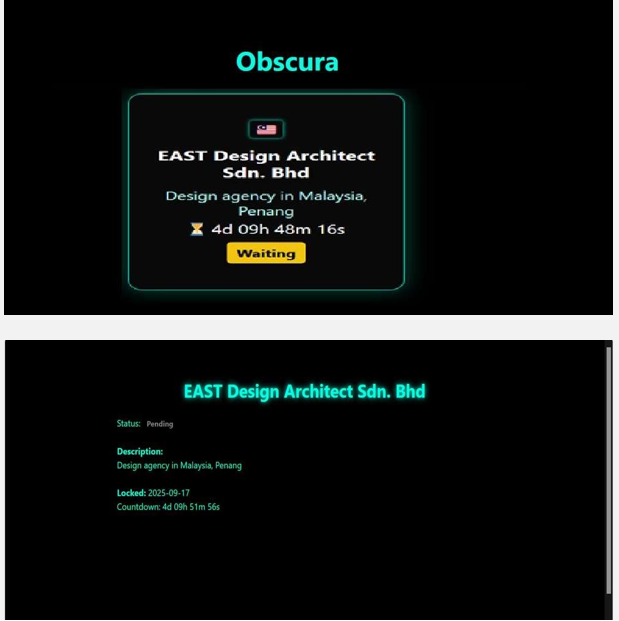
Obscura Ransomware Impacts EAST Design Architect Sdn. Bhd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia, EAST Design Architect Sdn. Bhd (https[:]//www[.]eastdesign[.]com[.]my/) was compromised by Obscura Ransomware. EAST Design Architect Sdn. Bhd is a prominent professional architectural design firm based in Malaysia. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Obscura Ransomware represents a modern, technically proficient ransomware operation, with a sophisticated encryption routine, privilege enforcement, and double-extortion techniques seen in targeted enterprise attacks.
Vulnerability in SolarWinds Web Help Desk
Relevancy & Insights:
The vulnerability exists due to insecure input validation when processing serialized data within the AjaxProxy. A remote attacker can pass specially crafted data to the application and execute arbitrary code on the target system.
Impact: Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products: https[:]//www[.]solarwinds[.]com/trust-center/security- advisories/cve-2025-26399
Recommendations:
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
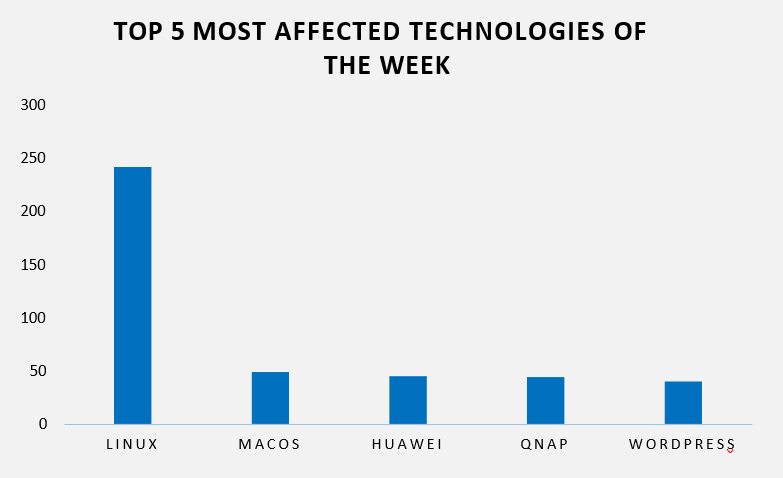
ETLM Assessment
SolarWinds Web Help Desk is a ticketing and IT asset management solution that streamlines IT service management. It provides features for help desk ticketing, knowledge base, asset management, SLA tracking, and workflow automation, helping organizations improve service delivery and reduce response times.
DragonForce Ransomware attacked and published the data of Concord New Energy Group
Summary:
Recently, DragonForce Ransomware was observed attacking and publishing the data of Concord New Energy Group (www[.]cn[.]cnegroup[.]com) on its dark web website. Concord New Energy Group Limited (CNE) is a leading global renewable energy company specializing in the development, operation, and management of wind and solar power plants. The ransomware attack resulted in a significant data leak, affecting multiple departments, including Finance, Human Resources, the International Department, and the Research Center. The exposed information also contains overseas company details and other sensitive and confidential records from the organization’s database. In total, approximately 108.76 GB of data has been compromised.
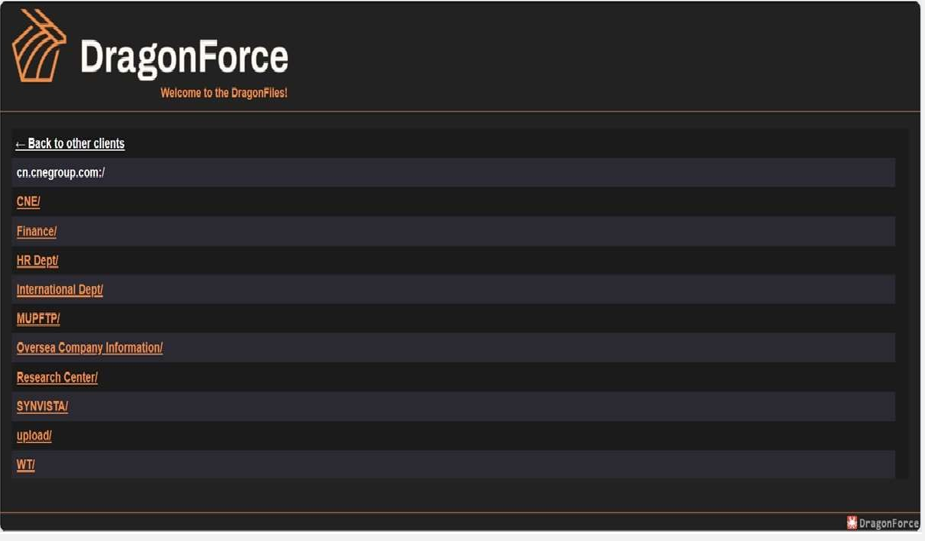
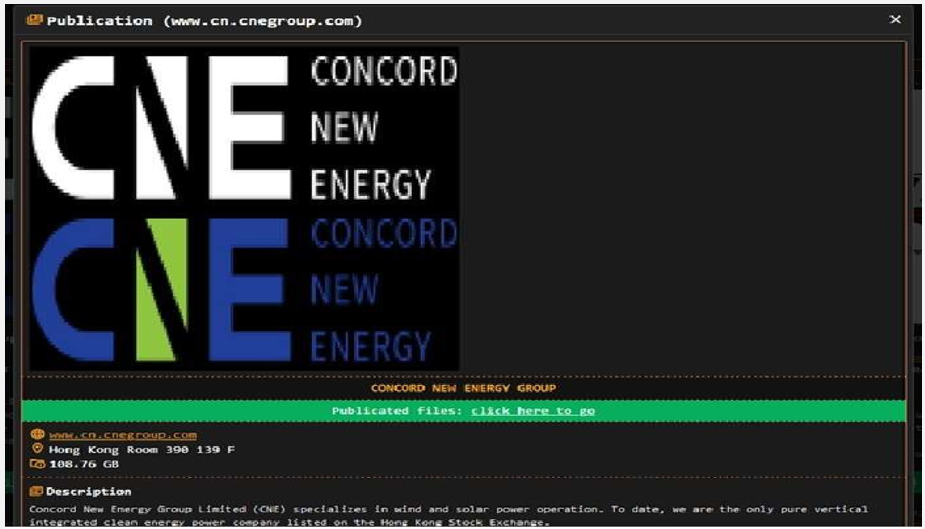
Source : Dak Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, DragonForce represents a significant threat in the ransomware landscape due to its advanced operational methods and extensive use of modified ransomware tools. As it continues to target high-profile organizations globally, ongoing vigilance and proactive cybersecurity strategies will be essential for mitigating risks associated with this formidable threat actor.
Organizations should remain alert to the evolving tactics employed by groups like DragonForce to protect their sensitive data and maintain operational integrity.
Fundline Finance Corporation’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that Fundline Finance Corporation, a significant provider of micro-lending and motorcycle financing services in the Philippines, has allegedly fallen victim to a substantial data breach. A threat actor “Sorb” has posted on a dark web forum claiming to have sensitive personal information of over one million users of the financial institution. The data is being offered for sale for $1,000.
Fundline Finance Corporation, which has been operating for over two decades, plays a crucial role in providing financial services to many Filipinos, particularly micro and small-scale entrepreneurs. The company’s extensive network of 144 branches across the country makes this alleged breach a serious concern for a large number of individuals who have entrusted their personal and financial information to the institution. The alleged leaked data includes a vast amount of personally identifiable information (PII), which could be exploited by malicious actors for various fraudulent activities, including identity theft and phishing scams.
According to the forum post, the compromised data allegedly includes:
The seller has provided samples of the data in CSV and TXT format to substantiate their claims, which appear to contain detailed customer and personal identification information. The investigation into this alleged data breach is ongoing.
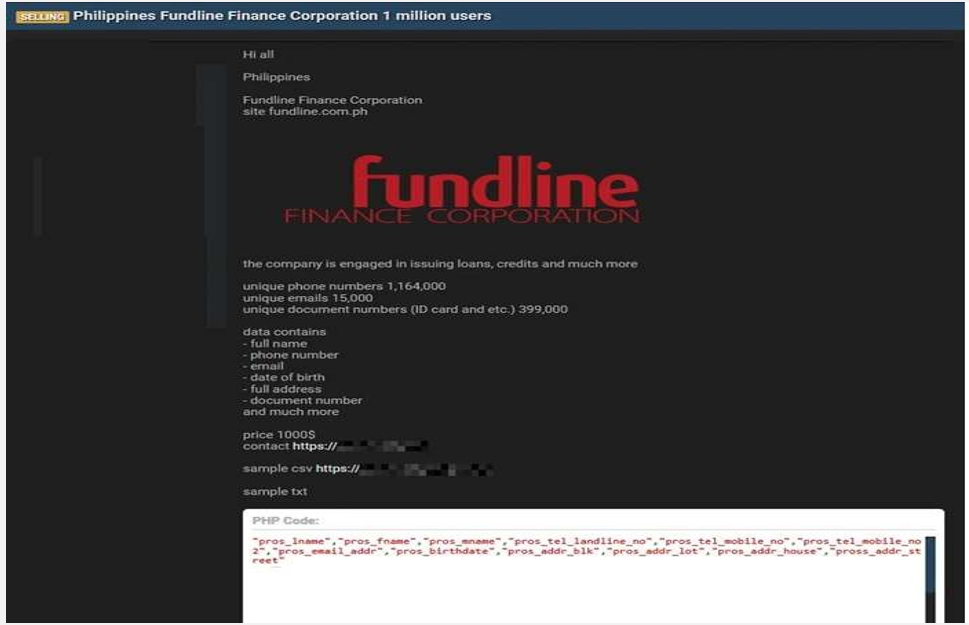
Source: Underground Forums
Reportage Empire’s Data Advertised on a Leak Site
Summary:
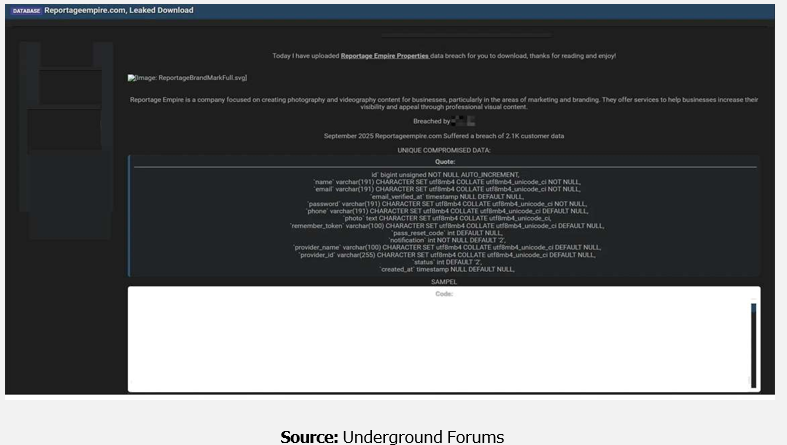
The CYFIRMA Research team has identified that a threat actor “N1KA” claims to have breached Reportage Empire, a company based in the United Arab Emirates that specializes in photography and videography content for business marketing and branding. The actor announced the data leak on a dark web forum, citing a breach date of September 2025.
According to the actor, the allegedly exfiltrated database contains the records of 2,100 customers. The compromised information reportedly includes full names, email addresses, phone numbers, and hashed passwords.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “N1KA” has recently gained attention as a highly active group specializing in data leaks. Reliable sources have connected the group to multiple security breaches involving unauthorized system access and the attempted sale of exfiltrated data on dark web marketplaces. N1KA’s ongoing operations highlight the evolving and persistent nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to strengthen their cybersecurity posture through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and infrastructure.
Recommendations:
Enhance the cybersecurity posture by:
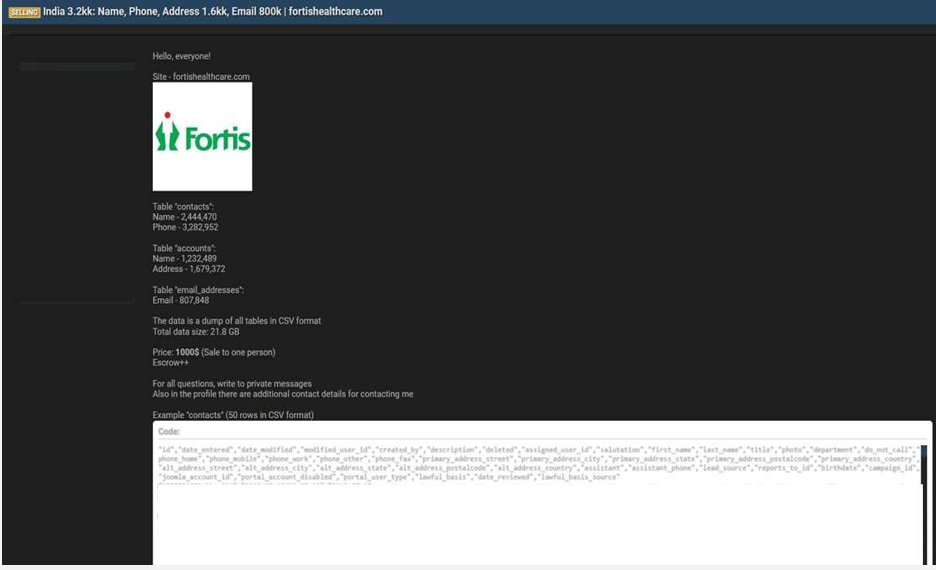
The CYFIRMA Research team observed that a threat actor claims to have breached Fortis Healthcare, a major Indian healthcare provider. The actor has posted the allegedly stolen database for sale, containing a significant volume of patient and contact information. The total size of the compromised data is listed as 21.8 GB. According to the actor, the exfiltrated database contains records of over 3.2 million individuals across multiple tables. The compromised information includes full names, phone numbers, physical addresses, email addresses, dates of birth, and other personal contact details.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
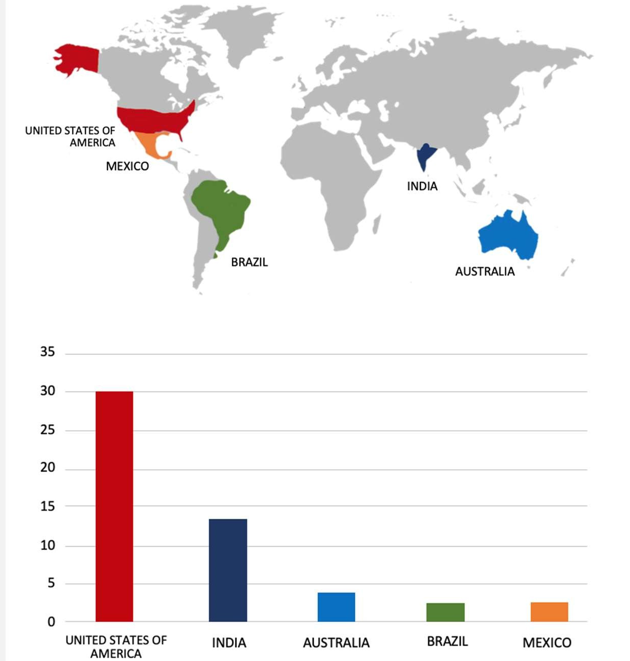
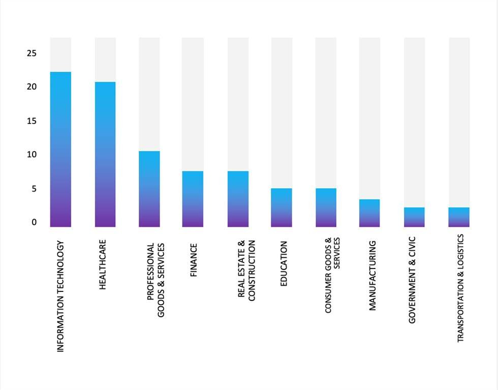
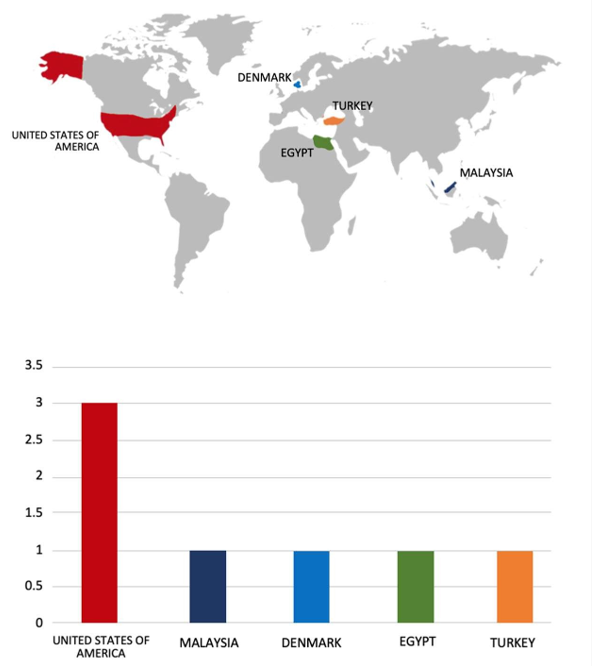
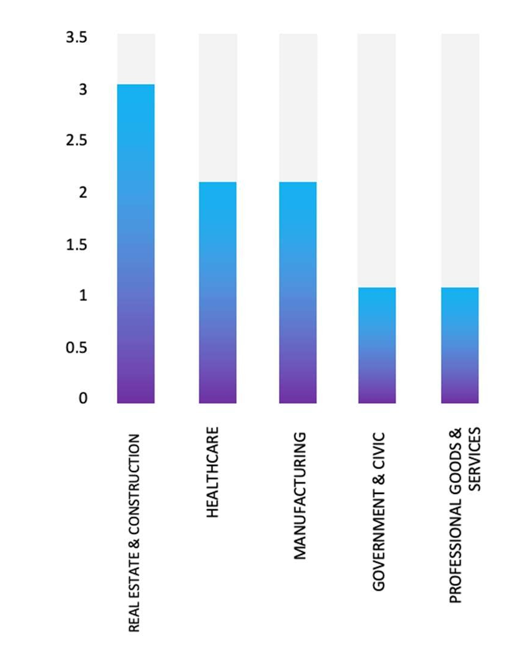
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.