


In this report, our researchers analysed recent cyber activity targeting Qatar, including data leaks, the sale of initial access, and ransomware incidents. We explain how initial access often escalates into ransomware or state-level operations and note that recent strikes by Israel could motivate hacktivist attacks against Qatar for perceived inaction. Large “combolists” are an additional concern, as they provide attackers with ready-made credential lists for credential-stuffing and brute-force campaigns that can yield system or server access.
Following Israel’s reported missile strike on a Hamas leader’s residence in Qatar, regional tensions may spill into cyberspace. Pro-Palestine hacktivist groups are likely to escalate operations against Israeli entities, while pro-Israel groups may retaliate with DDoS and website defacement campaigns against Qatar organizations.
On September 10, the pro-Palestine hacktivist group Team Fearless launched DDoS attacks on multiple Qatar government websites, citing Doha’s lack of action over the conflict, an incident that underscores the ongoing hacktivist trend of using disruptive but low-sophistication tactics like DDoS and defacements to pressure regional governments and gain visibility.
On a Russian forum, a data broker using the handle “stepbro” advertised roughly 13,000 Qatar customer records potentially containing sensitive PII (names, government emails, phone numbers), which is concerning because such data can be used for targeted social-engineering, phishing, and other follow-on attacks.
The same threat actor is also selling Qatar email leads, a serious concern because those lists enable large-scale phishing and spam, highly targeted spear-phishing and business-email-compromise (BEC) against government and critical personnel, credential-stuffing and account takeover, SMS/voice social-engineering, and can be used to seed follow-on intrusions or disinformation campaigns.
On a Chinese forum a data broker advertised a purported “big” leak of Qatar organisation records (names, emails, phone numbers, addresses and other sensitive fields) for about $1,400, but the claim should be treated with caution because such forums often host bogus listings nevertheless, if genuine this dataset enables mass phishing, targeted spear-phishing/BEC, credential-stuffing, SMS/voice social-engineering, doxxing and follow-on intrusions.
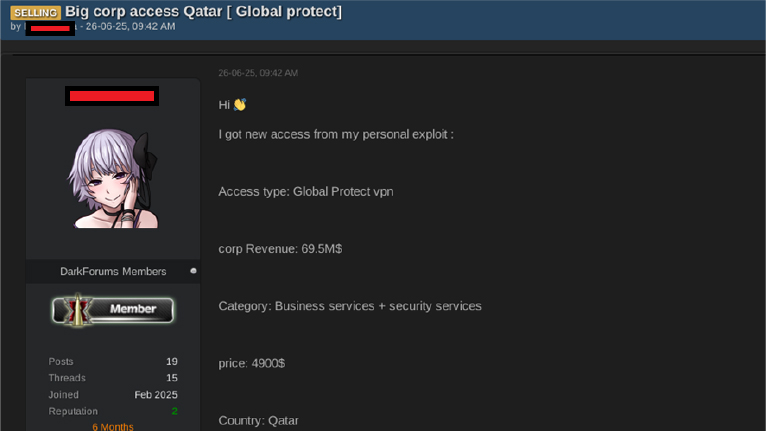
An initial-access broker is offering corporate access to a large Qatar organisation for $4,900, a critical concern because that foothold can be sold or resold to ransomware operators or a nation-state.
Access bought from an initial-access broker can enable a wide range of malicious activity: ransomware deployment (encryptors and extortion), large-scale data exfiltration for sale or blackmail, privilege escalation and lateral movement across corporate networks, deployment of persistent backdoors and long-term C2 implants, web shells and remote code execution on public hosts, credential harvesting leading to account takeover and BEC/spear-phishing, pivoting into supply-chain partners, wiper/destructive attacks in high-impact scenarios, espionage or targeted surveillance by state-sponsored actors, DDoS or availability attacks to disrupt services, disinformation or influence operations using stolen context, and lower-probability abuses such as cryptojacking or resource abuse.
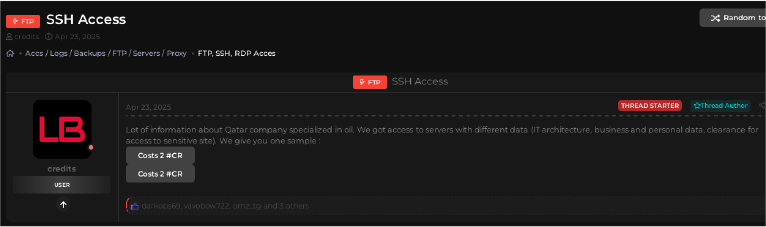
A user is advertising SSH access to a Qatar company, claiming entry to servers that contain infrastructure, business, personal, and clearance data, a serious operational compromise that can enable immediate data exfiltration, credential harvesting, and account takeover.
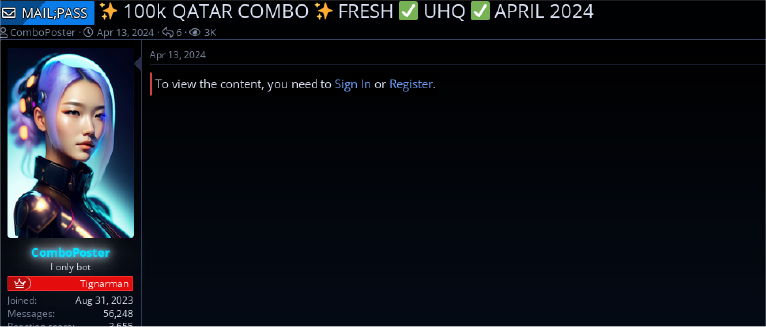
A user going by the name “comboposter” is selling 100,000 “Qatar combo” credentials (likely email:password pairs), which is concerning because such lists enable credential-stuffing and brute-force attacks against both private and government accounts. These combos can lead to account takeover, business-email-compromise, fraudulent transactions, unauthorized access to internal systems (including lateral movement), targeted phishing using real account context, and resale to other cybercriminals or initial-access brokers.
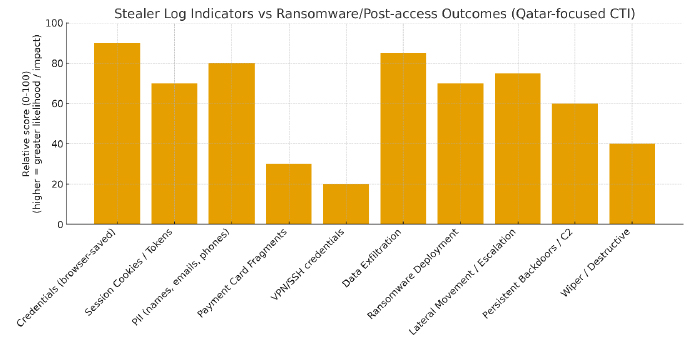
The chart illustrates how stealer logs and ransomware outcomes intersect. Stealer logs most often expose browser-saved credentials, session tokens, and PII, which adversaries can quickly weaponize for credential stuffing, account takeover, and phishing. Once such access is brokered or resold, ransomware groups frequently escalate privileges, exfiltrate sensitive data, deploy encryptors, or establish long-term persistence. This cycle shows how commodity data leaks feed directly into high-impact ransomware and extortion campaigns against regional organisations.
Ransomware
Both LockBit and Dispossessor have consistently included Qatar-based organisations among their targets in recent years. With the re-emergence of LockBit through its version 5 release, and Dispossessor’s return under the rebranded name “Radar”, these developments are concerning, as they indicate continued interest in the region. Qatar organisations must remain vigilant and proactive to stay ahead of potential unauthorized access and ransomware activity.
The cyber threat landscape around Qatar is intensifying, with multiple factors converging, including the sale of stolen data and initial access, the resurgence of ransomware groups like LockBit v5 and Dissposser/Radar, the circulation of large credential “combolists,” and the likelihood of hacktivist operations following geopolitical tensions. These trends demonstrate that Qatar organisations face risks not only from financially motivated cybercriminals but also from politically driven hacktivists and potentially state-sponsored actors.