


On 19 September 2025, multiple major European airports, including London Heathrow (LHR), Brussels (BRU), and Berlin Brandenburg (BER), experienced severe operational disruptions following a cyberattack that impacted check-in and boarding systems, resulting in widespread flight delays and cancellations. The incident has been attributed to an attack on Collins Aerospace’s MUSE check-in/boarding platform, highlighting how adversaries often exploit vulnerabilities in third-party suppliers rather than directly targeting the primary organization. While no threat actor has formally claimed responsibility, CYFIRMA Research assesses that Alixsec, Scattered Spider, and the Rhysida ransomware group are plausible actors, given their prior targeting patterns, history of high-profile disruptions, and demonstrated operational capabilities.
On 19–20 September 2025, a cyberattack targeting Collins Aerospace’s MUSE check-in and boarding platform resulted in widespread disruptions across London Heathrow (LHR), Brussels (BRU), and Berlin Brandenburg (BER) airports. Automated check-in, boarding, and baggage systems were rendered unavailable, forcing airports to revert to manual processes. The outage caused significant passenger delays, flight cancellations, and broader operational strain.
While early reporting attributed the incident to a “technical issue,” preliminary analysis suggests that Collins’ software platform was exploited, raising concerns of a supply-chain-style intrusion. No public indicators of ransomware encryption or data exfiltration have yet been confirmed, but the scale of disruption mirrors previous ransomware and state-sponsored campaigns against aviation.
This incident highlights the aviation sector’s vulnerability to cyber operations, particularly through supply-chain dependencies such as Collins Aerospace’s MUSE platform. Exploiting a shared platform offers adversaries a single point of failure to simultaneously disrupt multiple international airports — a strategy attractive to both ransomware operators seeking leverage and state actors pursuing geopolitical signaling.
Based on contextual, open-source, and dark web intelligence:
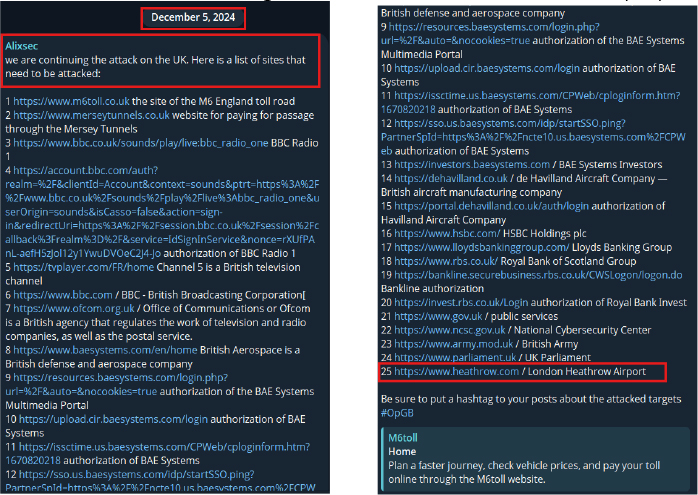
On December 5, 2024, the threat group Alixsec reportedly announced intentions to target multiple UK critical infrastructure sites, including transportation, media, banking, defense, and government organizations, with London Heathrow Airport mentioned. Their statements indicate a focus on high-value operational nodes, highlighting potential risks to airport operations, public services, and national infrastructure, underscoring the need for increased monitoring and defensive preparedness.
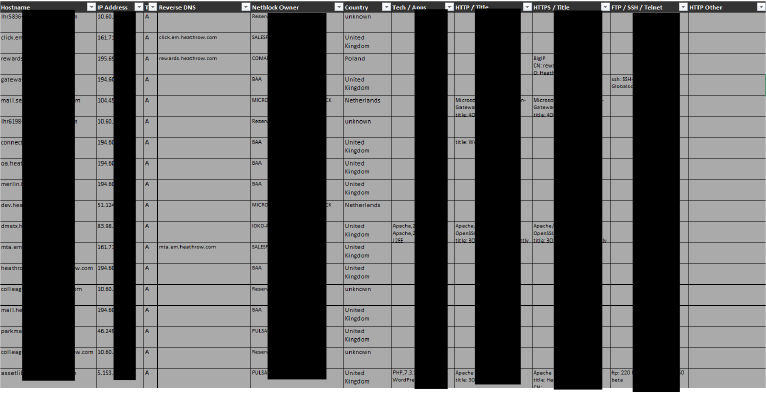
On December 22, 2024, an Excel file containing detailed information on Heathrow Airport infrastructure, including hostnames, IP addresses, technologies, and services, was reportedly posted on a Telegram group named Hydra Market 2 and later discussed on RaidForums in a thread forwarded from a Ransomware-as-a-Service (RaaS) group identified as Babuk Medieval. The dataset included internal and public-facing systems, such as email gateways, application servers, and network devices, highlighting the potential exposure of sensitive operational information.

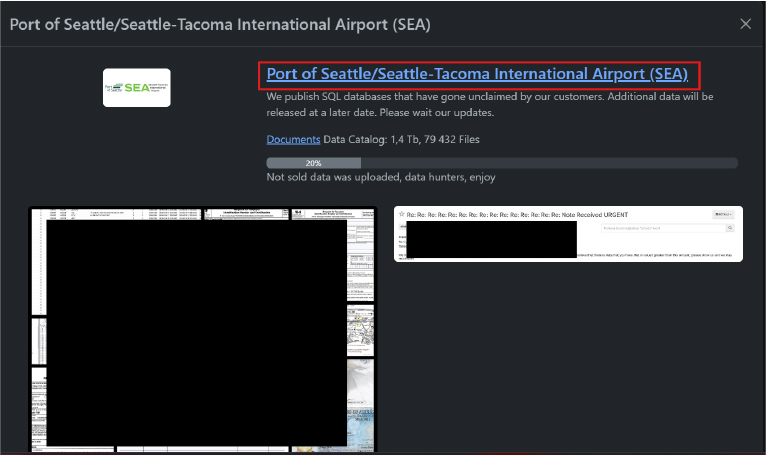
On 17 September 2024, the ransomware group Rhysida listed Port of Seattle / Seattle-Tacoma International Airport (SEA) on its leak site. The post claims the release of unclaimed customer SQL databases totalling 1.4 TB across 79,432 files, with a partial dataset (≈20%) already uploaded. The actor stated that additional data will follow. The Port of Seattle, a government agency formed in 1911, manages both Seattle’s seaport and airport and serves as a critical U.S. trade and transportation hub.
Scenario 1: Hacktivist / Ransomware Attribution
Scenario 2: State-Sponsored Attribution
Attribution Matrix (Intent vs Capability)
| Threat Actor | Type | Motivation | Aviation History | Assessment |
| Alixsec | Hacktivist | Ideological (anti-West/Pro-Palestine) | Threatened aviation (Dec 2024), no confirmed attacks | Intent only |
| Rhysida | Ransomware | Financial disruption, extortion | Seattle-Tacoma Airport attack (Aug 2024) | Proven capability |
| APT28 | State-backed (Russia) | Strategic disruption, espionage | Past transport/aviation targeting | High capability |
| APT33 | State-backed (Iran) | Regional influence, disruption | Known aviation sector intrusions | High capability |
| Lazarus | State-backed (North Korea) | Financial and geopolitical | Targeted transport/finance | High capability |
Alixsec: Alixsec is a pro-Palestinian hacktivist group active on Telegram (alixsecenglish), focused on politically motivated cyber disruptions targeting Western-aligned nations. While the group has threatened aviation attacks (Dec 2024), it has no proven capability in executing high-impact operations against critical infrastructure.
Rhysida Ransomware Group: Rhysida is a financially motivated ransomware group targeting critical infrastructure, particularly aviation and ports. The group is capable of encrypting operational systems and causing prolonged disruptions, as seen in the August 2024 Seattle-Tacoma International Airport attack.
APT28 (Fancy Bear): APT28 is a Russian state-sponsored group linked to the GRU, conducting advanced cyber operations against transport, government, and critical infrastructure. Their campaigns combine intelligence collection and disruption, leveraging sophisticated malware and persistent access techniques.
APT33 (Iran): APT33 is an Iranian state-backed actor targeting aviation and energy sectors for strategic disruption. The group employs malware campaigns, spear-phishing, and operational technology (OT) exploitation to achieve regional influence and compromise sensitive systems.
Lazarus Group (North Korea): Lazarus Group is a North Korean state-sponsored actor conducting financially and strategically motivated cyber operations. They target financial institutions, transport, and critical infrastructure globally, blending ransomware, wipers, and espionage campaigns.
Potential MITRE Framework
| Tactic | Technique ID | Technique Name | Threat Actors |
| Initial Access | T1195 | Supply Chain Compromise | Rhysida, APT28, APT33, Lazarus Group |
| Initial Access | T1566 | Phishing | APT33 |
| Initial Access | T1204 | User Execution | APT33 |
| Execution | T1486 | Data Encrypted for Impact | Rhysida, Lazarus Group |
| Execution | T1499 | Endpoint Denial of Service | Alixsec |
| Execution | T1491 | Defacement / Wiper | Alixsec, Lazarus Group |
| Persistence | T1078 | Valid Accounts | APT28, APT33 |
| Persistence | T1021 | Remote Services | APT28, APT33 |
| Privilege Escalation | T1078 | Valid Accounts | APT28, APT33 |
| Defense Evasion | T1070 | Indicator Removal | Rhysida |
| Defense Evasion | T1027 | Obfuscated Files or Information | Lazarus Group |
| Impact | T1489 | Service Stop | Rhysida |
| Impact | T1486 | Data Encrypted for Impact | Rhysida, Lazarus Group |
| Impact | T1491 | Defacement | Alixsec, Lazarus Group |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | APT28, APT33 |
| Exfiltration | T1530 | Data from Cloud Storage | Alixsec, Rhysida |
As of now, there are no known Indicators of Compromise (IOCs) associated with this incident, as no group or individual has claimed responsibility for the attack. Nevertheless, we continue to monitor the situation closely.
While the suspected attribution for the September 2025 airport disruptions remains pending, CYFIRMA Research assesses Alixsec, Scattered Spider, and the Rhysida ransomware group as plausible actors, based on their prior targeting statements, history of high-visibility attacks, and operational capabilities. The incident highlights systemic vulnerabilities in service providers supporting critical airport functions and underscores the need for proactive cyber defenses, continuous threat monitoring, and cross-border coordination to mitigate the risks posed by these threat actors.
Immediate Recommendations
1. Vendor Access Hardening
2. Network Segmentation & Containment
3. Backups & Fallback Procedures
4. Threat Hunting & Monitoring
5. Access & Account Security
6. System & Email Security
7. Training & Awareness
8. Third-Party Oversight