


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type:
Ransomware
Target Technologies:
Windows
Target Geographies:
Iran, Germany, USA, Turkey, and Ireland
Target Industries:
Real Estate & Construction, Public Services, Healthcare, and Manufacturing
Introduction
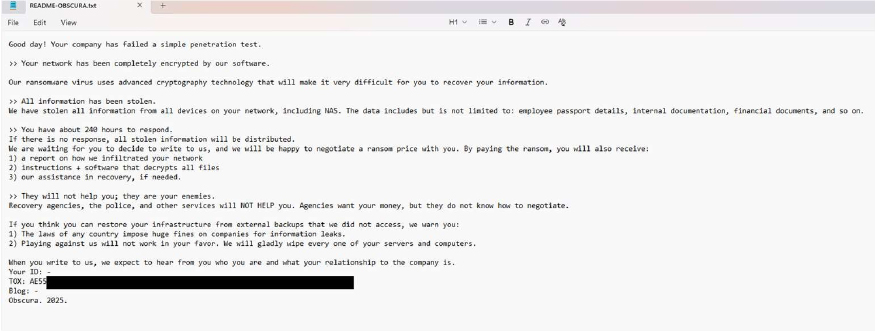
CYFIRMA Research and Advisory Team has found Obscura Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Obscura Ransomware
Researchers discovered a previously unseen ransomware variant called Obscura, first observed in late August 2025. The ransomware drops a ransom note named README_Obscura.txt, which repeatedly references the Obscura name. In at least one intrusion, the ransomware executable a Go binary was deployed across multiple hosts and staged within the domain controller’s SYSVOL scripts directory, using a filename mimicking the victim’s domain to evade suspicion. Due to limited visibility into the attack, the initial access vector remains unknown, but findings indicate the malware was tailored to blend into the victim environment and facilitate rapid propagation.


The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1074 | Data Staged |
| Command and Control | T1090 | Proxy |
| Impact | T1486 | Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Analyst assessment suggests that the Obscura ransomware operation is in its early stages but poised for rapid evolution. The use of a Go-based binary and deployment via the domain controller’s SYSVOL scripts indicates a focus on scalability and domain-wide impact traits consistent with groups seeking to professionalize. Over time, Obscura may adopt double extortion tactics, establish dedicated leak sites, and expand its targeting across industries beyond its initial victims. The choice of Go also suggests cross-platform ambitions, potentially enabling future Linux variants. If the operators mature their tradecraft and distribution methods, Obscura could evolve into a Ransomware-as-a-Service (RaaS) offering, making it a sustained and adaptable threat in the global ransomware ecosystem.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Type: Loader | Objectives: Malware Distribution |Target Technology: Windows OS | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “HijackLoader” is trending.
Overview of HijackLoader Malware
Researchers identified a spike in recent activity linked to HijackLoader, a malware family that first emerged in the latter half of 2023 and has steadily gained traction since. Initially recognized for its ability to deliver additional payloads, it quickly evolved into a Malware- as-a-Service platform supporting financially motivated operations worldwide. The latest wave of attacks, observed since June 2025, shows how attackers have been using tactics like Clickfix to lure victims into downloading malicious installers. These installers execute HijackLoader and deploy secondary threats such as DeerStealer.
Combined with earlier distribution methods—ranging from SEO-poisoned websites and fake installers to malvertising and pirated content—these campaigns demonstrate the loader’s ability to reach victims through multiple entry points. As HijackLoader continues to refine its approach, it has established itself as more than just a delivery tool. Its sophisticated evasion capabilities and adaptability make it a persistent threat.
Technical Analysis
The initial access starts with a CAPTCHA-based social-engineering campaign called Clickfix. This HTA file serves as the initial downloader and launches successive, heavily obfuscated PowerShell stages that rebuild themselves at runtime and fetch the next component from the web. Analysis shows multiple layers of packed code and environment checks designed to detect virtual machines and frustrate analysis; the final stages then unpack an executable and a protected DLL before reaching out to remote servers. Although the original command links are no longer reachable, the observable behavior matches long-standing loader patterns: a staged delivery that ultimately pulls down information-stealing malware (campaigns have previously delivered families such as NekoStealer and Lumma). In short, the chain relies on social trickery up front and multiple stealthy stages before the final infostealer payload is deployed.
Following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.002 | Phishing: Spearphishing Link |
| Initial Access | T1189 | Drive-by Compromise |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1211 | Exploitation for Defense Evasion |
| Defense Evasion | T1036 | Masquerading |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Collection | T1056 | Input Capture |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as HijackLoader continues to evolve, its campaigns may increasingly affect digital ecosystems at large, including personal devices, cloud services, and online platforms, making everyday users more vulnerable to data theft and account compromise. The malware’s adaptability could lead to more complex, multi-stage attacks that evade traditional security measures, resulting in broader disruptions and potential loss of trust in online services. In addition, the proliferation of sophisticated social-engineering tactics may normalize deceptive practices, creating an environment where digital interactions are more frequently exploited and harder to navigate safely.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule HijackLoader_Indicators
{
meta:
description = “Detects HijackLoader malware indicators” author = “CYFIRMA”
malware_family = “HijackLoader”
strings:
// SHA256 File Hashes
$sha256_1 = “1b272eb601bd48d296995d73f2cdda54ae5f9fa534efc5a6f1dab3e879014b57”
$sha256_2 = “37fc6016eea22ac5692694835dda5e590dc68412ac3a1523ba2792428053fbf4”
$sha256_3 = “3552b1fded77d4c0ec440f596de12f33be29c5a0b5463fd157c0d27259e5a2df”
$sha256_4 = “782b07c9af047cdeda6ba036cfc30c5be8edfbbf0d22f2c110fd0eb1a1a8e57d”
$sha256_5 = “921016a014af73579abc94c891cd5c20c6822f69421f27b24f8e0a044fa10184”
$sha256_6 = “e2b3c5fdcba20c93cfa695f0abcabe218ac0fc2d7bc72c4c3af84a52d0218a82”
$sha256_7 = “52273e057552d886effa29cd2e78836e906ca167f65dd8a6b6a6c1708ffdfcfd”
$sha256_8 = “c03eedf04f19fcce9c9b4e5ad1b0f7b69abc4bce7fb551833f37c81acf2c041e”
$sha256_9 = “D0068b92aced77b7a54bd8722ad0fd1037a28821d370cf7e67cbf6fd70a608c4”
$sha256_10 = “50258134199482753e9ba3e04d8265d5f64d73a5099f689abcd1c93b5a1b80ee”
// IP Addresses
$ip_1 = “91.212.166.51”
$ip_2 = “37.27.165.65”
// Domains
$domain_1 = “cosi.com.ar”
// URLs
$url_1 = “https://1h.vuregyy1.ru/3g2bzgrevl.hta”
$url_2 = “https://rs.mezi.bet/samie_bower.mp3”
$url_3 = “http://77.91.101.66/”
condition:
any of ($sha256*) or any of ($ip*) or
any of ($domain*) or any of ($url*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Tracking Mustang Panda: Expansion of Cyber Capabilities and Regional Focus
About the Threat Actor
Mustang Panda, a Chinese state-linked espionage group active since at least 2012, conducts disciplined, geopolitically driven intelligence operations characterized by rapid tradecraft evolution and long-running persistence. Its campaigns typically begin with targeted spear-phishing—politically themed messages carrying ZIP, RAR, LNK, or URL lures—then deploy multi-stage payloads (initial loaders or stagers that deliver backdoors, reverse shells, and lateral-movement tools). Common toolsets include PlugX, Poison Ivy, ToneShell, StarProxy, Claimloader, and SplatCloak, with operators favouring DLL sideloading and encrypted C2 channels for stealth and persistence; some operations have also used infected USB drives to propagate. Mustang Panda is a capable, adaptive actor that blends careful targeting with modular malware to maintain long-term access to high-value networks.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023- 4966 | NetScaler ADC and NetScaler Gateway | 7.5 | link |
| CVE-2021- 1675 | Microsoft Windows | 7.8 | link1, link2, link3 |
| CVE-2021-40444 | Microsoft Windows | 7.8 | link1, link2, link3 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1608 | Stage Capabilities |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1588.004 | Obtain Capabilities: Digital Certificates |
| Resource Development | T1583.002 | Acquire Infrastructure: Domains |
| Initial Access | T1091 | Replication Through Removable Media |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1047 | Windows Management Instrumentation |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1546.003 | Event Triggered Execution: Windows Management Instrumentation Event Subscription |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1546.003 | Event Triggered Execution: Windows Management Instrumentation Event Subscription |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1480 | Execution Guardrails |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.007 | Masquerading: Double File Extension |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1027.016 | Obfuscated Files or Information: Junk Code Insertion |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1218.004 | System Binary Proxy Execution: InstallUtil |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.014 | System Binary Proxy Execution: MMC |
| Defense Evasion | T1218.007 | System Binary Proxy Execution: Msiexec |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Collection | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1119 | Automated Collection |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1219.002 | Remote Access Tools: Remote Desktop Software |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1102 | Web Service |
| Command and Control | T1090 | Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Exfiltration | T1052.001 | Exfiltration Over Physical Medium: Exfiltration over USB |
Latest Developments Observed
The threat actor is suspected of deploying an advanced variant of the Toneshell backdoor capable of evading conventional detection systems, along with a newly identified USB-propagating malware, SnakeDisk, designed to specifically target devices in Thailand. The campaign’s primary objective appears to be the exfiltration of sensitive information.
ETLM Insights
Mustang Panda is a China-linked espionage group engaged in long-term intelligence collection targeting governments, NGOs, and strategic industries across Central, East, and Southeast Asia. The group employs sophisticated tactics, including localized spear- phishing campaigns with geopolitical themes, multi-stage deployment chains, USB/removable media propagation, and custom malware implants. Their operations are characterized by stealth and persistence, enabling the gradual exfiltration of sensitive and strategic intelligence. Mustang Panda’s activities are assessed to align with broader state intelligence objectives and long-term strategic ambitions designed to challenge U.S. global leadership.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule MustangPanda_Threat_Indicators
{
meta:
description = “Detects presence of indicators related to threat activity using CVEs, IPs, domains, and suspicious executables”
author = “CYFIRMA” date = “2025-09-15”
threat_actor = “Likely Mustang Panda or related threat group”
strings:
// Suspicious executables
$exe1 = “myp0912.exe” nocase
$exe2 = “rens.exe” nocase
$str1 = “eqfvkn”
// Suspicious domains
$domain1 = “www.profile-keybord.com”
$domain2 = “www.dest-working.com”
$domain3 = “www.ynsins.com”
$domain4 = “www.aihkstore.com”
$domain5 = “jcswcd.com”
// CVE references in exploits
$cve1 = “CVE-2023-4966”
$cve2 = “CVE-2021-1675”
$cve3 = “CVE-2021-40444”
// IP addresses (can appear in config files, C2 beacons, etc.)
$ip1 = “139.59.46.88”
$ip2 = “45.152.66.25”
$ip3 = “103.159.132.91”
$ip4 = “23.216.147.76”
condition:
any of ($exe*) or any of ($domain*) or any of ($cve*) or any of ($ip*) or
$str1
}
Strategic
Management
Tactical
China-Linked APT41 Hackers Target US Trade Officials During 2025 Negotiations.
The House Select Committee on China has issued a formal advisory warning of an “ongoing” series of highly targeted cyber espionage efforts related to the People’s Republic of China (PRC), amidst tense US-China trade talks.
These campaigns seek to compromise organizations and individuals involved in U.S.- China trade policy and diplomacy, including U.S. government agencies, U.S. business organizations, D.C. law firms and think tanks, and at least one foreign government, according to the committee.
The committee noted that suspected Chinese threat actors impersonated Republican Party Congressman John Robert Moolenaar in phishing emails sent to trusted counterparts in order to deceive and trick them into opening files and links that would grant them unauthorized access to their systems and sensitive information without their knowledge.
The attacks’ ultimate purpose was to steal important data by exploiting software and cloud services to hide evidence of their activity, a method frequently used by state- sponsored hackers to avoid detection.
The attack is thought to be the work of APT41, a prominent hacking group renowned for targeting many industries and locations for cyber espionage.
ETLM Assessment:
By impersonating Rep. Moolenaar (R-MI), a known Beijing critic, the attackers created urgency and legitimacy that encouraged fast responses.
Political communication goes beyond official government equipment and accounts. Sophisticated enemies recognize this truth and deliberately exploit it. By impersonating trustworthy officials via personal or non-official channels, attackers circumvent established security protections while increasing legitimacy.
North Korean Hackers Used ChatGPT to Help Generate Deepfake ID
A suspected North Korean state-sponsored hacking group used ChatGPT to build a deepfake of a military ID paper before attacking a target in South Korea.
The notorious group, Kimsuky, is suspected of being tasked by the North Korean leadership with gathering worldwide intelligence, and it has been tied to prior surveillance operations against South Korean targets.
The attackers employed an artificial intelligence technique to build a false draft of a South Korean military identification card in order to create a realistic-looking image that would make a phishing effort appear more believable. Instead of including an actual image, the email contained a link to malware capable of extracting data from the recipients’ devices. The number of victims violated was not immediately clear.
The pattern indicates that attackers can use emerging AI during the hacking process, such as attack scenario preparation, malware development, tool building, and impersonating job recruiters.
During their investigation into the bogus identification document, researchers used ChatGPT. Because duplication of government IDs is unlawful in South Korea, ChatGPT first refused to create an ID. But changing the prompt allowed them to get around the prohibition.
ETLM Assessment:
Researchers’ July discoveries are the most recent example of suspected North Korean spies using AI to acquire intelligence. In August, researchers reported that North Korean hackers used the Claude Code program to be hired and work remotely for US Fortune 500 software companies. In that case, Claude assisted them in creating sophisticated phony identities, passing coding tests, and performing actual technical work once employed.
According to American officials, North Korea has been attempting to obtain intelligence on behalf of the Pyongyang regime through cyberattacks, cryptocurrency theft, and IT contractors for quite some time. According to the US administration, these approaches are also employed to raise funds to assist the regime in circumventing international sanctions and developing its nuclear weapons programs.
The request for comment was not immediately responded to by OpenAI personnel. In February, the business announced that it had suspended suspected North Korean accounts that had used the service to construct bogus résumés, cover letters, and social media posts in an attempt to attract people for their schemes.
Medusa Ransomware Impacts TEAM GROUP
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, TEAM GROUP (https[:]//www[.]teamgroup[.]co[.]th/), was compromised by Medusa Ransomware. TEAM GROUP is a leading integrated consulting firm in Thailand and across the region, providing extensive expertise in building and infrastructure, water resources, environmental management, transportation and logistics, and power and energy. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 2.25 TB.
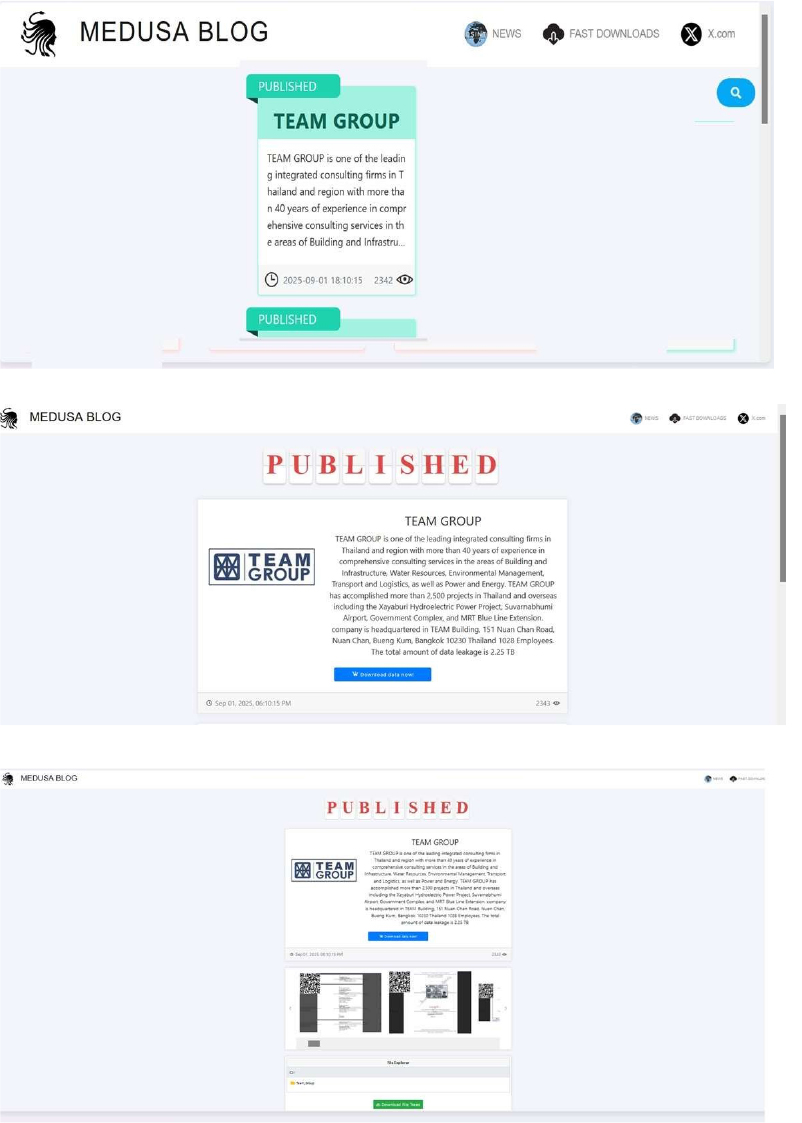
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Medusa Ransomware continues to pose a significant threat across various sectors. The group’s sophisticated tactics and aggressive demands highlight the need for organizations to enhance their cybersecurity measures, including regular updates, employee training on phishing recognition, and robust incident response plans to mitigate risks associated with ransomware attacks.
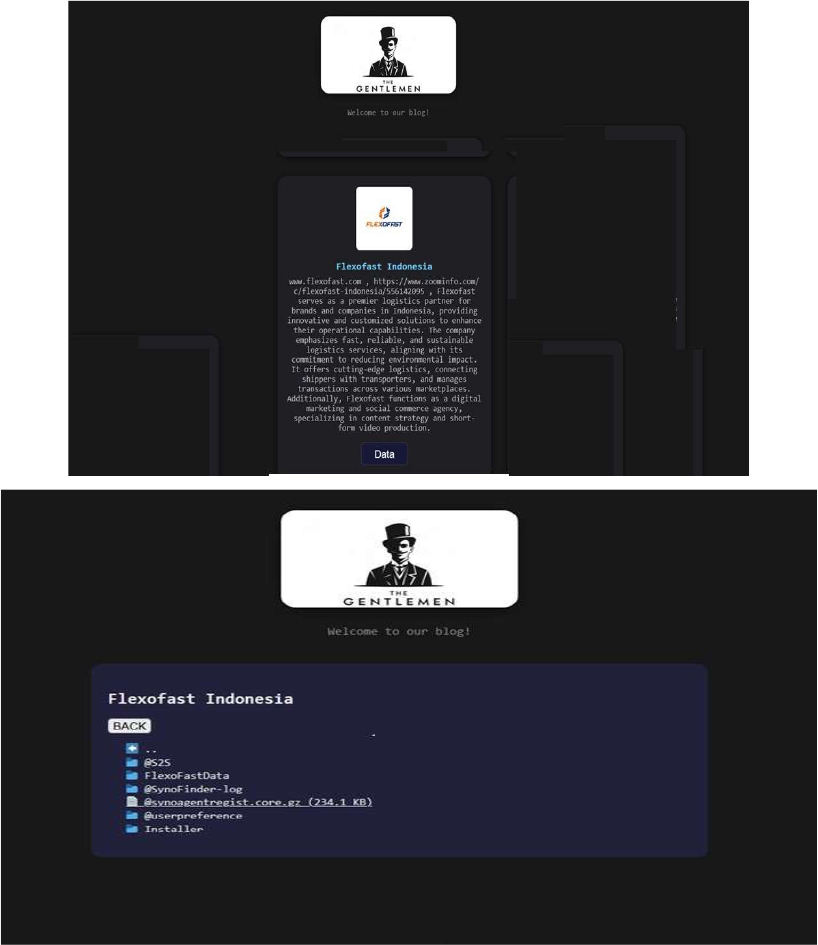
The Gentlemen Ransomware Impacts Flexofast Indonesia
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia, Flexofast Indonesia (https[:]//www[.]flexofast[.]com/), was compromised by the Gentlemen Ransomware.
Flexofast serves as a premier logistics partner for brands and companies in Indonesia, providing innovative and customized solutions to enhance their operational capabilities. The compromised data includes confidential and sensitive information belonging to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen ransomware group exemplifies the rising sophistication and persistence of modern ransomware actors, necessitating tailored enterprise defenses and vigilant threat monitoring.
Vulnerability in Spring Security
Relevancy & Insights:
The vulnerability exists since the annotation detection mechanism does not correctly resolve annotations on methods within type hierarchies with a parameterized super type with unbounded generics.
Impact:
A remote attacker can gain access to sensitive information.
Affected Products:
https[:]//spring[.]io/security/cve-2025-41248
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
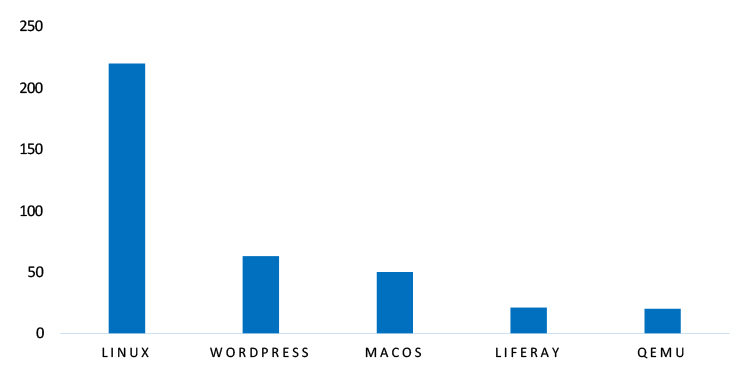
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
TOP 5 MOST AFFECTED TECHNOLOGIES OF THE WEEK
ETLM Assessment
Vulnerabilities in Spring Security, the powerful authentication and access-control framework for Java applications, can expose systems to serious risks. Exploitation of such flaws may lead to issues like authentication bypass, privilege escalation, session fixation, or exposure of sensitive data.
Killsec Ransomware attacked and published the data of Nathan and Nathan
Summary:
Recently, we observed that Killsec Ransomware attacked and published the data of Nathan and Nathan (https[:]//www[.]nathanhr[.]com/) on its dark web website. Nathan and Nathan is a global leader in delivering customized HR, staffing, and technology solutions that enable businesses to excel in today’s dynamic market.
Operating across 45+ countries, Nathan offers expertise in managed HR services, staffing, PEO/EOR solutions, and advanced AI-driven HR technology. With a strong focus on compliance, flexibility, and efficiency, Nathan helps organizations optimize operations, attract top talent, and scale seamlessly. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
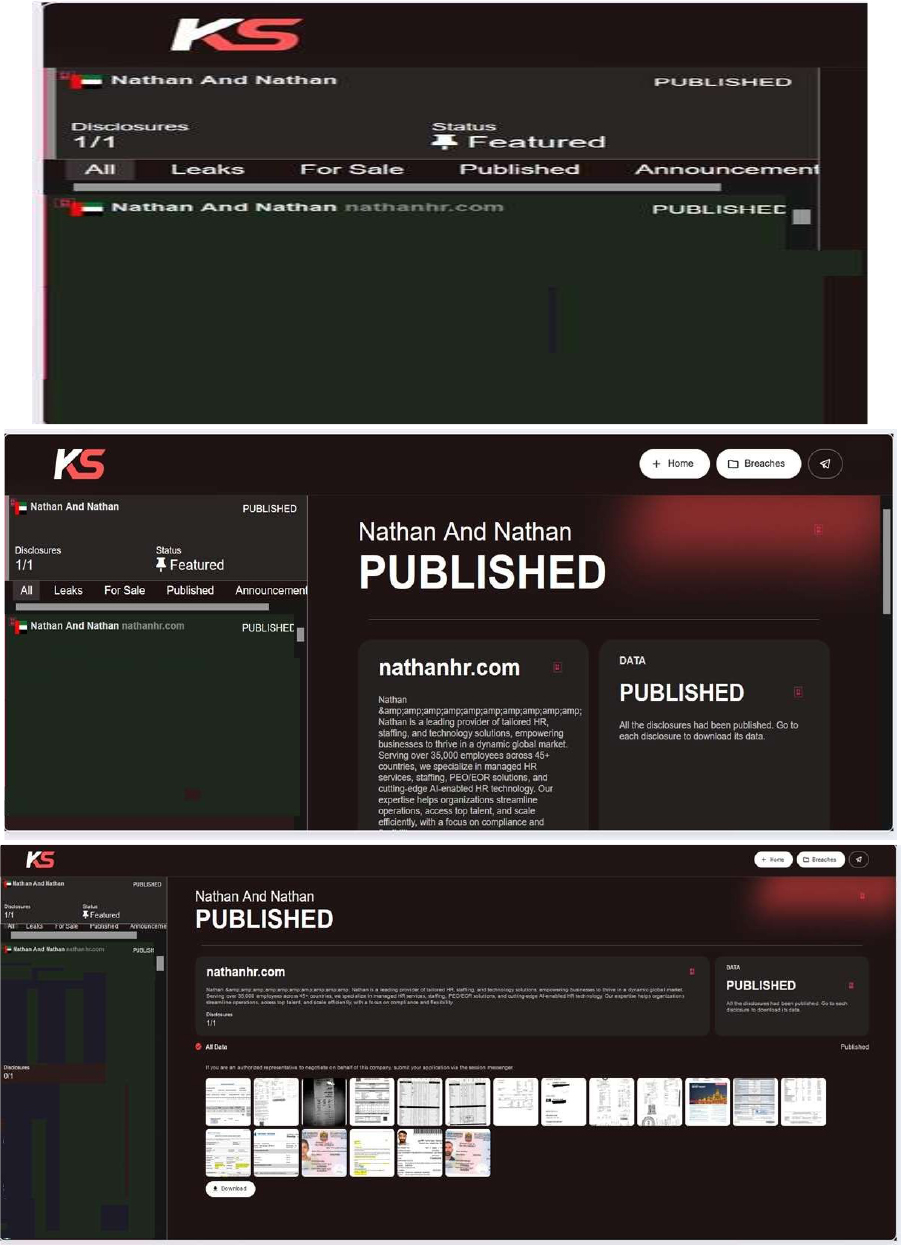
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
PS&KP Motor’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor has allegedly leaked the database of PS&KP Motor, a car dealership operating in Thailand. The breach has exposed a significant amount of sensitive personal and vehicle information, raising serious concerns about the privacy and security of the dealership’s customers.
PS&KP Motor is a local automotive business in Thailand involved in the sale of vehicles, and the leaked data appears to be related to its customer relationship management and sales operations.
The compromised data, displayed in screenshots from the database, allegedly contains a wide array of confidential information. The exposure of such detailed records could place affected individuals at a high risk of identity theft, targeted phishing campaigns, and other fraudulent activities. The inclusion of both personal identifiers and specific vehicle details provides malicious actors with a powerful combination of data for sophisticated scams.
An analysis of the samples shared by the threat actor reveals that the following information has allegedly been compromised:
Dubai’s Ports Customs, and Free Zone Corporation’s (PCFC) Data Advertised on a Leak Site
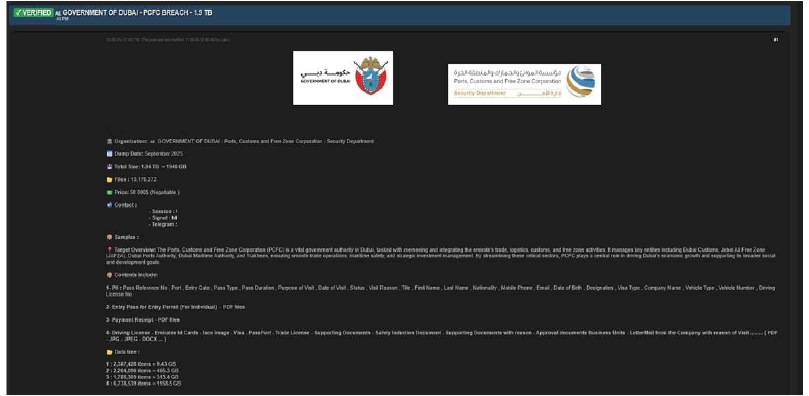
Summary:
The CYFIRMA Research team has identified that a threat actor “Kazu” has allegedly breached the Ports, Customs and Free Zone Corporation (PCFC), a critical government authority based in Dubai, United Arab Emirates. The PCFC is a cornerstone of the emirate’s economy, responsible for integrating and overseeing trade, logistics, customs, and free zone activities, including major entities like Dubai Customs and the Jebel Ali Free Zone (JAFZA). According to a post on a dark web forum, the cybercriminal claims to have exfiltrated 1.94 TB of data from the corporation’s Security Department during September 2025 and is offering it for sale for $50,000.
The scale of the alleged breach is substantial, reportedly involving over 13 million files. The threat actor provided a detailed list of the types of sensitive information contained within the stolen dataset, which poses a significant risk to individuals and businesses associated with the PCFC. The contents allegedly include a vast amount of Personally Identifiable Information (PII) and official documentation. The specific data types listed for sale are:

Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Kazu” has recently emerged as a notably active group engaged in data leak activities. Credible sources have tied the group to multiple security breaches involving unauthorized system access and attempts to sell stolen data on dark web marketplaces. The group’s ongoing operations illustrate the persistent and escalating cyber threats stemming from underground forums. These incidents reinforce the critical need for organizations to bolster cybersecurity through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
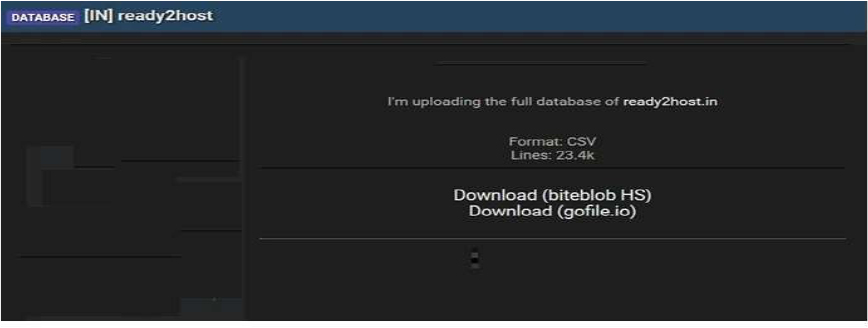
The CYFIRMA Research team observed that Ready2Host, a web hosting services provider based in India, has allegedly become the victim of a significant data breach. A threat actor recently posted on a dark web forum, claiming to have exfiltrated and leaked the company’s entire customer database. The leaked data, shared publicly in a CSV file format, reportedly contains 23,400 lines of customer information, exposing the company’s clientele to potential cyber threats.
An initial analysis of the data sample suggests that sensitive customer information has been compromised. While the passwords in the database appear to be hashed, the exposure of other personally identifiable information (PII) puts customers at risk of phishing, spam, and targeted social engineering attacks. The exposed data allegedly includes:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
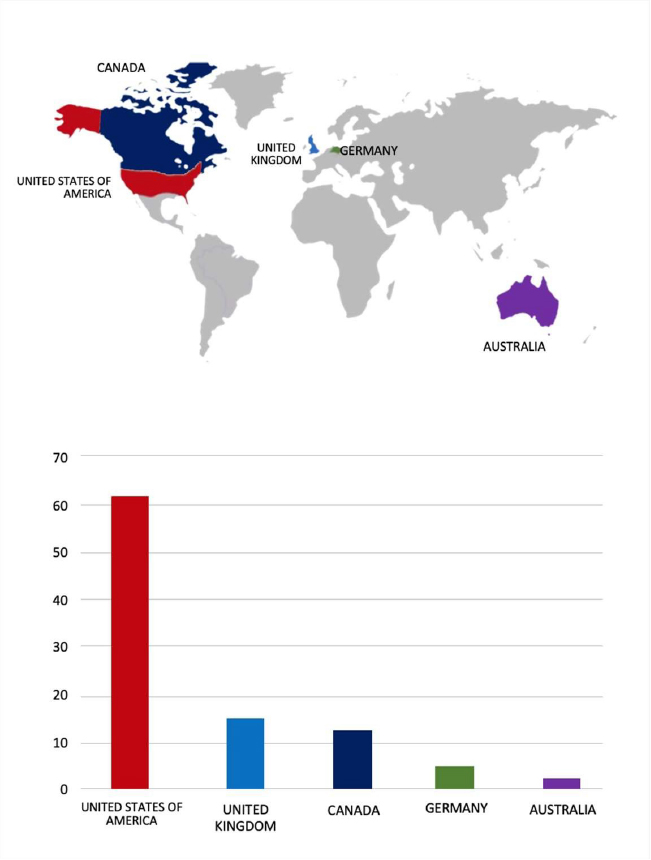
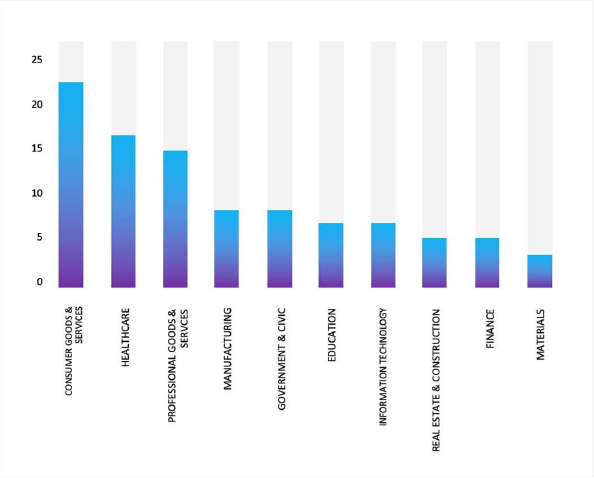
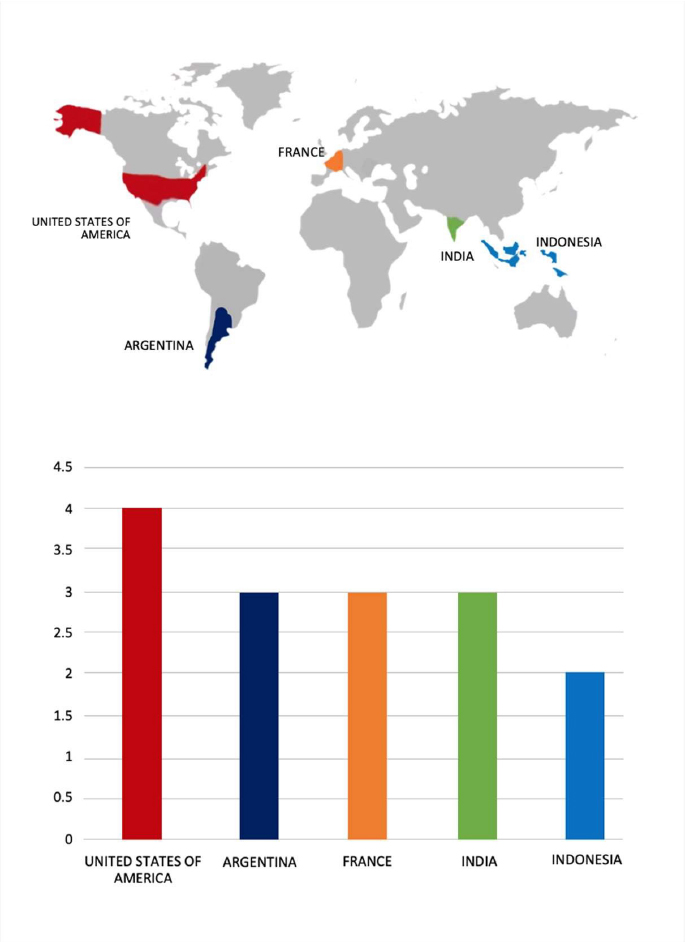
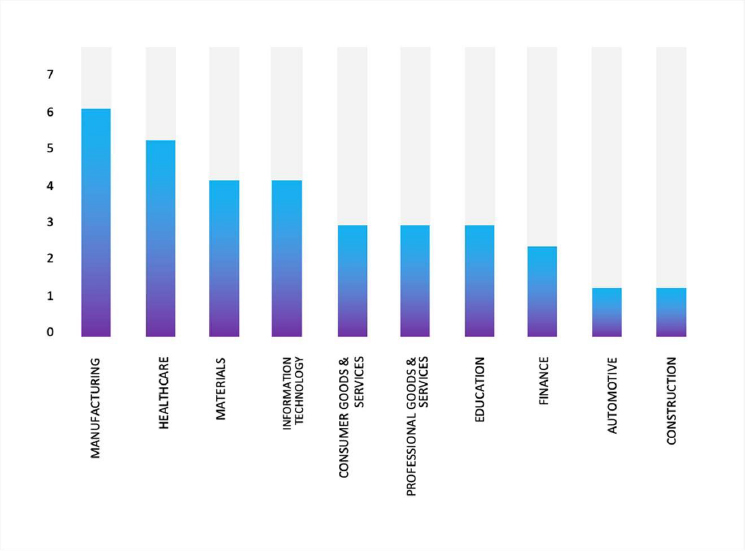
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.