


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found EXTEN Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
EXTEN Ransomware.
Researchers identified a new ransomware variant called EXTEN. This malicious program encrypts files on compromised systems and alters their filenames by appending the “.EXTEN” extension. All affected files are rendered inaccessible after encryption. Once the encryption process is complete, EXTEN generates a ransom note titled “readme.txt.”
The ransom note states that all data has been encrypted and can only be recovered by paying a ransom of 5 Bitcoin (BTC). The message provides a Bitcoin wallet address for the payment and instructs the victim to make further contact through the email address.
Victims are warned that failure to pay within five days will result in the public release of stolen data.
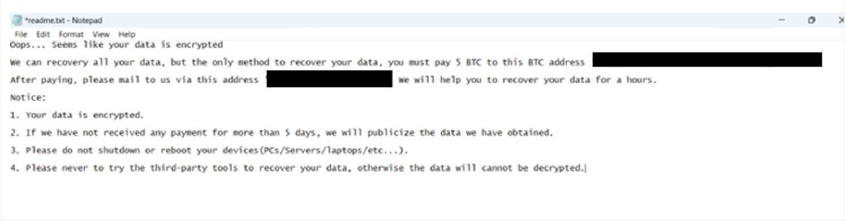
The ransom note also specifies several conditions for the victim. It explicitly instructs not to shut down or reboot infected devices and prohibits the use of recovery tools, claiming these actions could make decryption impossible.
Combined with the encryption behavior and the appended file extension, these elements define the operational characteristics of the EXTEN ransomware.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1614 | System Location Discovery |
| Command and Control | T1071 | Application Layer Protocol |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of the EXTEN ransomware campaign highlights the ongoing evolution of ransomware groups in both scale and tactics. The appearance of this variant reflects a continuing trend where adversaries refine their methods to maximize disruption and leverage data exposure as an additional pressure mechanism. This suggests that such threats will remain a dominant force in the cybercrime ecosystem, targeting organizations across diverse industries that rely heavily on Windows-based infrastructure.
Given the ransom demands in cryptocurrency and the threat of data leakage, the operators are not only seeking direct financial gain but also exploiting the fear of reputational and regulatory damage. This dual-extortion model is becoming a defining characteristic of modern ransomware incidents, and EXTEN’s activity aligns with that trajectory. The ability to deny victims access to recovery options further increases the likelihood of payment, making these campaigns particularly damaging for enterprises with limited resilience strategies.
Looking forward, the tactics demonstrated in this campaign are expected to inspire copycat actors and the development of more sophisticated variants. Organizations can anticipate a rise in ransomware activity that blends traditional file encryption with aggressive data-handling practices, extending the impact beyond immediate financial losses to long-term operational and brand consequences.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Botnet | Objectives: Data Theft, Remote control, Data Exfiltration |Target Technologies: Windows OS, Web Browsers | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “NightshadeC2” is trending.
Overview of NightshadeC2 Malware
Researchers have identified NightshadeC2, a recently discovered botnet that leverages a loader designed to bypass security checks. It employs a method known as UAC Prompt Bombing to evade detection and make analysis more difficult. It has been observed in both C and Python variants, each maintaining communication with its operators through different channels. Once deployed, NightshadeC2 provides attackers with a wide range of capabilities, including remote command execution, reverse shell access, downloading and running additional files, self-deletion, keylogging, clipboard data collection, browser credential theft, screen capture, and hidden browsing activity. These functions make it a flexible tool for espionage, data theft, and persistent control over infected systems. The appearance of NightshadeC2, with its dual C and Python builds, highlights how threat actors continue to experiment with diverse approaches to create adaptable and resilient botnets capable of evading defenses and expanding their reach.
Attack Method
The NightshadeC2 campaign begins with deceptive entry points designed to trick victims into running malicious code. In this campaign, attackers leveraged the ClickFix vector, where individuals are shown a fake captcha and then prompted to enter a command into the Windows Run dialog. Alongside this, researchers also found the malware distributed through trojanized versions of popular software tools, including well-known programs like VPN clients, system utilities, and file search applications.
With initial access secured, the threat progresses through multiple stages to deliver its payload. The loader stage is responsible for downloading and activating the core malware. To secure its position, it repeatedly pushes a User Account Control (UAC) prompt until the victim approves, a tactic known as UAC Prompt Bombing. This not only forces user compliance but also sidesteps Microsoft Defender protections and disables analysis environments, allowing the malware to slip through unnoticed. Persistence is then achieved by modifying registry entries, ensuring the malware launches automatically on system restart.
The payload stage delivers the full NightshadeC2 botnet. At this point, it gathers basic information about the device—such as system details, user identity, and location—before reporting back to its command-and-control server. Once communication is established, NightshadeC2 enables attackers to take complete control, with capabilities including keylogging, clipboard monitoring, reverse shells, hidden browsing, and credential theft from major web browsers. While most samples observed are compiled in C, a Python variant has also been identified, offering a slimmer but still functional version of the malware. Some versions even leverage Steam profiles to disguise and update their command servers dynamically.
Further analysis revealed that NightshadeC2 employs multiple privilege escalation tricks, including older bypasses of Windows’ UAC mechanism, making it adaptable across different operating system versions. These combined methods—stealthy entry, forced privilege acceptance, layered execution, and versatile payload delivery—demonstrate the botnet’s sophisticated approach to infiltration and persistence.
Following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1204 | User Execution |
| Execution | T1129 | Shared Modules |
| Execution | T1106 | Native API |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1571 | Non-Standard Port |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as malware like NightshadeC2 continues to evolve, techniques such as ClickFix could turn ordinary digital interactions into hidden points of compromise, where even a routine captcha or prompt might trigger infection. By exploiting familiar tools and everyday actions, attackers may increasingly spread threats across interconnected systems, software supply chains, and widely used platforms, targeting multiple browsers and potentially reaching users in broader regions. Over time, the combination of stealthy malware and deceptive techniques could reshape how people interact with digital interfaces, making awareness of hidden threats an essential part of navigating everyday technology.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule NightshadeC2_Indicators
{
meta:
description = “Detects NightshadeC2 malware indicators” author = “CYFIRMA”
malware_family = “NightshadeC2”
strings:
// SHA256 File Hashes
$sha256_1 = “8940944e4abc600b283703876def0403160a5109abdbcb9e97c488dc3cc59b94”
$sha256_2 = “39b40746de01af66c0e5ce5888df4c42e474adcdb4301275b1474423d7a0ff1f”
$sha256_3 = “f2ff4cbcd6d015af20e4e858b0f216c077ec6d146d3b2e0cbe68b56b3db7a0be”
$sha256_4 = “0c08b5f3c24841d5fe02ddebdcf4707a75c790916c3ad4c769108241ddf999e4”
$sha256_5 = “c4fd98db8d8181d949ee4ff47991dda70f73b47c72104aa519150223dd8d3588”
$sha256_6 = “cf0c7e0f3c3ea60da7bfe779f09d32b441d5089c905a5d905253e2f4b2b202fd”
$sha256_7 = “0fd7eb57f5f9d817dd497c1ce3be0791f5e798077f8dc2c3a4e2b2b0b0bdc2c6”
$sha256_8 = “1178fa21928e5aac0f320e18bfb15603e00d3b8874719f4e74dd4f49db6dc5a8”
$sha256_9 = “1ff6ee23b4cd9ac90ee569067b9e649c76dafac234761706724ae0c1943e4a75”
$sha256_10 = “26a5e18d6ac86a865250452528664d4cde74187d741fcf98370efb34d4219490”
$sha256_11 = “2fcb76dfdfcd390658bbc032faafef607804d5d4a2f1c0005f274ab2e06d8af4”
$sha256_12 = “3dd877835c04fde3f2d14ce96f23a1c00002fefa9d731e8c4ce3b656aac90063”
$sha256_13 = “420f13538c0c2620eba396e96afdf36430b2618d7d215e96c81444379ab8a7bc”
$sha256_14 = “5a741df3e4a61b8632f62109a65afc0f297f4ed03cd7e208ffd2ea5e2badf318”
$sha256_15 = “e77bc95772ae84e5ecf68c928059cab3e305f92b1518d0ec3f8a7eb6eb728503”
$sha256_16 = “24934295a5824ef8ec8df1df9ee5bc719bb98e9b6b55b2cbbb02498782762cc5”
$sha256_17 = “0e9d984f980ceffb846946a8926e1d69abf2d07a6b710b8f8c802026ba3bbdb4”
$sha256_18 = “05a4f648099d0b35d6eb4662266b1046d4691bb8e739a4fd4e4e55e69774ef1f”
$sha256_19 = “21497a0eb89f321f971b4346880b43b342df131c431788cff4685c5a5a71b53e”
$sha256_20 = “cbee972115b129ed3ce366217321a6f431ab86d9bf61c90ef7d224f1004a672c”
$sha256_21 = “375229df144b3fb0d0560d90b06aa7fe34825886069653a088fa4071476cf63e”
$sha256_22 = “ce2ad8b6d76ba03c96d9248ac3d22590801e00611244c1942875adf52c154971”
$sha256_23 = “7ce399ae92c3e79a25e9013b2c81fe0add119bda0a65336d1e5c231654db01a5”
$sha256_24 = “05d2d06143d363c1e41546f14c1d99b082402460ba4e8598667614de996d2fbc”
$sha256_25 = “94dc0f696a46f3c225b0aa741fbd3b8997a92126d66d7bc7c9dd8097af0de52a”
$sha256_26 = “58d54e2454be3e4e9a8ea86a3f299a7a60529bc12d28394c5bdf8f858400ff7b”
$sha256_27 = “53775af67e9df206ed3f9c0a3756dbbc4968a77b1df164e9baddb51e61ac82df”
$sha256_28 = “6d62210addb8268d0bd3e6ef0400d54c84e550ccad49f5867fdc51edc0c1db2c”
$sha256_29 = “282fa3476294e2b57aa9a8ab4bc1cc00f334197298e4afb2aae812b77e755207”
$sha256_30 = “a2feb262a667de704e5e08a8a705c69bbcc806e0d52f0f8e3f081a6aa6c8d7b4”
$sha256_31 = “85b4d29f2830a3be3a0f51fbe358bea1a35d2a8aaa6a24f5cc1f2e5d2769716e”
$sha256_32 = “04a1852aed5734d8aaf97730a7231272f103605a4f83ea8413abe6f8169aee4c”
// IP Addresses
$ip_1 = “185.208.158.250”
$ip_2 = “104.225.129.171”
$ip_3 = “34.72.90.40”
$ip_4 = “94.141.122.164”
$ip_5 = “64.52.80.82”
$ip_6 = “102.135.95.102”
$ip_7 = “178.17.57.102”
$ip_8 = “185.149.146.118”
$ip_9 = “185.149.146.1”
$ip_10 = “180.178.189.17”
$ip_11 = “195.201.108.189”
$ip_12 = “77.238.241.203”
$ip_13 = “5.35.44.176”
$ip_14 = “180.178.122.131”
$ip_15 = “91.202.233.250”
$ip_16 = “45.61.136.81”
$ip_17 = “45.11.180.174”
$ip_18 = “91.202.233.132”
$ip_19 = “107.158.128.90”
$ip_20 = “107.158.128.45”
$ip_21 = “170.130.165.28”
$ip_22 = “91.202.233.251”
$ip_23 = “79.132.130.142”
$ip_24 = “173.232.146.90”
// Domains
$domain_1 = “bioomx.com”
$domain_2 = “boiksal.com”
$domain_3 = “bkkil.com”
$domain_4 = “biosefjk.com”
$domain_5 = “bioakw.com”
$domain_6 = “bikbal.com”
$domain_7 = “bilaskf.com”
$domain_8 = “bliokdf.com”
$domain_9 = “tdbfvgwe456yt.com”
$domain_10 = “programsbookss.com”
// URLs
$url_1 = “http://www.ip-api.com/line/?fields=147457”
$url_2 = “http://www.ip-api.com/line/?fields=147505”
$url_3 = “http://www.ip-api.com/line/?fields=16385”
condition:
any of ($sha256*) or any of ($ip*) or
any of ($domain*) or any of ($url*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
FANCY BEAR: Unmasking a Decade of State-Sponsored Cyber Espionage
About the Threat Actor
FANCY BEAR is a Russian state-sponsored hacking group active since 2007, widely linked to Russian military intelligence. Known for cyber-espionage and political interference, including election-related operations, the group targets governments, corporations, and media worldwide. They exploit software vulnerabilities to gain access, extract credentials using custom and public tools, and deploy tailored malware. To evade detection, they delete system logs, manipulate file timestamps, and route command traffic through compromised systems. Their campaigns are highly targeted and align closely with Russian strategic objectives, reflecting advanced technical skill and a deep understanding of both offensive tactics and stealthy persistence.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2017-11882 | Microsoft Office | 7.8 | Link |
| CVE-2021-4034 | pkexec application | 7.8 | Link 1, Link 2 |
| CVE-2016-5195 | Linux kernel | 7.0 | Link1, Link2, Link3, Link4, Link5, and Link6 |
| CVE-2020-0688 | Microsoft Exchange | 8.8 | Link 1 and Link 2 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning |
| Reconnaissance | T1589.001 | Gather Victim Identity Information: Credentials |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.008 | Compromise Infrastructure: Network Devices |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1091 | Replication Through Removable Media |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Persistence | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Persistence | T1133 | External Remote Services |
| Persistence | T1137.002 | Office Application Startup: Office Test |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Privilege Escalation | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Privilege Escalation | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Defense Evasion | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1221 | Template Injection |
| Defense Evasion | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1110.001 | Brute Force: Password Guessing |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1528 | Steal Application Access Token |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Lateral Movement | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Lateral Movement | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Collection | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Collection | T1560 | Archive Collected Data |
| Collection | T1119 | Automated Collection |
| Collection | T1213 | Data from Information Repositories |
| Collection | T1213.002 | Data from Information Repositories: Sharepoint |
| Collection | T1005 | Data from Local System |
| Collection | T1039 | Data from Network Shared Drive |
| Collection | T1025 | Data from Removable Media |
| Collection | T1074.002 | Data Staged: Remote Data Staging |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1113 | Screen Capture |
| Command and Control | T1001.001 | Data Obfuscation: Junk Data |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1092 | Communication Through Removable Media |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1030 | Data Transfer Size Limits |
| Exfiltration | T1048.002 | Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non- C2 Protocol |
| Impact | T1498 | Network Denial of Service |
Latest Developments Observed
The threat actor is suspected of exploiting Microsoft Outlook by deploying a newly identified backdoor, referred to as NotDoor. This malware enables adversaries to exfiltrate sensitive data, upload malicious files, and remotely execute commands on compromised systems. The campaign’s primary objective appears to be the theft of confidential information, with social engineering techniques leveraged as the initial entry point into targeted environments.
ETLM Insights
APT28, along with other Russian state-sponsored and cybercriminal groups operating under the umbrella of Russian intelligence (GRU)-linked campaigns, is closely associated with cyber-espionage, disinformation operations, ransomware deployment, and disruptive attacks against governments, critical infrastructure, defense, energy, and financial sectors. The threat actor consistently aligns their operations with Russian state interests, supporting military, diplomatic, and geopolitical objectives through sustained espionage and influence campaigns. Looking ahead, the group may expand its focus toward supply- chain compromises and infrastructure targeting, underscoring continued strategic investment in advanced cyber capabilities to shape global political and military outcomes.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule FancyBear_IOCs_Match
{
meta:
author = “CYFIRMA”
description = “Detects IOC artifacts associated with Fancy Bear” date = “2025-09-09”
threat_actor = “FANCY BEAR / APT28” strings:
// CVEs as text (if present in code, comments, exploit kits, etc.)
$cve1 = “CVE-2017-11882”
$cve2 = “CVE-2021-4034”
$cve3 = “CVE-2016-5195”
$cve4 = “CVE-2020-0688”
$cve5 = “CVE-2023-32315”
$cve6 = “CVE-2021-44228”
$cve7 = “CVE-2018-13379”
$cve8 = “CVE-2023-23397”
$cve9 = “CVE-2020-1472”
$cve10 = “CVE-2023-38831”
$cve11 = “CVE-2018-8174”
$cve12 = “CVE-2020-2021”
$cve13 = “CVE-2020-5902”
$cve14 = “CVE-2014-4114”
$cve15 = “CVE-2020-15505”
$cve16 = “CVE-2019-19781”
$cve17 = “CVE-2022-30190”
$cve18 = “CVE-2022-38028”
$cve19 = “CVE-2024-21412”
$cve20 = “CVE-2022-21587”
$cve21 = “CVE-2021-1675”
$cve22 = “CVE-2020-1380”
$cve23 = “CVE-2023-27350”
$cve24 = “CVE-2012-0158”
$cve25 = “CVE-2009-3129”
$cve26 = “CVE-2021-22555”
$cve27 = “CVE-2023-36025”
$cve28 = “CVE-2023-27351”
$cve29 = “CVE-2023-27992”
$cve30 = “CVE-2015-2545”
$cve31 = “CVE-2023-32231”
$cve32 = “CVE-2019-11510”
$cve33 = “CVE-2014-1761”
// IPs
$ip1 = “208.91.197.27”
$ip2 = “127.0.0.1”
$ip3 = “198.49.23.177”
$ip4 = “50.7.210.226”
$ip5 = “185.220.101.143”
$ip6 = “142.250.31.102”
// Domains
$domain1 = “jinjinpig.co.kr”
$domain2 = “cloud-mail.ink”
$domain3 = “background-services.net”
$domain4 = “futuresfurnitures.com”
// Suspicious Files
$file1 = “win32 exe”
$file2 = “hrm3jvh9v.dll”
$file3 = “ruodjxk.exe” condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($file*)
}
Recommendations Strategic
Management
Tactical
Salt Typhoon updates, and China spying on US policymakers
Global media have recently reported that the Chinese cyberespionage campaign, dubbed Salt Typhoon, may have collected data on every American. The operation’s scope was unprecedented, sweeping up information from a wide range of U.S. sectors, including telecommunications, government, transportation, lodging, and military infrastructure networks. In response, several Western allies—including the U.S., U.K., Canada, Finland, Germany, Italy, Japan, and Spain—issued a joint “name-and-shame” statement last week. They publicly linked the Salt Typhoon campaign to Chinese technology companies that have ties to Beijing’s People’s Liberation Army and Ministry of State Security.
In another news, it was reported that during trade talks with China in July, Chinese hackers impersonated a U.S. lawmaker to target U.S. individuals and organizations. The hackers posed as the China committee chair and sent malicious attachments to trade groups, law firms, and government agencies. These attachments contained malware linked to a well-known Chinese threat actor, APT41. The goal of this operation was likely to gain an advantage in the trade negotiations by gathering inside information. It is still unclear whether any of the targeted entities were successfully breached.
ETLM Assessment:
As noted by CYFIRMA in a recent report, the Salt Typhoon campaigns mark a significant evolution in China’s cyber strategy, from economic espionage to politically-driven operations that threaten Western critical infrastructure. Salt Typhoon’s infiltration of telecommunications networks and Volt Typhoon’s sabotage preparations in U.S. sectors like energy and transportation reveal China’s intent to dominate cyberspace, exploiting vulnerabilities in the U.S.’s fragmented cybersecurity framework. These campaigns, leveraging sophisticated techniques and plausible deniability, pose significant risks to national security, from compromised communications to potential disruptions of military and civilian operations. The structural advantages of China’s authoritarian cyber defense model, contrasted with the U.S.’s decentralized approach, underscore the challenges of securing privately owned systems against a state-backed actor with vast resources. As China’s cyber capabilities grow more sophisticated and disruptive, Western nations must confront the reality of a new threat landscape, where digital vulnerabilities could reshape geopolitical outcomes and challenge the resilience of open societies.
Undersea cable cuts disrupt the Internet in the Middle East and Asia
Multiple undersea internet cables have been severed in the Red Sea, causing widespread disruption to internet access across parts of Asia and the Middle East. According to researchers, the incident impacted the SMW4 and IMEWE cable systems near Jeddah, Saudi Arabia. The damage has led to degraded connectivity in several countries, including India, Pakistan, and the UAE. Infrastructure operators confirmed that internet traffic routed through the Middle East may experience increased latency due to the cuts. The cause of the damage is currently unknown. While some have previously accused the Houthis of targeting subsea cables, the group has denied these allegations.
ETLM Assessment:
CYFIRMA warned about this scenario in a report published last year. In the report, we note that although the threat from non-state actors like the Houthis cannot be dismissed, non-state actors will probably be less likely and less capable of causing harm to the networks and operating systems that submarine cables depend on. Accidental damage caused by fishing boats or ship anchors will continue to be a hazard, however, the physical infrastructure is always at risk from highly capable state-sponsored actors, and the same goes for the cyber threat to the management systems.
Besides physical threats, there’s always the risk of cyber or network attacks. By hacking into the network management systems that private companies use to manage data traffic passing through the cables, malicious actors could disrupt data flows. A “nightmare scenario” would involve a hacker gaining control, or administrative rights, of a network management system: at that point, physical vulnerabilities could be discovered, disrupting or diverting data traffic, or even executing a “kill click” (deleting the wavelengths used to transmit data). The potential for sabotage or espionage is quite clear – and according to reports, the security of many of the network management systems is not up to date.
Qilin Ransomware Impacts Osaki Medical
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, Osaki Medical(https[:]//www[.]osakimedical[.]co[.]jp/), was compromised by Qilin Ransomware. Osaki Medical is a Japanese company that manufactures and markets safe, functional, and cost-effective medical supplies, sanitary materials, cosmetics, and medical equipment for the medical and nursing care industries. The ransomware group allegedly infiltrated Osaki Medical’s network and exfiltrated approximately 113 GB of data. The stolen information is reported to include multiple databases, supply chain management (SCM) records, customer relationship management (CRM) data, personal details, sales and logistics information, product-related files, internal correspondence, and other sensitive business data. The attackers have issued a warning that Osaki Medical must contact them before the countdown expires, claiming that failure to do so will leave the company with no alternative means of recovering its data or protecting its business operations.
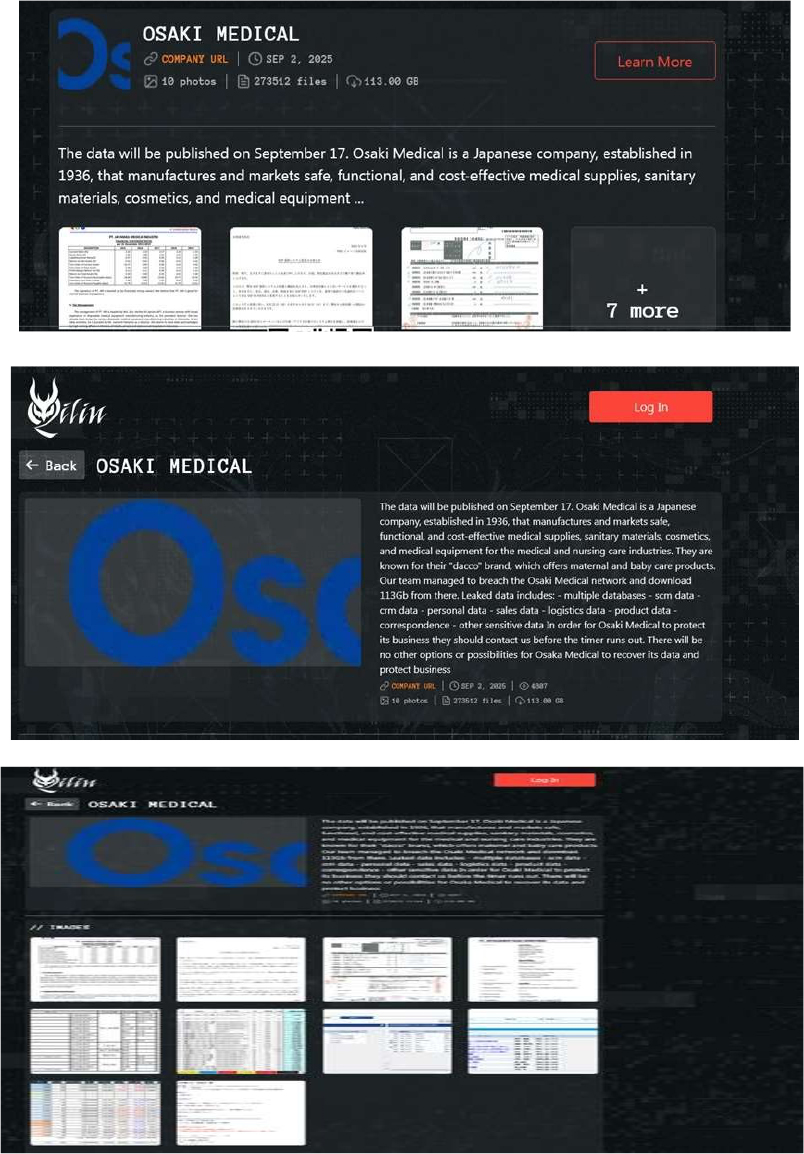
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Dire Wolf Ransomware Impacts the Purwana Group
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia, Purwana Group (https[:]//bahanagv[.]co[.]id), was compromised by Dire Wolf Ransomware. Purwana Group is a diversified Indonesian business conglomerate with major activities in coffee production, beverage distribution, and agricultural exports, serving local and international markets. The compromised data reportedly includes financial records, tax information, customer details, and subsidiary-related files. The affected entities span multiple group companies, including PT. Bahana Genta Viktory, PT. Bahana Gourmet Indonesia, PT. Balindo Mitra Perkasa, PT. Cipta Artha Victory, PT. Espressa Illindo, PT. Karsa Murni Centra Satya, PT. Karsa Victa Satya, PT. Parama Mandyadana, PT. UCC and PT. Victo Oro Prima. In total, the volume of exposed data is estimated to be around 40 GB.
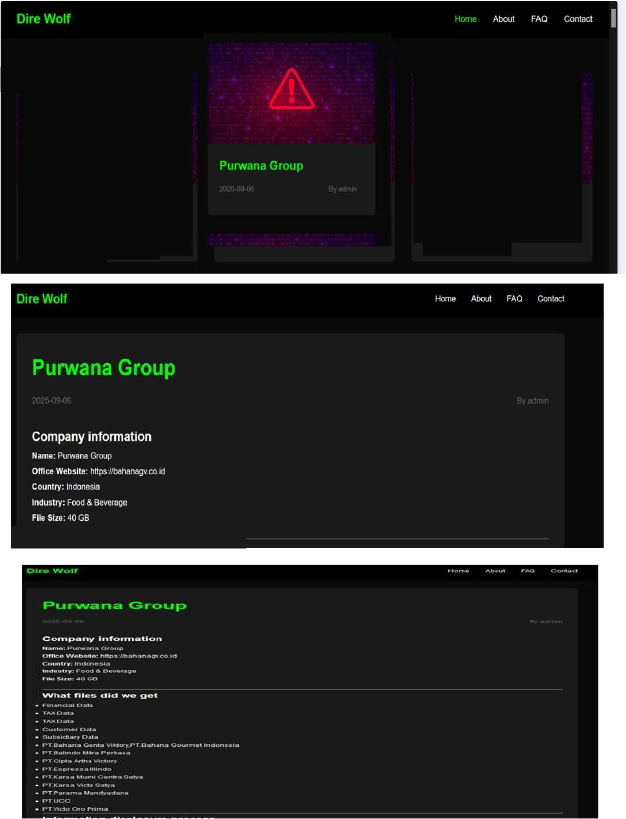
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion- based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
Vulnerability in cJSON
Relevancy & Insights:
The vulnerability exists due to a boundary condition within the decode_array_index_from_pointer() function in cJSON_Utils.c.
Impact:
A remote attacker can trigger an out-of-bounds read error and read the contents of memory on the system.
Affected Products:
https[:]//x-0r[.]com/posts/cJSON-Array-Index-Parsing- Vulnerability
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
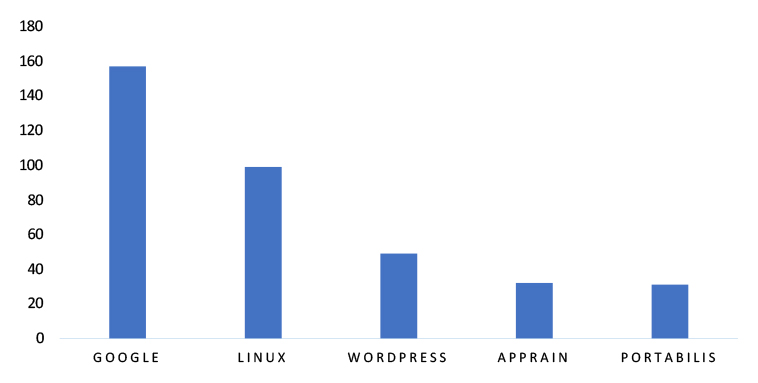
ETLM Assessment
Vulnerabilities in cJSON, a lightweight C library for parsing and printing JSON, can expose applications to security risks. Exploitation of such flaws may lead to denial of service (DoS), memory corruption, or, in some cases, remote code execution, depending on how the library is integrated into the application. Since cJSON is widely used in embedded systems, IoT devices, and applications requiring fast JSON handling, these vulnerabilities can have a broad impact.
Desolator Ransomware attacked and published the data of Tri Thuc Software
Summary:
Recently, we observed that Desolator Ransomware attacked and published the data of the Tri Thuc Software (https[:]//banquyenphanmem[.]com/) on its dark web website. Tri Thuc software specializes in providing a wide range of software solutions, including graphic design, data recovery, network management, and office applications. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The data leak resulting from the ransomware attack includes application source code, internal company documents, and backup files, along with highly confidential and sensitive information. In total, the volume of exposed data is estimated to be around 1.4 terabytes.
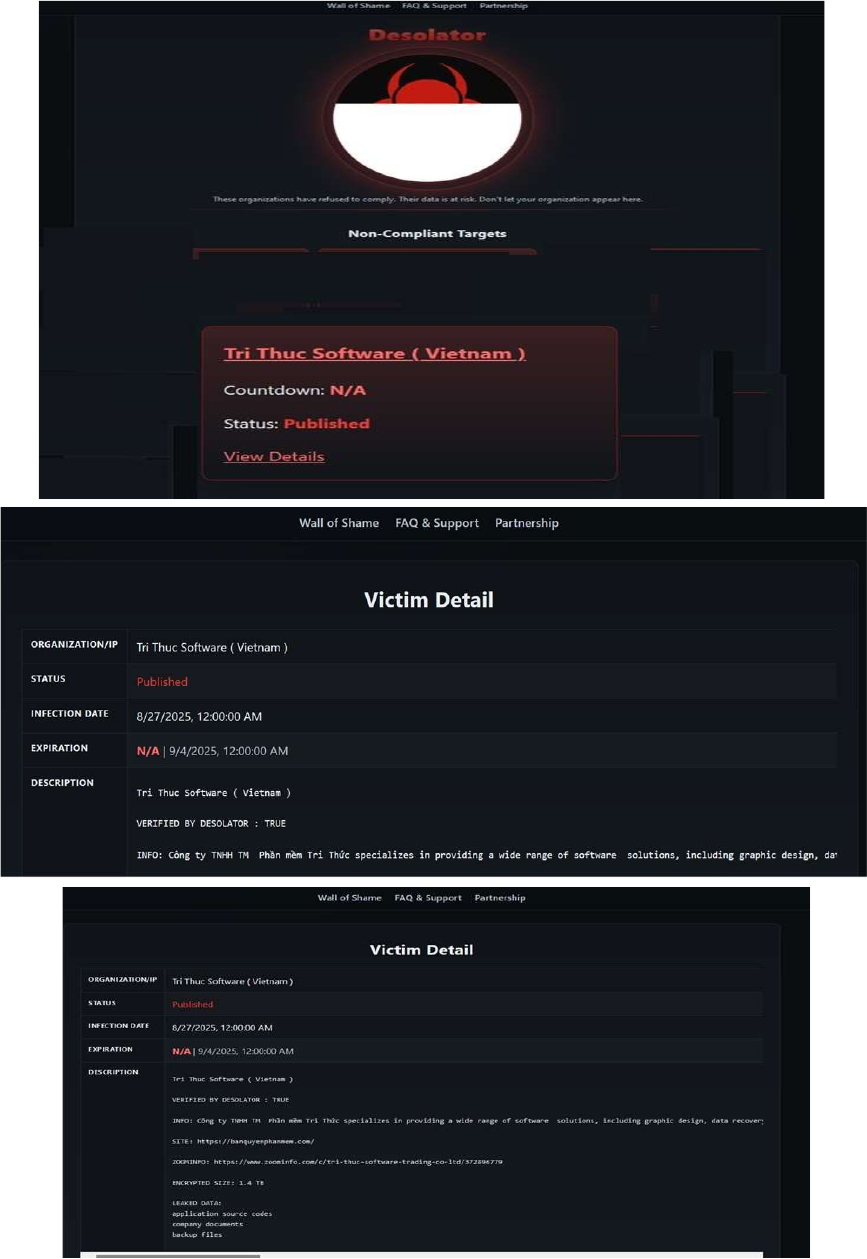
Relevancy & Insights:
Desolator Ransomware is a recently emerged ransomware group active in 2025, known for targeting organizations with data encryption, extortion, and demands for payment to restore access to encrypted files.
ETLM Assessment:
According to CYFIRMA’s assessment, Desolator Ransomware is an active player within the global ransomware landscape in 2025. The group employs aggressive tactics that have driven widespread operational disruptions across multiple industries. Desolator is characterized as a sophisticated and continuously evolving threat, with particular risk to enterprise environments where its impact can be especially severe.
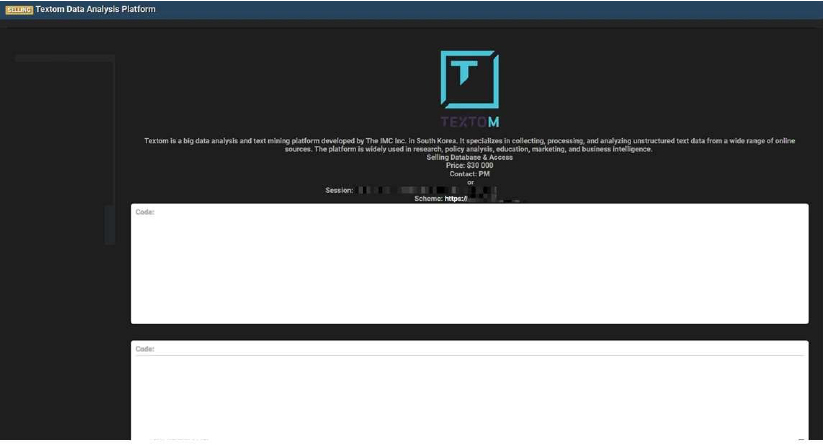
South Korean Big Data Platform Textom’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “Krekti” has allegedly put the database and platform access for Textom, a big data analysis and text mining platform, up for sale on a dark web forum. The victim, Textom, was developed by The IMC Inc., a company based in South Korea. The platform is known for its capabilities in collecting, processing, and analyzing unstructured text data from various online sources, making it a valuable tool for research, marketing, policy analysis, and business intelligence. The threat actor is asking for $30,000 in exchange for the compromised data and access.
The sensitive information allegedly exposed in the breach is extensive, containing multiple databases with personally identifiable information (PII) of the platform’s users. The shared samples suggest the leak includes user authentication details, payment records, and detailed personal profiles. A significant portion of the users appears to be associated with academic and research institutions in South Korea. The leak also reportedly contains YouTube API keys used by the platform.
The allegedly leaked data includes:
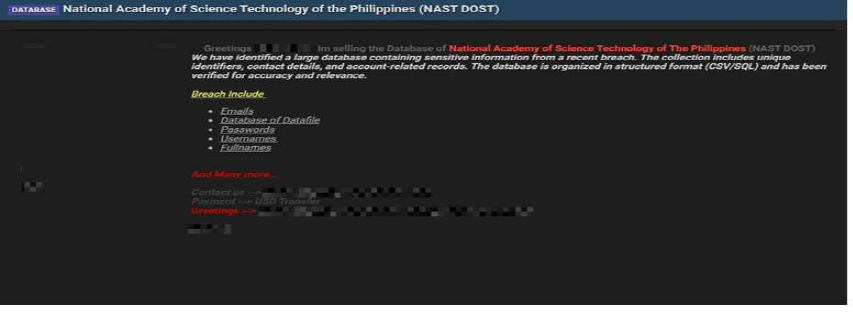
Philippines’ Top Science Academy (NAST DOST) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team has identified that a threat actor “Terror” has allegedly put a database belonging to the National Academy of Science and Technology of the Philippines (NAST DOST) up for sale on a dark web forum. NAST DOST serves as the Philippines’ premier recognition and advisory body on science and technology, playing a crucial role in the nation’s scientific development and policymaking. The breach could potentially expose sensitive information related to the country’s top scientists and governmental scientific affairs.
According to the forum post, the threat actor claims to have obtained a large collection of sensitive information from a recent breach. The seller asserts that the database, organized in CSV/SQL format, has been verified for accuracy. The allegedly compromised data includes a variety of personally identifiable information.
The breach allegedly includes:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “Krekti” has recently gained attention as a highly active group specializing in data leaks. Reliable sources have connected the group to multiple security breaches involving unauthorized system access and the attempted sale of exfiltrated data on dark web marketplaces. Krekti’s ongoing operations highlight the evolving and persistent nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to strengthen their cybersecurity posture through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and infrastructure.
Recommendations: Enhance the cybersecurity posture by:
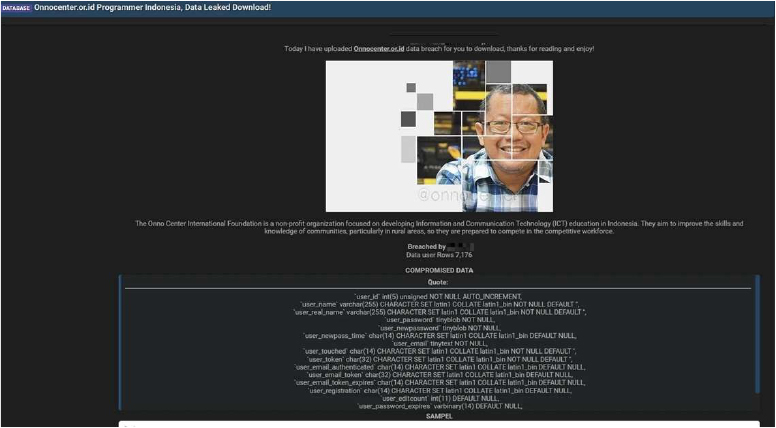
The CYFIRMA Research team observed that the Onno Center International Foundation, an Indonesian non-profit organization dedicated to advancing Information and Communication Technology (ICT) education, has allegedly been targeted in a data breach. A threat actor “N1KA” has claimed responsibility for the attack and has leaked a database containing the information of over 7,100 users on a cybercrime forum. The Onno Center is a key organization in Indonesia, focusing on improving the tech skills and knowledge of communities, especially in rural areas, to prepare them for the competitive workforce.
The leaked data allegedly exposes a significant amount of personally identifiable information (PII) from the organization’s user database. The compromised information reportedly includes sensitive user details that could be exploited for further malicious activities such as phishing, identity theft, and other cybercrimes. The threat actor shared a sample of the data to validate their claims.
The database allegedly contains the following types of information:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
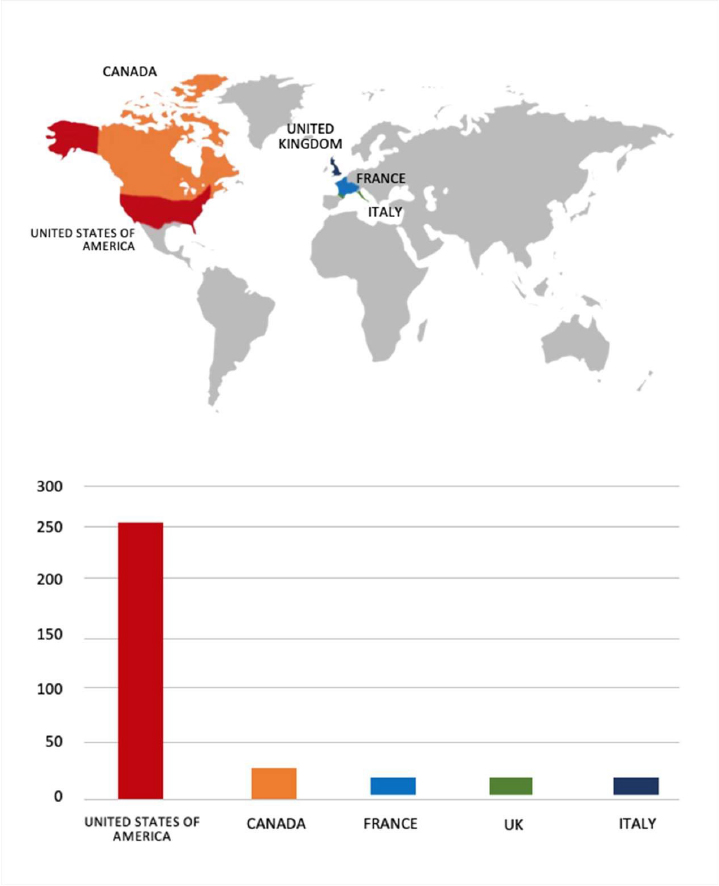
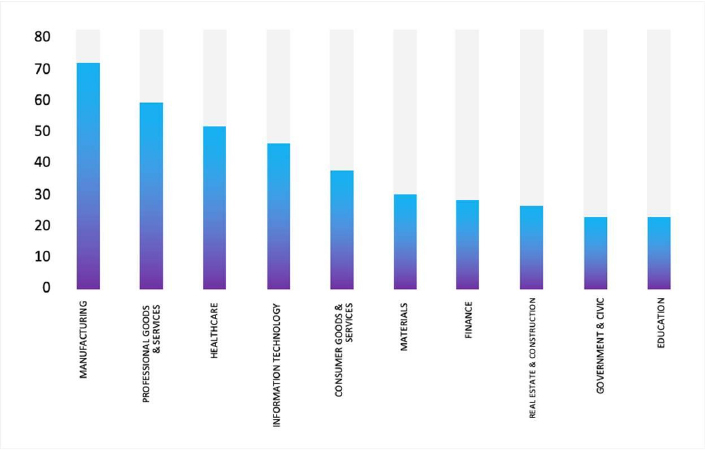
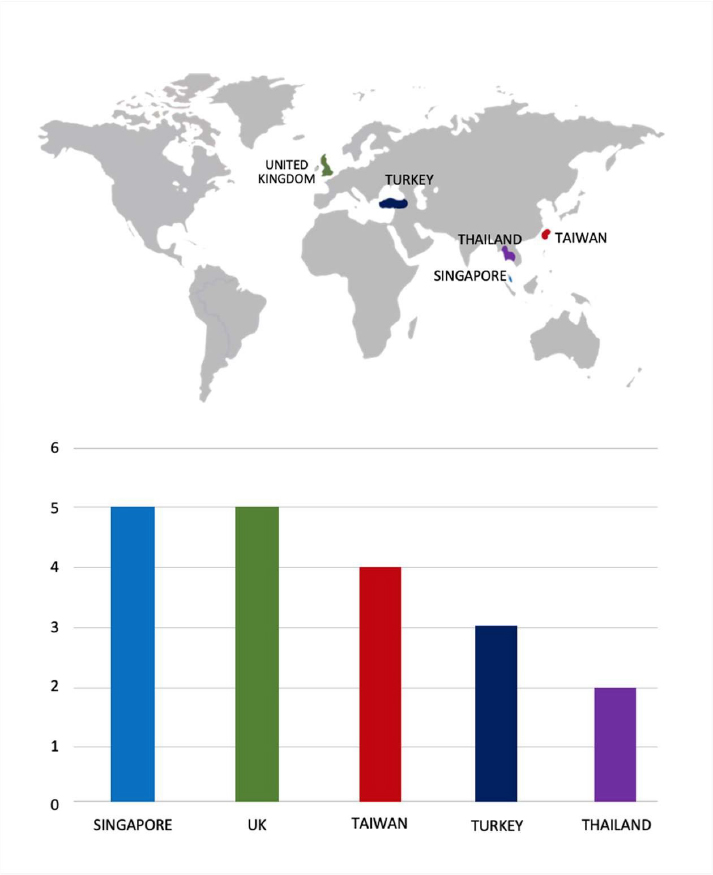
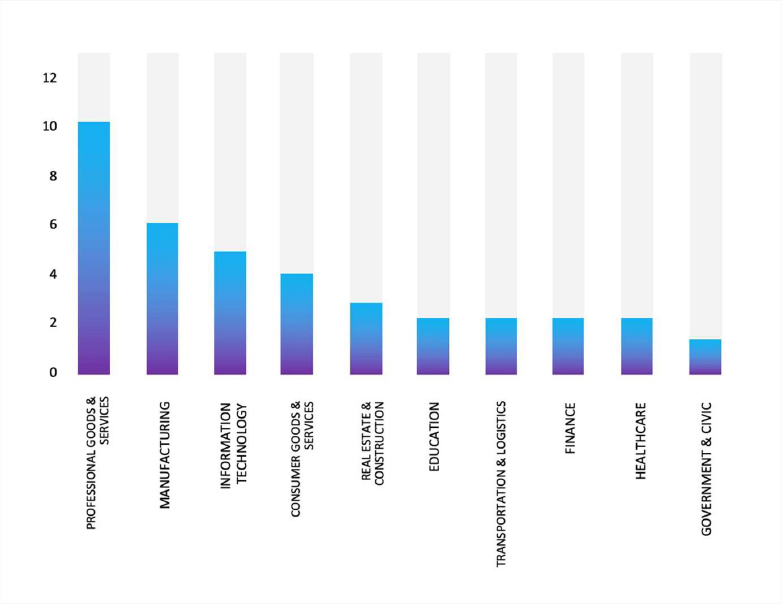
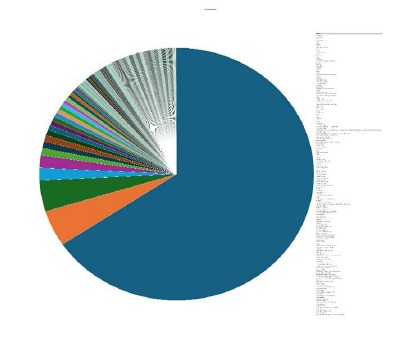
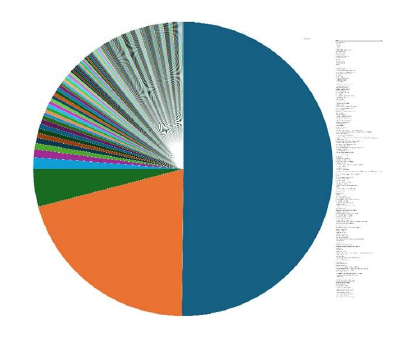
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.