


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Jackpot Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Jackpot Ransomware
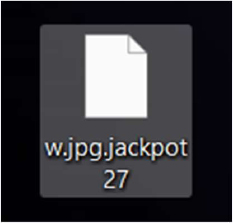
Researchers have determined that Jackpot is a variant belonging to the MedusaLocker ransomware family. Once executed, the ransomware encrypts files using RSA and AES algorithms, appends a unique extension in the format “.jackpot[number]” to each affected file, changes the desktop wallpaper, and creates a ransom note named READ_NOTE.html.
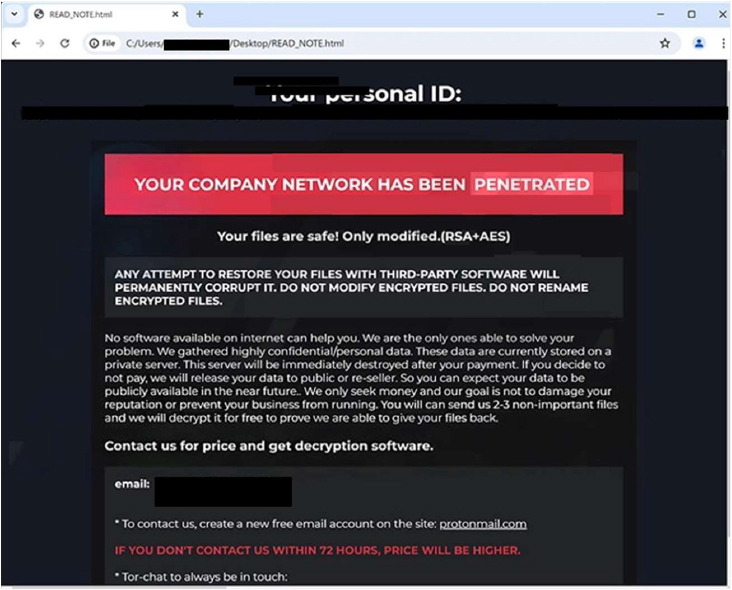
The ransom note informs victims that their files have been encrypted and sensitive data has been stolen. It warns that any attempt to restore or modify encrypted files with third- party software will cause permanent corruption. The note claims only the attackers can decrypt the data and offers to decrypt a few non-critical files as proof. Victims are instructed to contact the attackers via two specified email addresses within 72 hours to avoid a price increase, while also being threatened with the public release or sale of the stolen data if payment is not made.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 T1129 |
Command and Scripting Interpreter Shared Modules |
| Persistence | T1112 T1542.003 T1547.001 |
Modify Registry Pre-OS Boot: Bootkit Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1134.004 T1547.001 |
Access Token Manipulation:Parent PID Spoofing Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1006 T1014 T1027.002 T1027.005 T1036 T1070.004 T1112 T1134.004 T1140 T1202 T1222 T1497.001 T1497.003 T1542.003 T1564.001 T1564.003 |
Direct Volume Access Rootkit Obfuscated Files or Information: Software Packing Obfuscated Files or Information: Indicator Removal from Tools Masquerading Indicator Removal: File Deletion Modify Registry Access Token Manipulation: Parent PID Spoofing Deobfuscate/Decode Files or Information Indirect Command Execution File and Directory Permissions Modification Virtualization/Sandbox Evasion: System Checks Virtualization/Sandbox Evasion: Time Based Evasion Pre-OS Boot: Bootkit Hide Artifacts: Hidden Files and Directories Hide Artifacts: Hidden Window |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 T1012 T1016 T1057 T1082 T1083 T1120 T1124 T1497.001 T1497.003 T1518.001 T1614 |
Application Window Discovery Query Registry System Network Configuration Discovery Process Discovery System Information Discovery File and Directory Discovery Peripheral Device Discovery System Time Discovery Virtualization/Sandbox Evasion: System Checks Virtualization/Sandbox Evasion: Time Based Evasion Software Discovery: Security Software Discovery System Location Discovery |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Collection | T1056.001 T1074 |
Input Capture: Keylogging Data Staged |
| Command and Control | T1071 T1573 |
Application Layer Protocol Encrypted Channel |
| Impact | T1485 T1486 T1490 T1491.001 |
Data Destruction Data Encrypted for Impact Inhibit System Recovery Defacement: Internal Defacement |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis shows that Jackpot ransomware operates in line with patterns observed in the MedusaLocker family. The attackers employ a dual-extortion method, combining file encryption with the theft of sensitive data to strengthen their leverage. Victims are warned that their information will be released or sold if payment is not made, adding reputational risk to operational disruption.
The ransom note READ_NOTE.html serves as the primary communication channel, providing specific email addresses and imposing a 72-hour deadline before increasing the ransom amount. This time-bound pressure, paired with controlled communication, reflects a deliberate strategy to compel quick compliance and limit opportunities for alternative recovery options. The overall operation is highly structured, indicating a coordinated effort to disrupt victim environments, maintain negotiation control, and extract maximum financial gain while ensuring anonymity for the threat actors. Based on current tactics, Jackpot campaigns are likely to continue evolving with more targeted attacks and enhanced data-leak strategies to increase ransom payment success rates.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high (Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan| Objectives: Stealing Sensitive Information, Data Exfiltration | Target Technologies: Windows OS, Cryptocurrency wallets | Target Industry: Financial Services (Cryptocurrency)|Target Geographies: Brazil, India, Spain, Russia, Italy, Germany
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week This week “Efimer” is trending. About Malware Efimer
A recently identified cyber campaign has been distributing large volumes of identical emails, each carrying an archive file that conceals the Efimer stealer, designed to steal cryptocurrency. First appearing around October 2024, the threat initially spread through compromised WordPress sites before widening its reach in mid-2025 via malicious torrents and email-based delivery. While global in scope, activity has been particularly intense in certain regions, with notable spikes in Brazil, India, Spain, Russia, Italy, and Germany. The malware relies on the Tor network to communicate with its operators and can be enhanced with extra scripts allowing attackers to target WordPress logins and collect email addresses, fuelling future waves of attacks.
Attack Method
Attackers in this campaign sent carefully crafted phishing emails disguised as legal notices from a prominent company. The messages claimed the recipient’s domain name violated trademark rights and threatened legal action, while offering to drop the matter or even purchase the domain. Instead of naming a specific domain, the email included an attachment that appeared to contain the infringement details and purchase offer.
Inside was a disguised, password-protected file that, once opened, revealed a malicious script. This script acted as the installer for the Efimer Trojan, quietly setting it up on the victim’s computer while displaying misleading error messages to make it seem as though nothing had happened.
Once installed, the Efimer Trojan begins operating as a tool designed to intercept and alter cryptocurrency transactions. It quietly monitors the victim’s activity, waiting for any copied wallet addresses so it can swap them with the attacker’s own, ensuring funds are redirected without the user’s knowledge. The malware also uses hidden communication channels to stay connected to its operators, allowing it to receive instructions or execute additional code on the infected system. To avoid detection, it limits how often it contacts its servers and halts its activity when certain system tools are open. In addition to substituting wallet addresses, the malware captures recovery phrases and screenshots, transmitting them back to the threat actors to enhance their capability to compromise and exfiltrate digital assets.
Beyond phishing emails, the attackers also used compromised WordPress sites to spread the Efimer Trojan. They infiltrated poorly secured sites and posted enticing download offers for popular new movies. Clicking these links led victims to a password- protected file that, when opened, appeared to contain a film but instead installed the Trojan in the background. These tools methodically searched the internet for potential targets, attempting large numbers of password combinations until they gained access. Once inside, they could post new malicious content or harvest site user details, further expanding their reach.
By combining these website compromises with email campaigns, the attackers created a self-sustaining cycle — each newly hijacked site became another launchpad for the malware, attracting more victims and enlarging the pool of future targets.
Alternative Variants of the Efimer Campaign
Researchers uncovered additional malicious tools linked to the Efimer operation, each designed to extend its reach and capabilities. One variant, delivered through a script called “assembly.js,” followed the same overall goal as the original malware — targeting cryptocurrency users — but introduced new behaviors to help it persist and avoid detection. It created unique IDs for each infected system, adapted its actions depending on the environment, and quietly gathered details about the victim’s location and cryptocurrency wallets. Once this information was ready, it was sent to the attackers’ hidden servers, with built-in safeguards to retry if the connection failed. The malware also scanned for recovery phrases and wallet addresses in the clipboard, storing the results for future theft attempts.
Another script called “Liame,” had an entirely different focus. Instead of stealing cryptocurrency, it specialized in collecting email addresses from specific websites provided by the attackers. The script methodically browsed through the targeted domains, extracting addresses from both visible text and hidden “mailto” links. In some cases, it appeared capable of using this data to fill out web forms, potentially for spam or phishing purposes. By disguising its purpose with playful name reversals like “Liame” for “Email,” the tool attempted to mask its true intent within the code.
Together, these variants show that the Efimer campaign is not a single-purpose operation, but a flexible platform able to launch different types of attacks — from financial theft to data harvesting — depending on the attackers’ goals.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1053 | Scheduled Task/Job |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1053 | Scheduled Task/Job |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1539 | Steal Web Session Cookie |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1496 | Resource Hijacking |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as threats like Efimer continue to evolve, organizations may face a growing wave of blended attacks that erase the distinction between personal and professional security. A single compromised home device or personal email account could serve as the entry point for attackers to penetrate corporate networks, making the separation between “work” and “personal” safety increasingly irrelevant. Phishing campaigns are expected to become more persuasive, with adversaries leveraging stolen data from past breaches to craft messages that reference authentic business contacts or ongoing projects. Such tailored approaches will make malicious emails harder to recognize and more likely to succeed in high-trust environments. The modular design of campaigns like Efimer could usher in a future where malware adapts its objectives mid-operation — beginning as a financial theft tool and later shifting to steal confidential documents or corporate credentials. This fluidity will challenge security teams, making it significantly more difficult to anticipate, detect, and neutralize threats before serious harm occurs.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Efimer_Indicators
{
meta:
description = “Detects Efimer malware indicators” author = “CYFIRMA”
malware_family = “Efimer”
strings:
// MD5 hashes
$md5_1 = “39fa36b9bfcf6fd4388eb586e2798d1a”
$md5_2 = “5ba59f9e6431017277db39ed5994d363”
$md5_3 = “442ab067bf78067f5db5d515897db15c”
$md5_4 = “16057e720be5f29e5b02061520068101”
$md5_5 = “627dc31da795b9ab4b8de8ee58fbf952”
$md5_6 = “0f5404aa252f28c61b08390d52b7a054”
$md5_7 = “eb54c2ff2f62da5d2295ab96eb8d8843”
$md5_8 = “100620a913f0e0a538b115dbace78589”
$md5_9 = “b405a61195aa82a37dc1cca0b0e7d6c1”
$md5_10 = “5d132fb6ec6fac12f01687f2c0375353”
// URLs
$url_1 = “https://lovetahq.com/sinners-2025-torent-file”
$url_2 = “https://lovetahq.com/wp-content/uploads/2025/04/movie_39055_xmpg.zip”
$url_3 = “http://cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onion”
$url_4 = “http://he5vnov645txpcv57el2theky2elesn24ebvgwfoewlpftksxp4fnxad.onion”
condition:
any of ($md5*) or any of ($url*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Please refer to the trending malware advisory for details on the following:
Unmasking Lazarus Group: APT-Level Targeting of Critical Infrastructure and Financial Systems
About the Threat Actor
Lazarus Group, active since at least 2009, is a highly sophisticated cybercriminal organization linked to the North Korean government, specifically affiliated with Lab 110, a division of DPRK military intelligence. Lazarus Group is recognized for its rapid development and evolution of malware and exploits through a dedicated malware development unit. Recently, the group has increasingly targeted cryptocurrency exchange companies. The group’s key objectives include the monetization of cyber intrusions and the execution of global espionage campaigns, with a strong emphasis on compromising firms.
Details on Exploited Vulnerabilities
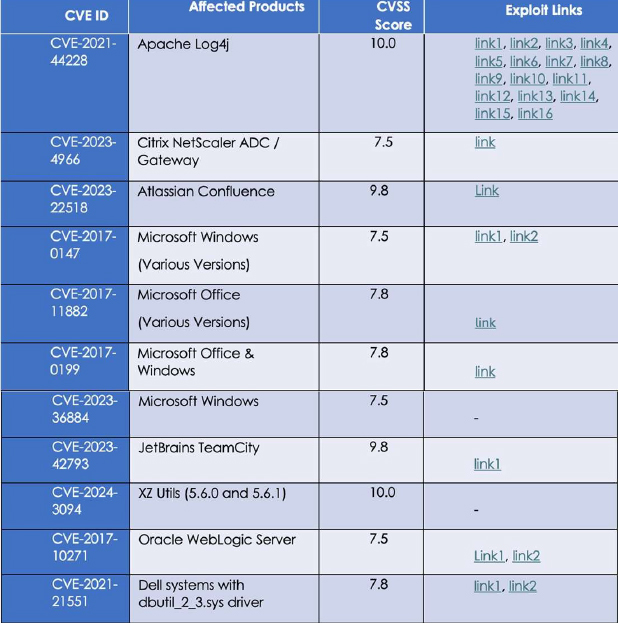
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1591.004 | Gather Victim Org Information: Identify Roles |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1608.002 | Stage Capabilities: Upload Tool |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1587.002 | Develop Capabilities: Code Signing Certificates |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.004 | Obtain Capabilities: Digital Certificates |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1566.003 | Phishing: Spear phishing via Service |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1106 | Native API |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Persistence | T1505.004 | Server Software Component: IIS Components |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Privilege Escalation | T1134.002 | Access Token Manipulation: Create Process with Token |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1134.002 | Access Token Manipulation: Create Process with Token |
| Defense Evasion | T1218 | System Binary Proxy Execution |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.003 | Indicator Removal: Clear Command History |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1036.003 | Masquerading: Rename Legitimate Utilities |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.007 | Obfuscated Files or Information: Dynamic API Resolution |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1220 | XSL Script Processing |
| Defense Evasion | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time-Based Evasion |
| Defense Evasion | T1622 | Debugger Evasion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1221 | Template Injection Authentication Process: Conditional Access Policies |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1622 | Debugger Evasion |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1124 | System Time Discovery |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1021.004 | Remote Services: SSH |
| Lateral Movement | T1534 | Internal Spear phishing |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1001.003 | Data Obfuscation: Protocol or Service Impersonation |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Exfiltration | T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| Impact | T1561.001 | Disk Wipe: Disk Content Wipe |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1489 | Service Stop |
| Impact | T1485 | Data Destruction |
| Impact | T1529 | System Shutdown/Reboot |
| Impact | T1491.001 | Defacement: Internal Defacement |
Latest Developments Observed
The threat actor is suspected of leveraging a new variant of malware known as PyLangGhost RAT, a Python-based evolution of GoLangGhostRAT. With the malware, the threat actor intends to target technology, finance, and crypto industries, with developers and executives as prime victims through social engineering techniques. The intent appears to be data exfiltration of sensitive details.
ETLM Insights
The Lazarus Group continues to demonstrate its strategic agility by innovating attack techniques and advancing operational sophistication. Recent intelligence indicates the group is leveraging “ClickFix” attacks and targeting developers within the software supply chain ecosystem to compromise trusted distribution channels. These campaigns involve the development of new malware variants specifically engineered for stealth, persistence, and credential harvesting.
Operations are increasingly multi-stage in nature, enabling both broad infiltration and highly targeted espionage objectives. The group’s heightened technical sophistication, including modular payloads, refined social engineering, and supply-chain compromise tactics, underscores an elevated threat profile to technology providers, open-source platforms, and high-value enterprises.
YARA Rules
rule APT_PyLangGhost_Lazarussubgroup_FamousChollima_Aug2025
{
meta:
description = “Detects components and infrastructure of PyLangGhost RAT campaign by Lazarus subgroup Famous Chollima”
author = “CYFIRMA” date = “2025-08-13”
threat_actor = “Famous Chollima (Lazarus subgroup)” malware_family = “PyLangGhost RAT”
hash_auto_py_bin
= “bb794019f8a63966e4a16063dc785fafe8a5f7c7553bcd3da661c7054c6674c7” hash_command_py_bin
= “c4fd45bb8c33a5b0fa5189306eb65fa3db53a53c1092078ec62f3fc19bc05dcb” hash_config_py_bin
= “c7ecf8be40c1e9a9a8c3d148eb2ae2c0c64119ab46f51f603a00b812a7be3b45”
hash_nvidia_py_bin
= “a179caf1b7d293f7c14021b80deecd2b42bbd409e052da767e0d383f71625940” hash_util_py_bin
= “ef04a839f60911a5df2408aebd6d9af432229d95b4814132ee589f178005c72f”
strings:
// Domain and IPs (C2 infrastructure)
$domain_1 = “360scanner.store”
$ip_1 = “13.107.246.45”
$ip_2 = “151.243.101.229”
// URLs used for C2/Delivery
$url_1 = “https://360scanner.store/cam-v-b74si.fix”
$url_2 = “http://151.243.101.229:8080/”
// Known file names associated with PyLangGhost
$filename_1 = “auto.py.bin”
$filename_2 = “command.py.bin”
$filename_3 = “config.py.bin”
$filename_4 = “nvidia.py.bin”
$filename_5 = “util.py.bin”
// File artifacts
$filename_6 = “chrome_logins_dump.txt”
$filename_7 = “gather.tar.gz”
// Mutex pattern (if in memory)
$mutex = “.store”
condition:
any of ($domain_*) or any of ($ip_*) or
any of ($url_*) or
any of ($filename_*) or
$mutex
}
Recommendations Strategic
Management
Tactical
Cyber war in the Middle East is Still Ongoing
In the wake of Israel’s airstrikes on Iran, Israeli authorities were inundated with dubious text messages laced with harmful links. These were the work of Iranian hackers, trying to gain strategic intelligence on behalf of the regime in Tehran, with which Israel has been engaged in a covert cyber conflict for years, escalating sharply alongside the physical clashes in June. While the physical conflict ceased after 12 days, the digital battle rages on. The ongoing shadow war intensified after the war began and hasn’t stopped since.
Since the ceasefire, groups linked to Iran have exploited a recently discovered flaw in a widespread breach of Microsoft server software to target Israeli businesses. Meanwhile, Iran’s Ministry of Communications and Information Technology recently revealed that Iran faced over 20,000 cyberattacks during the conflict, marking the most extensive cyber campaign in the nation’s history. Among these were attacks that disrupted Iran’s air defense systems as Israeli jets launched their airstrikes. However, analysts and former Israeli officials argue that the most critical factor in shaping the war’s trajectory was the cyber-espionage campaign that preceded it. This effort enabled Israel to compile detailed profiles of Iranian nuclear scientists and military officials, facilitating the targeted killing of over a dozen in the opening salvo of its offensive.
Early in the conflict, Gonjeshke Darande, a hacking group believed to be aligned with Israel, siphoned $90 million from Iran’s Nobitex crypto exchange by transferring funds to inaccessible digital wallets, accusing the platform of being a regime tool. Nobitex denied these claims, asserting it was an independent private entity. The group also targeted two major Iranian banks, disrupting services at the state-owned Bank Sepah, tied to the military, and the private Bank Pasargad. Dotin, a tech firm supplying software to both banks, reported that the attack damaged hardware, knocking out their primary, backup, and disaster recovery data centers.
Iranian-linked groups retaliated with hack-and-leak operations against around 50 Israeli firms and spread malware to cripple Israeli systems. While they failed to penetrate the defenses of Israel’s military or major corporations, they targeted smaller supply-chain businesses, such as logistics, fuel, and HR companies, leaking the resumes of thousands of Israelis with defense and security backgrounds. Simultaneously, hackers sent thousands of fake messages, seemingly from Israel’s home command system for emergency public safety orders, instructing people to avoid air raid shelters. They also attempted to compromise security cameras in Israel, a tactic one insider said could help track missile landings.
ETLM Assessment:
Although the two nations had not openly clashed until last year, these long-time adversaries have a history of exchanging cyberattacks. Israel, alongside the U.S., is widely credited with unleashing the Stuxnet virus that crippled centrifuges at Iran’s Natanz nuclear facility in 2010. Iran, in turn, is suspected of orchestrating attacks on Israel’s water systems in 2020. From what has emerged post-war, Israel’s cyber operatives seem to have delivered the most impactful strikes.
But Israel’s superior capability is unlikely to deter Iranian groups from further cyberattacks on Israel, especially since cyber operations are a simpler way to retaliate than military action after the severe damage Iran sustained in the physical conflict. The plausible deniability of cyberattacks allows both sides to keep striking despite pressure from the U.S. administration, which negotiated the ceasefire, to avoid renewing hostilities. The cyber war is thus likely to continue with a possibility of unintended second and third-order effects in the region and further beyond.
Australia warns of hackers targeting rare earths and AUKUS
Foreign operatives are intensifying efforts to target Australia across a range of industries, from rare earth minerals to Antarctic studies and even the theft of unique plant species, according to the nation’s intelligence agency, which has for the first time quantified the economic toll of espionage, including cyber-espionage. Australia’s participation in the AUKUS nuclear submarine agreement with the United States and United Kingdom has attracted “excessive and concerning” attention from foreign intelligence agencies, said Mike Burgess, director-general of the Australian Security Intelligence Organisation (ASIO).
The agency reported that espionage inflicted $8 billion hit on Australia’s economy in 2024 alone, based on a study conducted with the Australian Institute of Criminology—the first time ASIO has calculated the yearly cost of successful espionage operations. The agency called the figure conservative as it accounts for state-backed theft of intellectual property and the expenses of mitigating and responding to attacks, but omits cases where victims were unaware of being targeted or did not report incidents. This leaves out the most severe and far-reaching economic impacts of espionage.
Over the past three years, ASIO has uncovered and neutralized 24 significant espionage and foreign interference plots, surpassing the total from the prior eight years combined. The agency identified China, Russia, and Iran as particularly active in regional espionage, with foreign agents attempting to penetrate government institutions, defense contractors, media outlets, law firms, corporations, and universities.
ETLM Assessment:
As part of the “Five Eyes” intelligence-sharing alliance with the US, UK, Canada, and New Zealand, Australia and New Zealand have become focal points for foreign espionage, especially for China that seeks to dominate the Indo–Pacific region. Just this week, the FBI inaugurated the agency’s first office in New Zealand, aimed at countering the influence of the Chinese Communist Party in the Indo-Pacific, while also addressing narcotics trafficking and cyberattacks involving ransomware.
ASIO emphasized that foreign efforts to access sensitive information have expanded beyond conventional targets, with increased focus on scientific and technological research, mining operations, and commercial ventures. As CYFIRMA analysts warned in a report, the loss of intellectual property (IP) through cyber espionage and cybercrime constitutes the greatest transfer of wealth in history. U.S. companies alone loose around a quarter to half a trillion dollars annually through intellectual property theft, with over a hundred billion lost due to cybercrime – a number that can be tripled when the costs of downtime are taken into account. There are many challenges in the field of IP protection, however, the chief among them is China and its national program of integrating IP theft into the Chinese industry via cyber espionage, as its ambitions are curtailed by export restrictions. You can read the full report here.
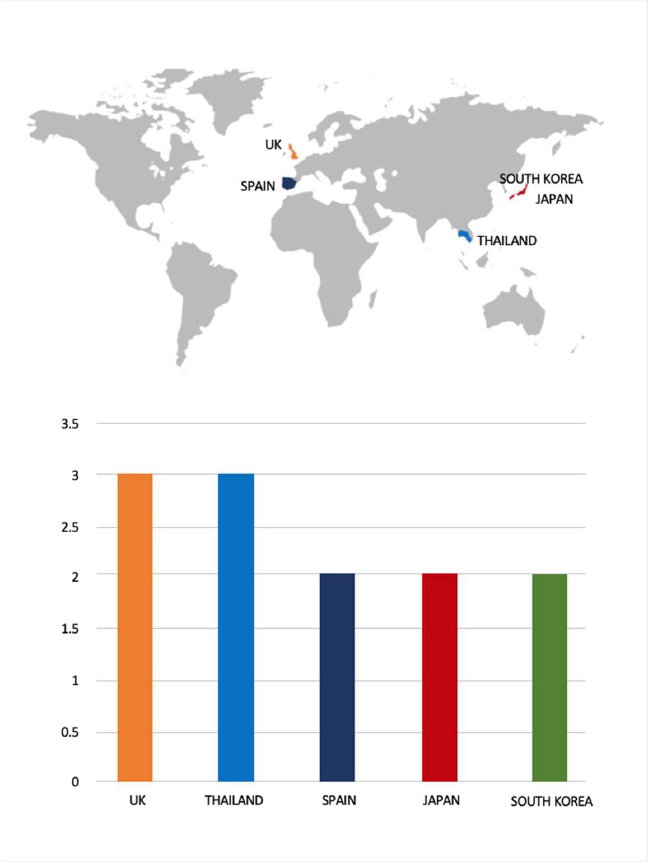
Qilin Ransomware Impacts Shinko Plastics Co. Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, Shinko Plastics Co. Ltd (https[:]//www[.]shinkopla[.]co[.]jp/), was compromised by Qilin Ransomware. Shinko Plastics Co., Ltd. specializes in the sale of plastic sheets, films, raw materials, related sub- materials, and finished plastic products. Serving a diverse range of industries, including construction, display, signage, home appliances, and industrial components. The company works with thousands of suppliers to support its operations. Headquartered in Tokyo, Shinko Plastics maintains multiple branches across Japan and operates overseas offices in Shanghai, China, and Bangkok, Thailand. The compromised data includes financial data, budgets, supplier and customer contacts, and other confidential and sensitive organizational data.
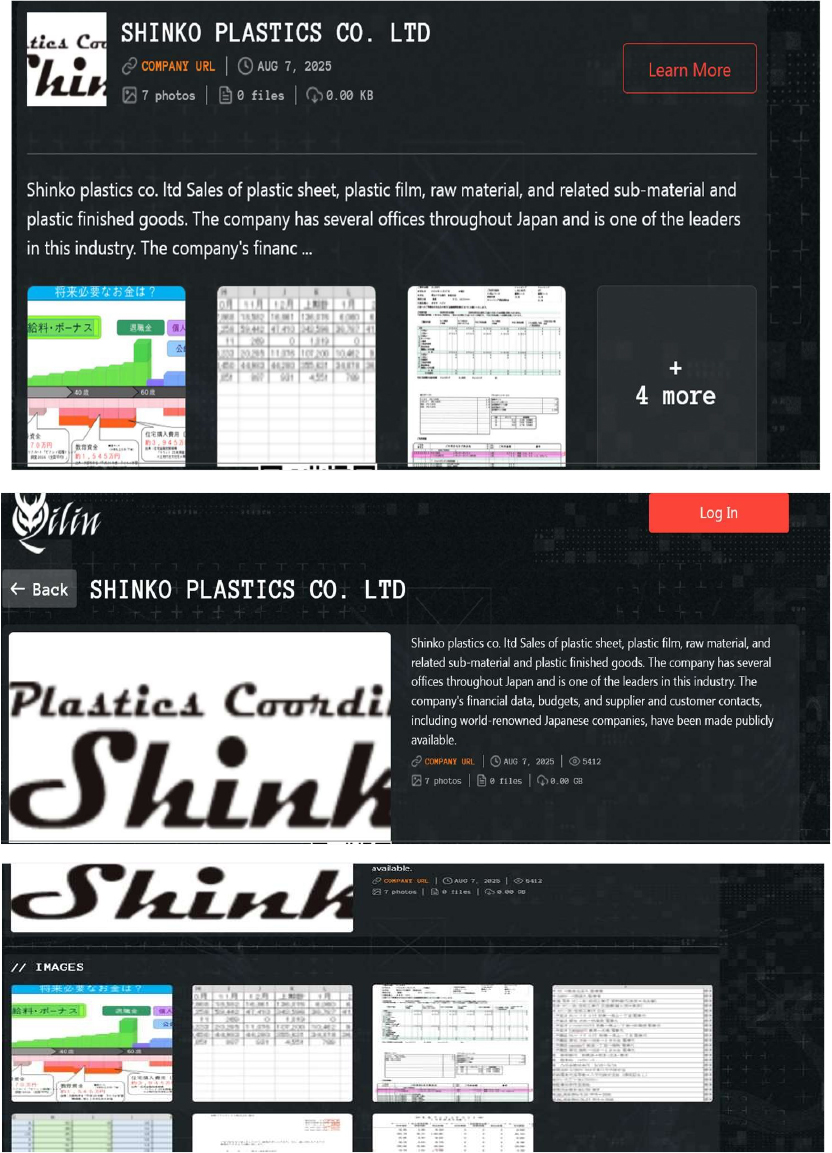
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Blacknevas Ransomware Impacts TANI & ABE
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, TANI & ABE (www[.]taniabe[.]co[.]jp), was compromised by Blacknevas Ransomware. TANI & ABE is a well-established Japanese intellectual property law firm offering a full spectrum of IP legal services with a client-centered approach. The compromised data consists of confidential and sensitive information related to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, BlackNevas ransomware is a sophisticated and multifaceted threat with extensible capabilities and a partnership model to maximize the impact and profitability of their attacks.
Vulnerability in WP Import Export Lite Plugin for WordPress
Relevancy & Insights:
The vulnerability exists due to insufficient validation of the file during file upload in the “wpie_parse_upload_data” function.
Impact:
A remote user can upload a malicious file and execute it on the server.
Affected Products:
https[:]//www[.]wordfence[.]com/threat- intel/vulnerabilities/wordpress-plugins/wp-import-export-lite/wp-import-export-lite- 3929-authenticated-subscriber-arbitrary-file-upload
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
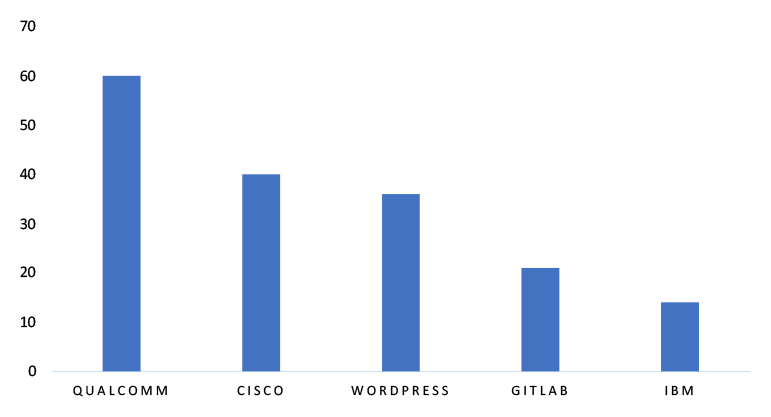
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
A vulnerability in WP Import Export Lite plugin for WordPress can pose significant threats to website integrity and user data. This can affect a wide range of industries using WordPress-based websites, such as e-commerce, education, media, and corporate platforms. Ensuring the security of the WP Import Export Lite plugin is essential for protecting content migration processes and preventing unauthorized access, data leakage, or code execution. Prompt patching and plugin hygiene are critical to mitigate the risks associated with content import/export functionality in WordPress environments.
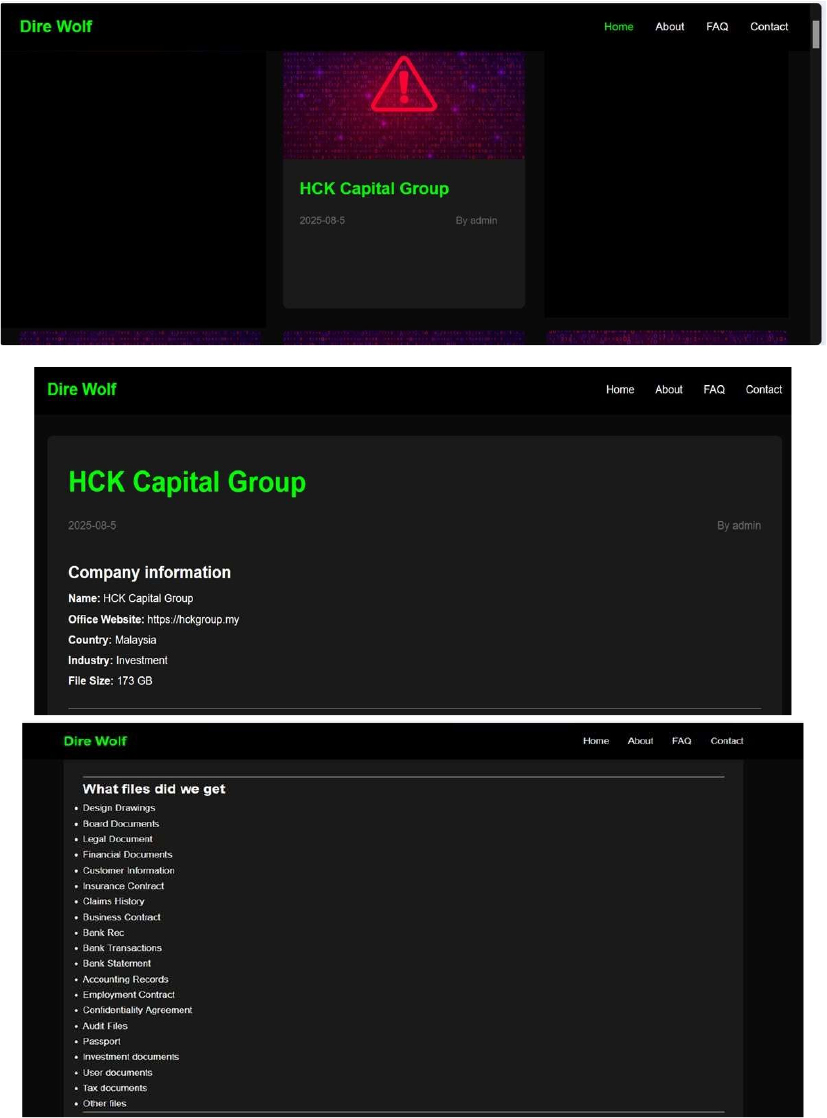
Dire Wolf Ransomware attacked and published the data of HCK Capital Group
Summary:
Recently, we observed that Dire Wolf Ransomware attacked and published the data of the HCK Capital Group (https[:]//hckgroup[.]my) on its dark web website. HCK Capital Group is a conglomerate based in Malaysia. The company specializes in integrated property development, education-oriented townships, and investment holdings. It is known for its broad business divisions related to property and corporate platforms. The ransomware attack resulted in a significant data breach, compromising roughly 173 GB of sensitive information. The exposed files include design drawings, board and legal documents, financial records, customer data, insurance contracts, claims histories, business agreements, bank reconciliations, transaction records, bank statements, accounting files, employment contracts, confidentiality agreements, audit reports, passports, investment documents, user records, tax files, and various other confidential materials.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors
Indonesian Logistics Giant PT. Tiki Jalur Nugraha Ekakurir (JNE) Data Advertised on a Leak Site
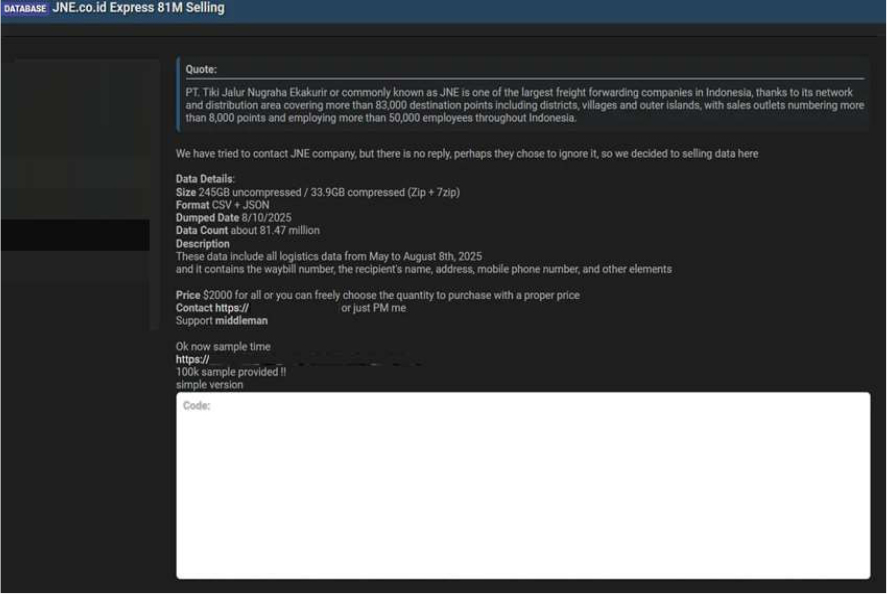
Summary:
The CYFIRMA Research team observed that a massive database allegedly belonging to the Indonesian freight forwarding company, PT. Tiki Jalur Nugraha Ekakurir (JNE) has been put up for sale on a dark web forum. A threat actor claims to have obtained approximately 81.47 million records, totalling 245 GB of uncompressed data. The actor stated they had attempted to contact JNE about the vulnerability but received no response, leading them to offer the database for sale. The data was reportedly exfiltrated on August 10, 2025.
JNE is one of the largest and most critical logistics and courier companies in Indonesia, boasting a network that covers over 83,000 destinations and employs more than 50,000 people. A breach of this magnitude could have severe consequences for millions of customers, exposing sensitive personal and shipping information. The threat actor has put the entire database up for sale for $2,000 and has provided a 100k-record sample to substantiate their claims.
The compromised information is said to encompass logistics data from May 2025 to August 8, 2025. The detailed records allegedly contain a wealth of personally identifiable information (PII) and shipping details. The exposed data reportedly includes:
Saudi Arabia’s online store Access advertised on a Leak Site
Summary:
The CYFIRMA Research team has identified a threat actor known as “Kazu” offering administrative panel access to an online store based in Saudi Arabia. The compromised Magento dashboard reportedly grants full control over customer information, orders, and sales analytics. According to the listing, the store has recorded over 9.7 million SAR in lifetime sales, with 66,050 customers and 72,077 orders. The access is being sold for USD 600.
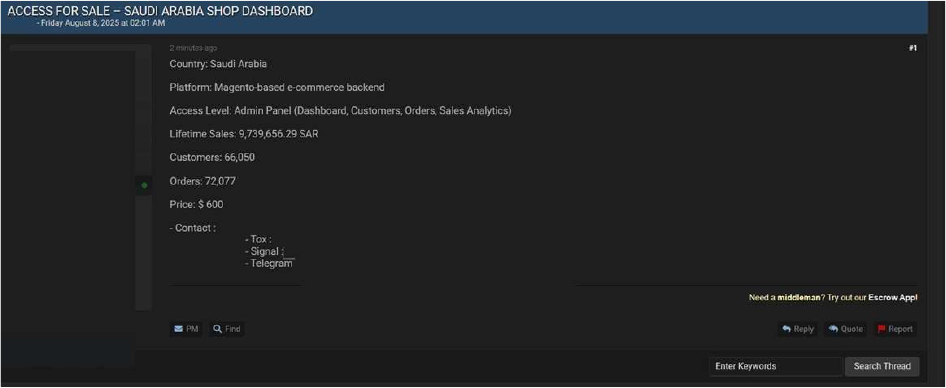
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Kazu” has recently emerged as a notably active group engaged in data leak activities. Credible sources have tied the group to multiple security breaches involving unauthorized system access and attempts to sell stolen data on dark web marketplaces. The group’s ongoing operations illustrate the persistent and escalating cyber threats stemming from underground forums. These incidents reinforce the critical need for organizations to bolster cybersecurity through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
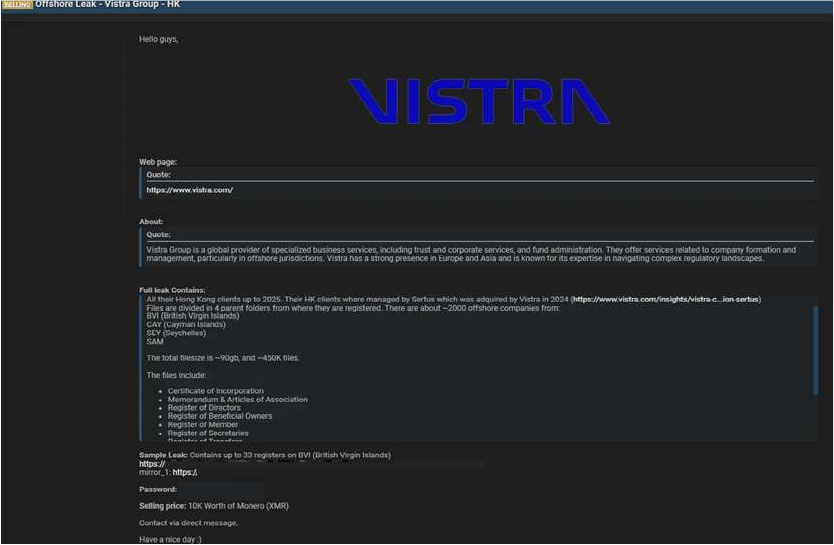
The CYFIRMA Research team observed that a threat actor has allegedly posted a significant trove of data for sale on a dark web forum, claiming it belongs to the clients of Vistra Group, a prominent global provider of corporate, trust, and fund administration services. Vistra is known for its specialization in managing company formations and navigating complex regulatory landscapes, particularly in offshore jurisdictions, making the potential exposure of its client data highly sensitive. The data is being sold for approximately 10,000 worth of Monero (XMR).
According to the dark web post, the leak originates from Vistra’s Hong Kong operations, specifically from clients previously managed by Sertus, a company acquired by Vistra in 2024. The total data size is reported to be around 90 GB, encompassing approximately 450,000 files related to nearly 2,000 offshore companies registered in jurisdictions like the British Virgin Islands, Cayman Islands, and Seychelles. The actor claims the data is current up to 2025.
The compromised information is said to be extensive and contains highly confidential corporate and personal details. The threat actor listed the types of data allegedly included in the leak:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
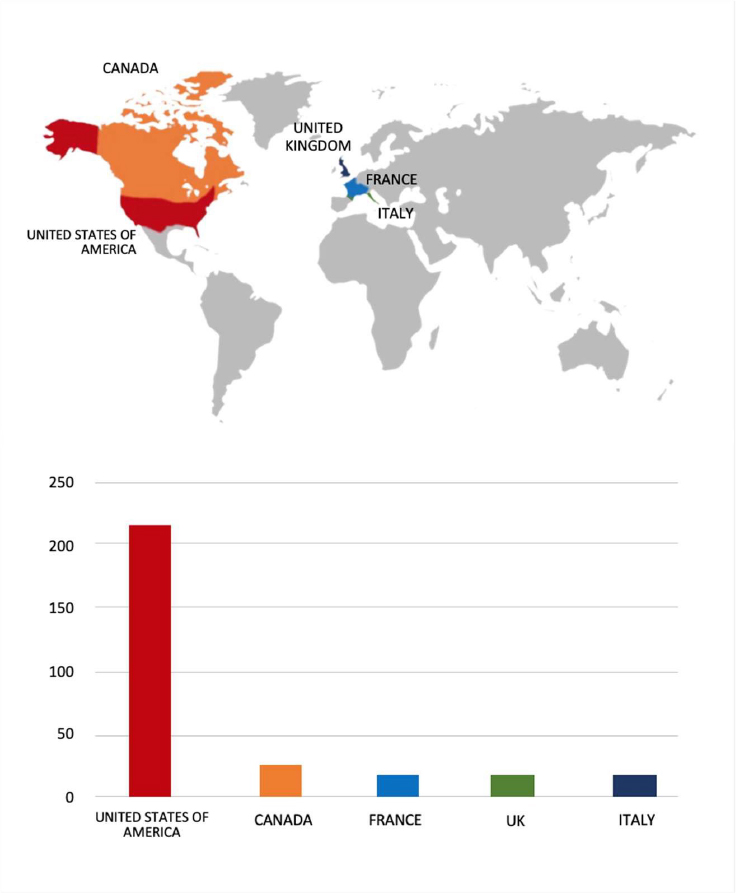
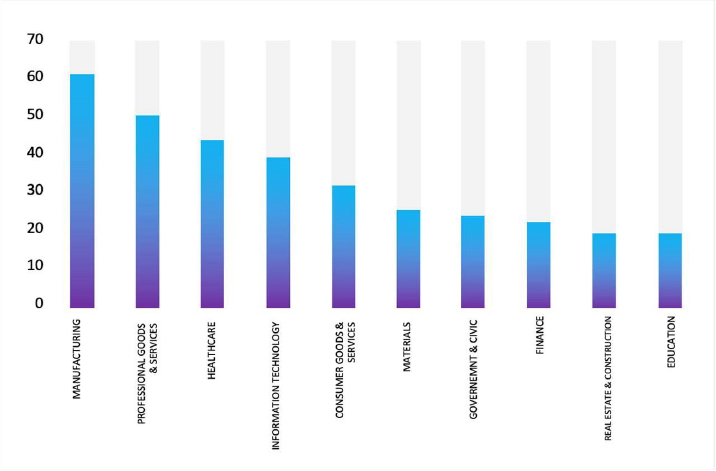
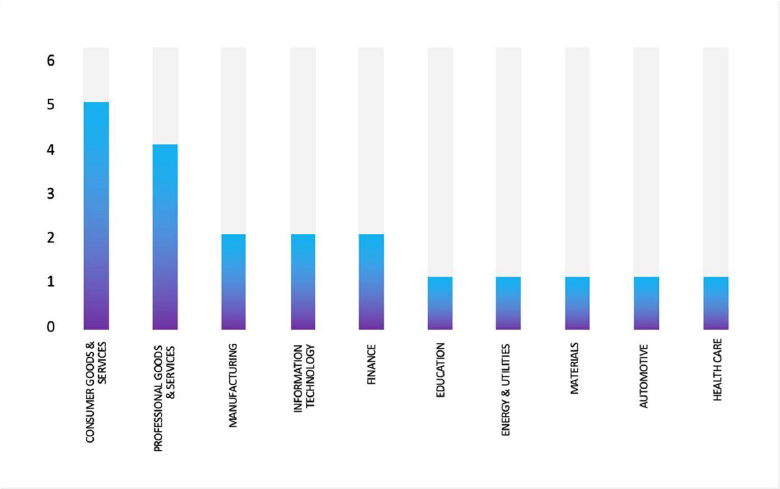
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.