


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found NOBACKUPS Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
NOBACKUPS Ransomware
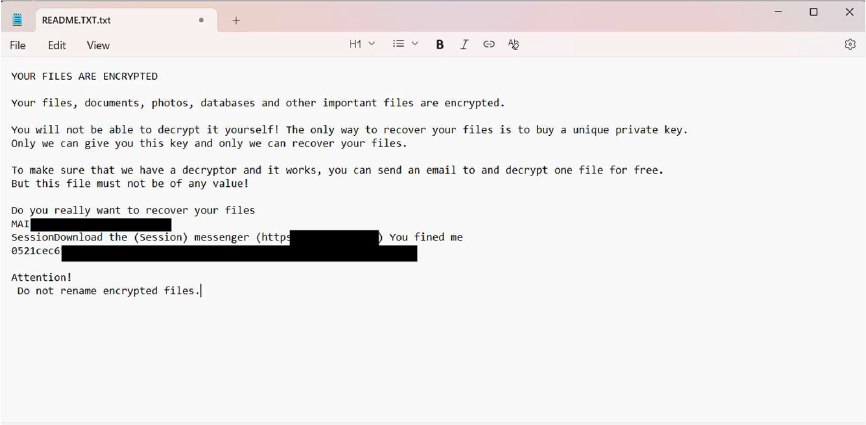
Researchers have identified a new ransomware variant named NoBackups, which appends the “.nobackups” extension along with a unique victim ID to encrypted files. It drops a ransom note (“README.TXT”) demanding payment for a decryption key and threatens to leak stolen data if not contacted within 24 hours.

The ransom note claims all user data has been encrypted using asymmetric cryptography, with file recovery dependent on a unique private key controlled by the attacker. A single non-critical file can be decrypted for verification. Communication is restricted to a Mailum (email service) email and the Session messenger, indicating use of anonymity-focused platforms. Victims are cautioned against file renaming or using third-party recovery tools, though no firm deadline or penalty structure is outlined.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Execution | T1059.001 | Command and Scripting Interpreter : PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter : Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter : Visual Basic |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1137.001 | Office Application Startup: Office Template Macros |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1222.001 | File and Directory Permissions Modification: Windows File and Directory Permissions Modification |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1007 | System Service Discovery |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol (RDP) |
| Lateral Movement | T1570 | Lateral Tool Transfer |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Command & Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command & Control | T1095 | Non-Application Layer Protocol |
| Command & Control | T1105 | Ingress Tool Transfer |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA assesses that the NOBACKUPS ransomware group is undergoing rapid operational advancement. The group is likely to adopt a more aggressive extortion model, not only encrypting data but also exfiltrating sensitive information to pressure victims through potential public exposure. As NOBACKUPS develops more automated workflows and leverages stealthier lateral movement techniques, it appears to be scaling toward broader, coordinated campaigns. The lack of a Tor- based leak site or established public branding indicates that this may be a low- visibility or emerging actor still shaping its operational identity but with the potential to evolve into a persistent global threat.
Sigma rule:
title: Uncommon File Created In Office Startup Folder tags:
– attack.resource-development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_*
falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high
Source: Surface Web
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan| Objectives: Credential Stealing, Data Exfiltration, Remote Access| Target Technology: Android OS | Target Industry: Financial Sector |Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “DoubleTrouble” is trending.
About Malware DoubleTrouble
Researchers have identified the latest variant of DoubleTrouble, a fast-evolving banking Trojan that has steadily enhanced both its delivery strategy and range of functions. Earlier versions mimicked legitimate European banking websites and relied on pop-up overlays to trick victims into sharing login details. In its latest campaign, DoubleTrouble now leverages Discord-hosted APKs for malware delivery — marking a disturbing trend of mobile threats being distributed via social media platforms. Alongside this shift, its capabilities have grown significantly, expanding from simple credential theft to more intrusive actions, including screen-capture and broader remote-control style commands.
Technical Analysis
This variant introduces several notable enhancements. The malware uses deceptive coding tactics by assigning random two-word names to its internal components, making it harder for analysts to interpret its behavior through static inspection. This deliberate confusion helps the threat stay hidden during early analysis. It also takes advantage of Android’s Accessibility Services to silently carry out malicious tasks. To secure the necessary permissions without raising suspicion, the malware hides its harmful code inside the app’s internal files and presents itself as a harmless extension. By leveraging the Google Play icon to give the impression of being legitimate, it prompts the victim to enable accessibility access. Once granted, it quietly begins stealing information and controlling device functions in the background.
Key Functional Capabilities of DoubleTrouble
The latest variant of DoubleTrouble showcases a broader and more intrusive set of features designed to strengthen device control, evade detection, and maximise data theft. Its primary capabilities include:
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1660 | Phishing |
| Defense Evasion | T1655.001 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1516 | Input Injection |
| Defense Evasion | T1406.002 | Obfuscated Files or Information: Software Packing |
| Credential Access | T1414 | Clipboard Data |
| Credential Access | T1417.001 | Input Capture: Keylogging |
| Credential Access | T1417.002 | Input Capture: GUI Input Capture |
| Discovery | T1418 | Software Discovery |
| Discovery | T1426 | System Information Discovery |
| Collection | T1513 | Screen Capture |
| Collection | T1417.001 | Input Capture: Keylogging |
| Collection | T1417.002 | Input Capture: GUI Input Capture |
| Collection | T1414 | Clipboard Data |
| Command & Control | T1637 | Dynamic Resolution |
| Command & Control | T1521 | Encrypted Channel |
| Exfiltration | T1646 | Exfiltration Over C2 Channel |
| Impact | T1516 | Input Injection |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that DoubleTrouble’s shift toward social media-based delivery could pave the way for broader exploitation across personal mobile devices, particularly as more people use their phones for accessing a mix of private and work-related services. This indirect pathway raises the risk of unauthorized entry into connected accounts, stored credentials, and sensitive applications. As the malware evolves, its tactics may become increasingly tailored to specific locations, user profiles, or commonly used tools, creating more convincing prompts that blend into everyday device usage and making detection significantly harder. Left unchecked, such campaigns could start a new phase of persistent mobile surveillance, allowing attackers to quietly monitor behaviour, gather insights over time, and manipulate digital activity, while bypassing traditional security controls and discreetly eroding confidence in mobile- based access mechanisms.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule DoubleTrouble_Indicators
{
meta:
description = “Detects DoubleTrouble Malware indicators” author = “CYFIRMA”
malware_family = “DoubleTrouble” strings:
// IP Addresses
$ip_1 = “104.238.34.15”
$ip_2 = “77.105.164.255”
$ip_3 = “41.216.183.248”
$ip_4 = “82.115.223.2”
// Domains
$domain_1 = “begans.cfd”
$domain_2 = “unicredit.appaggiornamento.com”
$domain_3 = “volksbank.applogininfo.com”
// SHA256 Hashes
$sha256_1 = “7a924c7bdb1fd32cfc838f3cdd624abc10da19713c123b84a0f2325fef3d2bbc”
$sha256_2 = “2f9d70c75330b49a1a97479587d5e0b6016cf8004e454badf2b021e8bbb28469”
$sha256_3 = “cefc92b5fecf162a2840d2c42d9411899b45704a1ee5a60cf2bc093a01e46c4d”
$sha256_4 = “89060156441434da8f016bd872aeaa542d32820d49b3c00bce4426120110282e”
$sha256_5 = “d181f30e0404c3ff85af22833600c3666c54cf904cc6387b926c9ad321c1206e”
$sha256_6 = “7eb4305dbc23c5acc2c35e0d4ccd417e9448be27facca1a1d42408464e156825”
$sha256_7 = “b187a29d1e9e3e616f166d2fa3076bc22b9268d0b7b01b59ea8bd89f39a90010”
$sha256_8 = “02e920d427b73d96a941d9eb47efaa9c55b8c43afbc111a28407184046feecfd”
$sha256_9 = “20db498b222a36896b92ed67fce902e45fb90f967d8a10786f1d0a55e03c2c31”
$sha256_10 = “f22f8a8cbe73248e04e5e5271df969d087967719f3aca6af58ef00dfd2f35f31”
$sha256_11 = “c247d9ec3fa20803ba769308c66d2b4c836ca0ac90f71d68a07f44d57eb8a501”
$sha256_12 = “b3d134eca184962eae23a8ade27b1faca5a48bd0211bc5a401ddecd045652cee”
$sha256_13 = “5a11f0cc9e3d8a080f6721964d3414ea638edc0fd4d22d3901f469feae4a8fa4”
$sha256_14 = “84faf02309080076fe526f8bc8c427fa6bb407c5da42c31866ba47c1478cbde9”
$sha256_15 = “d002f0e354841d7090df5f20dd2b2b4c8b9d2216ce331690807bb58414390a29”
$sha256_16 = “7903328e73a07a9d27a4d0ea954bed96385f37bbd4d9afd81faec443588ca890”
$sha256_17 = “b9a13c4fe93d5b42dc38ae1c864d17388a32bcb89e7279f4bb649c92f67f1498”
$sha256_18 = “64977c8e167609f52ebd89a4eda1a83282e3b9ea07115bf68acd7d9836e04a1b”
$sha256_19 = “b7887187e30583b9e543af73640049f9e555a32a1691f6fde7b3a3ec7858dc7a”
$sha256_20 = “fd558205fddb4c681c3799a28c97903ab19dfc96776df55d81edd835051523ed”
$sha256_21 = “d45cb00646d1ead9b54810be048323179414097087ef873d0b86d8d9bcf77217”
$sha256_22 = “e3f84482977854a5c79d253f6dcca83b2911b8c1dc7cc76b533bdc7fc31255c9”
$sha256_23 = “099a7a5bcceac0f91c63ac52b04213001b21afaeeac161b9adb2131fa62b4c57”
$sha256_24 = “cbfe190a81f5f10f4d7b5746fec7af51f8f02900e17f45b423aa768d1d013bb4”
$sha256_25 = “6bb0b6996adf1ebfd2291aca16622885c5072350e71740f9f0046f66c65bec5c”
$sha256_26 = “93601b436ccd7a7abde1546bd346fab820fe046164262c9105235e15f92a11e4”
$sha256_27 = “73ca0eb7bbaabb7f56cda98b28a483901527710fc1b6d4326503eda0cc884ba3”
$sha256_28 = “882b635024acbedb7b280ff6e7c2a3c334228770509a0855639073d9974ab03b”
$sha256_29 = “e8e3f3846f2319b7b739f04eb1b83b043e815d7a06fcc759b6c07c1371d3f6d6”
$sha256_30 = “e9c6cad185dac1513b7c0f62951a264165b75b40be61373c80835a9a10502579”
$sha256_31 = “91f5a4164bd557b34442550d204ad5e024dc02e2d5febf86699a7feae0a38480”
$sha256_32 = “2fb9ea57928223260abaffcbdbc11c01513d0f49c20c8e850113de3e7b339946”
$sha256_33 = “3e3a5d35eb5e11c3bfd63e75abd7f5022e8ee7288bc76a041354813f6ca601ce”
$sha256_34 = “05e00998bc5b18e3ac71987eeed9009ee8ba65de3f07ee90e761ace8c62878e1”
condition:
any of ($ip*) or
any of ($domain*) or any of ($sha256*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Scattered Spider: A Deep Dive into a High-Impact Threat Actor
About the Threat Actor
The threat actor was observed in late 2022, initially identified through its use of the 0ktapus phishing kit, a prebuilt phishing framework that included ready-made templates and hosting infrastructure designed to streamline credential theft campaigns. The group’s toolkit spans from hands-on social engineering and smishing (SMS phishing) attacks to the adept use of specialized penetration testing and digital forensics tools, providing it with a distinct operational edge.
Scattered Spider is also known to collaborate with prominent ransomware groups such as BlackCat (ALPHV), RansomHub, Qilin, and DragonForce, some of which are linked to Russian-speaking cybercriminal ecosystems. These alliances suggest a flexible and opportunistic threat actor capable of integrating into broader cybercrime operations while maintaining its own technical sophistication and agility.
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1589.001 | Gather Victim Identity Information: Credentials |
| Reconnaissance | T1598 | Phishing for Information |
| Reconnaissance | T1598.001 | Phishing for Information: Spear phishing Service |
| Reconnaissance | T1598.004 | Phishing for Information: Spear phishing Voice |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566.004 | Phishing: Spear phishing Voice |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1204 | User Execution |
| Persistence | T1556.006 | Modify Authentication Process: Multi-Factor Authentication |
| Persistence | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Persistence | T1133 | External Remote Services |
| Persistence | T1136 | Create Account |
| Persistence | T1098.005 | Account Manipulation: Device Registration |
| Persistence | T1098.003 | Account Manipulation: Additional Cloud Roles |
| Persistence | T1098.001 | Account Manipulation: Additional Cloud Credentials |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1098.001 | Account Manipulation: Additional Cloud Credentials |
| Privilege Escalation | T1098.003 | Account Manipulation: Additional Cloud Roles |
| Privilege Escalation | T1098.005 | Account Manipulation: Device Registration |
| Privilege Escalation | T1484.002 | Domain or Tenant Policy Modification: Trust Modification |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1564.008 | Hide Artifacts: Email Hiding Rules |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1484.002 | Domain or Tenant Policy Modification: Trust Modification |
| Defense Evasion | T1656 | Impersonation |
| Defense Evasion | T1556.006 | Modify Authentication Process: Multi-Factor Authentication |
| Defense Evasion | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Defense Evasion | T1578.002 | Modify Cloud Compute Infrastructure: Create Cloud Instance |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1556.006 | Modify Authentication Process: Multi-Factor Authentication |
| Credential Access | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Credential Access | T1621 | Multi-Factor Authentication Request Generation |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.006 | OS Credential Dumping: DCSync |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Credential Access | T1552.004 | Unsecured Credentials: Private Keys |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1538 | Cloud Service Dashboard |
| Discovery | T1580 | Cloud Infrastructure Discovery |
| Discovery | T1217 | Browser Information Discovery |
| Discovery | T1087.004 | Account Discovery: Cloud Account |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1087.003 | Account Discovery: Email Account |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1069.003 | Permission Groups Discovery: Cloud Groups |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1021.007 | Remote Services: Cloud Services |
| Collection | T1530 | Data from Cloud Storage |
| Collection | T1213.002 | Data from Information Repositories: Sharepoint |
| Collection | T1213.003 | Data from Information Repositories: Code Repositories |
| Collection | T1213.005 | Data from Information Repositories: Messaging Applications |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1572 | Protocol Tunneling |
| Command and Control | T1090 | Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Command and Control | T1102 | Web Service |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1657 | Financial Theft |
Latest Developments Observed
The threat actor is suspected of targeting a third-party platform used by an Australian airline, resulting in the compromise of customer data. The security breach is suspected to have originated when a threat actor targeted the airline’s call centre, subsequently gaining unauthorized access to a third-party customer service platform integrated within the support infrastructure. This indirect method allowed attackers to bypass direct defenses and reach sensitive data. The likely motive appears to be data exfiltration, with intentions to leak or sell the information for financial gains.
ETLM Insights
Scattered Spider is a sophisticated threat actor known for its collaboration with prominent ransomware groups operating under the Ransomware-as-a-Service (RaaS) model and leveraging it extensively for its objectives. The group has increasingly leveraged advanced tactics, techniques, and procedures (TTPs), including various levels of social engineering methods and living-off-the-land (LOTL) techniques, to infiltrate organisations. Additionally, targeting through supply chains and third-party service providers, the threat actor looks to bypass the robust security controls of organisations and target them in indirect ways by exploiting trusted relationships and targeting external vendors. Our assessments suggest the group may be providing indirect support or operational assistance to nation-state actors and their country’s origin intelligence agencies, raising concerns among global intelligence and cybersecurity agencies about its broader strategic objectives & affiliations, expanding digital footprint.
YARA Rules
rule Scattered_Spider_IOCs
{
meta:
description = “Detects domains and IP addresses associated with Scattered Spider infrastructure”
author = “CYFIRMA” date = “2025-08-04”
threat_actor = “Scattered Spider / 0ktapus / UNC3944 / Storm-0875” strings:
// Domains
$d01 = “expediagroup-servicenow.com”
$d02 = “fico-servicenow.com”
$d03 = “servicenow-help.com”
$d04 = “synchrony.servicenow-help.com”
$d05 = “realogy-hr.com”
$d06 = “connect-asurion.net”
$d07 = “supporthub-iqor.com”
$d08 = “corp-foundever.com”
$d09 = “corp-foundever.net”
$d10 = “foundever-sso.com”
$d11 = “ibexglobai.com”
$d12 = “creditkarma-help.com”
$d13 = “jacksonhewitt-service.com”
$d14 = “uscc-hr.com”
$d15 = “five9-hr.com”
$d16 = “taskus-sso.com”
$d17 = “grubhub-support.com”
$d18 = “kemper-support.com”
$d19 = “doordash-support.com”
$d20 = “rbx-hr.com”
$d21 = “block-hr.com”
$d22 = “hr-intercom.com”
$d23 = “securian-hr.com”
$d24 = “klaviyo-hr.com”
$d25 = “freshworks-hr.com”
$d26 = “okta-247.com”
$d27 = “servicenow-hrblock.com”
$d28 = “accenture-help.com”
$d29 = “pfchangs-support.com”
$d30 = “x-sso.com”
$d31 = “xn--gryscale-ox0d.com”
$d32 = “twitter-okta.com”
$d33 = “sts-vodafone.com”
$d34 = “sso-instacart.com”
// IP addresses
$ip01 = “143.244.162.134”
$ip02 = “64.176.214.51”
$ip03 = “45.32.171.19”
$ip04 = “104.248.120.34”
$ip05 = “64.95.10.189”
$ip06 = “67.217.228.42”
$ip07 = “159.65.72.54”
$ip08 = “45.32.230.32”
$ip09 = “45.77.92.214”
$ip10 = “143.198.116.59”
$ip11 = “137.220.50.227”
$ip12 = “45.76.247.99”
$ip13 = “155.138.229.198”
$ip14 = “144.202.57.16”
$ip15 = “138.68.255.62”
$ip16 = “137.220.43.146”
$ip17 = “68.183.116.246”
condition:
any of ($d*) or any of ($ip*)
}
Recommendations Strategic
Management
Tactical
China accuses the US of hacking Beijing’s defense industry
China has accused the US of exploiting vulnerabilities in Microsoft Corp.’s email servers to steal military data and launch cyberattacks on its defense industry. The Cyber Security Association of China, backed by the Cyberspace Administration of China, claimed US actors conducted two significant cyberattacks on Chinese military companies, exploiting Microsoft Exchange flaws to control a key defense sector company’s server for nearly a year.
Conversely, Western nations have frequently accused China of similar cyberattacks using Microsoft Exchange. In 2021, a suspected Chinese operation compromised tens of thousands of servers globally. In 2023, another alleged Chinese attack targeted senior US officials’ email accounts, with a US review later criticizing Microsoft for multiple security failures. Recently, Microsoft reported Chinese state-backed hackers exploiting vulnerabilities in its SharePoint software.
ETLM Assessment:
A US Embassy spokesperson in Beijing declined to address the specific allegations but stated that China remains the most active and persistent cyber threat to the US government, private sector, and critical infrastructure networks. The US is collaborating with allies to counter threats from Chinese state-sponsored groups like Salt Typhoon and Volt Typhoon.
In April, China accused three NSA employees of hacking systems related to the Asian Winter Games in Harbin, targeting sensitive personal data. Unlike the US, which has publicly named and charged alleged Chinese hackers, China has typically avoided directly accusing American spies.
The United States and China, as the world’s leading superpowers, are also cyber superpowers, where mutual espionage through sophisticated cyberattacks is an expected and routine aspect of their strategic rivalry.
Russian Hackers Posing as a Cybersecurity Company to Spy on Embassies
A notorious Russian hacking group, Turla (also known as Secret Blizzard), has been posing as the Russian cybersecurity firm Kaspersky and leveraging Russia’s internet service providers to conduct a large-scale cyber-espionage campaign targeting foreign embassies in Moscow, according to recent reporting by researchers. The hackers redirected victims’ internet traffic and deployed malware, disguised as Kaspersky software, to gather intelligence, without specifying targeted embassies. Kaspersky stated that trusted brands are often exploited without their consent and urged users to download software only from official sources and verify communications. The malware, ApolloShadow, decrypts targets’ internet activity, exposing sensitive data like browsing habits and credentials.
ETLM Assessment:
Turla, linked to Russia’s Federal Security Service (FSB) and active for over 25 years, is considered one of the world’s most sophisticated hacking groups; in 2023, the US Department of Justice disrupted its global network used for Moscow’s operations. The Russian Ministry of Foreign Affairs did not respond to requests for comment. The campaign coincides with heightened Russia-West tensions, particularly due to Russia’s war in Ukraine, while President Putin’s push for domestic internet control, including a super app and potential WhatsApp ban, is bolstered by Russia’s SORM surveillance system, which likely facilitates such espionage.
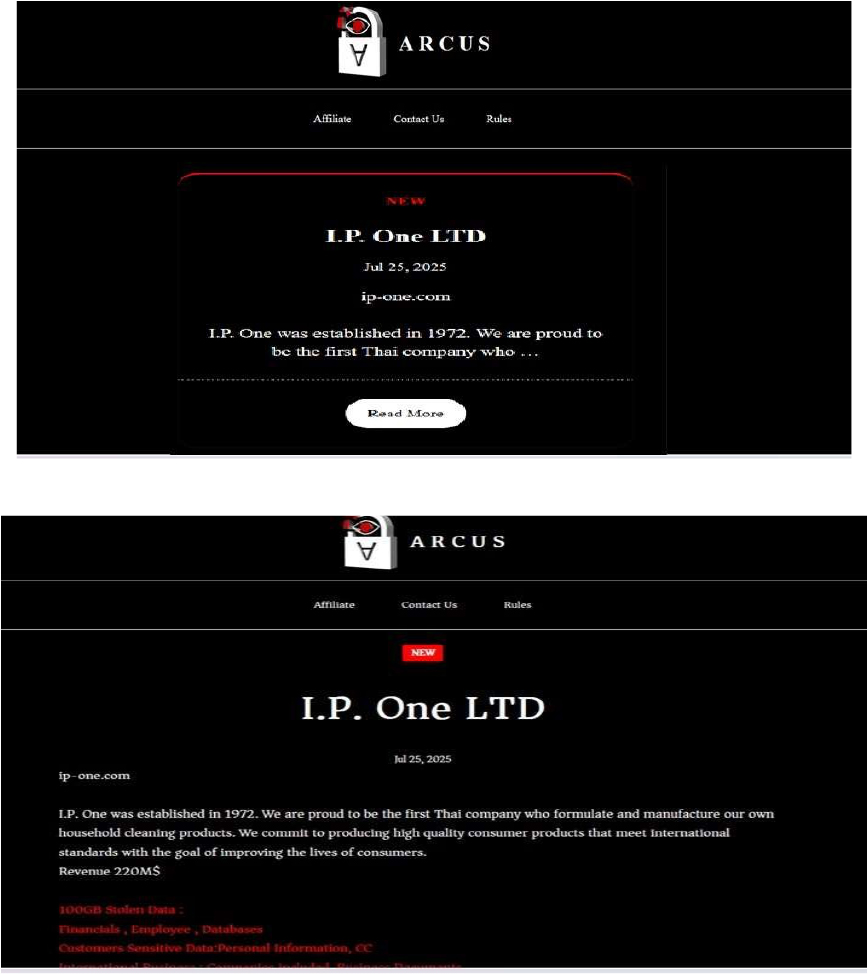
ArcusMedia Ransomware Impacts I.P. One LTD
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, I.P. One LTD (https[:]//www[.]ip-one[.]com/), was compromised by ArcusMedia Ransomware. I.P. One LTD is a pioneering Thai company, recognized as the first in the country to formulate and produce household cleaning products. It specializes in both household and personal care segments, offering a wide range of well-established brands. Its portfolio includes Hygiene (fabric care such as detergents, softeners, and bleach), Vixol (bathroom cleaners), Whiz (general household cleaners), Ivy (UHT drinking yogurts and Asian beverages), and personal care lines like Dance and Focus. The compromised data includes financial records, employee information, and internal databases. It also contains sensitive customer data, such as personal details, credit card information, documents related to international business companies, and other confidential business files. The total volume of the exposed data is estimated to be approximately 100 GB.
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, ArcusMedia ransomware represents a significant new threat in the cybersecurity landscape, characterized by its sophisticated tactics and aggressive approach to extortion. Organizations are advised to enhance their cybersecurity defenses, including employee training on phishing awareness, regular updates to systems, and comprehensive incident response plans to mitigate risks associated with this evolving threat actor. Continuous monitoring of ArcusMedia’s activities will be essential for understanding its impact on global cybersecurity efforts.
Dire Wolf Ransomware Impacts the MGI Singapore PAC
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, MGI Singapore PAC (https[:]//www[.]mgialliance[.]sg), was compromised by Dire Wolf Ransomware. MGI Alliance Singapore PAC is a professional firm specializing in auditing, accounting, and a broad suite of business advisory services for companies in Singapore. The firm operates as part of MGI Worldwide, an international network of independent audit, tax, accounting, and consulting firms. The compromised data includes a wide range of sensitive information, such as administration records, auditing data, commercial advertising materials, intellectual property assets, tax- related documents, and customer information. The total volume of exposed data is estimated to be approximately 226 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion- based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
Vulnerability in ZTE ZXHN-F660T and ZXHN-F660A
Relevancy & Insights:
The vulnerability exists due to the use of weak credentials.
Impact:
A remote attacker on the local network can gain access to the target device.
Affected Products:
https[:]//jvn[.]jp/en/jp/JVN66546573/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
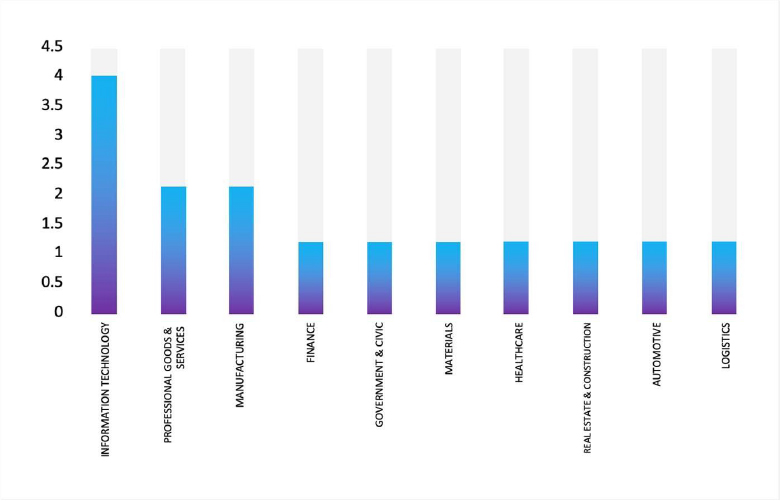
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in ZTE ZXHN-F660T and ZXHN-F660A can pose significant threats to user privacy and security. This can impact various industries globally, including telecommunications, technology, finance, and beyond. Ensuring the security of ZTE ZXHN-F660T and ZXHN-F660A is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding broadband network access, customer premises equipment (CPE) functionality, and secure internet connectivity across different geographic regions and sectors.
Crypto24 Ransomware attacked and published the data of TransCore ITS, LLC
Summary:
Recently, we observed that Crypto24 Ransomware attacked and published the data of the TransCore ITS, LLC (https://transcore.com/) on its dark web website. TransCore ITS, LLC maintains a regional office in the United Arab Emirates, supporting local and regional transportation infrastructure initiatives.
Headquartered in Nashville, Tennessee, USA, TransCore is a global leader in transportation solutions, specializing in electronic toll collection, traffic management, and Intelligent Transportation Systems (ITS). Its UAE presence plays a key role in delivering advanced mobility and tolling solutions across the region. The ransomware attack led to a significant breach of the internal network at TransCore’s Dubai office, resulting in the exfiltration of over 200 GB of sensitive internal data. The compromised information includes in-development source code, complete file sets from both active and archived client projects, internal financial records, and a substantial volume of unprotected customer data—all of which were stored without adequate security controls. The leak also reveals clear violations of multiple non-disclosure agreements (NDAs), exposing confidential third- party materials and sensitive client information.
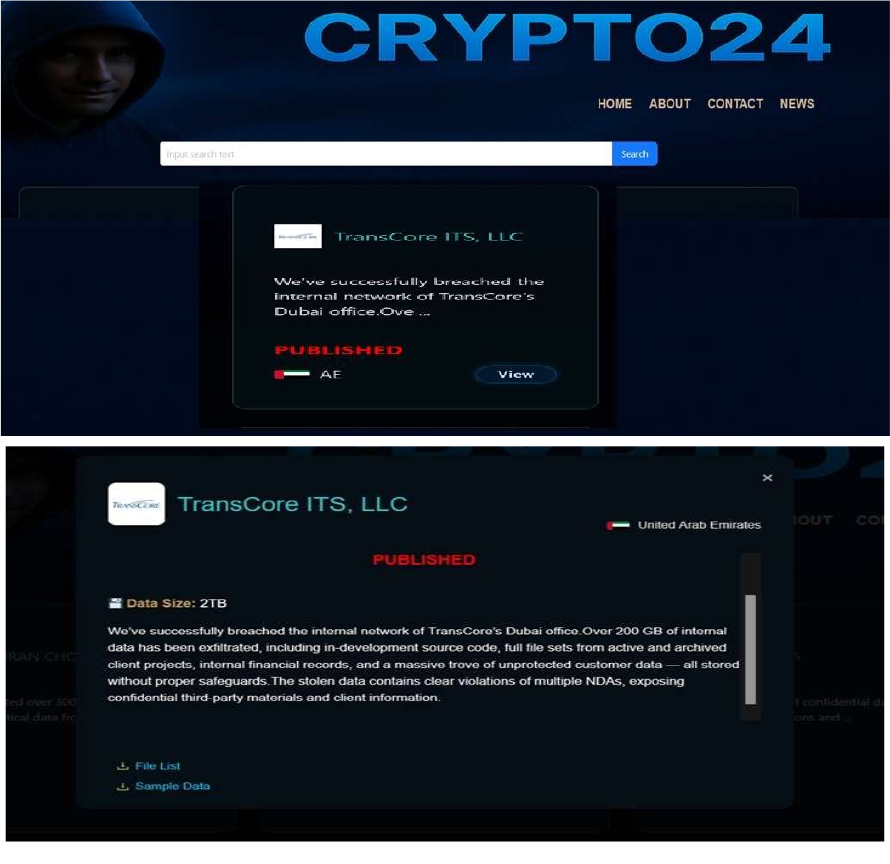
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Crypto24 is a high-profile ransomware group known for rapid, high-volume data theft, fast encryption, and aggressive pressure tactics that combine classic ransom demands with sensitive data leaks.
Organizations in Asia have been primary targets, with attacks resulting in the exfiltration and exposure of terabytes of sensitive information. Recovery without payment is rarely feasible, underscoring the need for robust defense and backup strategies.
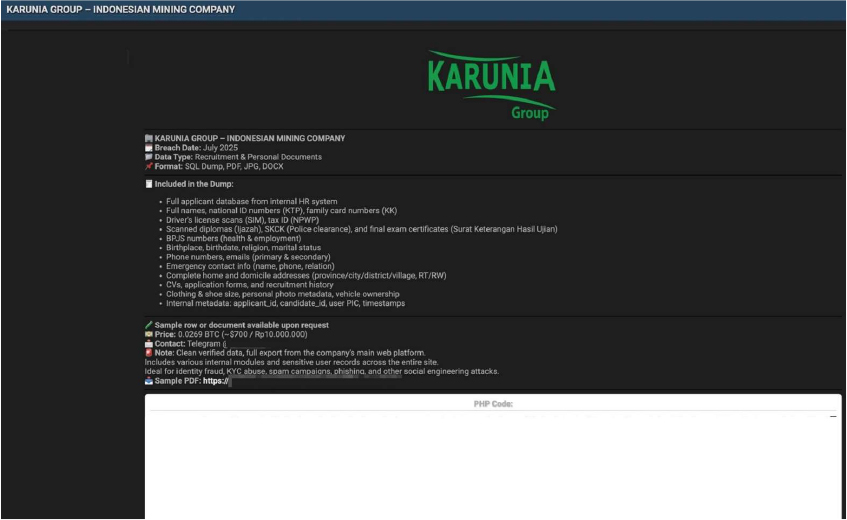
Karunia Group Data Advertised on a Leak Site
Summary: The CYFIRMA Research team observed that a threat actor, “ParanoidHax,” has allegedly put a sensitive database belonging to the Karunia Group up for sale on a dark web forum. The victim, Karunia Group, is a prominent mining company based in Indonesia. According to the post made on a hacking forum, the data was exfiltrated in July 2025 and contains a vast trove of personal and recruitment documents pertaining to applicants. The seller has listed the data for approximately $700, payable in Bitcoin (0.0269 BTC).
The data, presented in SQL, PDF, JPG, and DOCX formats, appears to be a complete export from the company’s internal Human Resources (HR) web platform. The threat actor claims the dump is ideal for malicious activities such as identity fraud, KYC (Know Your Customer) abuse, and targeted phishing campaigns. The sheer breadth of the allegedly leaked personally identifiable information (PII) poses a significant risk to the individuals whose data has been compromised.
The seller provided a detailed list of the information contained within the breached database, which allegedly includes:
The UAE Equestrian and Racing Federation (UAEERF) Data Advertised on a Leak Site
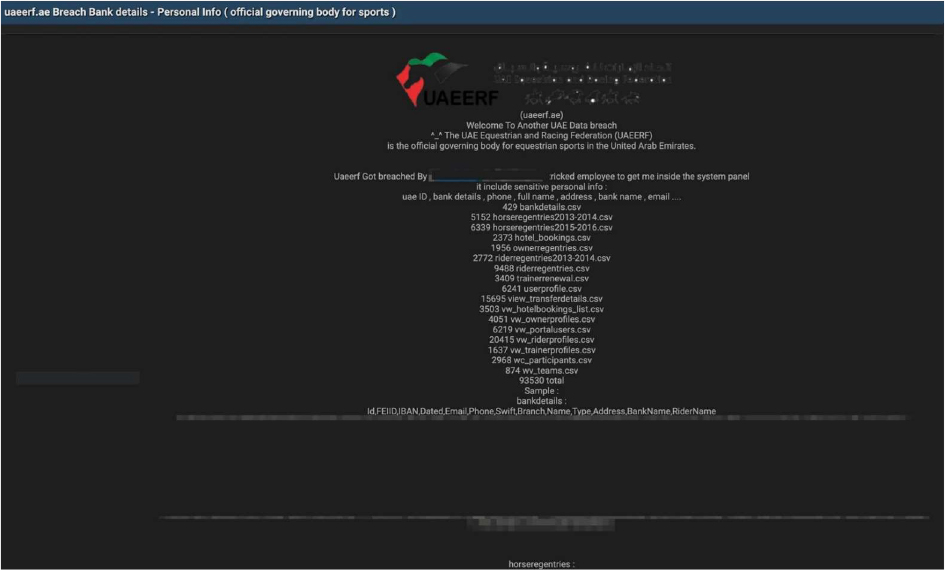
Summary:
The CYFIRMA Research team has identified a data breach involving the UAE Equestrian and Racing Federation (UAEERF), the official authority overseeing equestrian sports in the United Arab Emirates. According to claims made by a threat actor on a dark web forum, the breach was the result of a successful social engineering attack that deceived an employee into granting system access. As a result, a substantial volume of sensitive personal and financial data belonging to federation members — including riders, owners, and trainers — was allegedly compromised.
The data, allegedly totaling over 93,000 records, was posted online and appears to contain highly sensitive details. The leaked information allegedly includes full names, Emirates ID numbers, bank account details (including IBANs), phone numbers, physical addresses, and email addresses. The breach also exposed detailed records related to horse registrations, hotel bookings for events, and user profiles, painting a comprehensive picture of the federation’s operations and its members’ private information.
The threat actor shared a list of compromised database files, highlighting the breadth of the exposed data. The leak contains specific information about riders, horse owners, trainers, and even event participants, dating back over a decade in some cases. The files include:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “ParanoidHax” has recently emerged as a highly active group involved in data leaks. Trusted sources have linked the group to several security breaches, where they gained unauthorized access to systems and attempted to sell stolen data on dark web marketplaces. The continued activity of ParanoidHax reflects the growing and persistent cyber threats originating from underground forums. These incidents highlight the urgent need for organizations to enhance their cybersecurity measures through continuous monitoring, advanced threat intelligence, and proactive defense strategies to safeguard sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
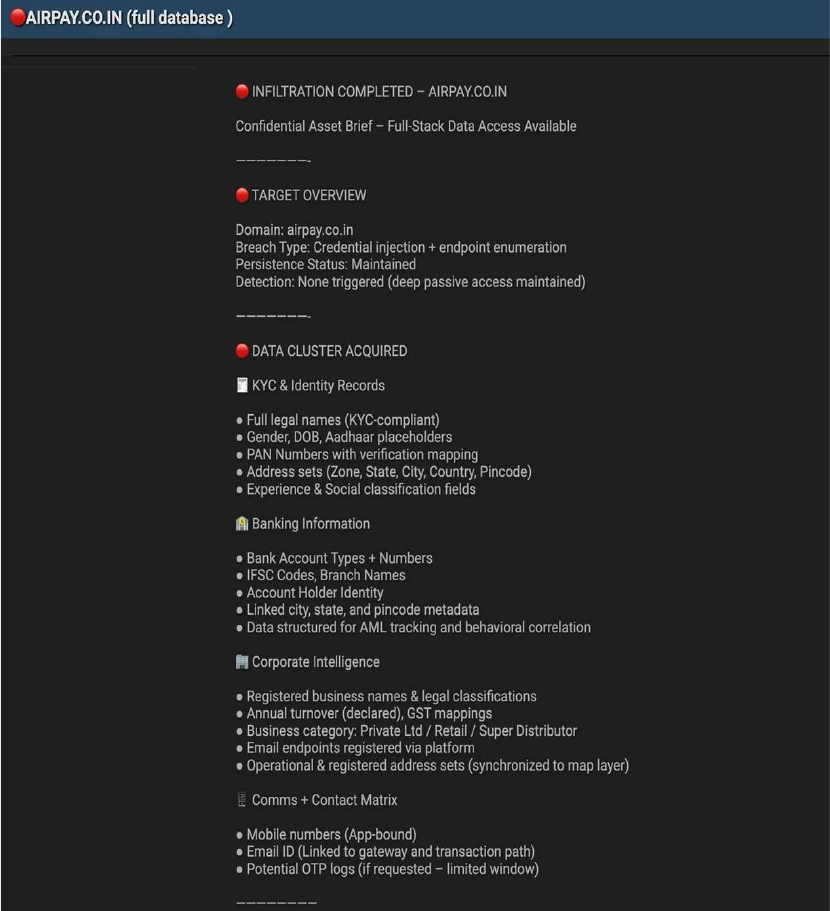
The CYFIRMA Research team observed that a threat actor has allegedly breached Airpay, a prominent Indian payment solutions provider, and is advertising the company’s full database for sale on a dark web forum. Airpay offers a comprehensive platform for businesses to manage online payments, making it a critical part of the digital commerce infrastructure in India. The cybercriminal claims to have gained deep, persistent access to the company’s systems through a credential injection attack, compromising a vast trove of sensitive financial and personal information.
The threat actor detailed the extent of the allegedly stolen data, which appears to be highly sensitive and valuable. The compromised information reportedly includes a wide range of personally identifiable information (PII) and financial records. The types of data listed for sale are:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
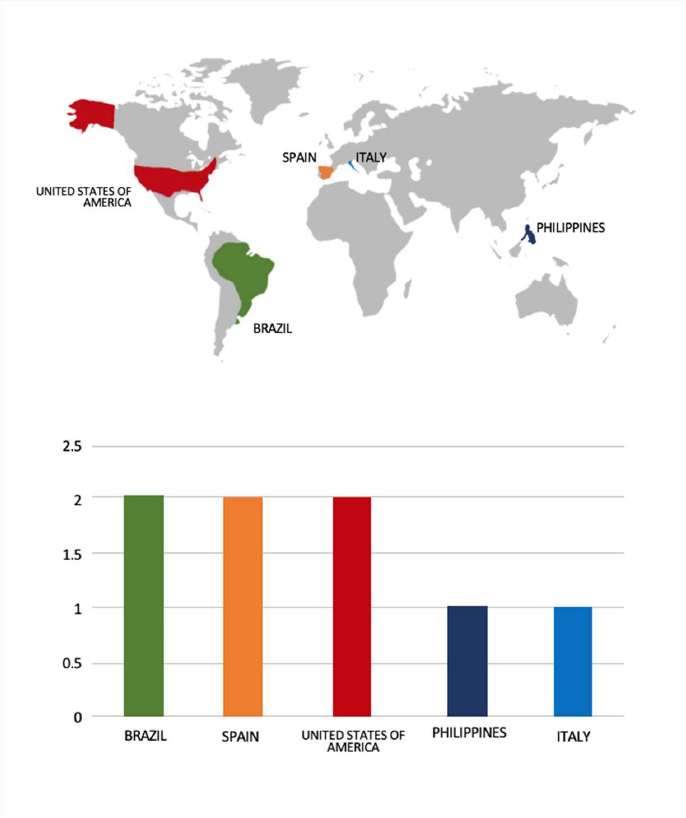
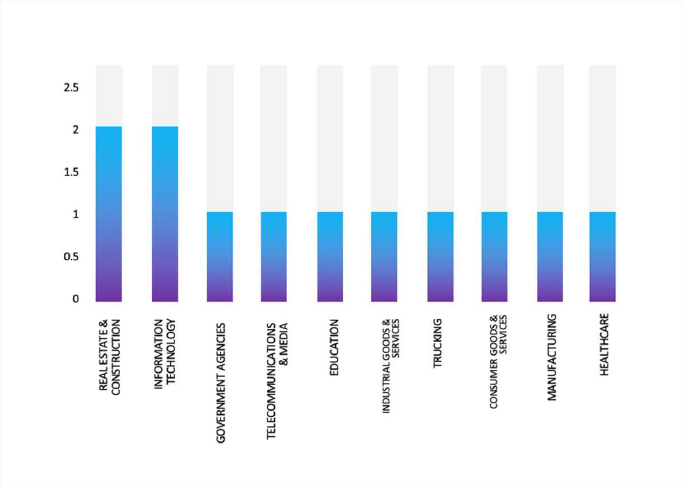
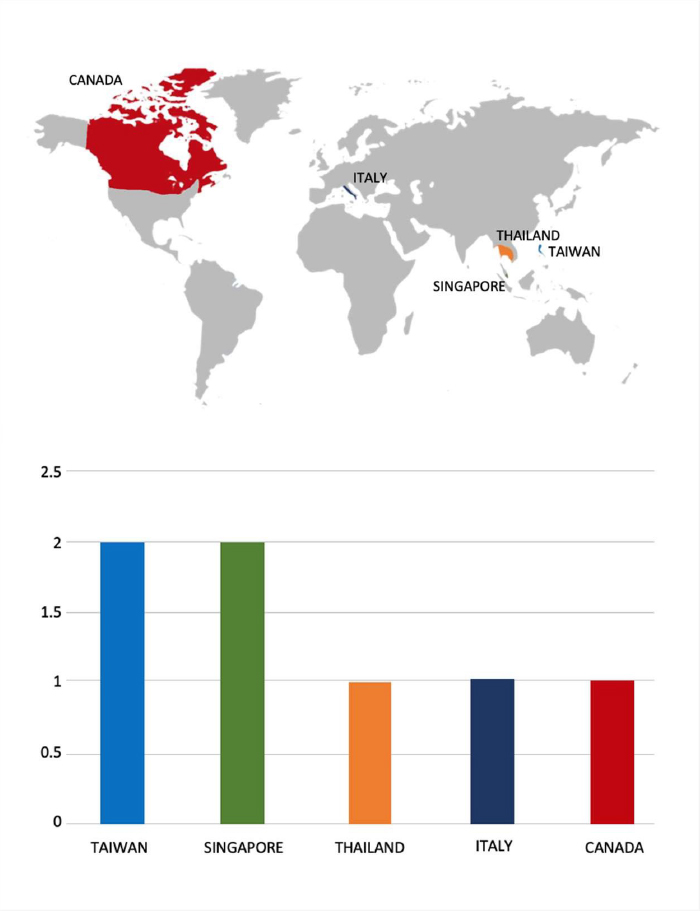
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.