


In July 2025, ransomware activity remained high, with major impacts on consumer services, professional services, and manufacturing. Qilin led in volume, while Incransom and Safepay saw sharp surges. New groups like Interlock introduced stealthy delivery via FileFix, Gunra expanded to Linux, and GLOBAL GROUP launched an AI-driven RaaS model. The U.S. remained the top target, followed by Canada and the UK. Sophisticated attacks on VMware ESXi (Scattered Spider) and the use of zero-days by Warlock signaled a merging of cybercrime with nation-state tactics. Emerging groups like Dire Wolf and D4RK4RMY shifted focus toward data leaks and politically charged narratives, moving away from conventional encryption-based attacks.
Welcome to the July 2025 Ransomware Threat Report. This report delivers a detailed analysis of the ransomware landscape, highlighting the emergence of new ransomware groups, evolving attack techniques, and notable shifts in targeted industries. By examining key trends, tactics, and significant incidents, this report aims to support organizations and security teams in understanding the current threat environment. As ransomware campaigns continue to grow in complexity, this report serves as a vital resource for anticipating future threats and strengthening proactive cybersecurity strategies.
Throughout July 2025, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
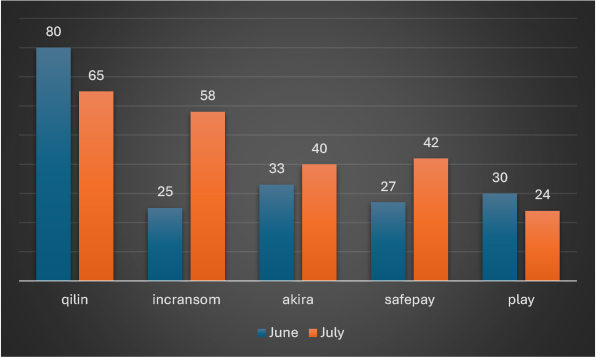
This trend comparison highlights dynamic shifts among the top five ransomware groups: Incransom recorded the most significant rise, with activity jumping 132%, signaling growing threat momentum. Safepay also surged by 55.6%, followed by Akira, which increased by 21.2%. In contrast, Qilin attacks declined by 18.8%, though it remained the most active group overall. Play experienced the steepest drop at 20%, indicating a possible strategic pause or disruption. These trends underscore the evolving nature of ransomware operations, with newer actors gaining ground and established groups showing volatility.
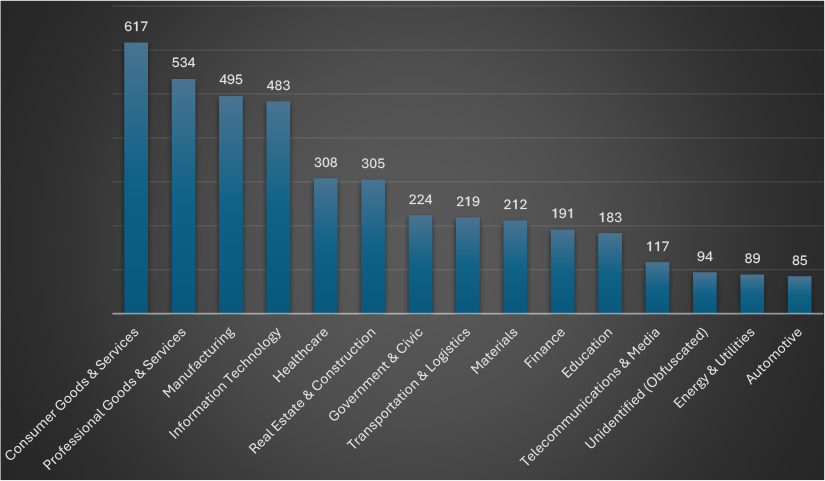
In July 2025, ransomware actors primarily targeted the Consumer Goods & Services sector, which recorded the highest number of victims (617), followed closely by Professional Goods & Services (534) and Manufacturing (495). Information Technology (483) and Healthcare (308) were also major targets, reflecting attackers continued focus on sectors rich in sensitive data and operational urgency. Real Estate & Construction (305) and Government & Civic (226 total, combining duplicates) suggest growing interest in infrastructure-related sectors. Victim counts in Transportation, Materials, and Finance indicate strategic targeting of critical supply chain and financial systems. Lower numbers in Energy, Automotive, and Telecom may reflect either stronger defenses or reduced focus. The presence of 94 obfuscated entities highlights ongoing challenges in attribution. Overall, ransomware campaigns appear tailored to exploit sectors with high operational pressure and ransom-paying potential.
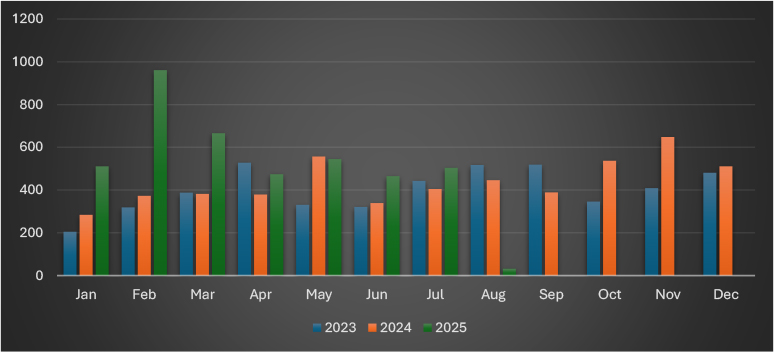
Ransomware victim numbers dropped from 545 in May to 504 in July 2025, marking a 7.5% decline over two months. While still elevated compared to early 2025, the slowdown suggests reduced activity from high-volume groups. Contributing factors may include affiliate realignments, reduced claims by groups like Incransom or Qilin, and shifting tactics away from public victim disclosure. Some actors, such as Devman or Safepay, may be regrouping following previous spikes or focusing on targeted attacks with longer dwell time. Despite the decline, volumes remain significantly higher than in 2023–2024, reflecting the sustained evolution of ransomware operations.
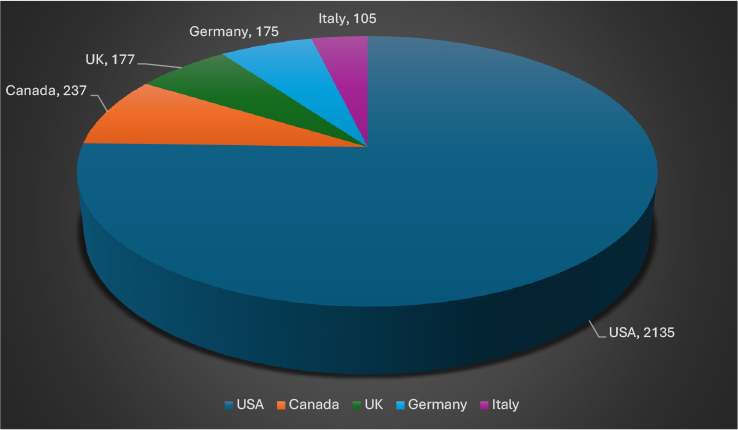
As of July 2025, the United States remained the most heavily targeted country by ransomware actors, with a staggering 2,135 victims – an order of magnitude higher than any other nation. Canada followed distantly with 237 incidents, while the United Kingdom (177), Germany (175), and Italy (105) also saw significant activity. These countries continue to be attractive targets due to their advanced digital infrastructure, high-value data, and economic capacity to pay ransoms. The sustained targeting of North America and Western Europe highlights threat actors’ strategic focus on regions with lucrative, disruption-sensitive sectors.
Interlock’s Tactical Leap: From ClickFix to FileFix in Modern Ransomware Delivery
The Interlock ransomware operation has swiftly evolved from leveraging traditional ClickFix techniques to adopting the more sophisticated FileFix method, a stealthy UI-driven attack chain. Initially deploying its RAT payload via PowerShell scripts embedded in fake CAPTCHA workflows, Interlock now exploits Windows File Explorer’s address bar to deliver commands masked as file paths. This shift, first observed in July 2025, marks the first confirmed use of FileFix in active campaigns and illustrates how Interlock has rapidly matured from script-based delivery to abusing native Windows UI elements for greater evasion, enabling deeper infiltration, persistence, and lateral movement within enterprise environments.
ETLM Assessment:
Interlock’s adoption of FileFix suggests a trajectory toward deeper integration of living-off-the-land techniques and UI-based deception. Future iterations may blend FileFix with zero-day exploits, Office macros, or QR code vectors to bypass defenses. We may also see expanded use of cloud delivery services (e.g., trycloudflare[.]com) and modular RAT components that enable exfiltration, ransomware encryption, and extortion from a single infection chain. With the growing popularity of FileFix, other threat actors may adopt and iterate on it, embedding it into ransomware-as-a-service platforms or phishing kits for wider-scale deployment.
GLOBAL GROUP RaaS Emerges as BlackLock Successor, Equips Affiliates with AI-Driven Extortion Tools
GLOBAL GROUP, a newly emerged ransomware-as-a-service (RaaS) platform active since June 2025, represents a calculated rebrand of BlackLock, itself an iteration of Mamona/Eldorado. Operated by the threat actor “$$$”, GLOBAL GROUP modernizes ransomware delivery through Go-based payloads, an AI-powered negotiation system, and mobile-friendly affiliate panels. Affiliates weaponize access obtained from IABs and brute-force tools targeting edge infrastructure (Cisco, Fortinet, Palo Alto) and Microsoft portals (Outlook, RDWeb). GLOBAL GROUP expands reach by offering ESXi/NAS/Windows support, domain-wide propagation, and a compelling 85% revenue share, enabling non-English-speaking actors to scale extortion across sectors from BPO to precision engineering.
ETLM Assessment:
GLOBAL GROUP exemplifies the future of RaaS: automated, multilingual, and mobile-optimized. Expect further enhancements like LLM-assisted phishing kit generation, real-time victim behavior tracking, and fraudulent compliance portals to simulate “regulatory” responses. As geopolitical instability rises, such platforms may target sensitive infrastructure or legal firms for geopolitical leverage or monetizable data. Integration with dark web escrow services, customizable double-extortion media kits, and intermittent encryption techniques may follow. The convergence of RaaS automation, AI tooling, and multilingual extortion removes technical barriers, democratizing ransomware operations for a global cybercriminal base.
Pushing Boundaries: Gunra’s Strategic Shift in Ransomware Operations
Gunra ransomware has demonstrated a swift and calculated evolution since its emergence in April 2025. Initially inspired by techniques from the defunct Conti group and focused solely on Windows systems, Gunra has now expanded its capabilities with the release of a Linux variant. This new variant features configurable, multithreaded encryption supporting up to 100 concurrent threads, surpassing the limits observed in other ransomware families. It also introduces partial file encryption and external keystore file management, providing attackers with enhanced control, speed, and stealth. This cross-platform pivot reflects a broader trend in ransomware development, signaling a strategic move toward targeting diverse enterprise infrastructures across operating systems.
ETLM Assessment:
Gunra is poised to evolve into a highly adaptable RaaS operation, potentially introducing monetization models for affiliates and expanding beyond encryption-based extortion. Future variants could incorporate data wipers, double or triple extortion tactics, stealthy pre-encryption reconnaissance modules, or even exploit AI-driven evasion techniques. As their Linux variant skips ransom notes entirely, they may experiment with silent extortion or leverage stolen data for strategic, long-term monetization, blurring lines between ransomware and advanced persistent threat (APT) behaviors.
Resurgence in Adversarial Sophistication Amid Operational Disruptions
The emergence of Chaos ransomware highlights the fluid evolution of the ransomware ecosystem, where threat actors seamlessly rebrand and reorganize under new banners following law enforcement crackdowns. With roots tracing back from Conti to Royal, then BlackSuit, and now Chaos, this lineage reveals a continuity in tactics, tooling, and operational tradecraft only repackaged with greater speed, scale, and stealth. The Chaos group’s emphasis on cross-platform compatibility, affiliate recruitment, and sophisticated automation showcases how modern ransomware operations are maturing into agile, business-like enterprises even amid mounting global pressure.
ETLM Assessment:
Ransomware groups like Chaos could begin using automation, artificial intelligence, and real-time data analytics to speed up their attacks and extortion processes. We might also see the growth of RaaS models offering full attack chains as subscription-based packages, potentially including DDoS capabilities, insider access tools, and even deepfake-powered social engineering kits. Some groups may experiment with posing as penetration testing firms or releasing fake security reports as part of their extortion efforts, adding a layer of psychological pressure while blurring ethical boundaries. If law enforcement crackdowns continue, these actors could shift toward decentralized, franchise-style operations that are harder to track, more anonymous, and better able to survive disruptions.
Warlock Ransomware: Blurring Lines Between Cybercrime and State-Backed Sabotage
Storm-2603, a suspected China-linked threat actor, is behind the recent Warlock ransomware campaign that signals a shift from traditional espionage to active cyber sabotage. Known for targeting enterprise infrastructure, the group exploited Microsoft SharePoint zero-day vulnerabilities to deploy ransomware payloads, demonstrating a move toward more destructive, overt operations. Using advanced techniques like credential dumping, lateral movement, and Group Policy abuse, Storm-2603 blends nation-state tradecraft with ransomware tactics, effectively blurring the lines between cybercrime and geopolitical interference. This campaign underscores a growing trend where state-enabled actors leverage ransomware not just for financial disruption but as a calculated tool of strategic coercion and destabilization.
ETLM Assessment:
The fusion of zero-day exploits with ransomware deployment in state-sponsored operations may become a dominant tactic in hybrid cyber conflict. Threat actors could increasingly target widely deployed enterprise software (like SharePoint, Exchange, or SAP) as vectors for mass-scale access and disruption. Moreover, these campaigns might leverage AI-assisted lateral movement, autonomous privilege escalation, and adaptive encryption schemes that respond dynamically to defenses. Expect future operations to further weaponize access to critical infrastructure, with ransomware serving as both a smokescreen and coercive tool to apply pressure without attribution, especially in regions with high geopolitical friction.
SafePay Ransomware: Precision Extortion Tactics Targeting Global Enterprises like Ingram Micro
The SafePay ransomware attack on Ingram Micro represents the ongoing industrialization of ransomware operations, where data theft and extortion have become strategically calibrated against high-value global enterprises. Operating quietly since 2024, SafePay has matured into a highly targeted, data-centric threat group, weaponizing both encryption and data leak threats with operational precision. Their playbook involving pre-encryption exfiltration, public shaming on dark web portals, and disruption of large-scale IT operations showcases a shift toward calculated, high-pressure extortion campaigns that aim to inflict reputational and logistical damage even as victims work rapidly to recover.
ETLM Assessment:
Ransomware groups like SafePay are likely to evolve further into specialized, intelligence-driven extortion syndicates. Expect future operations to incorporate detailed victim profiling, targeting not only IT infrastructure but also vendor ecosystems, third-party integrations, and partner supply chains. Sophisticated actors may weaponize stolen internal documentation to orchestrate secondary phishing campaigns or legal/regulatory leverage. Additionally, we may see a trend toward “hybrid extortion,” where ransomware is used in conjunction with deepfake communications, brand impersonation, or insider recruitment to compound pressure on targeted organizations.
From Human Trust to Hypervisor Control: A New Era in Ransomware Operations
Scattered Spider is a sophisticated threat group aggressively targeting virtualized environments, especially VMware ESXi hypervisors, by leveraging social engineering rather than software vulnerabilities. Attacks begin with impersonation calls to IT help desks, leading to Active Directory (AD) password resets and initial access. They scan for IT documentation, vSphere admins, and Privileged Access Management (PAM) tools, then escalate access by impersonating high-value users. Once they gain access to vCenter Server Appliance (vCSA), they enable SSH, reset ESXi root passwords, and perform disk-swap attacks to extract the NTDS.dit database. This grants control over virtual infrastructure, including backup systems, which are wiped. In the final stage, ransomware is deployed via SSH to encrypt all VM files. The full attack from access to encryption can occur within hours. The group exploits poor VMware security practices, bypassing traditional defenses. Recommended mitigations include locking down vSphere, phishing-resistant MFA, infrastructure segmentation, and centralized logging with immutable backups.
ETLM Assessment:
Building on their success with social engineering and control over virtual infrastructure, actors like Scattered Spider may evolve into full-spectrum extortion crews, combining virtualization layer attacks with data theft, deep access to privileged identity systems, and deliberate disruption of business continuity tools. Future campaigns could introduce staged attacks where virtual infrastructure is compromised first, followed by timed exploitation of disaster recovery processes, regulatory exposure (via stolen internal compliance reports), or extortion of third-party partners. They may also adopt AI-driven reconnaissance to map organizational trust structures faster, and even manipulate IT ticketing systems or internal communications to prolong undetected access.
Dire Wolf
Dire Wolf is an emerging ransomware group that began operations in May 2025 and gained momentum through June and July. It has claimed over 30 victims to date, targeting sectors such as healthcare, legal, manufacturing, real estate, and education. The group publicly leaks stolen data on its leak site, with July 2025 showing peak activity (12+ new victims). Rather than deploying traditional encryption-based ransomware, Dire Wolf appears to focus solely on data theft and extortion. Its global targeting, regular updates, and diverse victim profile indicate a rapidly evolving threat actor with a clear emphasis on reputational and financial coercion.
D4RK4RMY
D4RK4RMY – 共产主义勒索软件党 (Communist Ransomware Party) is a politically themed ransomware group that emerged in June 2025. It uses a double extortion model, combining file encryption with public data leaks on a propaganda-style leak site featuring ideological and anti-capitalist messaging. As of now, the group has claimed 10 victims, with 7 added in July 2025 alone, marking its most active month to date. Victims span education, IT, manufacturing, and government-related sectors. While still early in its lifecycle, D4RK4RMY’s fusion of cybercrime and political narrative positions it as a uniquely motivated threat actor worth close monitoring.

kawa4096
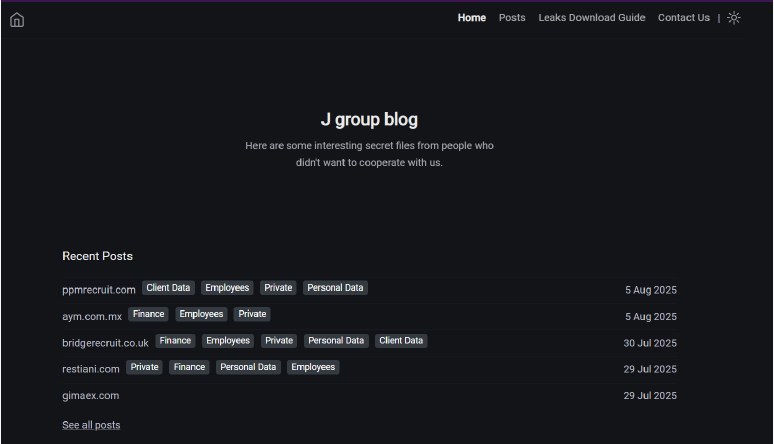
J Ransomware Group is a rising data extortion actor active since February 2025, with operations expanding steadily across multiple sectors and regions. The group saw its highest activity in July 2025, leaking data from 6 victims during that month alone – the most in any single month to date. Targets included companies in finance, recruitment, IT, and manufacturing, with data types ranging from client records to employee and personal information. The consistent July leaks suggest a scaling operation and increasing capability. With a growing victim list and international reach, J Group is positioning itself as a persistent threat actor.
Breaking Norms: Ransomware Targets Beyond Traditional Boundaries
The ransomware attack on WineLab highlights a shifting trend in the threat landscape where traditional geographic “safe zones” are increasingly disregarded. Historically, major ransomware groups avoided targeting Russian or CIS-based entities, but this incident, paired with growing exceptions like OldGremlin and NB65, signals a breakdown of these informal boundaries. The attack also reflects how ransomware has evolved into a tool for operational sabotage beyond data theft, targeting business continuity directly by disrupting logistics, retail operations, and consumer access in real time, even without immediate public attribution or group claims.
ETLM Assessment:
In the future, ransomware campaigns may grow more agnostic to geopolitical boundaries, especially as splinter groups, hacktivists, and opportunistic operators blur lines between the politically motivated attacks and financial gain. We can expect more disruptions aimed at high-availability retail and logistics networks, using techniques like systemic downtime, supply chain paralysis, and even ransomware deployment without data exfiltration, prioritizing reputational and operational damage over monetization. Additionally, as attackers target national-level consumer infrastructure, it opens the door to more strategic influence operations under the guise of financially driven cybercrime.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware remains a major threat to both organizations and individuals, locking critical data and demanding payment for its release. The consequences extend well beyond the ransom, often leading to costly recovery efforts, extended downtime, reputational harm, and potential regulatory fines. Such disruptions can destabilize operations and erode stakeholder trust. Addressing this growing risk demands a proactive cybersecurity posture and stronger collaboration between public and private sectors to build resilience against future attacks.
Victimology
Cybercriminals are increasingly targeting industries that manage vast amounts of sensitive data, ranging from personal and financial information to proprietary assets. Sectors such as manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology remain high on the threat radar due to their complex and extensive digital infrastructures. Adversaries strategically exploit vulnerabilities in economically advanced regions, launching well-planned attacks designed to encrypt critical systems and extract significant ransom payments. These operations are calculated to yield maximum financial returns.
The ransomware threat landscape in July 2025 revealed a shift toward modular, evasive, and high-impact operations. While overall victim numbers declined slightly, key groups like Qilin demonstrated technical maturity by exploiting zero-day vulnerabilities and introducing legal pressure tactics. Emerging groups such as Fog and Anubis showcased complex tool chains, indicating a strategic pivot to stealth and long-term compromise. Established actors also began leveraging legitimate tools and cloud platforms for persistence and data exfiltration. Organizations must enhance resilience, as ransomware now operates as a service ecosystem, rapidly adapting to security counter measures.