


A sophisticated phishing campaign, possibly attributed to Pakistan-linked APT36 (Transparent Tribe) is targeting Indian defense organizations and related government entities using spoofed domains. These typo-squatted domains mimic official government platforms to steal credentials, and infrastructure analysis reveals connections to Pakistani IPs and possible staging via Zah Computers. The campaign demonstrates advanced social engineering, real-time one-time password (OTP) harvesting and coordinated domain usage, potentially posing a significant threat to national security.
A malicious URL has been identified which, when accessed, redirects the user to a counterfeit webpage designed to closely mimic the official Indian government portal, replicating key visual elements such as the official logo, page layout, and title to create a convincing appearance of legitimacy and deceive users into believing they are interacting with a genuine government platform.
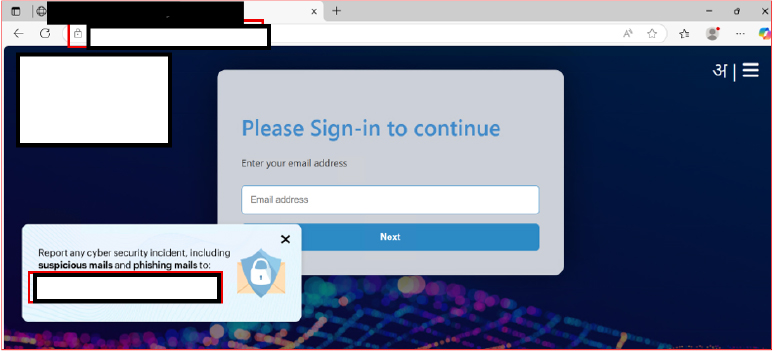
Upon entering a valid email ID in the initial phishing page and clicking the “Next” button, the victim is redirected to a second page that prompts the user to input their email account password and the Kavach authentication code.
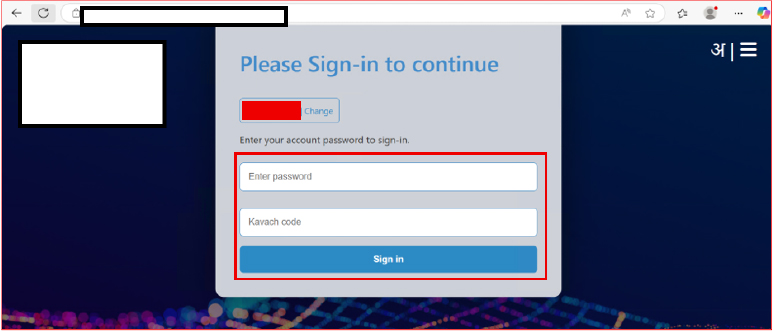
This phishing campaign employs advanced social engineering techniques by incorporating legitimate government cybersecurity reporting email addresses to enhance credibility and reduce suspicion. The attackers request both the victim’s password and a time-sensitive Kavach-generated OTP, aiming to bypass multi-factor authentication (MFA) and gain real-time access to official email accounts.
By referencing trusted authorities and secure communication flows, the threat actors create a false sense of legitimacy. The real-time harvesting of credentials and OTPs demonstrates a sophisticated effort to compromise MFA-protected accounts, and, if successful, could result in unauthorized access to sensitive systems, exposure of classified data, and broader threats to national security infrastructure.
Kavach is a MFA application developed by the National Informatics Centre (NIC) to enhance the security of government email services in India, generating time-based OTPs that function alongside the user’s password to authenticate official email accounts.
During the inspection of the phishing web page, it was observed that the domain is configured to establish an outbound connection to a remote server with the IP address 37.221.64[.]202 over port 443 (HTTPS), indicating active communication with an external command and control (C2) server. The phishing site is designed to capture sensitive user inputs—including email IDs, passwords, and Kavach OTPs—and transmit this information securely to the remote server, enabling the attacker to harvest credentials in real time while evading basic detection mechanisms using encrypted traffic.
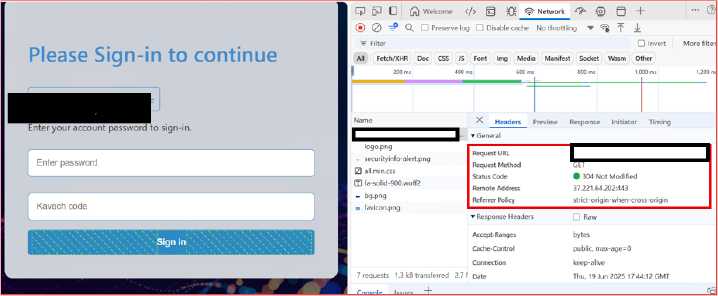
An investigation into the domain reveals, with high confidence, that it is being used for phishing and other malicious activities. The domain appears to have been specifically registered to target the government entities through spoofing and credential harvesting campaigns. It exhibits multiple indicators of impersonation and deceptive behavior, consistent with tactics commonly employed in targeted phishing operations.
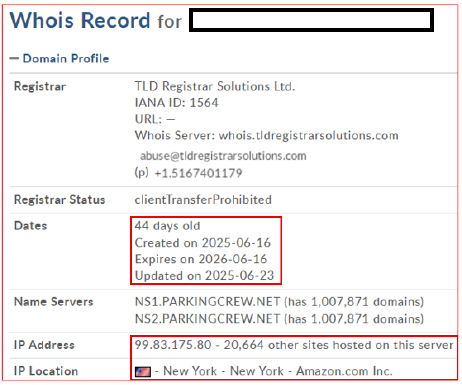
The domain was registered on June 16, 2025, with an expiration date set one year later, indicating recent creation and potential use for short-term malicious activity. It is resolved to the IP address 99[.]83[.]175[.]80, which is hosted by TLD Registrar Solutions Ltd.
This domain mimicry technique, often referred to as typo squatting, is commonly used by threat actors to exploit user trust by spoofing well-known brands, particularly foundations government and NGOs .
During technical analysis, the following IP address was associated to the domain:
| IP Address | ASN | ISP | Country | Notes |
| 99.83.175.80 | AS16509 | AMAZON-02 | US | Flagged as phishing |
The IP is hosted within Amazon’s cloud infrastructure (AS16509), a common choice for both legitimate and malicious services. However, in this case:
Further analysis revealed three subdomains associated with Indian Government entities.
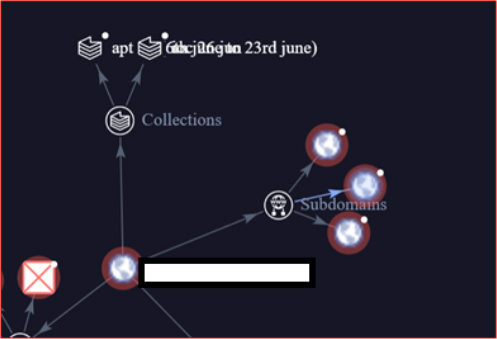
Subsequent analysis has identified additional phishing campaign URLs that follow a similar pattern, including domain names crafted to resemble official Indian government-related entities. These domains exhibit consistent characteristics in structure, naming conventions, and visual design, all intended to deceive users by mimicking legitimate government platforms.
Notably, these domains were registered within the same time frame, indicating a coordinated and premeditated effort by the threat actors. The uniformity across these domains, coupled with their use in similar credential harvesting schemes, suggests they are part of a broader, organized phishing campaign specifically targeting government infrastructure.
This coordinated approach reinforces the severity of the threat, highlighting the attackers’ strategic intent and potential access to resources enabling simultaneous domain registration and deployment.
| URL | Domain | Registration Detail |
| Virtualeoffice[.]cloud | Virtualeoffice[.]cloud | 19-05-2025 |
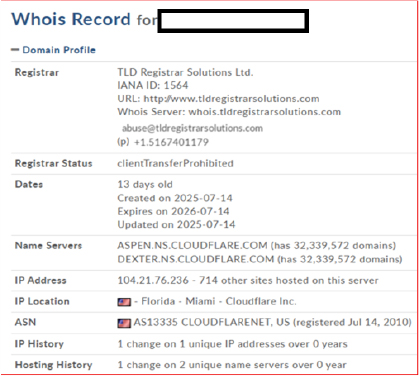
The primary domain was registered on July 14, 2025, with an expiration date of June 16, 2026, indicating recent creation and potential use for short-term malicious activity. It resolves to the IP addresses 172[.]67[.]202[.]22, 104[.]21[.]76[.]236, and 78[.]40[.]143[.]169 (Malicious) are hosted by TLD Registrar Solutions Ltd.
The subdomain resolves to the IP address 37[.]221[.]64[.]202, which has been flagged in multiple threat intelligence feeds for phishing-related activity. The associated hostnames and observed network behaviour indicate that this subdomain is likely part of a broader typosquatting campaign, designed to impersonate legitimate government services. Its infrastructure suggests possible use in phishing attacks, credential harvesting, or malware distribution, posing a significant risk to unsuspecting users who may be tricked by its deceptive structure.
An investigation into the domain revealed a notable connection to Pakistani infrastructure: an associated subdomain was observed hosting content from Zah Computers, a Pakistani IT services firm, which suggests either the use of shared or compromised infrastructure to host malicious content, or potential direct involvement by actors operating from Pakistan.
Furthermore, APT36 is a Pakistan-aligned threat group – known for deploying phishing infrastructure that impersonates Indian government entities – and the tactics observed here (including typosquatted domains and spoofed portals) are consistent with their known behavior.
The presence of Zah Computers’ web content within this malicious infrastructure raises two possibilities: either APT36 is leveraging Pakistani-hosted services for staging phishing assets, or Zah Computers has been compromised and used to lend legitimacy to malicious traffic. In both scenarios, the evidence strongly supports the attribution of this operation to APT36, reflecting their continued use of deceptive, infrastructure-based targeting of Indian government entities.
This phishing campaign is assessed with medium confidence to be the work of APT36 – also known as Mythic Leopard or Transparent Tribe – which is a Pakistan-linked advanced persistent threat group known for targeting Indian government entities and critical infrastructure through sophisticated credential harvesting and social engineering tactics. The use of typo-squatted domains combined with infrastructure hosted on Pakistan-based servers (and IP addresses previously flagged in threat intelligence feeds) is consistent with the group’s established tactics, techniques, and procedures. The deployment of spoofed government login portals to capture sensitive credentials further reinforces attribution to APT36.
Transparent Tribe / APT36 is believed to be a State-sponsored Pakistani threat actor specifically targeting military, embassies, and government entities. Active since 2016, the group carries out cyber-espionage operations with the goal of collecting sensitive information from foreign countries that serves its military and diplomatic interests. Their modus operandi relies on phishing and watering hole attacks to take a position on the victims, and the phishing email is either a malicious macro text or a vulnerability-based RTF file.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Reconnaissance | T1598 | Phishing for Information |
| Resource Development | T1583.001 | Acquiring infrastructure: Domains |
| Initial Access | T1566.001 | Phishing: Spear phishing attachment |
| Execution | T1204.001 | User execution: Malicious Link |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Persistence | T1547.001 | Boot or logon autoStart execution: Registry Run Keys / Startup Folder |
| Discovery | T1033 | System owner/User discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System information discovery |
| Discovery | T1083 | File and directory discovery |
| Collection | T1005 | Data from local system |
| Collection | T1113 | Screen capture |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
rule APT36_MultiIndicator_Threat
{
rule APT36_Phishing_Indicators
{
meta:
author = “Cyfirma Research”
description = “Detects IOCs related to APT36 phishing infrastructure”
threat_actor = “APT36 (Transparent Tribe)”
last_updated = “2025-07-30”
strings:
// IP addresses
$ip1 = “99.83.175.80”
$ip2 = “37.221.64.202”
$ip3 = “78.40.143.169”
// Domains and subdomains
$domain = “virtualeoffice.cloud”
condition:
any of ($ip*) or any of ($domain*)
}
The phishing campaign possibly linked to APT36 underscores the persistent threat posed by state-sponsored actors targeting Indian government entities. By leveraging social engineering and spoofed infrastructure, the attackers aim to bypass authentication and compromise sensitive systems. Mitigating such threats requires a coordinated approach strategic domain control, robust operational defenses, and strong cybersecurity governance to safeguard national assets and ensure the resilience of critical government infrastructure against advanced phishing attacks.
Strategic Recommendations
Operational Recommendations
Management Recommendations
| sl.no | Indicator of compromise | Recommendation |
| 1 | 99[.]83[.]175[.]80 | Block |
| 2 | 37[.]221.64[.]202 | Block |
| 3 | 78[.]40[.]143[.]169 | Block |
| 4 | Virtualeoffice[.]cloud | Block |