


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found GAGAKICK Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
GAGAKICK Ransomware.
Researchers have identified a newly emerged ransomware strain known as GAGAKICK. This malware operates by encrypting user data and appending a unique victim ID followed by the .GAGAKICK extension to each encrypted file. Upon completing the encryption process, the ransomware generates a ransom note named README.TXT.
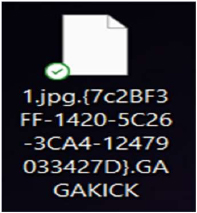
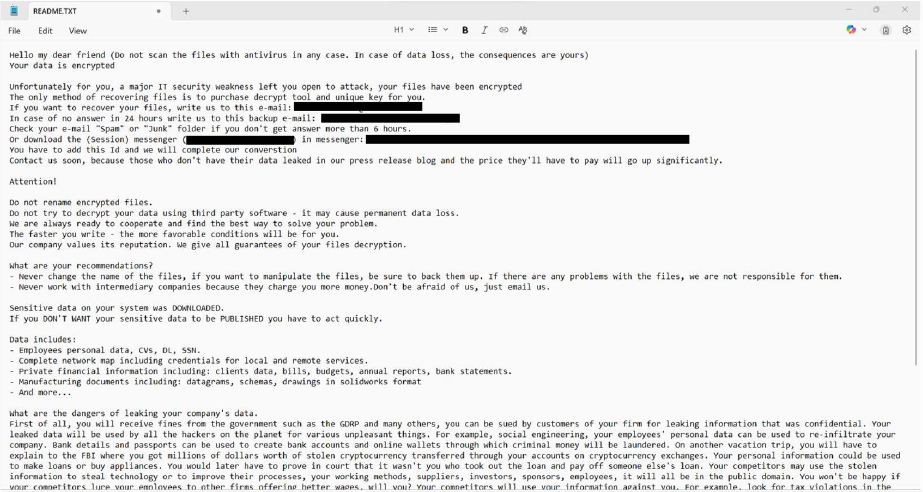
The ransom note informs the victim that their data has been encrypted due to security vulnerability. It says that the files can only be restored by buying a decryption tool along with a unique key. Victims are directed to contact the attackers via two provided email addresses or through a messaging platform using a specified ID. In addition to encryption, sensitive data has been exfiltrated including employee records, financial documents, network credentials, and proprietary manufacturing files. Victims are warned that failure to pay the ransom will result in the public release of this stolen information.
The attackers strongly discouraged renaming files, using antivirus software, or seeking assistance from third-party recovery services, claiming these actions could cause permanent data loss. They also advise against involving authorities, asserting that law enforcement cannot assist and may make the situation worse. The message concludes with warnings of legal, reputational, and financial consequences should the data be leaked, and emphasizes that payment is the quickest and least damaging resolution.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of GAGAKICK ransomware indicates that it is likely part of a well- planned and coordinated operation with a clear focus on financial gain through psychological manipulation. The messaging within the ransom note uses intimidation to influence victim behavior highlighting potential legal penalties, reputational damage, and operational disruption to amplify pressure. The attackers present themselves as professional and untraceable, discouraging external help and urging direct communication, which reflects a deliberate attempt to isolate the victim and control the negotiation process.
The structure and tone of the note suggest that the operators are following a model commonly seen in advanced ransomware campaigns, where threat actors combine technical disruption with social engineering to maximize impact. CYFIRMA assesses that GAGAKICK may be under active development or part of a broader campaign framework, potentially signaling ongoing activity or future variants. The calculated language and emphasis on consequences point toward an experienced group employing tactics designed to bypass traditional defense and recovery strategies.
Sigma rule:
title: Uncommon File Created In Office Startup Folder
description: Detects the creation of a file with an uncommon extension in an Office application startup folder
tags:
– attack.resource-development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_*
falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Loader| Objectives: Data Theft, Malware distribution| Target Technology: Windows OS | Target Industry: Government |Target Geography: United States
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “CastleLoader” is trending.
About Malware CastleLoader
CastleLoader is a newly surfaced malware loader that has quickly gained traction since early 2025. It serves as a delivery mechanism for a variety of information-stealing and remote-control malware, spreading primarily through deceptive phishing tactics that cleverly exploit the ClickFix method. These attacks often mimic legitimate platforms— such as software libraries, video conferencing tools, or document verification systems—to trick users into executing harmful commands on their devices. What sets CastleLoader apart is its stealth and effectiveness. Once users engage with the malicious content, the loader silently connects to its backend servers and delivers different types of malwares depending on the campaign. Despite limited engagement from users, a significant portion of those who interacted with the malicious links became infected, highlighting the effectiveness of the campaign. Over a short span of time, CastleLoader was linked to hundreds of infections, supported by a variety of distribution tactics and rotating command servers. The reach and flexibility of these operations indicate that CastleLoader is poised to remain a favored tool among threat actors for delivering multi-stage attacks.
Attack Method
CastleLoader relies heavily on deception to gain access to victims’ systems, using tactics that exploit trust in familiar platforms. One of its primary methods is through Cloudflare- themed ClickFix phishing, where users are tricked into copying and executing commands disguised as steps to fix supposed loading errors. These phishing pages are designed to resemble software platforms, browser alerts, and even document verification tools, making them appear legitimate. Once users follow the instructions, they unknowingly activate the malware, triggering a chain of downloads that lead to further infection. In many cases, the downloaded file arrives as a compressed package containing a script that silently runs in memory. This script unpacks and executes hidden code that reaches out to remote servers, fetches further payloads, and completes the compromise— highlighting the multi-layered nature of CastleLoader’s delivery chain.
Another strategy involves fake GitHub repositories posing as trusted development tools. These repositories host modified software that, when installed, connects back to CastleLoader’s infrastructure and downloads malicious content. This approach takes advantage of developers’ confidence in open-source platforms, making it more likely for the attack to succeed. In some cases, CastleLoader has been found delivering malware variants already seen in other campaigns, suggesting collaboration or shared objectives among different threat actors.
Across both distribution methods, the attackers use multi-stage download processes and draw on multiple sources, some of which are legitimate or compromised websites—making their activity harder to trace and shut down. These well-planned campaigns have led to widespread infections, including several high-profile incidents targeting government entities in the United States. The repeated use of overlapping malware and carefully crafted delivery paths points to a broader effort to carry out persistent, coordinated, and resilient attacks.
CastleLoader’s operations are backed by a purpose-built web control panel that gives threat actors full command over their malware campaigns. This management interface allows them to track infections, monitor visitor activity, and fine-tune their delivery methods in real-time. Every infected device is logged with detailed system information, helping attackers understand each victim’s environment and tailor further actions accordingly. From this panel, operators can control which malware gets delivered, how it’s executed, and even when to re-infect or remove a device from their system. Though the infrastructure shows characteristics similar to malware-as-a-service platforms, CastleLoader has not appeared for sale in underground markets, suggesting it may be operated privately by a dedicated group. Campaigns are executed through customizable tasks that define delivery paths, launch behavior, and country-specific targeting. Attackers can choose to restrict distribution to certain regions, including deceptive error messages, and use tools that help avoid detection or simulate legitimate software behavior.
The platform’s ability to log detailed visitor data—from device types to geographical locations—provides insights that guide future attacks. Combined with encrypted task containers and built-in tools for escalating system privileges, CastleLoader’s backend reinforces the strength of its overall delivery strategy. This infrastructure reflects a mature and evolving threat, carefully designed to maintain control, evade disruption, and adapt to different operational goals.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566 | Phishing |
| Initial Access | T1189 | Drive-by Compromise |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1204.004 | User Execution: Malicious Copy and Paste |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.010 | Command and Scripting Interpreter: AutoHotKey & AutoIT |
| Defense Evasion | T1036 | Masquerading |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
| Collection | T1005 | Data from Local System |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that CastleLoader’s adaptable infrastructure is poised to play a central role in the future evolution of cybercrime campaigns. As it supports the delivery of various malware strains based on attacker intent, it’s likely to enable a surge in more customized, persistent, and geographically targeted operations. This flexibility means attackers could shift tactics mid-campaign, pivoting data theft to remote control or surveillance without deploying new infrastructure. The growing use of deceptive delivery paths and multi-stage deployment tactics may allow CastleLoader to prolong infection cycles, delay detection, and maintain a presence across digital ecosystems for extended periods. What might seem like isolated breaches today could become the foundation for broader, coordinated threats across multiple sectors.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule CastleLoader_Indicators
{
meta:
description = “Detects CastleLoader Malware indicators” author = “CYFIRMA”
malware_family = ” CastleLoader”
strings:
// Domain
$domain_1 = “teamsi.org”
$domain_2 = “bytehub.asia”
// SHA256 Hashes
$sha256_1 = “bb42d5828af233ebec31e0b233b3614b1c189185805ecd5a4469629ca08337ed”
$sha256_2 = “f7061b2c4d8759f5d76a48b8f1512154e1fc4e4feeaa69274e63ebd0443d45e9”
$sha256_3 = “05ecf871c7382b0c74e5bac267bb5d12446f52368bb1bfe5d2a4200d0f43c1d8”
condition:
any of ($domain*) or any of ($sha256*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Emissary Panda: China-Linked Cyber Espionage Threat Actor
About the Threat Actor
Active since at least 2010 – 2013, this nation-state threat actor is believed to be a Chinese cyber espionage group with suspected ties to the People’s Liberation Army (PLA). The group primarily targets organizations to exfiltrate trade secrets, intellectual property, and other sensitive information that may offer strategic or competitive advantages to Chinese enterprises operating in similar sectors.
They are known for deploying the HttpBrowser backdoor, particularly to compromise Microsoft Exchange servers, thereby gaining full administrative control over the victim’s IT environment. Demonstrating a high level of sophistication, the group conducts precise reconnaissance to identify critical data repositories and selectively exfiltrates high-value information, often from multinational corporations across various industries.
Vulnerabilities Exploited
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2025-53770 | Microsoft SharePoint | 9.8 | Link |
| CVE-2025-49706 | Microsoft SharePoint | 6.5 | – |
| CVE-2025-49704 | Microsoft SharePoint | 8.8 | – |
| CVE-2025-53771 | Microsoft SharePoint | 6.5 | – |
| CVE-2022-26134 | Atlassian Confluence (Data Center, Server) | 9.8 | Link1, Link2, Link3, Link 4 |
| CVE-2021-26855 | Microsoft Exchange Server | 9.8 | Link 1, Link 2, Link 3, Link 4 |
| CVE-2017-0147 | Microsoft Windows (Multiple Versions) | 7.5 | Link 1, Link 2, Link 3 |
| CVE-2017-11882 | Microsoft Office (Multiple Versions) | 7.8 | Link |
| CVE-2017-0199 | Microsoft Office (Multiple Versions) | 7.8 | Link 1, Link 2, Link 3 |
| CVE-2019-0797 | Microsoft Windows | 7.8 | – |
| CVE-2018-8174 | Microsoft Windows (Multiple Versions) | 7.5 | Link |
| CVE-2019-0708 (BlueKeep Vulnerability) |
Microsoft Windows (Remote Desktop Protocol (RDP)) | 9.8 | Link 1, Link 2, Link 3, Link 4, Link 5 |
| CVE-2014-3153 | Linux Kernel | 7.8 | Link |
| CVE-2017-15303 | CPUID CPU-Z | 7.8 | – |
| CVE-2020-5902 | F5 BIG-IP | 9.8 | Link 1, Link 2, Link 3, Link 4, Link 5, Link 6 |
| CVE-2018-7600 | Drupal | 9.8 | Link 1, Link 2, Link 3 |
| CVE-2014-4114 | Microsoft Windows (Multiple Versions) | 7.8 | Link 1, Link 2, Link 3 |
| CVE-2017-0143 | Microsoft Windows (Multiple Versions) | 8.8 | Link 1, Link 2, Link 3 |
| CVE-2017-0144 | Microsoft Windows (Multiple Versions) | 8.8 | Link 1, Link 2, Link 3, Link 4 |
| CVE-2019-0604 | Microsoft SharePoint | 9.8 | – |
| CVE-2020-25213 | WordPress File Manager Plugin | 7.5 | Link 1, Link 2 |
| CVE-2021-3129 | Laravel Framework | 9.8 | Link 1, Link 2 |
| CVE-2020-14882 | Oracle WebLogic Server | 9.8 | Link 1, Link 2, Link 3 |
| CVE-2019-19781 | Citrix Application Delivery Controller (ADC) and Gatewa | 9.8 | Link 1, Link 2, Link 3, Link 4, Link 5 |
| CVE-2021-40539 | Zoho ManageEngine ADSelfService Plus | 9.8 | Link |
| CVE-2021-26858 | Microsoft Exchange Server | 7.8 | – |
| CVE-2021-27065 | Microsoft Exchange Server | 7.8 | Link 1, Link 2 |
| CVE-2021-26857 | Microsoft Exchange Server | 7.8 | – |
| CVE-2017-17215 | Huawei | 8.8 | – |
| CVE-2018-0802 | Microsoft Office (Multiple Versions) | 7.8 | Link 1, Link 2 |
| CVE-2023-4966 | Citrix NetScaler ADC and Gateway | 9.4 | Link |
| CVE-2018-8453 | Microsoft Windows (Multiple Versions) | 7.8 | Link |
| CVE-2021-1675 (PrintNightmare Vulnerability) | Windows Print Spooler | 7.8 | Link 1, Link 2, Link 3 |
| CVE-2020-0796 | Microsoft Server | 10.0 | Link 1, Link 2, Link 3, Link 4, Link 5, Link 6 |
| CVE-2015-1701 | Microsoft Windows (Multiple Versions) | 7.8 | Link 1, Link 2 |
| CVE-2014-4113 | Microsoft Windows (Multiple Versions) | 7.8 | Link 1, Link 2, Link 3 |
| CVE-2021-34527 (PrintNightmare Vulnerability) | Windows Print Spooler | 8.8 | Link |
| CVE-2019-2215 | Android, Linux Kernel | 7.8 | Link 1, Link 2, Link 3 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1608.004 | Stage Capabilities: Drive-by Target |
| Resource Development | T1608.002 | Stage Capabilities: Upload Tool |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1078 | Valid Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.002 | Scheduled Task/Job: At |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1047 | Windows Management Instrumentation |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1133 | External Remote Services |
| Persistence | T1112 | Modify Registry |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1562.002 | Impair Defenses: Disable Windows Event Logging |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.005 | Indicator Removal: Network Share Connection Removal |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded Files |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing |
| Defense Evasion | T1027.015 | Obfuscated Files or Information: Compression |
| Credential Access | T1555.005 | Credentials from Password Stores: Password Managers |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1003.002 | OS Credential Dumping: Security Account Manager |
| Credential Access | T1003.004 | OS Credential Dumping: LSA Secrets |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1012 | Query Registry |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1087.001 | Account Discovery: Local Account |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Lateral Movement | T1021.006 | Remote Services: Windows Remote Management |
| Collection | T1119 | Automated Collection |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
| Exfiltration | T1030 | Data Transfer Size Limits |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
Latest Developments Observed
The threat actor is suspected of targeting SharePoint servers leveraging recently disclosed vulnerabilities. By using the recent vulnerabilities as initial access, the threat actors are looking to infiltrate into the organizations network and gain access. The motive appears to be stealing intellectual property of government entities, defense, human rights groups.
ETLM Insights
The group is assessed to operate in alignment with the strategic objectives of the Chinese government and is known for conducting cyber-espionage campaigns targeting both public and private sector entities on a global scale.
There is evidence of infrastructure overlap with other Chinese state-linked threat actors, such as APT41, indicating possible coordination or shared operational resources. Indicators of zero-day exploit usage prior to public patch releases, coupled with coordinated activity among multiple Chinese APT groups, underscore the group’s advanced technical capabilities and strategic collaboration.
Their operations appear to be closely aligned with China’s broader economic and strategic initiatives, including the “Made in China 2025” plan and the “100-Year Strategy Vision”. These campaigns are characterized by a focus on intellectual property theft, corporate espionage, and the compromise of critical infrastructure to support long-term national interests. Looking ahead, the threat actor is expected to expand its focus on supply chain compromises, increasingly blend cyber espionage with financially motivated operations, and intensify targeting of operational technology (OT) environments, posing heightened risks to critical infrastructure and industrial systems.
YARA Rules
rule APT27_EmissaryPanda_SharePoint_Exploit
{
meta:
description = “Detects Emissary Panda activity targeting Microsoft SharePoint” author = “CYFIRMA”
date = “2025-07-29”
malware_family = “Emissary Panda / APT27” target_application = “Microsoft SharePoint” threat_level = 9
strings:
$s1 = “powershell.exe -ExecutionPolicy Bypass -NoProfile -WindowStyle Hidden” wide
$s2 = “Invoke-WebRequest” wide
$s3 = “System.Management.Automation” ascii
$s4 = “Invoke-Expression” wide
$s5 = “C:\\Program Files\\Common Files\\Microsoft Shared\\Web Server Extensions\\15\\ISAPI” ascii
$s6 = “SharePoint.dll” ascii
$c2_1 = “http://updatepanel[.]xyz” nocase
$c2_2 = “https://cdn-client[.]org” nocase condition:
(any of ($s1, $s2, $s3, $s4) and any of ($s5, $s6)) or (2 of ($c2_*) and 2 of ($s*))
}
Strategic
Management
Tactical
Russian National Airline Cancels Dozens of Flights After Hacktivist Attack
Russia has launched a criminal investigation into a cyberattack that targeted the information systems of Aeroflot, the country’s flagship airline. According to the Prosecutor General’s Office, the breach led to unauthorized access to the company’s internal networks, severely disrupting operations. Aeroflot reported that at least 50 flights to and from Moscow’s Sheremetyevo Airport were cancelled, with many others delayed, citing a failure in its IT infrastructure.
The pro-Ukrainian hacker collective Silent Crow, in coordination with the Belarusian group Cyber-Partisans, has claimed responsibility for the recent cyberattack on Aeroflot. Both groups have a track record of targeting critical infrastructure in Russia and Belarus through digital sabotage.
In a statement posted on Telegram, the hackers asserted they had fully compromised and destroyed Aeroflot’s IT systems. They claimed to have exfiltrated a wide range of sensitive data, including the airline’s entire flight history database, audio recordings of internal communications, and surveillance material, such as records from systems monitoring staff activity. Silent Crow also revealed that it had maintained long-term access to Aeroflot’s corporate network for over a year slowly expanding its control before executing the large-scale disruption.
Though Silent Crow remains a relatively obscure actor in the cyber realm, it has previously been linked to several high-profile incidents inside Russia. These include a breach of Rosreestr, the federal agency responsible for land and property registries, and a cyberattack on a contractor for the telecom giant Rostelecom.
ETLM Assessment:
In recent months, Russian air travel has been repeatedly disrupted due to escalating drone threats from Ukraine. Earlier this month, nearly 500 flights were cancelled and close to 2,000 were delayed as Ukrainian drone activity over Moscow and St. Petersburg intensified. Similar disruptions occurred on May 7–8, coinciding with high-profile visits from global leaders, including China’s President Xi Jinping, for World War II anniversary events.
Ukraine’s strategy increasingly appears aimed at making the war felt on the Russian home front. By targeting critical infrastructure like airlines and airports, Ukraine is not only creating logistical headaches but also increasing daily inconveniences for ordinary Russian citizens. These attacks serve a psychological and political purpose—reminding Russians that the war, which the Kremlin has sought to keep distant from daily life, now affects their own travel, mobility, and sense of normalcy.
Lynx Ransomware Impacts NIPPN Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, NIPPN Corporation (https[:]//www[.]nippn[.]co[.]jp/), was compromised by Lynx Ransomware. NIPPN Corporation is a diversified food manufacturer with its core business rooted in flour milling. Over the years, the company has broadened its scope across various food sectors, including food ingredients, processed foods, frozen products, and ready-to-eat meals. Its extensive product lineup includes premixes, pasta, grocery items, frozen dough, boxed lunches, and delicatessen foods. The compromised data includes financial documents, purchase, and sale deed bills, along with other confidential and sensitive information pertaining to the organization.
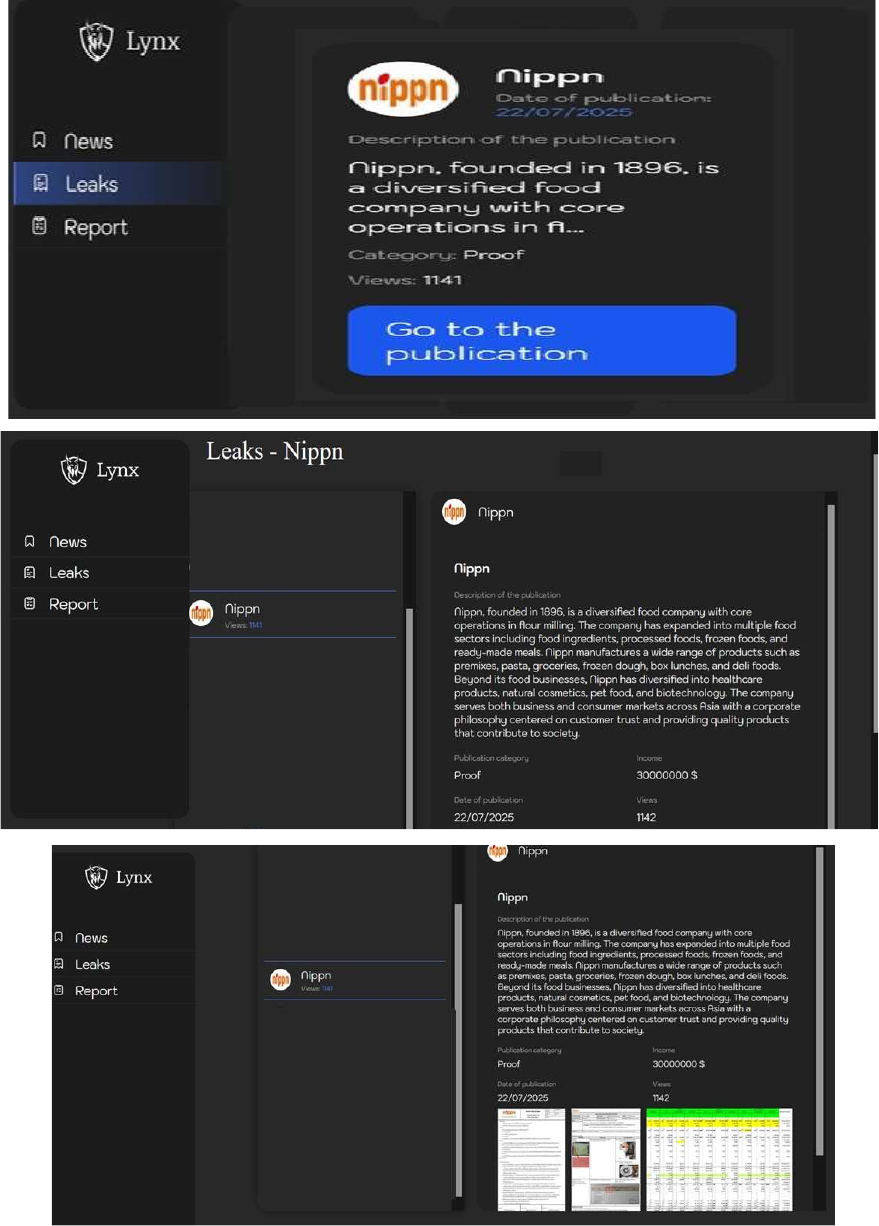
Relevancy & Insights:
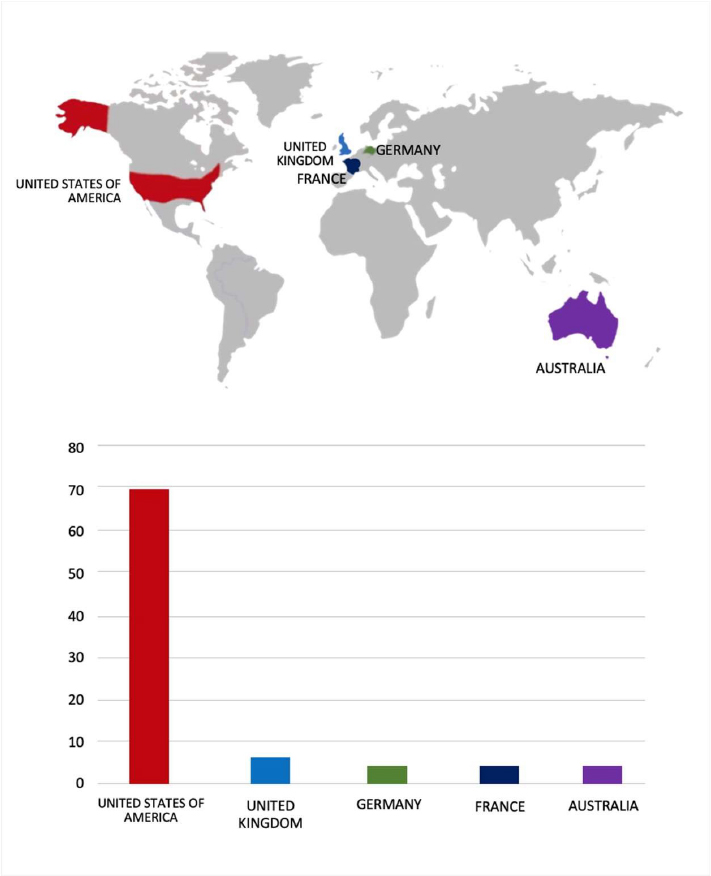
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
Qilin Ransomware Impacts the Adiantes
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, Adiantes (https[:]//adiantes[.]com/) was compromised by Qilin Ransomware. Adiantes is a Thailand-based manufacturer renowned for its premium sustainable leather goods, including handcrafted handbags, belts, and accessories. The company emphasizes bespoke design, combining traditional craftsmanship with contemporary style, while upholding ethical and eco-friendly production standards. Adiantes serves a diverse clientele across Thailand, Japan, and Germany. The compromised data includes financial records, human resources (HR) information, personally identifiable information (PII), and other confidential and sensitive organizational data. The total volume of the exposed data is estimated to be approximately 111 GB.
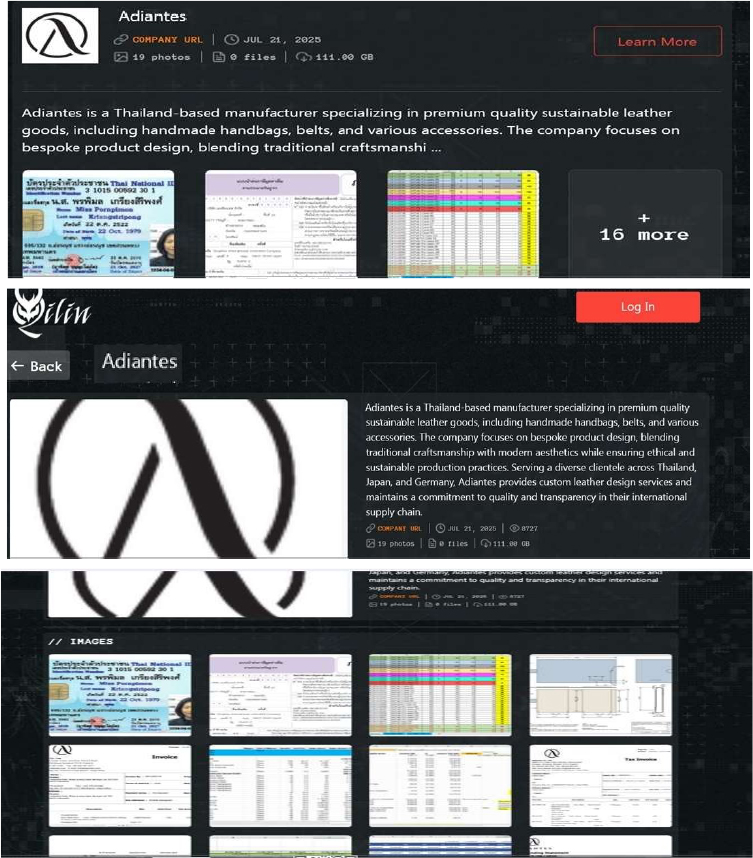
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in Drupal
Relevancy & Insights:
The vulnerability exists due to the affected module does not properly validate input when handling file access requests.
Impact:
A remote attacker can bypass protections and access private files.
Affected Products:
https[:]//www[.]drupal[.]org/sa-contrib-2025-089
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
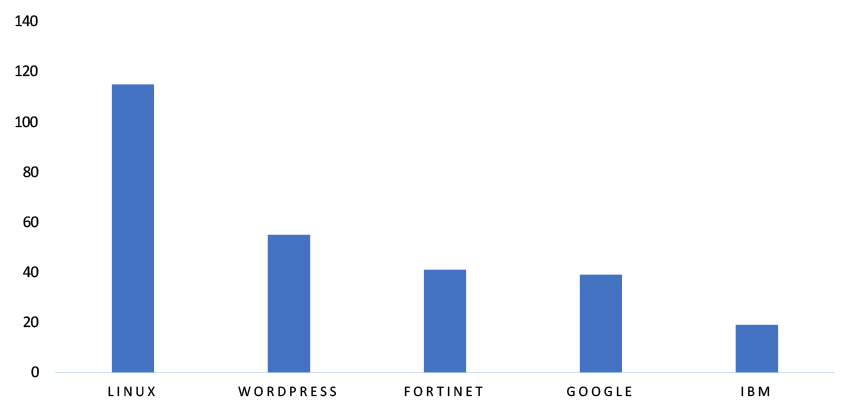
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Drupal can pose significant threats to user privacy and security. This can impact various industries globally, including government, education, healthcare, finance, and media. Ensuring the security of Drupal is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding content management, user authentication, and modular web application development across different geographic regions and sectors.
Dire Wolf Ransomware attacked and published the data of Akribis Systems
Summary:
Recently, we observed that Dire Wolf Ransomware attacked and published the data of the Akribis Systems (https[:]//akribis-sys[.]com) on its dark web website. Akribis Systems is a Singapore-based company that specializes in the design and manufacture of direct drive motors—including linear, rotary, and voice coil motors—as well as high-precision positioning systems and stages for advanced automation and motion control applications. The ransomware attack has led to a major data breach, exposing approximately 650 GB of sensitive information. The compromised data includes legal documents, financial records, customer information, design drawings, business contracts, bank transactions and statements, accounting records, employment contracts, confidentiality agreements, audit files, and various other confidential materials.
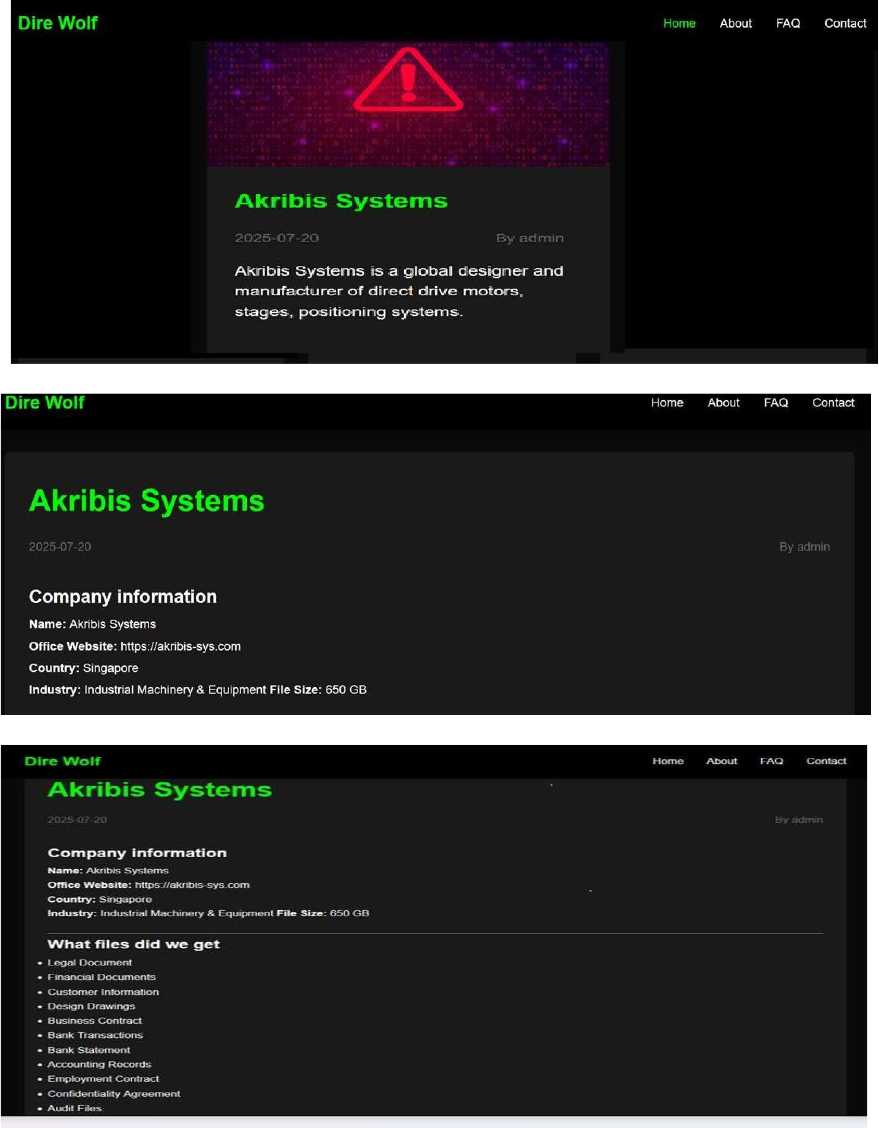
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
PT Bank Perkreditan Rakyat (BPR) Data Advertised on a Leak Site
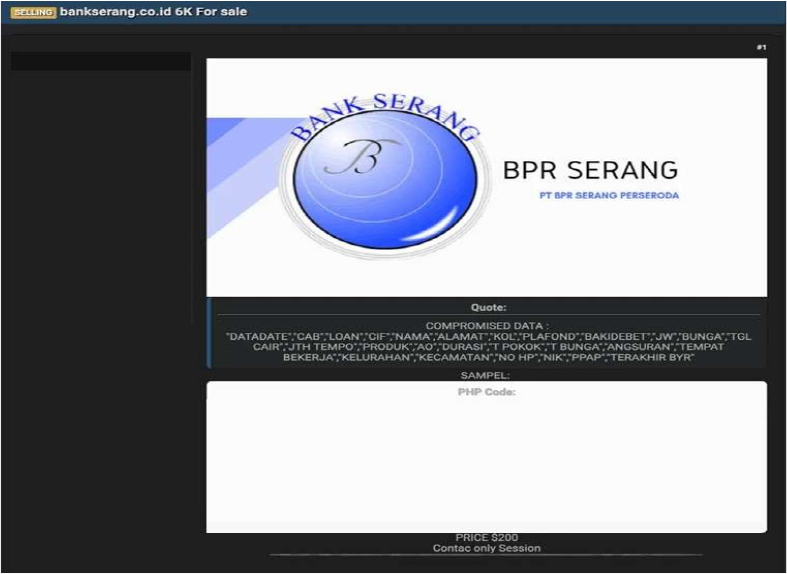
Summary: The CYFIRMA Research team observed a data leak related to PT Bank Perkreditan Rakyat (BPR)(www[.]bankserang[.]co[.]id) in an underground forum. PT Bank Perkreditan Rakyat (BPR) Serang, a regional development bank based in Serang, Indonesia. A threat actor “N1KA” has posted a database containing sensitive customer and loan information for sale on a dark web forum. The bank, which operates as a Regional Owned Enterprise (BUMD), plays a crucial role in the local economy by providing financial services, primarily to civil servants and private sector employees in the Banten province.
The breach exposes highly sensitive financial and personal data of the bank’s customers. The actor behind the sale released a sample of the data to prove the authenticity of their claims. The compromised information appears to be recent, with data entries dated as recently as mid-July 2025. This incident raises serious concerns about the security of financial data held by regional institutions and the potential for financial fraud and identity theft targeting the affected individuals.
The leaked database allegedly contains a wide array of personally identifiable information (PII) and financial details. The data fields listed for sale include:
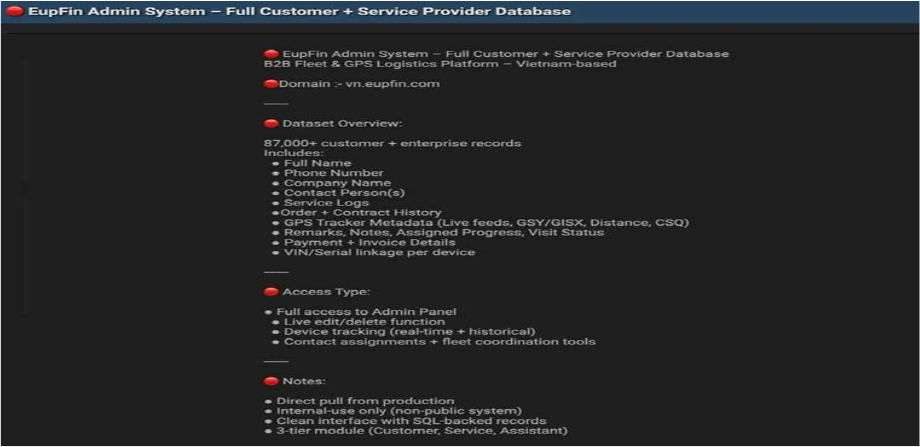
EupFin Data and Access Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that A threat actor has allegedly put the full administrative system and customer database of EupFin, a B2B fleet and GPS logistics platform based in Vietnam, up for sale on a dark web forum. EupFin is a key player in the country’s logistics industry, providing fleet management and GPS tracking solutions to a wide range of enterprise clients. The alleged breach is particularly severe as the seller is not just offering a static database but full, live access to the company’s internal administration panel.
The threat actor claims the dataset contains over 87,000 customers and enterprise records, which were allegedly pulled directly from the company’s production environment. The access being sold would reportedly grant a malicious actor complete control, including the ability to edit or delete records, track vehicles in real-time, and manage fleet coordination. The sensitive information allegedly for sale includes:
This incident poses a significant threat not only to EupFin’s operations but also to the security and privacy of its numerous clients. The exposure of such detailed logistical and financial information could lead to targeted fraud, corporate espionage, and major disruptions to supply chain operations.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “N1KA” has recently gained attention as a highly active group specializing in data leaks. Reliable sources have connected the group to multiple security breaches involving unauthorized system access and the attempted sale of exfiltrated data on dark web marketplaces. N1KA’s ongoing operations highlight the evolving and persistent nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to strengthen their cybersecurity posture through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and infrastructure.
Recommendations: Enhance the cybersecurity posture by:
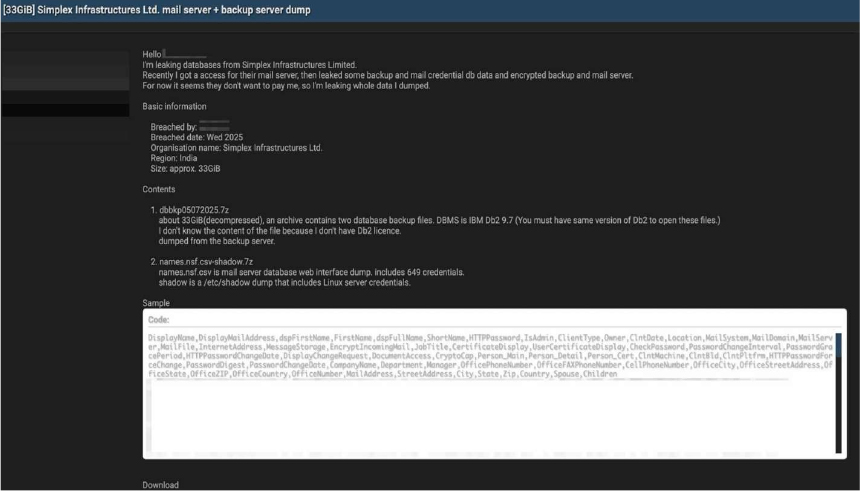
The CYFIRMA Research team observed that a threat actor has claimed responsibility for a significant data breach targeting Simplex Infrastructures Ltd., posting on a dark web forum that approximately 33GB of sensitive data was exfiltrated from the company’s systems. Simplex Infrastructures Ltd., a leading Indian engineering and construction firm, is widely recognized for its large-scale projects in the transportation, energy, and real estate sectors both in India and internationally. According to the threat actor, the compromised data was obtained from the company’s mail and backup servers, with the breach allegedly taking place on Wednesday, July 23, 2025.
The leaked data dump appears to contain highly sensitive corporate and employee information. A sample shared by the threat actor suggests a significant exposure of personally identifiable information (PII). The contents of the leak allegedly include:
This breach could pose a severe risk to the company’s operational security, exposing internal communications, employee data, and potentially confidential project details.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
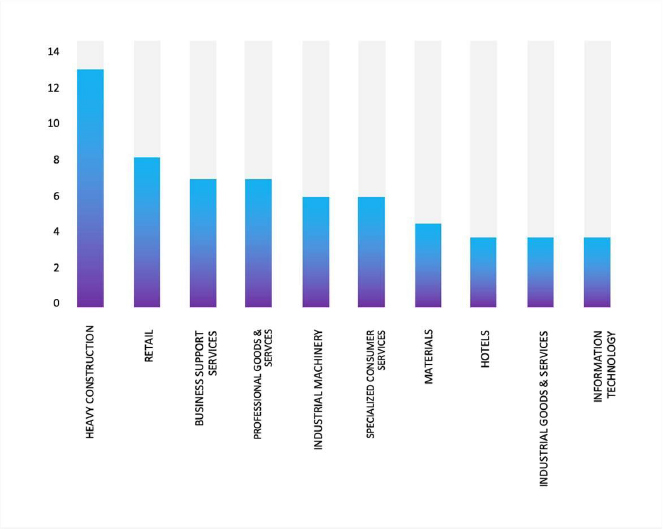
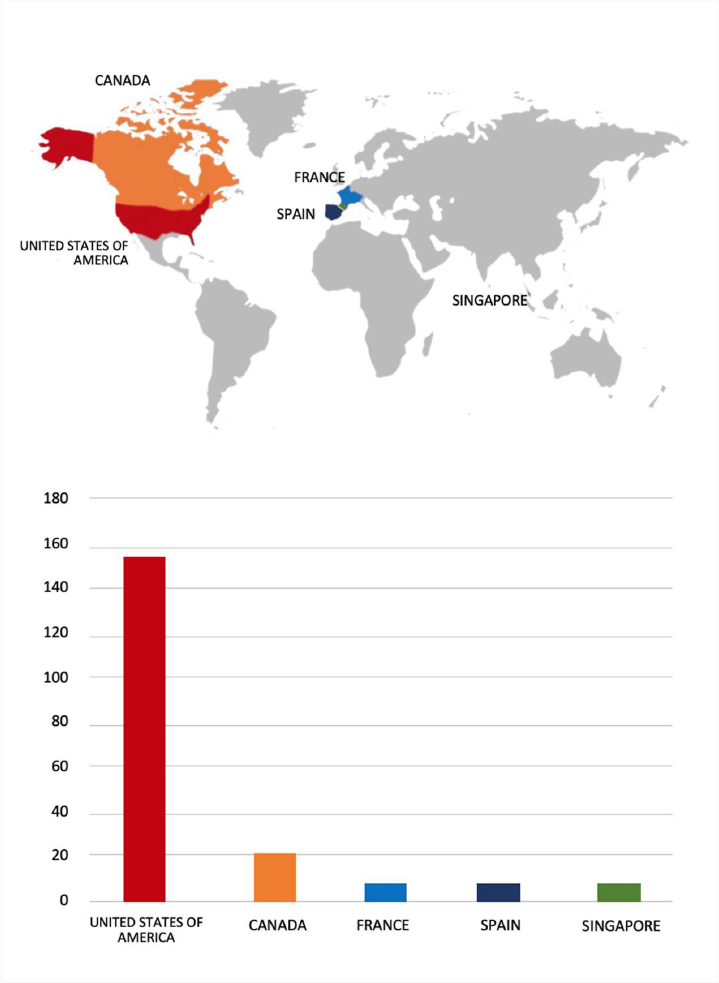
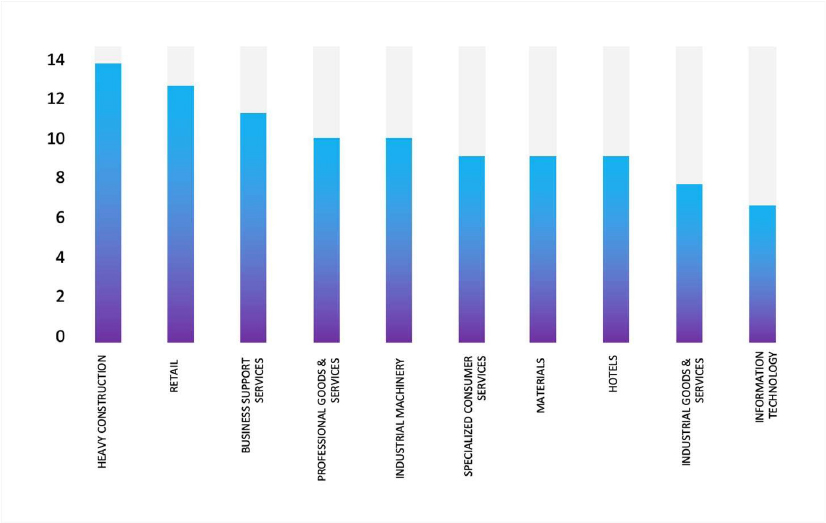
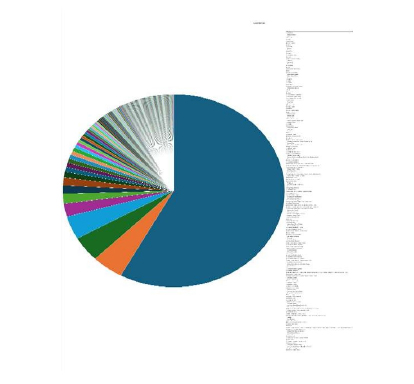
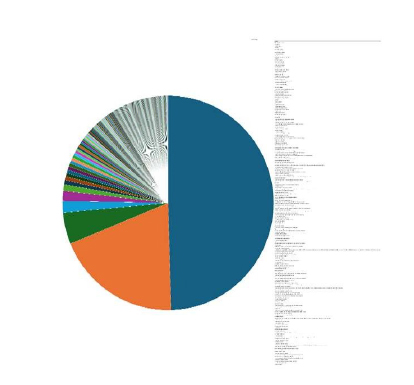
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.