


In June 2025, ransomware attacks targeted critical industries such as professional services, healthcare, and information technology, exploiting their dependence on sensitive data and minimal tolerance for downtime. A total of 463 victims were recorded globally, down 15% from May. Qilin emerged as the most active group, exploiting unpatched Fortinet vulnerabilities. New actors like Fog and Anubis introduced stealthier and more destructive methods, including modular toolkits and file-wiping capabilities. The U.S. remained the top target, followed by Canada and the UK. These developments highlight the growing sophistication, diversification, and psychological tactics used by ransomware actors to maximize pressure and profits.
Welcome to the June 2025 Ransomware Threat Report. This report delivers a detailed analysis of the ransomware landscape, highlighting the emergence of new ransomware groups, evolving attack techniques, and notable shifts in targeted industries. By examining key trends, tactics, and significant incidents, this report aims to support organizations and security teams in understanding the current threat environment. As ransomware campaigns continue to grow in complexity, this report serves as a vital resource for anticipating future threats and strengthening proactive cybersecurity strategies.
Throughout June 2025, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:

The trend comparison for June 2025 shows notable shifts among the top five ransomware groups. Qilin attacks surged by 47.3%, making it the most active group, whereas Akira rose moderately by 9.7%. In contrast, Play’s activity dropped by 31.8%, while Safepay saw the steepest decline at 62.5%, suggesting a major pullback. Dragonforce emerged rapidly, with attacks spiking by 212.5%. These trends reflect a shifting ransomware landscape, with emerging players gaining traction and others potentially retooling or retreating.
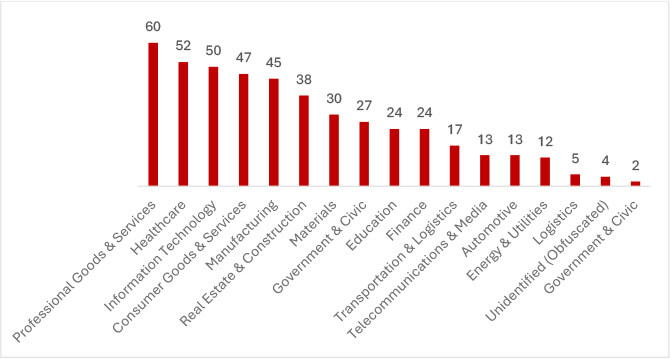
In June 2025, ransomware actors predominantly targeted the Professional Goods & Services sector (60 victims), followed by Healthcare (52), and Information Technology (50). These industries often handle sensitive data and critical operations, making them lucrative and time-sensitive extortion targets. Consumer Goods, Manufacturing, and Real Estate also saw high impact, likely due to their complex supply chains and limited cyber resilience. Government, Education, and Finance were repeatedly attacked for access to public data, personal records, or financial gains. The focus on IT and logistics points to attempts at broader disruption. Overall, attackers strategically chose sectors where downtime or data loss could force quick ransom payments.

Ransomware victims fell from 545 in May to 463 in June 2025 – a 15% drop. Key drivers include SilentRansomGroup, which did not claim any victims following the launch of its leak site, and Devman’s sharp decline, possibly due to ransom gains or affiliate shifts, as well as a notable decrease in Safepay activity.
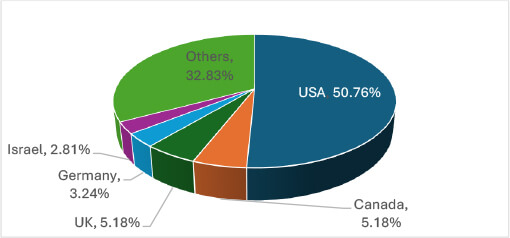
In June 2025, the United States remained the primary target of ransomware attacks, recording 235 victims, far surpassing other nations. Canada (24), the United Kingdom (24), Germany (15), and Israel (13) also experienced notable activity. These regions are attractive targets due to their advanced economies, data-rich organizations, critical infrastructure, and greater likelihood of ransom payment, making them highly lucrative for threat actors.
Critical Fortinet flaws now exploited in Qilin ransomware attacks
The Qilin ransomware group has launched a new wave of attacks exploiting Fortinet vulnerabilities, specifically CVE-2024-21762 and CVE-2024-55591. These flaws enable authentication bypass and remote code execution on unpatched FortiGate and FortiProxy devices. Initial access in recent intrusions—observed between May and June 2025—was obtained through these vulnerabilities, allowing the deployment of Qilin ransomware in a partially automated fashion. While the campaign currently focuses on Spanish-speaking regions, targeting remains opportunistic rather than confined to geography or sector. CVE-2024-21762, patched in February 2025, remains a major concern with tens of thousands of exposed systems. The same vulnerability has been leveraged by other ransomware groups, including those deploying the SuperBlack strain. Qilin, a Ransomware-as-a-Service operation with over 310 victims since its emergence, continues to evolve its attack surface by incorporating zero-day exploits and leveraging widely used perimeter devices for initial compromise.
ETLM Assessment:
Given Qilin’s opportunistic targeting and adoption of critical zero-day exploits, the campaign is likely to expand beyond Spanish-speaking regions. Its reliance on Fortinet vulnerabilities suggests future intrusions will target under-patched enterprise environments globally. The group may increasingly automate exploitation chains, broadening the attack scale.
Fog Ransomware Leverages Uncommon Tools to Evade Detection and Exfiltrate
The Fog ransomware group has adopted a distinct and stealthy attack strategy using a mix of legitimate and open-source tools. Initially observed exploiting compromised VPN credentials and executing pass-the-hash attacks, the group disables defenses and encrypts files across systems, including virtual machines. Recent campaigns target Veeam and SonicWall vulnerabilities and introduce a unique arsenal, including Syteca—a legitimate employee monitoring tool used for screen and keystroke logging. Delivered via Stowaway, a covert proxy tool, Syteca collects sensitive credentials without detection. Lateral movement is achieved through SMBExec from the Impacket framework, while GC2, a rare post-exploitation tool, enables command-and-control through Google Sheets or SharePoint. Additional utilities include Adapt2x for C2, Process Watchdog, PsExec, and Impacket SMB. For data exfiltration, 7-Zip, MegaSync, and FreeFileSync are employed. This eclectic mix enhances stealth, bypasses traditional defenses, and broadens Fog’s capabilities, marking a significant evolution in ransomware operations.
ETLM Assessment
Fog ransomware’s tool diversity signals a shift toward modular, low-signature attack chains. Future campaigns may increasingly favor legitimate and open-source utilities to evade EDR systems. As adoption spreads, other ransomware actors could replicate this model, complicating attribution and detection. Expect rising abuse of legitimate enterprise software for initial access, surveillance, and silent credential harvesting prior to payload deployment.
Anubis Ransomware Adds File Wiper to Escalate Destruction
Anubis, a relatively new ransomware-as-a-service (RaaS) operation active since December 2024, has introduced a destructive file-wiping feature to its malware arsenal. Distributed via phishing campaigns, the ransomware leverages ECIES encryption, appends a “.anubis” extension to encrypted files, and drops an HTML ransom note. The wiper module, triggered with the /WIPEMODE parameter, erases file contents while retaining filenames and structure, rendering data recovery impossible, even if ransom is paid. This tactic intensifies pressure on victims to meet demands quickly. The malware also removes Volume Shadow Copies, terminates interference-prone processes, and excludes key system directories to maintain usability. The wiper’s activation requires key-based authentication, adding control over the destructive phase. Anubis’s feature set also includes privilege escalation, directory exclusions, and configurable target paths. Despite listing only a few victims currently, the ongoing refinement of features like this wiper suggests a strategy to enhance technical confidence and affiliate engagement in future campaigns.
ETLM Assessment
Anubis is likely to increase its attack volume as its destructive capabilities mature. The integration of a wiper function could influence other RaaS groups to adopt similar coercive tactics. As affiliate confidence grows, wider deployment across industries can be expected, with enhanced pressure tactics reducing negotiation windows and forcing immediate ransom decisions, potentially making Anubis a high-impact threat in 2025.
Qilin Ransomware Adds Legal Pressure Tactics to Boost Payouts
The Qilin ransomware-as-a-service (RaaS) operation has introduced a “Call Lawyer” feature within its affiliate panel, aiming to psychologically pressure victims by simulating legal engagement during ransom negotiations. This addition reflects Qilin’s evolution into a full-spectrum cybercrime platform, offering affiliates not only malware but also services like spam distribution, DDoS attacks, PB-scale data storage, and in-house journalists. Qilin ranks among the top ransomware groups of 2025, with over 300 claimed victims, positioning itself to fill the vacuum left by defunct groups like LockBit and BlackCat. Its payloads, written in Rust and C, are supported by advanced features such as Safe Mode execution, automated negotiation tools, and network propagation capabilities. Recent activity spikes may be attributed to an influx of affiliates from rival groups. This strategic shift suggests Qilin’s ambition to dominate the ransomware landscape with operational maturity and psychological extortion tactics.
ETLM Assessment
Qilin’s use of legal simulation tools marks a new frontier in psychological extortion. Future campaigns may further gamify or automate negotiation dynamics to exploit organizational panic. As more affiliates migrate from defunct groups, Qilin is poised to escalate both in scale and sophistication, integrating multi-layered pressure techniques and evolving toward a ransomware ecosystem mimicking legitimate enterprise service models.
Ransomware Groups Exploit RMM Tools and Expand Espionage Tactics
Ransomware actors are actively exploiting unpatched SimpleHelp RMM software (versions ≤5.5.7), particularly leveraging CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 to achieve remote code execution, privilege escalation, and information disclosure. This vector has enabled actors like DragonForce to pivot from service providers to downstream victims in double extortion attacks. Meanwhile, Fog ransomware continues operations with a dual-use toolkit. Using VPN compromise or phishing, attackers deploy LNK-based droppers to download PowerShell scripts that deliver Fog lockers. Tactics include in-memory execution, endpoint evasion, and unusual use of tools like Syteca, GC2, Adaptix, and Stowaway for surveillance and post-exploitation. Fog targets both Windows and Linux and uses tools like MegaSync and FreeFileSync for data exfiltration. Persistence is ensured through delayed service creation, indicating long-term access intentions. LockBit operations also persist, with active affiliate recruitment post-panel leak and expanded geographic targeting, including China.
ETLM Assessment
Exploitation of third-party tools like RMM and monitoring software will intensify, with threat groups blending espionage and ransomware for dual objectives. Expect broader abuse of unpatched infrastructure and stealth tools, longer dwell times, and cross-platform targeting. Ransomware will increasingly serve as both a financial weapon and a smokescreen for persistent espionage-focused campaigns in industrial and critical sectors.
Former Black Basta Members Pivot to Teams Phishing, Python Payloads
In 2025, former affiliates of the Black Basta ransomware group resurfaced with evolving techniques, incorporating Microsoft Teams phishing and Python scripting into their intrusion campaigns. Initial access is gained via phishing messages posing as IT support, leading victims to initiate remote access tools like Quick Assist or AnyDesk. Following access, a Python script is retrieved through cURL requests and executed to establish command-and-control communications. The malware chain includes Java-based RATs that leverage cloud platforms such as Google Drive and OneDrive for proxying commands, facilitating data transfer, SOCKS5 tunneling, credential theft, and fake login overlays. The campaign also employs a tunneling backdoor known as QDoor and a Rust-based custom loader, with a Python RAT referred to as Anubis. Observed tactics mirror those seen in other ransomware operations, such as BlackSuit and 3AM, signaling affiliate crossover or code sharing. These developments showcase persistent post-Black Basta adaptation and a shift toward stealthy, multi-stage intrusion strategies.
ETLM Assessment
Expect broader abuse of legitimate platforms like Microsoft Teams and cloud services for ransomware delivery and C2 communication. The fusion of social engineering, cloud exploitation, and modular payloads will intensify. Threat actors linked to defunct groups will regroup, enhancing operational stealth and expanding cross-platform malware capabilities to target enterprise networks with prolonged persistence and higher ransom leverage.
Teamxxx
Teamxxx is a newly emerged ransomware group that launched its leak site in early June 2025 and has since claimed nine victims. Currently, limited information is available regarding the group’s tactics or affiliations. CYFIRMA is actively monitoring Teamxxx’s activities and will provide updates as further intelligence emerges.

Warlock
Warlock is a new ransomware that is built on the Chaos ransomware framework, encrypting files with a randomized extension and dropping a ransom note named read_it.txt. It demands payment in Bitcoin and avoids lateral movement. Infection vectors likely include RDP brute-force or drive-by-downloads, and its payload focuses on single-system impact without data exfiltration. During the writing of this report, the ransomware has claimed 19 victims.

kawa4096
A newly identified ransomware variant, KaWaLocker, rapidly encrypts multiple file types upon infecting a system, appending a randomly generated character string to each filename to hinder identification and recovery. It also drops a ransom note named “!!Restore-My-file-Kavva.txt” in affected directories, detailing payment instructions for data decryption. During this period, the ransomware group claimed 9 victims globally.

Ransomware Breach at Sensata Disrupts Operations, Exposes Employee Data
A recent ransomware attack on Sensata led to significant operational disruption and data exfiltration. Threat actors maintained unauthorized access to the network for several days, extracting sensitive files containing personally identifiable information. The compromised data includes names, Social Security numbers, financial and medical records, driver’s license and passport numbers, and health insurance details. Both current and former employees, along with their dependents, were impacted, with the scope of data exposure varying by individual. Credit monitoring and identity theft protection services have been offered. Although ransomware was involved and data theft confirmed, no specific ransomware group has claimed responsibility, highlighting the growing trend of double-extortion attacks where encryption is combined with data theft to increase leverage over victims. It also reinforces the vulnerability of industrial and operational environments to targeted ransomware campaigns that exploit gaps in detection and response capabilities.
Chaos Ransomware Hits Optima, Steals and Leaks Sensitive Data
A recent double-extortion attack by the Chaos ransomware group targeted a U.S.-based tax resolution firm, resulting in both server encryption and data theft. The threat actors exfiltrated approximately 69 GB of sensitive data, now listed on their data leak site. Stolen information includes customer case files and tax documents, which typically contain Social Security numbers, contact details, and home addresses, raising risks of identity theft and further exploitation. (This marks one of several recent claims by Chaos, a ransomware group that emerged in March 2025 and should not be confused with the older Chaos ransomware builder toolkit used in phishing campaigns.) In this attack, Chaos encrypted internal servers while simultaneously stealing data, following a typical double-extortion model to pressure the victim into payment. The group also recently claimed responsibility for other high-profile intrusions, highlighting its rapid expansion and aggressive tactics within the ransomware ecosystem targeting data-rich industries.
Interlock Ransomware Hits Kettering Health, Leaks Sensitive Medical Data
A recent ransomware attack attributed to the Interlock group severely impacted a major healthcare provider, disrupting operations and leading to the exfiltration of approximately 941 GB of sensitive data. The attackers leveraged tools and persistence mechanisms that have since been removed following a comprehensive forensic review and network hardening. The intrusion disrupted access to electronic health records, patient communication systems, and forced medical staff to revert to manual processes. Interlock has published samples of stolen data, which reportedly include patient records, pharmacy and blood bank documents, payroll data, internal police files, and scanned identity documents such as passports. Known for targeting the healthcare sector, Interlock is linked to ClickFix intrusions that masquerade as legitimate IT tools and has deployed a custom RAT named NodeSnake in previous campaigns. This incident underscores the group’s growing capabilities in exploiting healthcare infrastructure through sophisticated initial access techniques and large-scale data exfiltration.
Qilin Ransomware Breach Disrupts Lee Enterprises, Leaks Sensitive Data
A ransomware attack attributed to the Qilin group targeted a major U.S. publishing network, resulting in widespread service disruption and the exfiltration of sensitive personal and corporate data. Attackers gained unauthorized access on February 3, encrypting critical applications and stealing approximately 350 GB of data, including 120,000 documents. Exfiltrated files reportedly contained Social Security numbers, driver’s licenses, financial account details, health insurance records, and internal documents such as contracts and spreadsheets. The breach affected nearly 40,000 individuals, prompting notification to impacted parties and regulatory filings. The incident caused significant operational downtime, disrupting newspaper printing, delivery, VPN access, and internal systems. Qilin later listed the victim on its dark web leak site, sharing samples to pressure for payment under a double-extortion model. The campaign highlights Qilin’s strategic focus on data-rich sectors and its evolving tactics that combine encryption with large-scale data theft to increase impact, visibility, and extortion leverage.
Ryuk Ransomware Access Broker Extradited for Global Intrusions
A key member of the Ryuk ransomware operation has been extradited following international law enforcement efforts targeting ransomware activity across multiple countries. The 33-year-old suspect, arrested in Kyiv, specialized in identifying vulnerabilities within corporate networks and providing unauthorized access to ransomware affiliates. This access was later used to exfiltrate data and deploy ransomware payloads. The investigation began in 2023 and targeted actors behind several ransomware families, including Ryuk, LockerGoga, MegaCortex, Hive, and Dharma. Seized digital evidence helped identify the individual’s role in Ryuk’s attack chain. Ryuk was active between 2018 and 2020, targeting critical sectors worldwide, including healthcare. It later evolved into the Conti ransomware operation, which splintered into multiple active threat groups. Ryuk is estimated to have collected over $150 million in ransom payments during its operations. The extradition underscores the increasing global focus on dismantling ransomware supply chains by targeting access brokers and technical enablers.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware remains a major threat to both organizations and individuals, locking critical data and demanding payment for its release. The consequences extend well beyond the ransom, often leading to costly recovery efforts, extended downtime, reputational harm, and potential regulatory fines. Such disruptions can destabilize operations and erode stakeholder trust. Addressing this growing risk demands a proactive cybersecurity posture and stronger collaboration between the public and private sectors to build resilience against future attacks.
Victimology
Cybercriminals are increasingly targeting industries that manage vast amounts of sensitive data, ranging from personal and financial information to proprietary assets. Sectors such as manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology remain high on the threat radar due to their complex and extensive digital infrastructures. Adversaries strategically exploit vulnerabilities in economically advanced regions, launching well-planned attacks designed to encrypt critical systems and extract significant ransom payments. These operations are calculated to yield maximum financial returns.
The ransomware threat landscape in June 2025 revealed a shift toward modular, evasive, and high-impact operations. While overall victim numbers declined slightly, key groups like Qilin demonstrated technical maturity by exploiting zero-day vulnerabilities and introducing legal pressure tactics. Emerging groups such as Fog and Anubis showcased complex toolchains, indicating a strategic pivot to stealth and long-term compromise. Established actors also began leveraging legitimate tools and cloud platforms for persistence and data exfiltration. Organizations must enhance resilience, as ransomware now operates as a service ecosystem, rapidly adapting to security countermeasures.