


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Target Countries: USA
Target Industry: Finance
Introduction
CYFIRMA Research and Advisory Team has found Sinobi Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Sinobi Ransomware
Researchers identified a new ransomware variant known as Sinobi, which emerged in late June 2025. This crypto ransomware employs a combination of AES and RSA encryption algorithms to lock victims’ files, appending them with the .SINOBI extension. Upon infection, victims receive a ransom note titled README.txt, instructing them to contact the attackers via a Tor-based chat site to negotiate payment. The note emphasizes that the group is financially motivated, not politically, and offers proof of data decryption and a list of exfiltrated files. Victims are given seven days to initiate communication, with warnings against using third-party recovery tools or rebooting their systems.

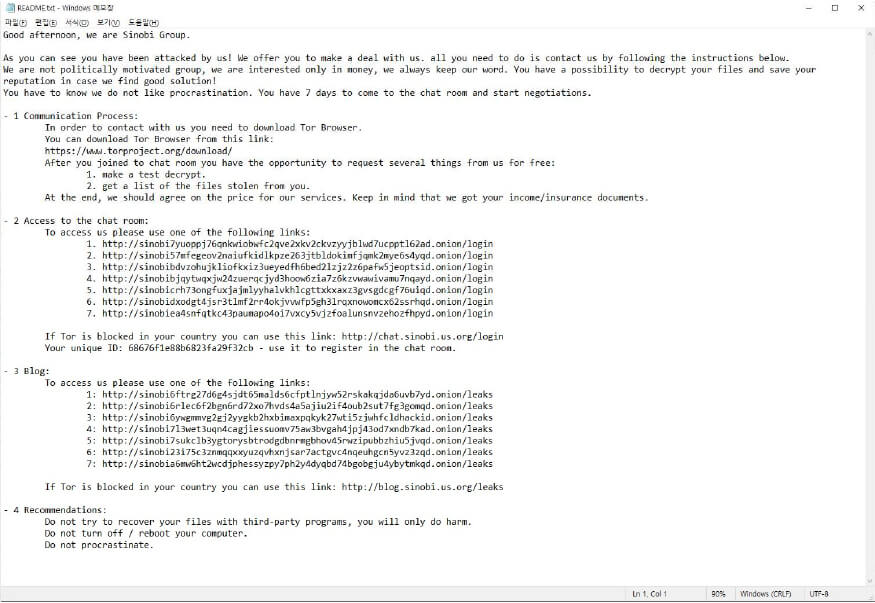
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Privilege Escalation | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1070.004 | Indicator Removal on Host: File Deletion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1218.011 | Signed Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1482 | Domain Trust Discovery |
| Discovery | T1518 | Software Discovery |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Lateral Movement | T1021.003 | Remote Services: Distributed Component Object Model |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1572 | Protocol Tunneling |
| Collection | T1005 | Data from Local System |
| Collection | T1074 | Data Staged |
| Collection | T1113 | Screen Capture |
| Collection | T1114 | Email Collection |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that the Sinobi ransomware group is likely to evolve rapidly, with signs pointing toward a possible rebrand or pivot from the now- dormant Lynx group. Given its current tactics and infrastructure, Sinobi may shift to a Ransomware-as-a-Service (RaaS) model, expand into double extortion operations, and broaden its targeting beyond finance to sectors like healthcare and manufacturing. As the group refines its methods, including credential theft and lateral movement via USB, Sinobi is positioned to become a persistent and scalable global threat in the ransomware landscape.
Sigma rule:
title: Suspicious desktop.ini Action
Description: Detects unusual processes accessing desktop.ini, which can be leveraged to alter how Explorer displays a folder’s content (i.e. renaming files) without changing them on disk.
tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Botnet| Objectives: Operational Disruption | Target Technologies: Linux OS, Routers, DVRs | Target Geography: Global | Exploited Vulnerability: CVE-2024-3721, CVE- 2024-12856
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “RondoDox” is trending.
About Malware RondoDox
The RondoDox botnet has recently emerged as a growing threat, exploiting two critical vulnerabilities – CVE-2024-3721 in TBK DVRs and CVE-2024-12856 in Four-Faith routers—to gain access to targeted devices. Once inside, it uses stealthy tactics to avoid detection, disguising its traffic as that from popular online games or VPN services. RondoDox also ensures it stays active on infected systems through strong persistence methods and can launch disruptive DDoS attacks using multiple protocols. Its ability to blend in, stay hidden, and exploit specific flaws highlights the urgent need for timely security updates and increased awareness around connected device vulnerabilities.
Attack Strategy
RondoDox, which was initially distributed to infect Linux systems running on ARM and MIPS architectures, is now showing signs of expanding its reach to a much wider range of
Linux-based devices. Recent evidence points to a downloader script that can install the malware on systems using various processor types, including older and more common ones like Intel and PowerPC. The script is designed to quietly prepare the system, locate a suitable environment to run the malware, and then erase its tracks to avoid detection.
This shift signals that RondoDox is becoming more adaptable and determined to infect as many systems as possible, making it a growing concern for Linux environments across different hardware platforms.
Technical Analysis
RondoDox demonstrates a multi-layered approach built to remain hidden and maintain control over Linux-based environments for extended periods. Its configuration is hidden through simple obfuscation and decoded during execution, after which it establishes persistence by modifying system files and startup routines. Even if one method fails, others ensure it reactivates on reboot. The malware also neutralizes security and monitoring tools by terminating known analysis processes, helping it operates without interruption.
Interestingly, it drops an unused email reference—likely a relic or placeholder—in a hidden file, hinting at either future use or abandoned features.
Once embedded, RondoDox corrupts essential system files by renaming key executables, effectively disrupting critical functions like firewall management and user control. This tactic not only impairs recovery but also makes systems unstable. After completing its setup, it connects to its control server and can launch powerful distributed denial-of-service (DDoS) attacks through HTTP, UDP, and TCP protocols. To avoid detection, it disguises its traffic using patterns from popular games and services such as Fortnite, Roblox, and Discord. It can even imitate encrypted communication protocols like OpenVPN and WireGuard, blending in with legitimate network behavior. This level of impersonation makes RondoDox difficult to detect and positions it as a technically advanced threat engineered for both persistence and evasion.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Persistence | T1543 | Create or Modify System Process |
| Persistence | T1543.002 | Create or Modify System Process: Systemd Service |
| Privilege Escalation | T1543 | Create or Modify System Process |
| Privilege Escalation | T1543.002 | Create or Modify System Process: Systemd Service |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Discovery | T1082 | System Information Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as threats like RondoDox continue to evolve, their impact is expected to extend beyond individual systems and into the broader digital infrastructure that supports daily operations across sectors. By exploiting unpatched vulnerabilities in network-facing devices, RondoDox can silently compromise Linux-based systems embedded in critical equipment and edge infrastructure. This covert misuse can lead to unexpected network instability, service disruptions, or become part of coordinated attacks affecting public platforms. For organizations, the presence of silently exploited systems—especially those beyond direct visibility—may lead to prolonged investigation cycles, delayed recovery, and growing uncertainty around the integrity of their operational environment.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule RondoDox_Botnet_Indicators
{
meta:
description = “Detects RondoDox Botnet-related strings ” author = ” CYFIRMA ”
threat_name = “RondoDox”
strings:
// IP addresses
$ip1 = “45.135.194.34”
$ip2 = “83.150.218.93”
$ip3 = “14.103.145.202”
$ip4 = “14.103.145.211”
$ip5 = “154.91.254.95”
$ip6 = “78.153.149.90”
// SHA-256 Hashes
$sha256_1 = “c88f60dbae08519f2f81bb8efa7e6016c6770e66e58d77ab6384069a515e451c”
$sha256_2 = “eb3e2a6a50f029fc646e2c3483157ab112f4f017406c3aabedaae0c94e0969f6”
$sha256_3 = “f4cd7ab04b1744babef19d147124bfc0e9e90d557408cc2d652d7192df61bda9”
$sha256_4 = “e3c080e322862d065649c468d20f620c3670d841c30c3fe5385e37f4f10172e7”
$sha256_5 = “e62df17150fcb7fea32ff459ef47cdd452a21269efe9252bde70377fd2717c10”
$sha256_6 = “53e2c2d83813d1284ddb8c68b1572b17cca95cfc36a55a7517bf45ff40828be5”
$sha256_7 = “43d4847bf237c445ed2e846a106e1f55abefef5c3a8545bd5e4cad20f5deb9a4”
$sha256_8 = “4c2429fc8b8ec61da41cbba1b8184ec45fa93a9841b4ca48094bba7741b826b8”
$sha256_9 = “694d729d67f1b0c06702490bfab1df3a96fe040fe5d07efa5c92356c329757be”
$sha256_10 = “edae3b75deb8013bd48ac4534cca345b90938a2abb91672467c2bf9ae81ff683”
$sha256_11 = “0814a0781ab30fca069a085dba201d6fd0f414498fafa4bb42859786d91d4781”
$sha256_12 = “59b4deee977e9e27b60e7e179d54a1ce8e56624e73b799523416eee828bfaf76”
$sha256_13 = “9f916a552efc6775367a31357a633dc0be01879830d3fddccdf3c40b26e50afd”
$sha256_14 = “0a9ebbecc8ec58c253039520304ca373cfb8d1674d67993e6485e244a77d6ec9”
$sha256_15 = “6c81fd73b4bef6fef379cbefdcce7f374ea7e6bf1bf0917cf4ca7b72d4cee788”
$sha256_16 = “a55a3859a203ca2bae7399295f92aeae61d845ffa173c1938f938f5c148eef99”
$sha256_17 = “57573779f9a62eecb80737d41d42165af8bb9884579c50736766abb63d2835ba”
$sha256_18 = “3daa53204978b7797bd53f5c964eed7a73d971517a764785ce3ab65a9423c2e7”
$sha256_19 = “8bf8928bc255e73e0b5b0ce13747c64d82d5f2647da129f189138773733ac21f”
$sha256_20 = “20a24b179bdbbdcc0053838c0484ea25eff6976f2b8cb5630ab4efb28b0f06b5”
$sha256_21 = “42aa715573c7d2fca01914504cb7336db715d73d1e20d23e4bd37f2e4f4fe389”
$sha256_22 = “c9278ce988343606350a94156ca28ee28bd605d1d95c810a16866eee1f997598”
$sha256_23 = “a197f60d5f5641f2c56576b4c867d141612c6e00db29c512f266835510b8a62d”
$sha256_24 = “8250d289c5ec87752cec1af31eed0347cf2dd54dc0fbeea645319c4dae238ee2”
$sha256_25 = “d02414a54e97ad26748812002610f1491a2a746e9ba0f9d05de3d47d7bab4f5e”
$sha256_26 = “c123a91fdacd9a4c0bcf800d6b7db5162cfd11cb71e260647ef0f2c60978ebfc”
$sha256_27 = “ef708fec1afbea4fb32b586e0dacf0d228c375a532008d81453c367256afea5a”
$sha256_28 = “305507f34c14c72cab35715b7f7b25b32352a8e19b8a283003aaf539d12ca517”
$sha256_29 = “937e6ab0dfcedfa23eced7b52d3899b0847df3fcb7a9c326b71027a7ab5f5b93”
condition:
any of ($ip*) or any of ($sha256*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
APT36 (Transparent Tribe): The Persistent Adversary Behind South Asian Cyberattacks
About the Threat Actor
Transparent Tribe, also known as APT36, ProjectM, Mythic Leopard, Earth Karkaddan, and SideCopy, is a Pakistan-based state-sponsored advanced persistent threat (APT) group active since at least 2013. The threat actor is known for spear-phishing campaigns exploiting Windows OLE vulnerabilities, watering-hole attacks, and deploying a range of malware, including Crimson RAT, CapraRAT, and DRAT. The group operates by impersonating government or defence entities, leveraging spoofed domains and decoy documents to lure victims. It demonstrates operational overlaps with various subgroups such as SideCopy, TAG-140, and has shown potential coordination & collaboration with hacktivist affiliates, including Team Crack Codes and Cyber Legion PK.
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1587.003 | Develop Capabilities: Digital Certificates |
| Resource Development | T1608.004 | Stage Capabilities: Drive-by Target |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.002 | Phishing: Spear-phishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Command and Control | T1568 | Dynamic Resolution |
Latest Developments Observed
The threat actor, identified as TAG-140 with potential established links to SideCopy and Transparent Tribe, has been observed deploying a modified variant of the DRAT remote access trojan (DRAT V2) to target Indian government entities, as well as the defence and transportation sectors, indicating a modular and evolving approach to cyber-espionage. The group’s latest campaign involved spoofing the Indian Ministry of Defence’s press release portal to deliver DRAT V2, which features enhanced command-and-control capabilities and supports arbitrary shell command execution. The primary motive behind these attacks appears to be the exfiltration of sensitive information from high-value targets in India.
ETLM Insights
The Pakistan-based nation-state threat actor APT36 is believed to operate with backing from the country’s military intelligence, primarily targeting India and allied nations. The group employs a range of social engineering tactics, such as emotionally charged themes, disinformation, and luring techniques, including honey traps, to compromise individuals and organizations and exfiltrate sensitive information.
There are indications that APT36 may be receiving infrastructure support from other nation-state actors, including Chinese-affiliated groups and Turkish-speaking threat groups, who have historically supported Pakistan with logistics, intelligence, and ammunition, particularly during operations such as the Op Sindoor conflict.
The threat actor is expected to continue advancing its capabilities by developing more sophisticated, cross-platform malware and possibly integrating AI-driven evasion techniques. Future campaigns may increasingly leverage legitimate cloud services and communication platforms while expanding their focus to include mobile and IoT devices. Additionally, the group is likely to employ highly targeted social engineering tactics aligned with real-time events to enhance effectiveness.
The actor is also anticipated to adopt automated attack delivery mechanisms, diversify its malware payloads, and rapidly evolve in response to emerging defence measures. These advancements will likely result in more persistent, scalable, and difficult-to-detect operations across multiple industries.
YARA Rules
rule APT36_MultiIndicator_Threat
{
meta:
author = “CYFIRMA”
description = “Detects malware and artifacts associated with APT36 (Transparent Tribe)”
threat_actor = “APT36” last_updated = “2025-07-08”
strings:
// File names commonly used in APT36 delivery
$fname1 = “noway.bat” wide ascii
$fname2 = “index.php” wide ascii
$fname3 = “sysinte.hta” wide ascii
$fname4 = “survey.pdf” wide ascii
$fname5 = “Briefing_MoD_April25.docx” wide ascii
$fname6 = “Alert_Kavach_Update.exe” wide ascii
// Known malicious URLs/domains (C2 or lure pages)
$url1 = “email.gov.in.drdosurvey.info” nocase
$url2 = “trade4wealth.in” nocase
$url3 = “toner-digital.com” nocase
$url4 = “kavach-app.com” nocase
$url5 = “gov-inportal.org” nocase condition:
// Match any one or more unique indicators (filenames, URLs, or behavior) (any of ($fname*) or any of ($url*))
}
Strategic
Management
Tactical
Italy arrests Chinese industrial cyber espionage operative, OpenAI tightens cybersecurity in the face of Chinese spying threats
Italian authorities arrested Xu Zewei, a Chinese citizen, at Milan’s Malpensa airport, following a US international warrant, Italian police confirmed. The 33-year-old is suspected of ties to Hafnium, a Chinese government-backed hacking group accused of stealing Covid-19 vaccine secrets from the US in 2020 and breaching Microsoft email software in 2021. The suspect is detained in an Italian jail near the airport, with extradition proceedings set to begin in a Milan court.
The arrest could complicate diplomacy for Prime Minister Giorgia Meloni, who balances strong US ties, including a personal rapport with President Donald Trump, along with maintaining cordial relations with Beijing, despite Italy’s withdrawal from China’s Belt and Road Initiative, possibly setting Italy up for cyber retaliation from Beijing. Deputy Prime Minister Matteo Salvini’s upcoming Beijing visit adds to the delicate situation.
Meanwhile, OpenAI has strengthened its security to protect intellectual property from corporate espionage, particularly after alleged targeting by Chinese competitors. In recent months, the $300bn San Francisco-based AI company implemented tighter controls on sensitive data and enhanced staff vetting, measures put in place to prevent industrial espionage from Chinese competitors.
ETLM Assessment:
During the COVID-19 pandemic, the FBI and the US Cybersecurity Agency accused China of hacking US coronavirus research. This allegation came on top of years of intellectual property theft in which the Chinese government has been directly involved. As predicted by CYFIRMA analysts, the moves of the current US administration towards a more balanced trade relationship with diminishing overt IP transfer are pushing China to double down on covert efforts to illegally gain competitor intellectual property, the main tool of which would be cyber espionage. China is a global champion in using cyber-attacks as a tool of statecraft, and the hands-on role of the government in the economy only reinforces the drive to use cyber-attacks for IP theft, even in matters that are of no military or dual use. China has a bigger hacking program than that of every other major nation combined, and any large company in industries outlined in Chinese development plans will need to invest in external threat landscape management solutions to stay ahead of relentless and repeated assaults by Chinese hackers.
Qilin Ransomware Impacts the Cenomi Retail
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia, Cenomi Retail (https[:]//www[.]cenomiretail[.]com/), was compromised by Qilin Ransomware. Cenomi Retail is a retail company specializing in sports merchandise, clothing, and fashion, with a presence spanning North America, the Middle East, Africa, and Asia, including operations in Saudi Arabia and Japan. The compromised data reportedly includes signed contracts, employee personal information, customer contracts, source code for web applications, SQL and other codebases, financial records, sales data, API details, databases, reports, and various other sensitive information. The total volume of the exposed data is estimated to be approximately 816 GB.
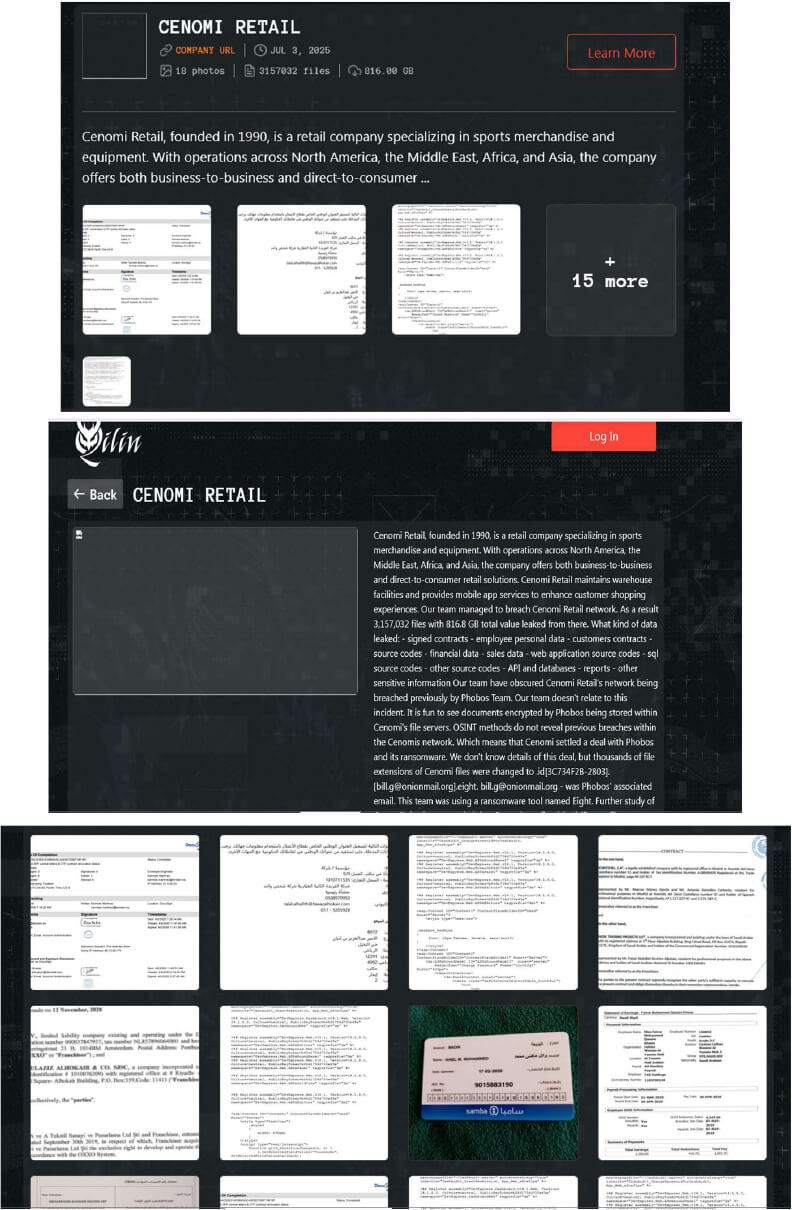
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
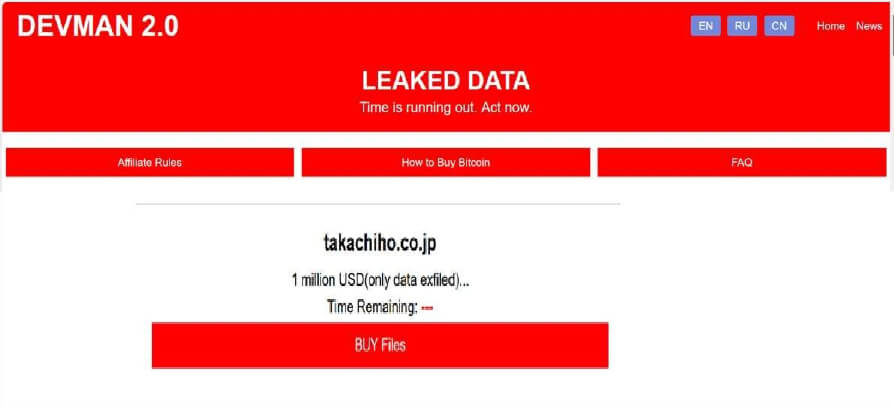
DevMan ransomware impacts Takachiho Co., Ltd.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Takachiho Co., Ltd. (website: takachiho[.]co[.]jp), was compromised by DevMan ransomware. Takachiho Co., Ltd. is a Japanese company primarily engaged in the manufacturing, wholesale, and retail of tourism souvenirs and confectionery products. The compromised data consists of confidential and sensitive information related to the organization. The Asking price for compromised data is 1 million USD.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, DevMan ransomware is a sophisticated, evolving threat built on established ransomware codebases but with unique features and flaws. It exemplifies the growing ransomware-as-a-service trend, posing significant risks to Windows environments, especially in Asia and Africa.
Vulnerability in DjVuLibre
Relevancy & Insights: The vulnerability exists due to a boundary error when processing untrusted input within the MMRDecoder::scanruns method.
Impact: A remote attacker can create a specially crafted file, trick the victim into opening it using the affected software, trigger an out-of-bounds write, and execute arbitrary code on the target system.
Affected Products: https[:]//github[.]blog/security/vulnerability-research/cve-2025- 53367-an-exploitable-out-of-bounds-write-in-djvulibre/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
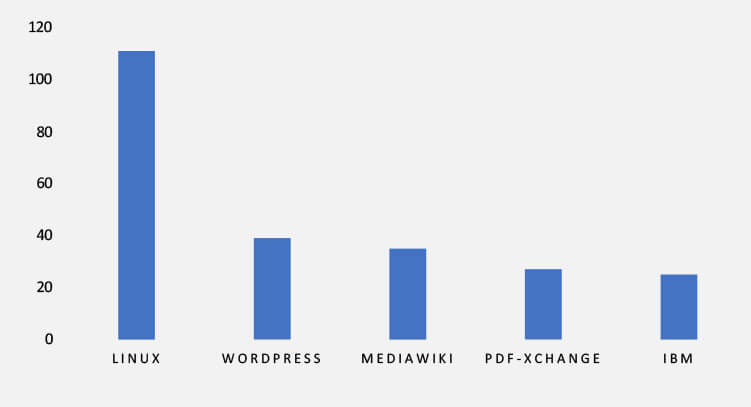
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in DjVuLibre can pose significant threats to user privacy and security. This can impact various industries globally, including publishing, education, research, and digital archiving. Ensuring the security of DjVuLibre is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding document rendering and compression processes, especially when handling scanned documents and images across different geographic regions and sectors.
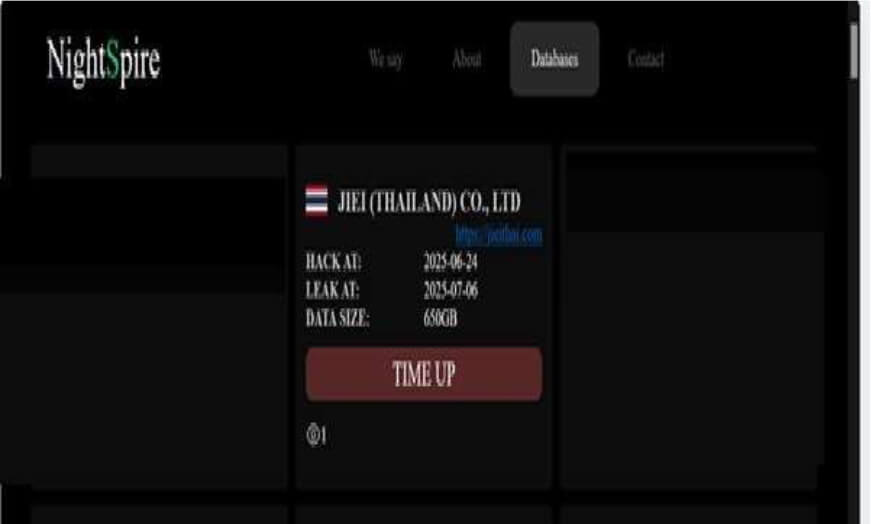
NightSpire Ransomware attacked and published the data of JIEI CO., LTD
Summary:
Recently, we observed that NightSpire Ransomware attacked and published the data of the JIEI CO., LTD (https[:]//jieithai[.]com/) on its dark web website. JIEI (Thailand) Co., Ltd. is a company specializing in the production of rubber products primarily for construction materials, automobiles, and various industrial applications. It operates with a focus on the ASEAN region and employs advanced proprietary technologies to deliver high-precision rubber components that support the manufacturing of aesthetically pleasing and comfortable vehicles. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The total size of the data compromised is approximately 650 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
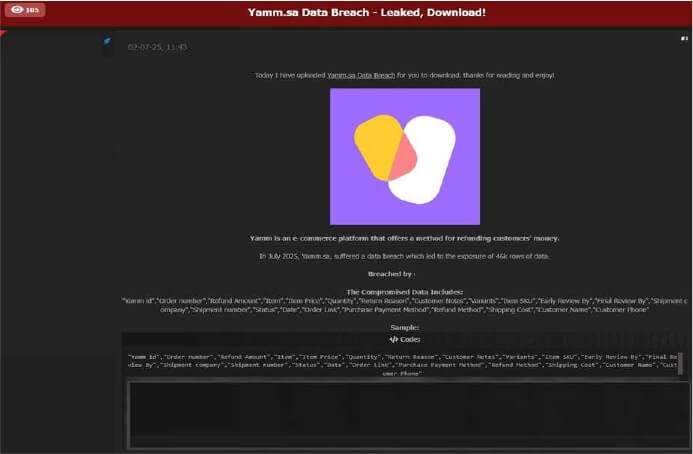
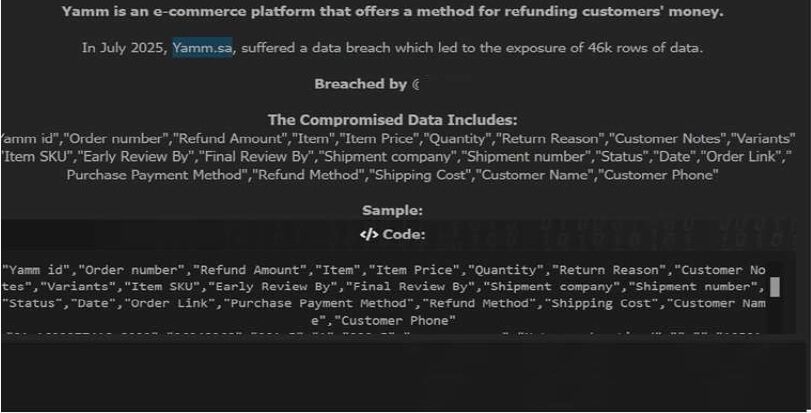
Yamm Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Yamm (https[:]//yam[.]sa/) in an underground forum. Yamm is an e-commerce platform that offers a method for refunding customers’ money. The compromised data includes sensitive details, such as Yamm ID, order number, refund amount, item name, item price, quantity, return reason, customer notes, product variants, item SKU, early and final review by personnel, shipping company, shipment number, return status, date, order link, purchase payment method, refund method, shipping cost, customer name, and customer phone number. The breach has been attributed to the threat actor known as “888.”
Global Insurance Company (GIC) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor identified as “UPS” claimed to be selling a partial database stolen from the Global Insurance Company (GIC) of Vietnam. According to the forum post, the dataset includes information on 65,997 customers and over 4,000 personal insurance contracts. The leak allegedly contains full personal details, contract records, government ID numbers, emails, phone numbers, birthdates, and insurance policy documents.
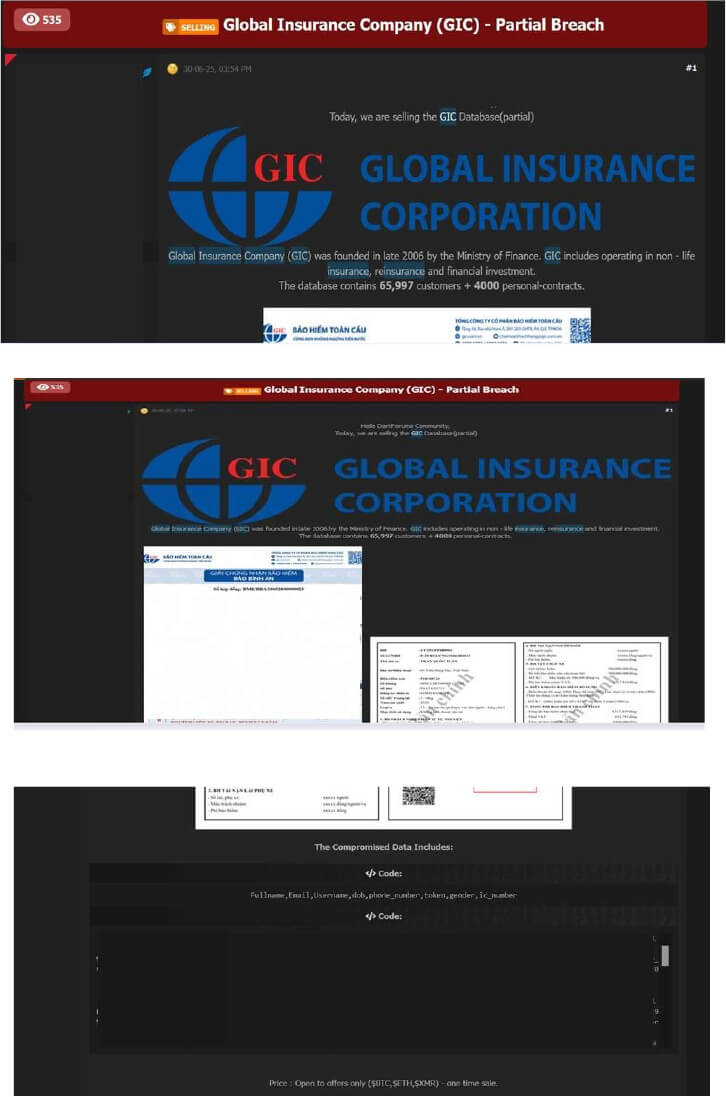
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat Actor “888” is a persistent and notorious cybercriminal entity with a mixed record of verified and unverified data breaches, focusing on stealing and leaking sensitive data from large organizations worldwide to extort or sell information illicitly. Their activities highlight ongoing cybersecurity challenges for multinational corporations and institutions.
Recommendations: Enhance the cybersecurity posture by:
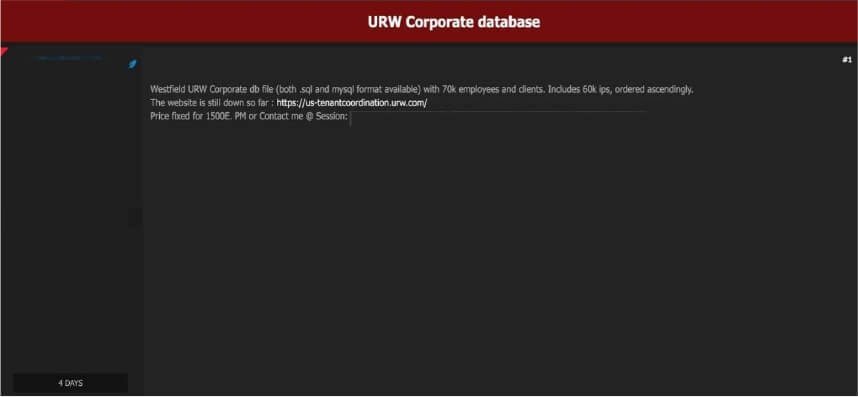
The CYFIRMA Research team has observed that a threat actor has allegedly breached and is offering for sale the corporate database of Unibail-Rodamco- Westfield (URW), a prominent global player in commercial real estate.
Headquartered in Paris, URW owns, develops, and manages an extensive portfolio of high-profile shopping centers, office buildings, and convention venues across Europe and the United States, including 39 properties under the well-known Westfield brand. Given the company’s vast international presence, a breach of this nature raises significant concerns for its employees, clients, and business partners.
The alleged breach was disclosed on a hacking forum, where the threat actor advertised the URW corporate database for sale at €1,500. The database, reportedly available in both .sql and MySQL formats, is said to contain sensitive corporate information. Additionally, the attacker claimed that the US tenant coordination portal—a key platform used to manage URW’s relationships with retail tenants in the U.S.—was rendered inaccessible due to the incident.
The compromised data allegedly includes a significant amount of information belonging to both company personnel and clients. The threat actor specified the contents of the database as including:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
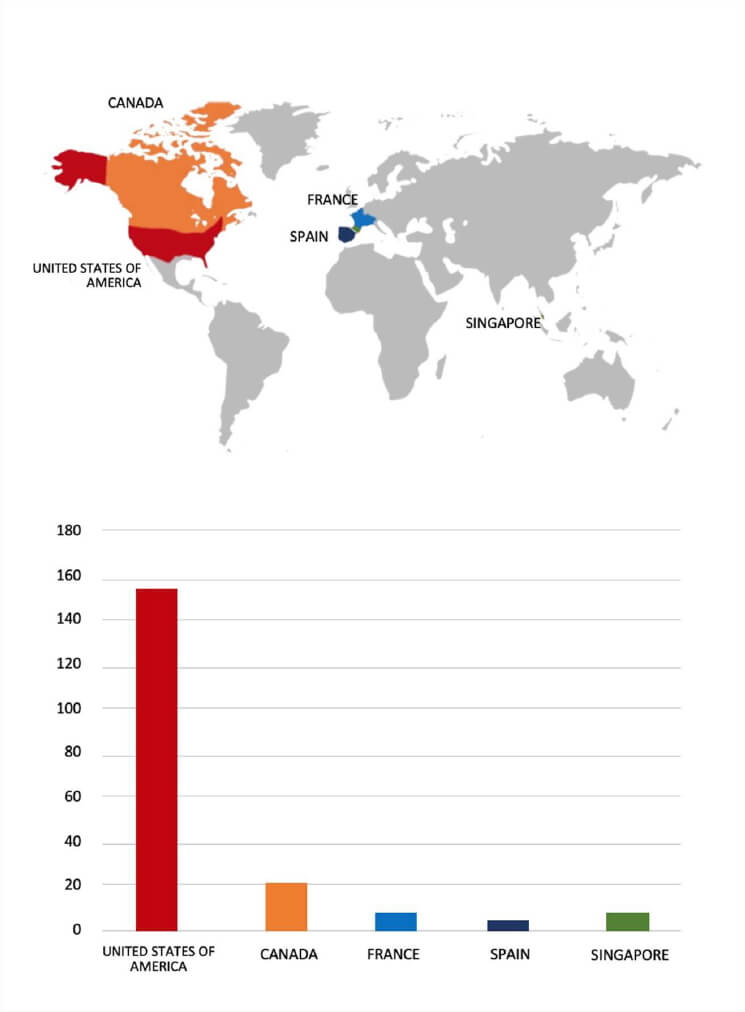
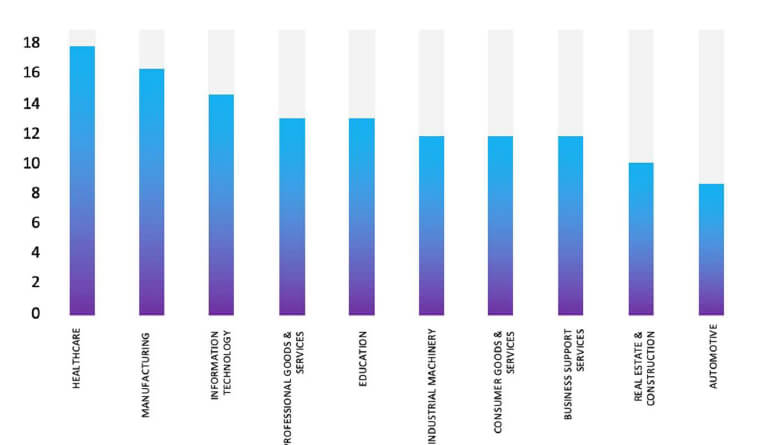
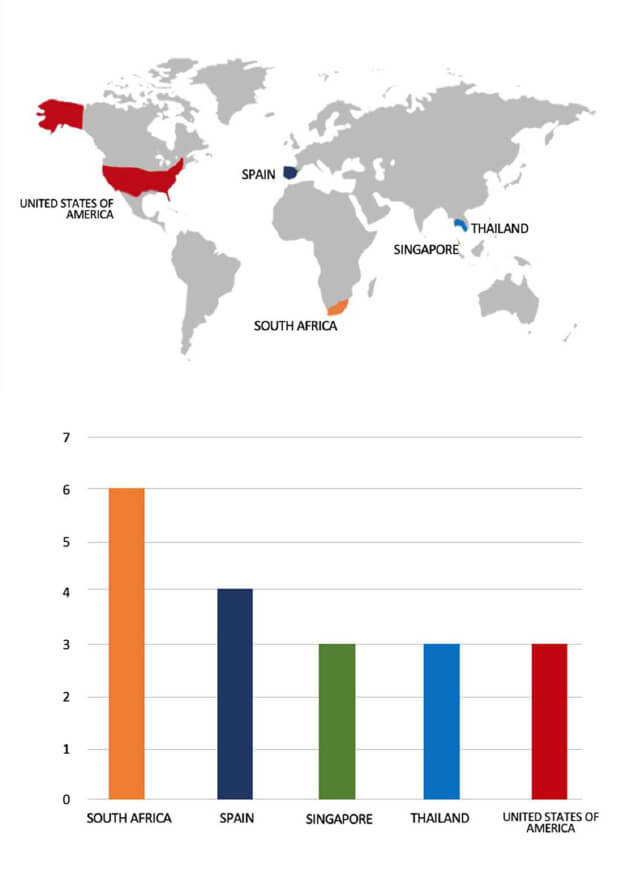
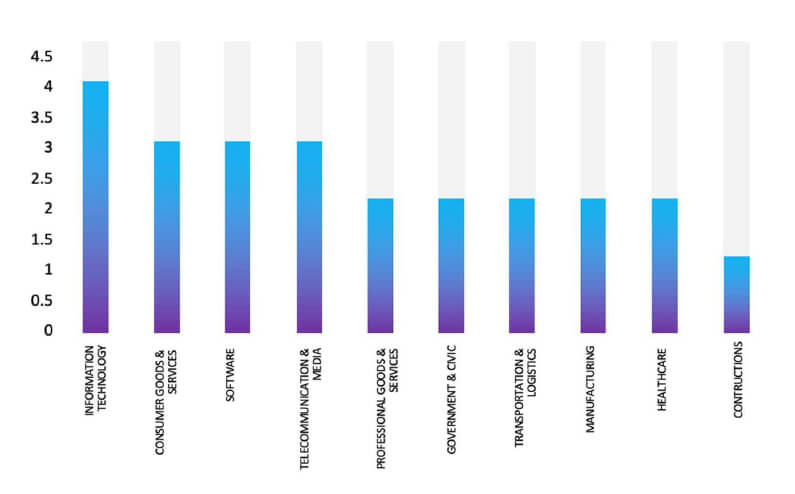
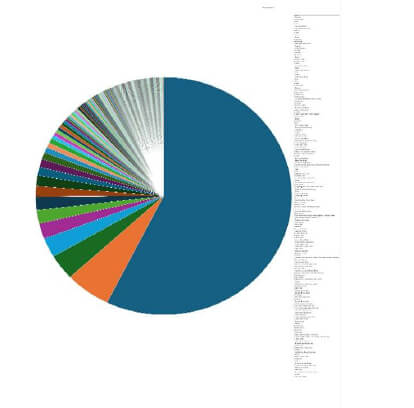
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
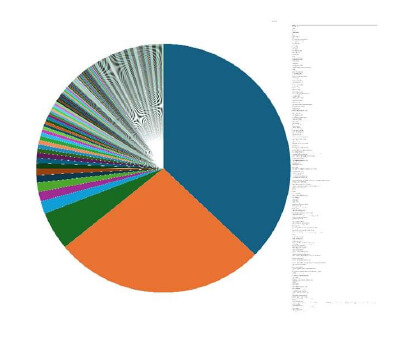
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.