Why Cyber Threat Actors Target Australia?Why Cyber Threat Actors Target Australia?Why Cyber Threat Actors Target Australia?Why Cyber Threat Actors Target Australia?Why Cyber Threat Actors Target Australia?
Why Cyber Threat Actors Target Australia?
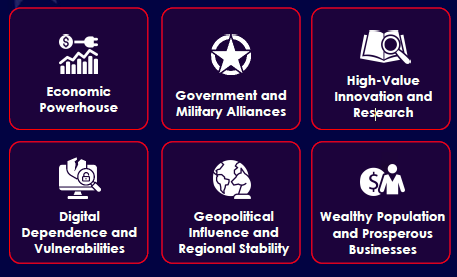
CYFIRMA observed consistent cyber campaigns targeting Australia, with peaks in 2021 (23) and a resurgence in 2024 (19). While 2025 shows a dip, it likely reflects partial-year data rather than reduced threat activity. The sustained volume highlights Australia’s strategic relevance to threat actors. Executive-level vigilance and proactive defense remain essential to strengthen the cyber security posture in the region.
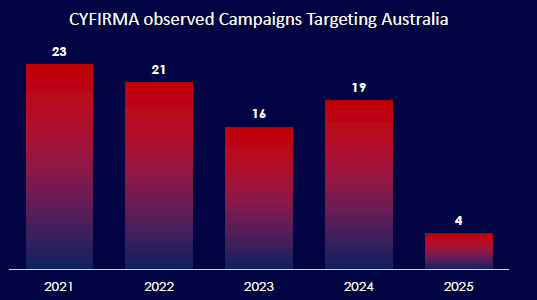
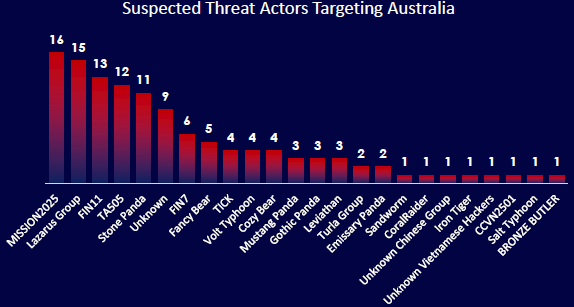
CYFIRMA observed a diverse set of threat actors targeting Australia, led by MISSION2025, Lazarus Group, and FIN11, indicating sustained interest from both state-linked and financially motivated groups. Notably, top actors are linked to China, North Korea, and Russia, reflecting geopolitical and economic motives. The presence of unidentified and regional actors signals an evolving threat landscape. Strategic defense planning must account for both known and emerging adversaries.
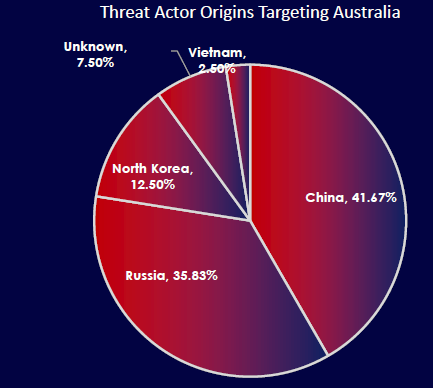
CYFIRMA observed that the majority of threat actors targeting Australia originate from China (41.67%) and Russia (35.83%), reflecting intense geopolitical and economic interest. North Korea and Vietnam also contribute to the threat landscape. This concentration of hostile activity from state-linked actors demands a cyber defense strategy aligned with national security priorities.
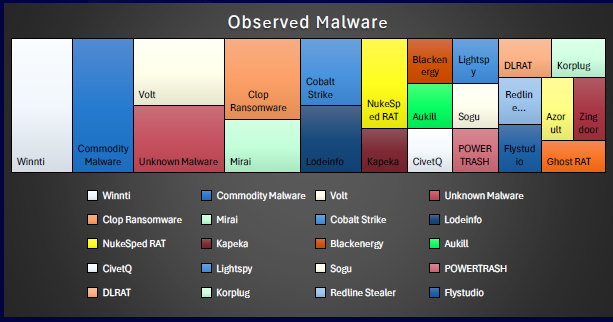
CYFIRMA observed that cyber threat actors targeting Australia primarily focus on exploiting web applications and operating systems technologies with broad exposure and high impact. Lesser but notable targeting includes application infrastructure, VPNs, and remote access tools, indicating efforts to infiltrate networks and maintain persistence. The pattern reflects a clear preference for high-leverage entry points in enterprise environments.

CYFIRMA observed that the majority of threat actors targeting Australia originate from China (41.67%) and Russia (35.83%), reflecting intense geopolitical and economic interest. North Korea and Vietnam also contribute to the threat landscape. This concentration of hostile activity from state-linked actors demands a cyber defense strategy aligned with national security priorities.
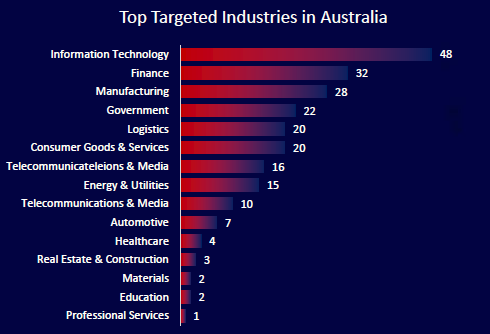
CYFIRMA observed that Information Technology, Finance, and Manufacturing are the top three industries targeted by threat actors in Australia. Critical sectors such as Government, Logistics, and Energy also faced significant targeting, reflecting adversaries’ focus on disrupting high-value and operationally essential verticals. The broad spread of targets highlights a strategic approach by both cybercriminal and nation-state actors to exploit systemic and economic vulnerabilities.
Year-to-Year Elevation: High
CYFIRMA observed a steady rise in global ransomware activity, with 4,723 victims in 2023, peaking at 5,123 in 2024. In just the first half of 2025, 3,567 victims have already been recorded, signaling an aggressive and sustained pace by ransomware groups. The global threat landscape remains highly active, with no signs of slowdown.

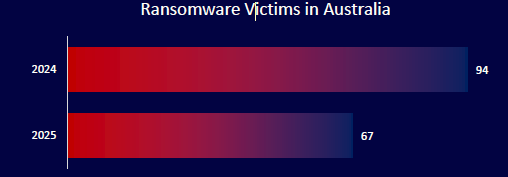
CYFIRMA observed 94 ransomware victims in Australia in 2024 and 67 cases already in the first half of 2025 (as of July 1st). This indicates a continued high tempo of ransomware operations. Australia remains one of the top-targeted countries globally, with threat actors leveraging data theft, extortion, and leak site pressure tactics to maximize impact.
Ransomware Groups Targeting Australia
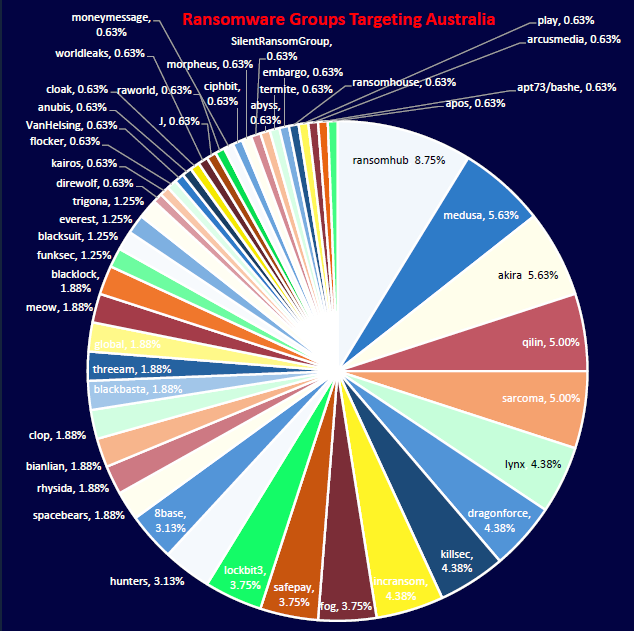
CYFIRMA observed a highly fragmented ransomware threat landscape in Australia, with over 40 active groups. RansomHub leads at 8.75%, followed by Medusa, Akira, Qilin, and Sarcoma, each accounting for 5% or more of observed attacks. The wide distribution highlights a competitive and aggressive ransomware ecosystem, with both established and emerging groups actively targeting Australian entities across sectors. This diversity reflects the increasing use of Ransomware-as-a-Service (RaaS) models, making attacks easier to launch and harder to predict. Organizations should view ransomware as a persistent business risk requiring proactive board-level governance and sector-specific threat mitigation.
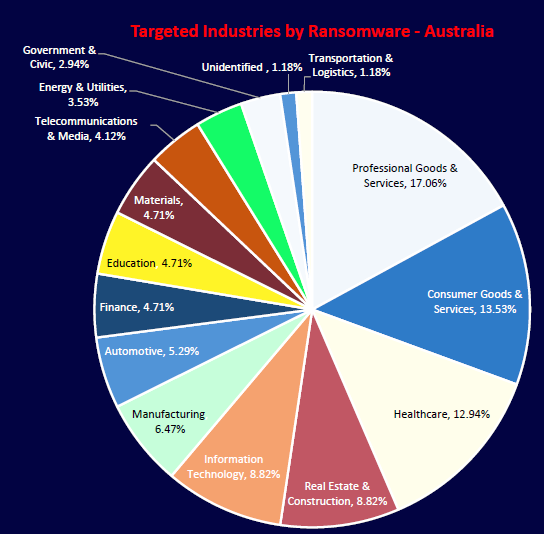
CYFIRMA observed ransomware groups targeting a wide spectrum of industries in Australia, with Professional Services (17.06%), Consumer Goods (13.53%), and Healthcare (12.94%) among the most affected. Critical sectors like IT, Manufacturing, and Real Estate also faced significant attacks. This wide distribution highlights the opportunistic and financially driven nature of ransomware operations, with no sector immune.
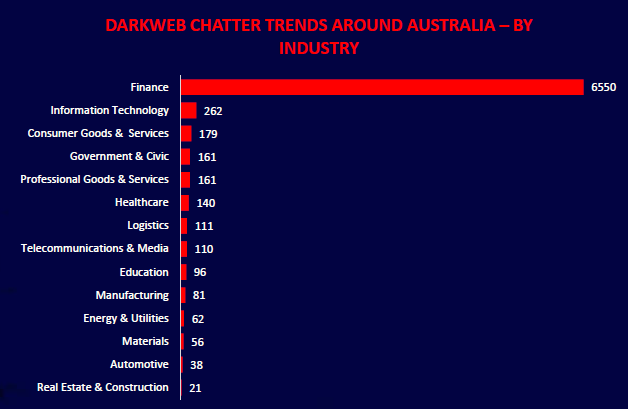
Darkweb Chatter Trends
CYFIRMA observed an overwhelming concentration of darkweb chatter related to Australia’s finance sector, accounting for over 6,500 mentions in the past six months, far surpassing all other industries. This signals heightened threat actor interest in financial data, fraud opportunities, and potential extortion. Information Technology, Consumer Goods, Government, and Healthcare also saw notable chatter, indicating broader multi-sector targeting and reconnaissance by cybercriminal ecosystems.
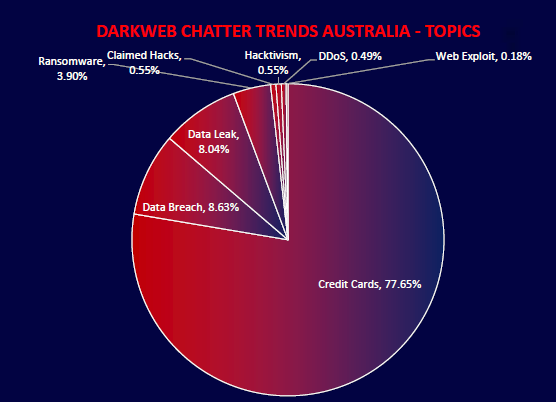
CYFIRMA observed that 77.65% of dark web chatter related to Australia over the past six months focused on stolen credit card data, highlighting the country’s high exposure to financial fraud. Data breaches (8.63%) and leaks (8.04%) were also prominent, reflecting active compromise and trade of sensitive information. Ransomware, while less frequent in chatter (3.9%), remains a persistent threat vector. The data emphasizes a financially driven threat landscape with a clear focus on monetizable assets.
The vulnerabilities exploited in Australia since January 1, 2025, reflect a strategic focus by threat actors, particularly ransomware groups, on widely deployed enterprise software and internet-facing devices. CYFIRMA observed that at least 10 of these exploited vulnerabilities are actively leveraged by ransomware operators, including flaws in Microsoft Exchange (CVE-2021-26855, CVE-2021-34473), dotCMS (CVE-2022-26352), Atlassian Crowd (CVE-2019-11580), and Check Point firewalls (CVE-2024-24919). Most CVEs listed are part of CISA’s Known Exploited Vulnerabilities (KEV) catalog, underscoring their real-world exploitation and urgency. The consistent targeting of outdated routers, CMS platforms, and remote infrastructure reveals a hybrid tactic combining opportunistic exploitation of unpatched systems with targeted attacks on core business applications, enabling both initial access and lateral movement. This trend highlights a sustained effort by threat actors to exploit systemic weaknesses in Australia’s digital ecosystem.