


In May 2025, a set of critical zero-day vulnerabilities was disclosed in Versa Concerto, a popular SD-WAN and SASE solution used across enterprises for secure cloud and network operations. Among them, CVE-2025-34027 stands out due to its severity and exploitability. The flaw stems from a path-based authentication bypass vulnerability in Concerto’s orchestration platform RESTful API, which allows unauthenticated attackers to gain administrative access and execute arbitrary commands remotely.
The vulnerability enables improper access control enforcement in API endpoints, where authentication mechanisms can be trivially bypassed by manipulating the request path. This can give threat actors direct access to sensitive functions that typically require administrator-level privileges. Moreover, CVE-2025-34027 is part of a broader cluster of unpatched issues (including CVE-2025-34025 and CVE-2025-34026), raising red flags about the overall security posture of the platform.
CYFIRMA Research has studied CVE-2025-34027 as a critical, unpatched zero-day vulnerability in Versa Concerto’s RESTful API, enabling authentication bypass and remote code execution. Exploited actively in the wild, the flaw may allow unauthenticated attackers to craft malicious API requests and gain unauthorized admin access to orchestrator instances. The vulnerability results from improper path validation in the API, and when chained with other known CVEs (CVE-2025-34025/34026), it escalates risk significantly.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers, cybersecurity vendors, and the open-source community in identifying, analyzing, and mitigating the CVE-2025-34027 vulnerability. Their contributions have been instrumental in raising awareness and ensuring timely security patches to protect organizations from potential exploitation.
CVE-2025-34027 is a critical authentication bypass vulnerability in Versa Concerto, affecting its orchestration platform’s REST API endpoints. The vulnerability arises from improper path handling, where attackers can bypass login requirements by appending crafted paths to specific API routes. This allows unauthenticated users to access functions intended only for administrators, including configuration changes, system management, and potentially remote command execution.
The vulnerability can be exploited without any valid credentials, making it ideal for external attackers. By chaining the vulnerability with other known flaws (such as CVE-2025-34025 and CVE-2025-34026), an attacker can pivot from initial access to full compromise of the network orchestrator. The flaw is considered highly dangerous due to the critical role of the Versa Concerto platform in managing SD-WAN/SASE networks. It also lacks robust logging and alerting mechanisms for such unauthorized API calls, making detection difficult.
Is there an exploit tool available for this vulnerability?
As of now, there is no confirmed information about the availability of publicly released exploit tools specifically targeting CVE-2025-34027. While some testing templates (e.g., for security scanners) may exist, it remains unclear whether these are capable of full exploitation or are intended solely for detection purposes.
Has this vulnerability been actively exploited in the wild?
There are currently no definitive confirmations of in-the-wild exploitation of CVE-2025-34027. However, given the nature of the vulnerability and the sensitivity of affected systems, security teams are advised to remain vigilant and monitor for potential signs of abuse, particularly in environments where Versa Concerto orchestrators are publicly exposed.
Are there discussions about this vulnerability on the deep and dark web?
At this stage, no direct evidence has emerged of widespread dark web activity explicitly referencing CVE-2025-34027. Similar network appliance vulnerabilities have historically attracted underground attention, and it is possible that exploratory discussions or private exchange of techniques could surface as awareness of the issue increases.
What is the attack complexity level?
Based on publicly available information, the attack surface appears to involve exposed management APIs and potentially unauthenticated request flows. However, the exact conditions required for successful exploitation—including network posture, configurations, and affected firmware versions—are still being evaluated. A detailed assessment of the exploitation complexity is pending further analysis.
Historical trends and exploitation risk
While no mass exploitation of CVE-2025-34027 has been observed, past incidents involving similar authentication bypass flaws in orchestration and network management appliances (e.g., Fortinet, Pulse Secure, Palo Alto) have shown that such vulnerabilities can escalate quickly once technical details become widespread. Proactive patching, network segmentation, and access restrictions are recommended until more is known.
CYFIRMA Recommendation
Organizations should urgently apply available patches and restrict external access to Versa Concerto management interfaces. Until a full patch is deployed, isolating vulnerable assets, enabling strict firewall rules, and monitoring for anomalous API activity are strongly recommended. Proactive threat hunting should be conducted to identify any indicators of compromise associated with known attack behaviors.
This vulnerability stems from a flawed implementation of URI decoding and filtering logic in Versa Concerto’s Spring Boot-based web interface. The authentication filter performs full URL decoding using URLDecoder.decode(), assuming that encoded characters (such as %2f) should be normalized. This allows the attacker to craft path-equivalent strings that match “safe” endpoints and bypass authentication mechanisms.
Consider the following logic observed in vulnerable filters:

In this case, a request like:

This will bypass authentication, because decodedUri becomes /portalapi/v1/users/admin;/v1/ping, which matches the whitelisted /v1/ping.
However, the dispatcher routing component in Spring does not decode the URI again.
It still sees:

Due to this inconsistency, the request is routed to the internal sensitive path /v1/users/admin, allowing the attacker to interact with privileged admin APIs without authentication.
Remote Code Execution (Chained via Upload API)
After bypassing authentication, an attacker can escalate the attack by targeting the package upload interface:
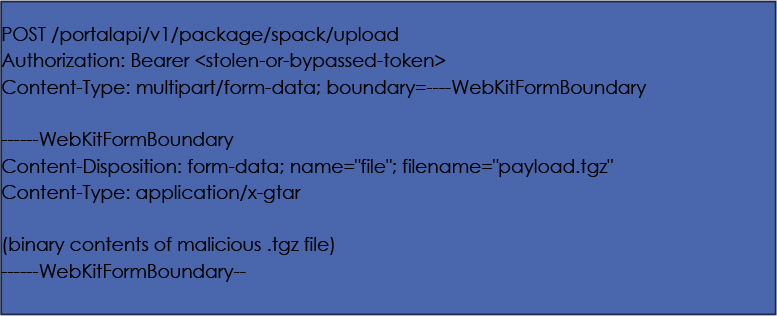
The .tgz file can contain path traversal payloads such as:

When extracted, this file writes to a controlled location on the disk. If the upload handler or a scheduled task runs scripts in these paths (e.g., post-install hook), the shell can be triggered, achieving unauthenticated RCE.
Malicious .tgz archive structure:

Example payload inside reverse.sh:

Once deployed, if any scheduled process or misconfigured path executes files under /tmp, the attacker gains a reverse shell.
While an official patch for CVE-2025-34027 is pending from Versa Networks, immediate mitigations are strongly recommended. Organizations should restrict API access using network segmentation and limit external exposure of the orchestration platform. Implementing IP allowlists, WAF rules, and custom API request validation can help block unauthorized access attempts. Monitoring API logs for unusual request patterns, especially those using non-standard paths, is essential. Disable unused API functions temporarily and rotate admin credentials. Enterprises should also deploy endpoint detection tools near Versa assets to catch lateral movement. Security teams are advised to follow Versa’s PSIRT updates and subscribe to real-time threat feeds. Where possible, isolate vulnerable Concerto instances from production environments and prioritize manual review of all recent configuration or administrative changes. CYFIRMA also recommends simulating this vulnerability in test environments to assess internal exposure and build proactive response playbooks until an official patch is released.
Target Geography
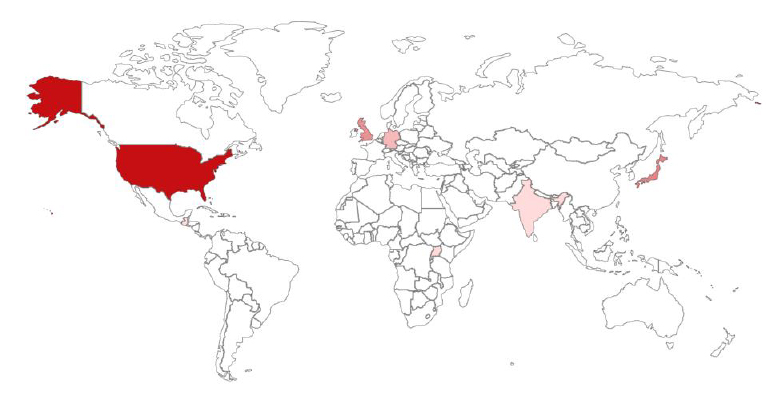
CVE-2025-34027 presents a global security threat, with confirmed exploitation incidents spanning the United States, Europe, Japan, and Asia-Pacific. As Versa Concerto is widely deployed by multinational telecommunications providers, managed security service providers (MSSPs), and large enterprises, the exposure risk is not limited to any single region. The orchestration platform’s global reach in software-defined WAN (SD-WAN) and Secure Access Service Edge (SASE) infrastructures makes this vulnerability highly relevant across both developed and emerging cybersecurity markets.
Target Industry
This vulnerability poses a significant threat to sectors where Versa Concerto is integral to secure network management and orchestration. High-risk industries include:
Given the criticality of network orchestration in these sectors, successful exploitation could result in unauthorized access, data exfiltration, service disruptions, and lateral movement across enterprise networks.
Target Technology
CVE-2025-34027 impacts the Versa Concerto Orchestration Platform, specifically its REST API authentication logic. By exploiting path equivalence inconsistencies, unauthenticated attackers can invoke privileged API endpoints. As the orchestration interface controls core security functions, including VPNs, traffic policies, and device management, the compromise of this component poses a systemic risk to the broader Versa deployment.
Systems exposed to the internet lacking strict access controls or API path validation, are especially vulnerable, particularly in hybrid cloud or multi-tenant network architectures.
The case of CVE-2025-34027 highlights the severe consequences of flawed authentication mechanisms in critical network orchestration platforms. This vulnerability emphasizes the importance of securing API endpoints and validating all access paths within enterprise software, particularly those managing infrastructure such as SD-WAN and SASE. Failure to enforce consistent authentication checks across API routes creates a dangerous entry point for attackers to bypass controls and execute unauthorized operations.
This incident highlights the growing need for organizations to adopt a security-by-design approach, prioritize software supply chain assessments, and implement robust API governance. As attackers increasingly target control-plane interfaces and automation tools, proactive measures—including vendor risk evaluations, external threat surface management, and timely application of patches—are essential to reduce the likelihood of compromise and limit exposure to high-impact vulnerabilities.