Published On : 2025-05-15
APT36, also known as Transparent Tribe, is a Pakistan-based advanced persistent threat (APT) group active since at least 2013. The group is widely attributed to Pakistani state interests and is primarily focused on cyber espionage against the Indian government organizations, military, defense contractors, research centers, diplomats, and critical infrastructure. APT36 is also known by aliases such as Project M, Mythic Leopard, Earth Karkaddan, and others
Alias: APT-C-56, Mythic Leopard, ProjectM, SideCopy, Storm-0156, TEMP.Lapis
Motivation: Espionage, Information Theft
Target Technologies: Office Suites Software, Operating System, Web Application
Targets

Targeted Countries
Primary Target: India

Secondary Targets and opportunistic interest: Afghanistan, Sri Lanka, Australia, Austria, Azerbaijan, Belgium, Botswana, Bulgaria, Canada, China, Czech Republic, Germany, Iran, Japan, Kazakhstan, Kenya, Malaysia, Mongolia, Nepal, Netherlands, Oman, Pakistan, Romania, Saudi Arabia, Spain, Sweden, Thailand, Turkey, the United Arab Emirates (UAE), the United Kingdom (UK), and the United States (USA).
Tools Used by APT 36:
SilentCMD, Amphibeon, beendoor, UPDATESEE, Mobzsar , Stealth Mango, USBWorm, MumbaiDown, DarkComet
Malware used by APT 36:
Luminosity RAT, Andromeda, Breach RAT, Android RAT, Dark Comet RAT, Oblique RAT, NJRat, Limepad, Mobzsar, ApoloStealer, Beendoor RAT, Peppy, Quasar RAT, Crimson RAT, Bezigate, Waizsar RAT, Bozok, CapraRAT
MITRE ATT&CK Techniques used by APT 36
| Resource Development |
Execution |
| T1608.004 |
T1203 |
| T1584.001 |
T1204.001 |
| T1583.001 |
T1204.002 |
|
T1059.005 |
| Initial Access |
|
| T1189 |
Defense Evasion |
| T1566.001 |
T1027 |
| T1566.002 |
T1036.005 |
|
T1564.001 |
|
Command and Control |
|
T1568 |
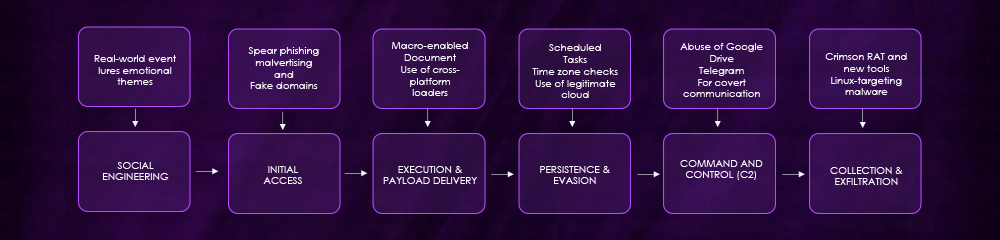
ATTACK FLOW DAIGRAM OF APT 36
APT 36’s Recent Campaign Highlights and Trends
Campaign Highlights
- Pahalgam Terror Attack-Themed Phishing:
APT36 leveraged the April 22, 2025, Pahalgam terror attack as a lure, distributing phishing PDFs and macro-laced documents to the Indian government and defense personnel. The campaign used fake domains impersonating the Jammu & Kashmir Police and Indian Air Force, created soon after the real-world event, to harvest credentials and deploy Crimson RAT for full remote access and data exfiltration.
- Kavach MFA Malvertising and Credential Harvesting:
The group abused Google Ads to promote malicious domains mimicking India’s official Kavach multi-factor authentication portal. These sites distributed backdoored Kavach apps, enabling APT36 to steal government employee credentials and deploy malware, such as Crimson RAT and the newly discovered Limepad exfiltration tool.
- Targeting the Indian Education Sector:
APT36 expanded its focus to include Indian educational institutions and students, distributing malicious Office documents with embedded OLE objects to stage Crimson RAT infections. This marks a shift from exclusive targeting of government and military personnel to a broader set of Indian critical sectors.
- Cross-Platform and All-in-One Espionage Tools:
The group has adopted cross-platform programming languages (Python, Golang, Rust) to develop tools that can target both Windows and Linux systems. Notably, a new Golang-compiled espionage tool was observed, capable of file exfiltration, screenshot capture, and remote command execution.
Trends
- Strategic Use of Real-World Events and Social Engineering:
APT36 consistently exploits current events (e.g., terror attacks, geopolitical tensions) and emotional themes (like the Kashmir conflict) to increase the success rate of phishing and lure documents.
- Abuse of Legitimate Web Services:
The group increasingly leverages popular cloud and messaging platforms (Google Drive, Telegram, Discord, Slack) for command-and-control (C2) and data exfiltration, making detection and blocking more difficult.
- Advanced Malvertising and Domain Impersonation:
APT36 has refined its use of malvertising, registering domains closely resembling official Indian government sites and using paid search ads to drive targeted traffic.
- Toolset Evolution and Diversification:
The group’s malware arsenal has expanded to include new tools (e.g., Limepad, ElizaRAT, Poseidon for Linux) and updated versions of Crimson RAT, with enhanced evasion and persistence features.
- Broadened Targeting:
While government and defense remain primary targets, APT36 is now also targeting educational institutions, research centers, and critical infrastructure in India.
Tactics, Techniques, and Procedures (TTPs)
Spear phishing (including ClickFix), Vulnerabilities & exploits, Malware implant
Initial Access
- Spear phishing emails with malicious attachments (PDFs, Office docs, PPAM files, ISO images).
- Malvertising campaigns using Google Ads to distribute Trojanized software.
- Fake websites and domains impersonating Indian government services.
Execution & Payload Delivery
- Macro-enabled documents and OLE-embedded files to stage malware.
- Use of cross-platform loaders (Python, Golang, Rust) for broader compatibility.
- Binaries are often compiled with PyInstaller or packed in VHDX archives for stealth.
Persistence & Evasion
- Scheduled tasks, startup folder modifications, and logon scripts for persistence.
- Time zone checks to execute only on Indian systems, reducing exposure.
- Use of legitimate cloud and messaging services for C2 and data exfiltration.
Command and Control (C2)
- Abuse of Google Drive, Telegram, Discord, and Slack for covert communications and data theft.
Collection & Exfiltration
- Crimson RAT and new tools (Limepad, ElizaRAT) for screen capture, file theft, keystroke logging, and remote command execution.
- Linux-targeting malware (Poseidon) to compromise non-Windows environments6.
Social Engineering
- Themed lures based on current events, military topics, and academic interests.





