Published On : 2025-05-14
Group123 is a North Korean state-sponsored advanced persistent threat (APT) group active since at least 2012. It is also tracked under other names such as APT37, Reaper, and ScarCruft by various cybersecurity firms. The group is known for its cyber espionage campaigns primarily targeting South Korea, however since 2017 it has expanded its operations to Japan, Vietnam, the Middle East, and other regions.
Alias:
Cloud Dragon, InkySquid, APT37, ITG10, Reaper, Red Eyes, RedAnt, Ricochet Chollima, ScarCruft, TEMP.Reaper
Target Technologies:
Office Suites Software, Operating System, Web Application
Motivation:
Information Theft, Espionage
Targeted Regions:
East Asia, Southeast Asia, Middle East
Targeted Country:
South Korea, Japan, Vietnam, China, Russia, Nepal, India, Kuwait, Romania, Czechia, Poland, Middle East countries, and the United States

Targeted Industries:

Tools Used by Group123:
SLOWDRIFT, MS Office exploits, Konni, Oceansalt, HAPPYWORK, Freenki Loader, N1stAgent, KevDroid, PoohMilk Loader, WINERACK, KARAE, RUHAPPY, GELCAPSULE, Flash Exploits, RICECURRY, SOUNDWAVE, ZUMKONG, Nokki, Syscon, CARROTBALL, GreezeBackdoor, NavRAT, RokRat, CVE-2016-4117, DOGCALL, CARROTBAT, CORALDECK, POORAIM, MILKDROP, SHUTTERSPEED, Final1stSpy, ScarCruft, Erebus
Malware used by Group123:
KARAE, HAPPYWORK, PoohMilk Loader, Oceansalt, BLUELIGHT, WINERACK, CORALDECK, Chinotto, RokRat, SHUTTERSPEED, Konni, Erebus, GreezeBackdoor, Final1stSpy, Syscon, N1stAgent, Nokki, SOUNDWAVE, GELCAPSULE, ScarCruft, RUHAPPY, ROKRAT, POORAIM, KevDroid, KoSpy, CARROTBALL, NavRAT, Freenki Loader, DOGCALL, SLOWDRIFT, M2RAT, CARROTBAT, ZUMKONG, Final1stspy, RICECURRY, MILKDROP
Recently Exploited Vulnerabilities by Group123
- CVE-2018-4878
- CVE-2022-41128
ATTACK FLOW DIAGRAM OF APT GROUP123
MITRE ATT&CK Techniques used by Group123
| Initial Access |
Privilege Escalation |
Discovery |
| T1189 |
T1548.002 |
T1057 |
| T1566.001 |
T1055 |
T1033 |
|
T1053.005 |
T1120 |
| Execution |
T1547.001 |
T1082 |
| T1059 |
|
|
| T1203 |
Defense Evasion |
Collection |
| T1053.005 |
T1548.002 |
T1005 |
| T1059.003 |
T1027 |
T1123 |
| T1059.006 |
T1055 |
|
| T1204.002 |
T1027.003 |
Command and Control |
| T1559.002 |
T1036.001 |
T1071.001 |
| T1059.005 |
|
T1102.002 |
| T1106 |
Credential Access |
T1094 |
|
T1555.003 |
T1105 |
| Persistence |
|
|
| T1053.005 |
|
Impact |
| T1547.001 |
|
T1561.002 |
|
|
T1529 |
Group123’s Recent Campaign Highlights and Trends
Recent reporting indicates Group123 continues to engage in persistent global espionage campaigns.
Key highlights and trends observed:
- Continued Espionage Focus: The group maintains a strong focus on collecting intelligence from sectors critical to defense, aerospace, nuclear technology and engineering. This aligns with their long-standing goal of acquiring beneficial information for North Korea’s strategic programs.
- Ransomware for Funding: A notable trend is the continued use of ransomware attacks, such as those leveraging Maui ransomware, to generate illicit revenue. This financial motivation appears to directly support their broader espionage activities, blurring the lines between state-sponsored espionage and cybercrime.
- Expanding Scope and Sophistication: Group123 and North Korean APTs in general (often linked or sharing TTPs) are assessed to be increasing the sophistication and scope of their operations. This includes developing and utilizing more advanced malware and employing techniques designed to enhance stealth and persistence.
- Adaptation of Techniques: The group demonstrates an ability to quickly incorporate newly disclosed vulnerabilities (including zero-days) into their operations. They also adapt their techniques, for instance, by leveraging legitimate services for command and control (C2) and employing sophisticated evasion tactics.
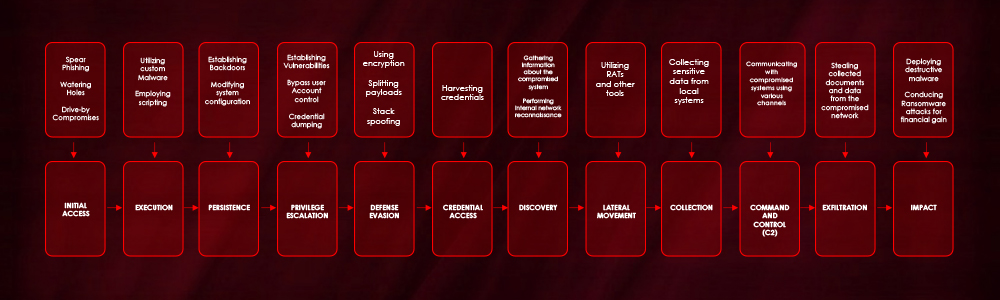
Tactics, Techniques, and Procedures (TTPs):
Group123 employs a diverse set of TTPs throughout the attack lifecycle. These include:
Initial Access:
- Spear Phishing: A primary method involves highly targeted spear phishing emails, often containing malicious attachments. These documents commonly exploit vulnerabilities in word processors popular in South Korea (like Hangul Word Processor – HWP) and Microsoft Office. The lures are often socially engineered and relevant to the victim’s interests or profession.
- Exploitation of Public-Facing Applications: They actively exploit known vulnerabilities in web servers and other internet-facing applications (such as Log4j, and various older CVEs) to gain initial access or establish web shells.
- Strategic Web Compromises (Watering Holes): Compromising legitimate websites likely visited by their targets and using them to serve malicious content or exploits.
- Drive-by Compromises: Exploiting vulnerabilities in web browsers or plugins when users visit malicious or compromised websites.
Execution:
- Utilizing custom malware (e.g., ROKRAT, PoohMilk, Freenki) and commodity malware.
- Employing scripting and leveraging Windows API calls for executing malicious code.
Persistence:
- Establishing backdoors for continued access.
- Modifying system configurations, such as adding entries to Registry Run Keys/Startup Folders.
Privilege Escalation:
- Exploiting vulnerabilities in the operating system or applications.
- Attempting to bypass User Account Control (UAC).
- Credential dumping and password cracking to gain higher-level access.
Defense Evasion:
- Using encryption, particularly HTTPS, for C2 communications to blend in with normal traffic.
- Splitting payloads into multiple stages to complicate analysis.
- Utilizing compromised legitimate web servers or cloud-based platforms for C2 infrastructure.
- Implementing checks for the presence of security and analysis tools.
- Employing techniques like DLL sideloading, DLL hollowing, and call stack spoofing.
Credential Access:
- Harvesting credentials from web browsers and the Windows Credential Manager.
Discovery:
- Gathering information about the compromised system, including computer name, username, execution path, and BIOS model.
- Performing internal network reconnaissance to identify other valuable targets and map the network.
Lateral Movement:
- Utilizing their RATs and other tools to move deeper into the network from the initial point of compromise.
Collection:
- Collecting sensitive data from local systems.
- Employing tools for specific data collection, such as audio capturing utilities.
Command and Control (C2):
- Communicating with compromised systems using various channels, historically including platforms like X, Yandex, and Mediafire and more recently potentially leveraging services like Google Drive.
- Utilizing compromised web servers as C2 points.
Exfiltration:
- Stealing collected documents and data from the compromised network. This often involves staging data before exfiltration.
Impact:
- Deploying destructive malware, such as disk wipers, in some operations.
- Conducting ransomware attacks for financial gain.





