


April 2025 witnessed a decline in ransomware incidents, with 470 reported victims worldwide. Qilin remained the dominant group, while newer actors like Silent, Crypto24, Bert, and Gunra made their presence felt. The Manufacturing sector continued to be the primary target, followed by significant impacts on the IT industry. The USA sustained its position as the most targeted region. This report delves into key ransomware trends, emphasizing the growing sophistication of threat actors and their expanding focus on global regions, highlighting the urgent need for enhanced cybersecurity measures.
The ransomware landscape in April 2025 showed a decline, yet the frequency and complexity of attacks remained consistent. This report provides a comprehensive analysis of ransomware activity, comparing trends from previous months. It highlights the most affected industries, regions, and the emergence of new ransomware groups. Additionally, the report examines the evolving tactics of prominent threat actors, offering insights into the shifting cyber threat landscape.
Throughout April 2025, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
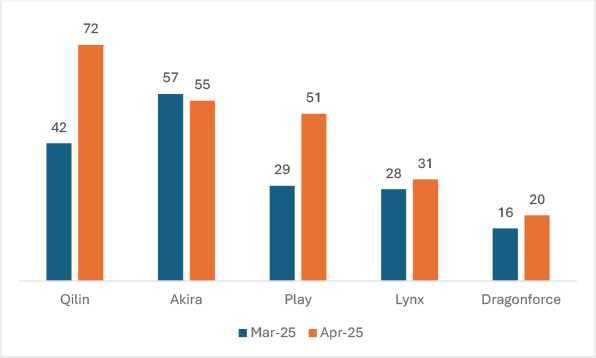
In April 2025, Qilin demonstrated the most significant surge among the top ransomware groups, recording a 71.4% increase in activity compared to March. Play also saw a notable escalation, with a 75.9% rise, indicating a strong upward momentum. Dragonforce showed moderate growth of 25%, while Lynx increased slightly by 10.7%. On the other hand, Akira was the only group that recorded a decline, albeit marginal, with a 3.5% drop in activity. This overall trend highlights a growing threat landscape led by Qilin and Play, demanding heightened vigilance from enterprises.
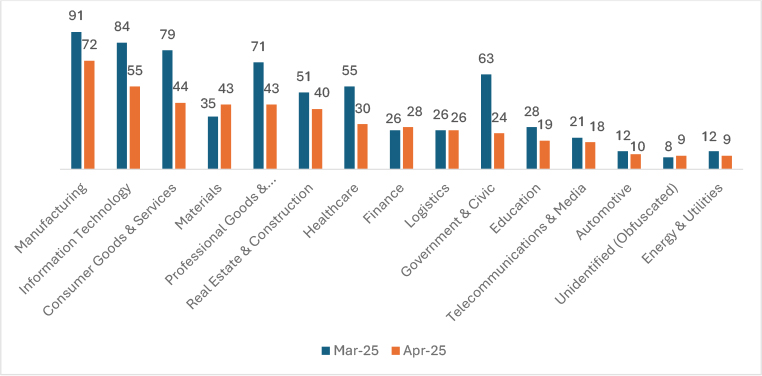
In April 2025, ransomware incidents declined in most sectors. Manufacturing fell by 21%, Information Technology by 34.5%, and Consumer Goods & Services by 44.3%. Materials rose by 22.9%, Professional Goods & Services by 39%, and Real Estate & Construction by 22%. Healthcare saw a 45% reduction, Finance increased by 7%, and Education incidents fell by 32%. Telecommunications & Media declined 14%, while Automotive dropped 16%, and Energy & Utilities dropped by 25%. Government & Civic suffered the steepest contraction, a 62% plunge, reflecting a shifting threat focus across industries.
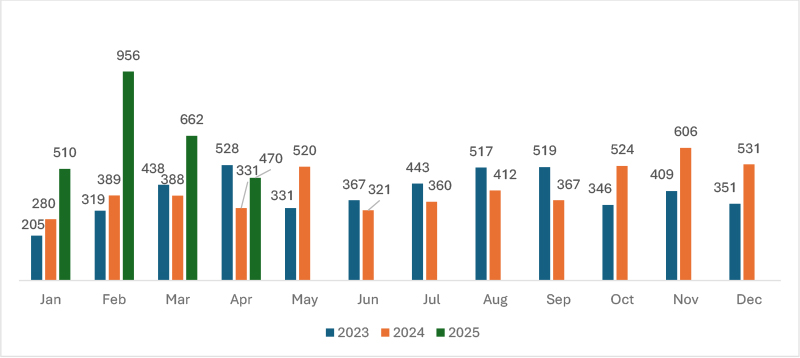
Ransomware activity declined significantly in April 2025, with a 29% drop compared to March. After a peak in February, March marked a partial cooldown, which continued into April. Despite this dip, early 2025 still shows higher attack volumes than previous years. The year began with aggressive spikes, suggesting heightened threat actor operations, although the sustained pace may now be gradually tapering off.
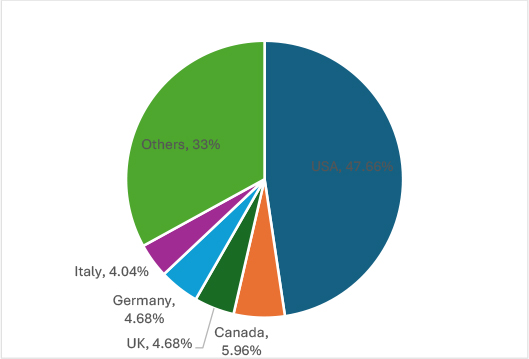
The data reveals that ransomware attacks in April 2025 were heavily concentrated in the United States (224), followed by Canada (28), the United Kingdom (22), Germany (22), and Italy (19). These regions are prime targets due to their strong economies, data-rich enterprises, critical infrastructure, and high ransom-paying potential, making them lucrative for cybercriminals.
FOG is being widely distributed by cybercriminals
FOG ransomware has resurfaced through a campaign leveraging a ZIP archive named “Pay Adjustment.zip”, containing a malicious LNK file. Distributed via phishing emails, the LNK executes a PowerShell script (“stage1.ps1”) that downloads a ransomware loader (cwiper.exe), a privilege escalation tool (ktool.exe), and data-harvesting scripts. The scripts (lootsubmit.ps1, trackerjacker.ps1) gather system details, MAC address, and geolocation via Wigle API, exfiltrating data to a Netlify-hosted server. Ktool.exe exploits a known vulnerability in iQVW64.sys to escalate privileges.
The ransomware checks for virtualized environments via system indicators before execution. Once validated, it decrypts and executes the embedded FOG ransomware binary, drops a ransom note (readme.txt), and creates a log file (dbgLog.sys). Victims’ files are encrypted with the “.flocked” extension. The ransom note contains politically themed messaging and instructs victims to propagate the malware further. A QR code redirects to a Monero wallet address.
FOG ransomware has targeted over 100 victims across sectors including technology, education, manufacturing, and transportation. Threat actors may be impersonating or trolling a government initiative named DOGE, embedding social engineering into their notes. Variants differ only in the encryption key used to decrypt the payload embedded within each loader.
ETLM Assessment:
FOG ransomware is likely to evolve with enhanced sandbox evasion, refined privilege escalation methods, and broader phishing lures. Its incorporation of political themes and impersonation tactics suggests future variants may intensify social engineering. With the growing cloud and virtual environment targeting, FOG may expand payload delivery through trusted services or compromised third parties, making it more persistent and evasive across enterprise networks.
Interlock Ransomware Group Exploits Fake IT Utilities in Sophisticated ClickFix Attacks
The Interlock ransomware group has adopted ClickFix attacks to deliver malware by impersonating legitimate IT tools. These attacks lure victims into executing malicious PowerShell commands under the guise of resolving system errors or verifying their identity. Once executed, the command downloads a 36MB PyInstaller payload that installs both a legitimate IT tool and a malicious script. This script achieves persistence by modifying the Windows Registry, collecting system information, and exfiltrating data, such as OS details, user privileges, and active processes.
Malicious URLs mimic trusted domains, including IP scanning and Microsoft-related sites, to deceive users. After initial access, the group deploys a range of malware, including LummaStealer, BerserkStealer, keyloggers, and the Interlock RAT—a lightweight backdoor supporting file exfiltration, command execution, and DLL loading.
Lateral movement is enabled via stolen credentials and remote access tools like PuTTY, AnyDesk, and LogMeIn. Stolen data is exfiltrated to attacker-controlled Azure Blob storage. The ransomware payload, primarily targeting Windows and FreeBSD systems, is scheduled to execute daily at 8:00 PM, using file extension filtering to avoid redundant encryption.
The ransom note has evolved to emphasize legal and regulatory consequences, increasing psychological pressure on victims. Interlock is not a ransomware-as-a-service operation but maintains a public data leak site to intensify extortion.
ETLM Assessment:
Interlock is expected to expand its use of social engineering vectors like ClickFix, combining them with impersonation of widely-used IT tools. Future iterations may include modular payloads with AI-assisted reconnaissance and enhanced RAT capabilities. The group may diversify initial access methods and exploit emerging remote access software trends, targeting broader enterprise environments. Greater emphasis on legal threats in ransom notes suggests a psychological pivot to maximize compliance through fear of regulatory fallout.
A New variant of Mimic has been seen targeting the victims aggressively
The ELENOR-corp ransomware is a rebranded variant of Mimic ransomware v7.5, primarily targeting the healthcare sector. Initial access was achieved through the deployment of Clipper malware to harvest credentials. After foothold establishment, attackers escalated privileges using Mimikatz and performed network reconnaissance with NetScan. For persistence, they deployed NSSM to configure malicious services. The payload, named 1ELENOR-corp.exe, was responsible for extracting multiple encrypted modules and configuration files into hidden directories, later executed via scheduled tasks. Tools like Process Hacker and PEView were abused to disable security controls and aid system exploration. Data exfiltration was achieved using Microsoft Edge sessions connecting to Mega.nz storage. Encryption routines began after thorough network mapping, focusing on high-value systems, including domain controllers. The ransomware’s structure and tactics, such as modular payload staging, layered obfuscation, and stealthy data exfiltration, highlight a shift towards long-term, stealthy intrusions rather than rapid smash-and-grab attacks. The operators demonstrated patience, carefully setting up their infrastructure before detonating the final payload. ELENOR-corp reflects the growing sophistication of threat actors who blend commodity malware with custom tooling to maximize impact while evading detection.
ETLM Assessment:
Future ransomware attacks will likely continue adopting modular architectures and living-off-the-land techniques to blend into legitimate operations. Groups will increase their focus on stealthy credential harvesting and exfiltration prior to encryption. The healthcare and other critical sectors will remain a high-priority target due to its critical nature and vulnerability to operational disruption.
PipeMagic Trojan Leverages Windows Zero-Day Flaw to Launch Ransomware Attacks
A recently patched flaw in Windows CLFS (CVE-2025-29824) was exploited as a zero-day by the threat group Storm-2460. The vulnerability allowed privilege escalation to the SYSTEM level by corrupting memory and overwriting process tokens. Attackers used the certutil tool to download a malicious MSBuild file hosting an encrypted payload, which unpacked the PipeMagic trojan. PipeMagic, a plugin-based malware active since 2022, was used to facilitate the exploit and deploy ransomware payloads. Although the initial access vector remains unknown, post-exploitation activities included credential theft via LSASS memory dumping and file encryption with random extensions. The ransom note contained a TOR link tied to the RansomEXX ransomware family. This activity marks PipeMagic’s involvement in exploiting multiple CLFS-related vulnerabilities, including CVE-2025-24983 and CVE-2023-28252, often leading to Nokoyawa ransomware attacks. Systems running Windows 11 version 24H2 are unaffected due to enhanced privilege restrictions. The exploitation chain highlights the importance of privilege escalation for ransomware operators seeking widespread system compromise and lateral movement.
ETLM Assessment:
Given Storm-2460’s continued exploitation of CLFS vulnerabilities and their use of advanced post-exploitation tools like PipeMagic, future attacks are likely to target unpatched or less secure environments aggressively. Modular trojans embedded within legitimate processes will increasingly support stealthy ransomware delivery, emphasizing the critical need for proactive patch management and privilege restriction enhancements.
DragonForce Launches White-Label Ransomware Cartel Model for Affiliate Expansion
DragonForce is restructuring the ransomware landscape by creating a cartel-like model, allowing multiple ransomware groups to operate under its infrastructure while maintaining independent branding. Affiliates use DragonForce’s negotiation tools, data leak platforms, and encryptors, avoiding the burden of infrastructure development. In return, DragonForce takes a 20% cut of ransom payments. The model supports attacks on ESXi, NAS, BSD, and Windows systems, offering flexibility for both sophisticated and less technical threat actors. DragonForce enforces strict rules on affiliates and claims to avoid attacking critical healthcare targets. Newly formed groups like RansomBay have already joined this model.
ETLM Assessment:
DragonForce’s cartel structure is likely to trigger a major shift in ransomware operations, lowering technical barriers and increasing the number of active threat groups. This could lead to a surge in smaller, independent ransomware brands while simultaneously making attribution and disruption efforts more challenging for defenders and law enforcement.
RaLord has been renamed to Nova
The ransomware group, initially known as RaLord, rebranded to Nova RaaS (Ransomware-as-a-Service) as of April 2025. This group operates a RaaS platform, allowing affiliates to launch attacks using their Rust-based ransomware payload. The malware encrypts files with the “.ralord” extension and creates ransom notes directing victims to contact the attackers via qTox IDs for negotiation. Notably, the group has publicly stated a policy of not targeting schools and nonprofit organizations, although earlier victims included such institutions, which have since been removed from their leak site. The Nova RaaS platform offers affiliates 85% of ransom proceeds, retaining 15% for the operators. The group continues to update its ransomware features and maintains an onion site detailing its operations and affiliate program.
ETLM Assessment:
Given Nova RaaS’s active development and affiliate recruitment, it’s likely the group will expand its operations, potentially increasing the sophistication of its ransomware and targeting a broader range of organizations. Despite their current policy of excluding schools and nonprofits, this stance may change as the group seeks higher profits. Organizations should remain vigilant, as the RaaS model lowers the barrier for launching attacks, potentially leading to a surge in ransomware incidents.
Silent
Silent is the new ransomware group that launched its leak site at the end of April 2025.
Unlike many other groups, Silent claims to operate with a high level of anonymity and discretion. According to their own statement, they avoid public negotiations and encrypt minimal data. Instead, their focus is on stealing valuable confidential corporate information — and either selling it to competitors, on the dark web, or publishing it selectively. During the time of writing of this report, the group has claimed 4 victims.
Gunra Ransomware:
CYFIRMA Research identified Gunra Ransomware recently. This ransomware encrypts victim files by appending a “.ENCRT” extension and drops a ransom note named “R3ADM3.txt.” The note claims both file encryption and theft of sensitive business data, demanding payment for decryption. Victims are given five days to respond, with the threat of data leakage on the dark web if ignored. To validate their offer, attackers allow the decryption of a few files for free. The note also warns against tampering with encrypted files, further emphasizing the threat of permanent data loss or exposure. During the writing of this report, the group has claimed 5 victims.
Crypto24
A new ransomware group named Crypto24 emerged in April 2025, claiming to have targeted eight victims worldwide.
Bert
Another group called Bert has surfaced by the beginning of April and has actively claimed 4 victims globally.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware presents a major threat to both organizations and individuals by encrypting vital data and demanding payment for its release. In addition to the ransom demand, these attacks result in significant financial costs associated with recovery efforts and enhanced cybersecurity measures. They also disrupt operations, damage reputations, and erode customer trust. Victims frequently face regulatory fines, reputational harm, and market instability, further diminishing consumer confidence. To protect financial stability and maintain public trust, it is essential for businesses and governments to adopt proactive strategies to combat ransomware threats.
Victimology
Cybercriminals are increasingly targeting businesses that manage significant amounts of sensitive data, such as personal information, financial records, and intellectual property. Sectors like manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology are particularly vulnerable due to their large data repositories. These attackers primarily focus on economically advanced nations with robust digital infrastructures, exploiting vulnerabilities to encrypt critical data and demand hefty ransoms. Their aim is to maximize financial gains through increasingly sophisticated and strategic methods.
The April 2025 ransomware activities saw a decline, yet consistency highlight the persistent evolution of cyber threats, with increased sophistication in attack methods. Key industries, including Manufacturing, IT, Healthcare, and others, remain at heightened risk. Organizations must prioritize robust cybersecurity measures, including regular patching, employee training, and incident response planning to mitigate risks. Strengthening defenses against ransomware is essential to safeguard operations, protect sensitive data, and ensure resilience against this escalating global cyber threat.
STRATEGIC RECOMMENDATIONS:
MANAGEMENT RECOMMENDATIONS:
TACTICAL RECOMMENDATIONS: