


At CYFIRMA, we are committed to delivering timely insights into emerging cyber threats and the evolving tactics of cybercriminals targeting individuals and organizations. This report provides a concise analysis of Gunra Ransomware, highlighting its techniques, impact, and potential risks.
Gunra ransomware targets various industries globally, including real estate, pharmaceuticals, and manufacturing. It employs a double-extortion technique by threatening to leak stolen data on its Tor-hosted extortion. The malware exhibits several malicious behaviours such as enumerating running processes, deleting shadow copies via Windows Management Instrumentation (WMI), and retrieving system information. Gunra’s sample exhibits capabilities to detect debuggers and enumerate files. Victims of this ransomware group include companies from Japan, Egypt, Panama, Italy, and Argentina. Organizations should bolster phishing defences, monitor internal movement, and ensure robust backup strategies.
Gunra Ransomware is a recently observed ransomware that primarily targets Windows systems and employs advanced encryption methods, along with exfiltration tactics to maximize its extortion potential.
| Target Technologies | Windows |
| Encrypted Files Extension | .ENCRT |
| Ransom Note File | R3ADM3.txt |
| Contact Mode | Tor-based negotiation portal |
| Based On | Conti Ransomware |
| Programming Language | C\C++ |
Gunra ransomware employs advanced evasion and anti-analysis techniques used to infect Windows Operating systems while minimizing the risk of detection. Its evasion capabilities include obfuscation of malicious activity, avoidance of rule-based detection systems, strong encryption methods, ransom demands, and warnings to publish data on underground forums.
Once Gunra ransomware infects a system, it encrypts files and appends a ‘.ENCRT’ extension to each filename. It also drops a ransom note file in every directory with the name “R3ADM3.txt”, providing victims with instructions for file recovery and ransom payment, with the likely motive of financial gains.
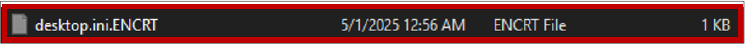
Basic Details
| Filename | gunraransome.exe |
| Size | 194.50 KB |
| Signed | Not signed |
| File Type | Win32 EXE |
| Timestamp | Thu Apr 10 11:27:24 2025 (UTC) |
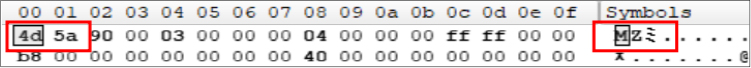
MZ Header: begins with the ASCII characters “MZ” (0x4D 0x5A). The signature is an executable file.
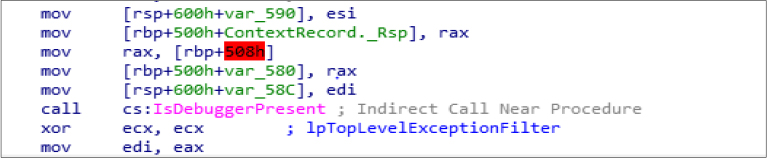
Anti-debugging & Anti-reversing: The Windows API function IsDebuggerPresent is used for anti-analysis and detects if it’s being run under a debugger (e.g., x64dbg, WinDbg, OllyDbg).
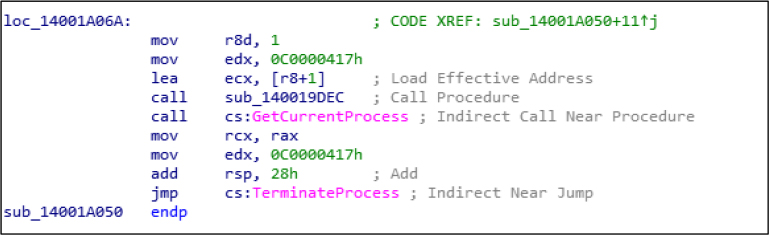
Detect Evasion: It uses GetCurrentProcess and TerminateProcess functions for process manipulation, privilege escalation, and anti-analysis. Attackers use this function to monitor and control the execution of their own process, privilege escalation, and inject malicious code into other processes and anti-malware tools.
Data Discovery: FindNextFileExW is used to search the files in the directory to enumerate targets with specific extensions such as .docx, .pdf, .xls, .jpg etc.
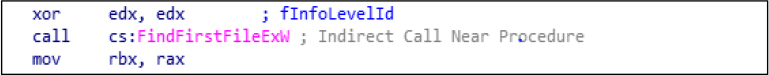
FileNextFilew: This is used to continue the file enumeration.
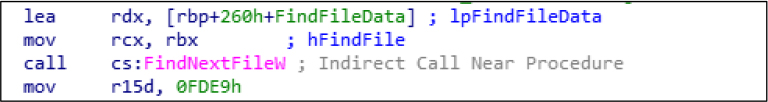
FileClose: This is used to release the handle from FindFirstFileExW.
1. It creates a process with the name ‘gunraransome.exe’ in ‘taskmgr’.
2. Deletes available shadow copies using the Windows Management Instrumentation (WMI) utility.
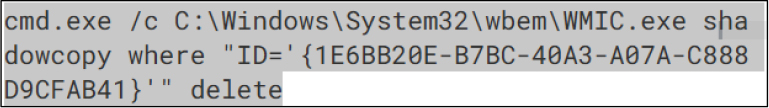
3. It encrypts the victim’s files and appends them with the extension “. ENCRT”.
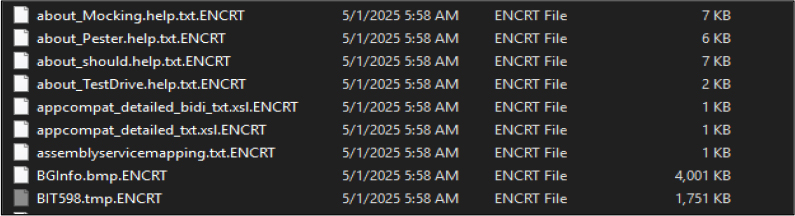
4. Drops a ransom note file named “R3ADM3.txt” in every directory where files are encrypted by the ransomware.
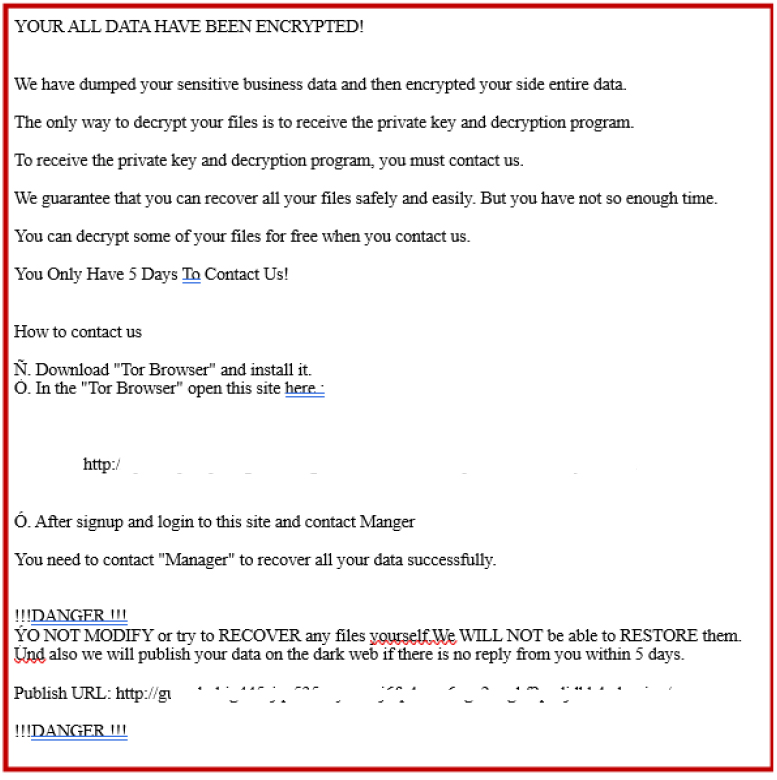
The ransom notes indicate that sensitive data has also been encrypted as well as exfiltrated. The attacker instructs the victim to contact them via a specified .onion site on the Tor network, giving a limited time of 5 days to initiate communication. The note includes standard coercive elements such as the promise of free decryption of some files, threats of permanent data loss if manual recovery is attempted, and the potential public release on underground forums of the stolen data if demands are not met.
The Gunra Ransomware Group emerged in April 2025 and has been identified as a financially motivated threat actor leveraging double extortion tactics encrypting victims’ data while also exfiltrating sensitive information to pressure payment.
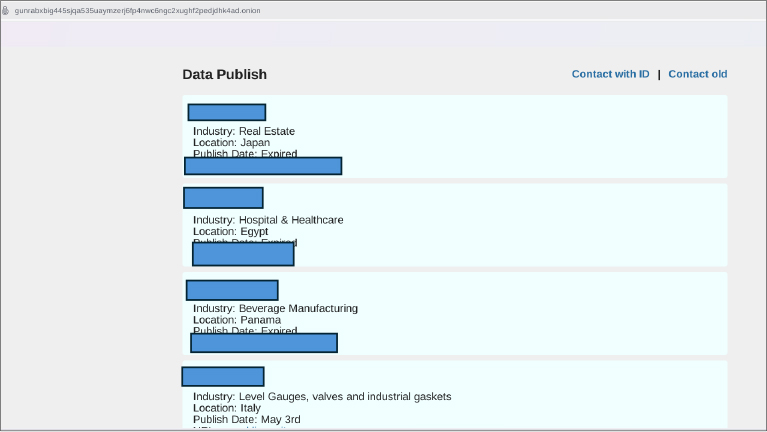
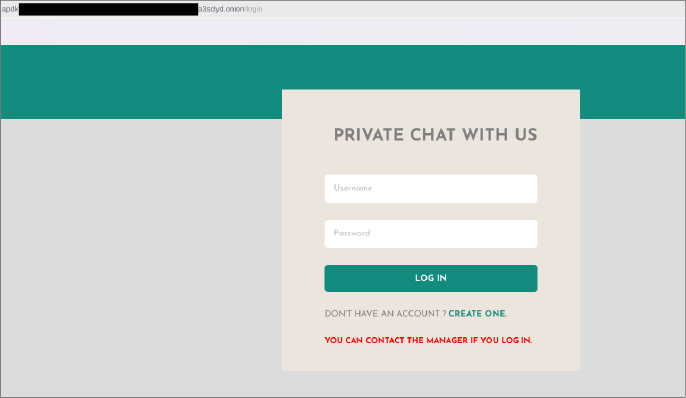
Victims are typically given a five-day deadline, and the group conducts negotiations via Tor-based portals styled similarly to messaging apps like WhatsApp, complete with assigned roles such as “Manager.”
| No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1047: Windows Management Instrumentation T1129: Shared Modules |
| 2 | Persistence (TA0003) | T1176: Software Extensions T1542: Pre-OS Boot T1542.003: Bootkit T1574: Hijack Execution Flow T1574.002: DLL Side-Loading |
| 3 | Privilege Escalation (TA0004) | T1055: Process Injection T1548: Abuse Elevation Control Mechanism T1574: Hijack Execution Flow T1574.002: DLL Side-Loading |
| 4 | Defense Evasion (TA0005) | T1014: Rootkit T1027: Obfuscated Files or Information T1027.002: Software Packing T1027.005: Indicator Removal from Tools T1036: Masquerading T1055: Process Injection T1143: Hidden Window T1542: Pre-OS Boot T1542.003: Bootkit T1548: Abuse Elevation Control Mechanism T1564: Hide Artifacts T1564.001: Hidden Files and Directories T1574: Hijack Execution Flow T1574.002: DLL Side-Loading |
| 5 | Credential Access (TA0006) | T1003: OS Credential Dumping T1081: Credentials in Files T1539: Steal Web Session Cookie T1552: Unsecured Credentials T1552.001: Credentials in Files T1555: Credentials from Password Stores T1555.003: Credentials from Web Browsers |
| 6 | Discovery (TA0007) | T1057: Process Discovery T1063: Security Software Discovery T1082: System Information Discovery T1083: File and Directory Discovery T1518: Software Discovery |
| 7 | Collection (TA0009) | T1005: Data from Local System T1119: Automated Collection T1185: Browsers Session Hijacking |
| 8 | Command-and-control (TA0011) | T1071: Applications Layer Protocol T1090: Proxy |
| 9 | Impact (TA0040) | T1486: Data Encrypted from Impact T1490: Inhibit System Recovery T1496: Resource Hijacking |
Gunra ransomware exemplifies the growing sophistication of threats within the cybersecurity landscape, showcasing advanced malicious behaviours aligned with modern ransomware campaigns. It begins by enumerating system processes and files and collecting system information through reconnaissance. The malware then deletes Volume Shadow Copies using WMI, effectively disabling system restore and backup capabilities to ensure the encryption is irreversible without external help. Using the IsDebuggerPresent API, it employs anti-analysis techniques to evade detection and hinder reverse engineering. It proceeds to terminate active processes, likely to unlock files for encryption, before encrypting victim data and appending a custom file extension. To deliver its demands, it drops a ransom note across multiple directories, signalling the completion of the attack and initiating the extortion phase. These coordinated actions confirm the malware’s purpose as ransomware, aimed at disrupting business operations and coercing the victim into paying a ransom for decryption.
Malware such as Gunra can infiltrate systems through ransomware attacks. Implementing the following mitigations recommended by CYFIRMA can help block its installation, prevent infiltration, and reduce the overall attack surface:
Enhance Endpoint Detection and Response (EDR):
Implement advanced EDR solutions that can detect abnormal behaviours such as:
Backup and Recovery Planning:
Ransomware Detection & Prevention:
Limit Administrative Privileges:
Network Isolation and Containment:
WMI and Process Monitoring:
File Integrity Monitoring (FIM):
Training and Awareness:
Immediate Incident Response Actions:
File Recovery and Restoration:
Forensics and Root Cause Analysis:
WMI Remediation:
Preventing Future Attacks:
Deploy EDR, SIEM, and Network Visibility:
Stay updated with CYFIRMA’s threat intelligence sharing platform to effectively detect emerging TTPs, enhance situational awareness, and enable timely mitigation of threats relevant to your industry and region.
| S.No | Indicator | Type |
| 1 | 9a7c0adedc4c68760e49274700218507 | MD-5 |
| 2 | 854e5f77f788bbbe6e224195e115c749172cd12302afca370d4f9e3d53d005fd | SHA-256 |
rule Gunra_Ransomware
{
meta:
description = “Detects Gunra Ransomware specific file hash”
author = “CYFIRMA Research”
date = “2025-05-02”
strings:
// SHA-256 and MD-5 hashes of files associated with Gunra Ransomware
$hash1= “854e5f77f788bbbe6e224195e115c749172cd12302afca370d4f9e3d53d005fd”
$hash2 = “9a7c0adedc4c68760e49274700218507”
condition:
// If any of the hashes are found, trigger the rule
any of ($hash*)
}