


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Jackalock Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Jackalock Ransomware
Jackalock is a newly discovered ransomware. This ransomware belongs to MedusaLocker ransomware family.
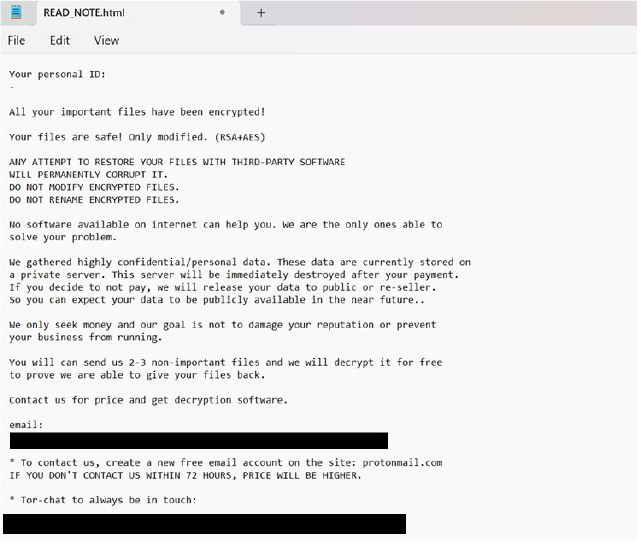
Upon execution, it encrypts files and appends the “.jackalock” extension to their names. After the encryption process is complete, Jackalock drops a ransom note in the form of an HTML file titled “READ_NOTE.html”.
The ransom message states that the victim’s files have been encrypted using RSA and AES cryptographic algorithms. It strongly warns victims not to modify the encrypted files or attempt recovery using third-party tools, as doing so could result in permanent data loss.
Additionally, the message reveals that confidential or personal data has been exfiltrated from the compromised system.
To recover their files, the victim is instructed to pay a ransom. Failure to comply will result in the leakage of the stolen data. Moreover, if the attackers are not contacted within 72 hours, the ransom amount (which is not disclosed in the note) will increase.
Before making any payment, victims are allowed to test the decryption process on 2–3 non- critical files as proof of functionality.
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion |
T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data reveals that MedusaLocker ransomware has been actively targeting multiple sectors—such as manufacturing, healthcare, finance, and IT services—since 2019. The recent emergence of Jackalock, a sophisticated variant of MedusaLocker, demonstrates the adoption of advanced evasion techniques aimed at expanding its reach across both individual users and enterprises. Given these developments, Jackalock is projected to remain a persistent global threat, particularly to critical industries, which highlights the pressing need for robust cybersecurity strategies to counter these evolving risks.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule
title: Suspicious Volume Shadow Copy VSS_PS.dll Load tags:
– attack.defense-evasion
– attack.impact
– attack.t1490 logsource:
category: image_load product: windows
detection: selection:
ImageLoaded|endswith: ‘\vss_ps.dll’ filter_legit:
Image|startswith: ‘C:\Windows\’ Image|endswith:
– ‘\clussvc.exe’
– ‘\dismhost.exe’
– ‘\dllhost.exe’
– ‘\inetsrv\appcmd.exe’
– ‘\inetsrv\iissetup.exe’
– ‘\msiexec.exe’
– ‘\rundll32.exe’
– ‘\searchindexer.exe’
– ‘\srtasks.exe’
– ‘\svchost.exe’
– ‘\System32\SystemPropertiesAdvanced.exe’
– ‘\taskhostw.exe’
– ‘\thor.exe’
– ‘\thor64.exe’
– ‘\tiworker.exe’
– ‘\vssvc.exe’
– ‘\WmiPrvSE.exe’
– ‘\wsmprovhost.exe’ filter_programfiles:
# When using this rule in your environment replace the “Program Files” folder by the exact applications you know use this. Examples would be software such as backup solutions
Image|startswith:
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_update:
CommandLine|startswith: ‘C:\$WinREAgent\Scratch\’ CommandLine|contains: ‘\dismhost.exe {‘
filter_image_null: Image: null
condition: selection and not 1 of filter_* falsepositives:
– Unknown level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Information Stealer
Objective: Data theft, Data Exfiltration
Threat Actor: Sapphire Werewolf
Target Technologies: Windows OS, Browsers (Chrome, Opera, Yandex, Brave, Orbitum, Atom, Kometa, Edge Chromium), FileZilla, VPN Clients, Remote Desktop Tools
Active Malware of the Week
This week “Amethyst Stealer” is trending.
Amethyst Stealer
Researchers discovered a new campaign involving an updated version of Amethyst Stealer, attributed to the threat actor Sapphire Werewolf. The campaign uses deceptive emails that appear to be HR department memos, with the malware delivered through compressed attachments containing a decoy PDF to distract the recipient. Once executed, Amethyst Stealer quietly harvests sensitive data from the infected system, including credentials, browser-stored information, configuration files, and documents from both internal and removable drives. This latest variant also includes enhanced evasion techniques, such as virtual environment detection and advanced encryption, highlighting a more refined and stealthy approach in the evolving campaign.
Attack Method
Initially, Sapphire Werewolf poses as an HR representative and sends a malicious attachment disguised as an official memo. This tactic is crafted to trick victims into opening the file, triggering the execution of the malware.
The attacker sends a compressed archive, disguised as an official memo, which contains an executable file disguised with a PDF icon. This is a C#-based malware, protected with .NET Reactor, that functions as a loader. Upon execution, it loads a Base64-encoded payload, which is a PE file, allowing the malware to carry out its malicious actions on the victim’s system.
Once the Base64 string is decoded, it is loaded into memory and executed using specific methods in the code. The resulting PE file is the Amethyst Stealer, also protected with .NET Reactor. This variant download malicious files into the memory of the DotNetZip.dll helper library for file compression. It then sends system data, such as the IP address and a string identifying whether the system is a virtual machine, to a specific address. The malware also communicates with several external servers, including one for IP verification, and uses its resources to execute a decoy PDF document, further deceiving the victim.

Capabilities of Updated Amethyst Stealer
The updated Amethyst Stealer features the following special capabilities:
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the tactics employed by Sapphire Werewolf and the Amethyst Stealer campaign are a clear indication that cybercriminals are becoming more calculated and adaptive in their approach, intensifying the threat landscape for both organizations and individual users. As threat actors sharpen their phishing tactics and refine malware delivery, individuals handling sensitive information—whether for work or personal purposes—could become prime targets. In the coming years, we may see a surge in highly targeted attacks aimed at specific sectors or high-value individuals, allowing cybercriminals to quietly infiltrate networks and extract critical data. These operations are likely to become harder to detect, prolonging exposure and amplifying the potential damage. As personal devices grow more interconnected with organizational systems, they could serve as vulnerable entry points, blurring the line between corporate and individual risk. This shift underscores a growing need for broader cybersecurity awareness and resilience across all levels of digital interaction.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Supply Chain Attack via Malicious NPM Packages Targeting PayPal
Summary:
Researchers have identified a wave of malicious NPM packages created by a threat actor using the aliases tommyboy_h1 and tommyboy_h2, believed to be the same individual. These packages were published between March 5 and March 14 and were specifically designed to target PayPal users by mimicking legitimate software libraries. By including “PayPal” in the package names—such as oauth2-paypal and buttonfactoryserv-paypal—the attacker created a false sense of legitimacy, tricking developers into installing them.
The campaign primarily targets PayPal users, suggesting a global attack scope, particularly across regions where PayPal is widely used, such as North America, Europe, and Asia-Pacific. The attacker’s strategy involves abusing the trust developers place in well-known service-related package names, transforming this into a supply chain attack that can affect individuals and organizations worldwide.
Once installed, these packages use a “preinstall hook”, a feature in NPM that allows scripts to run before installation. This hook executes a malicious script that silently collects sensitive system data including the current user, hostname, and working directory. To evade detection, the script encodes the data in hexadecimal, obfuscates directory paths, and sends the information to a remote attacker-controlled server using dynamically generated URLs, making it difficult for network security tools to block the communication.
The malicious packages share identical or nearly identical code, indicating a coordinated campaign. The researcher’s investigation found that numerous such packages were published within a short period, all exhibiting similar behaviour aimed at exfiltrating system information for further exploitation or resale on the dark web. The actor’s rapid publishing of these packages increases the likelihood of unsuspecting developers using them in their projects.
Researchers observed identical malicious code across multiple packages, suggesting that all were likely published by the same attacker.
Relevancy & Insights:
The threat actor operating under the aliases tommyboy_h1 and tommyboy_h2 has shown a consistent pattern of using open-source ecosystems, particularly NPM, to distribute malicious packages. In their recent campaign, the attacker rapidly published multiple packages within a short timeframe, using social engineering techniques such as impersonating legitimate services like PayPal. This tactic leverages the trust developers place in popular services to trick them into installing malicious dependencies. While there is no explicit mention of a prior campaign outside of this timeframe (March 5–14), the repetition of tactics, like the use of preinstall hooks, code obfuscation, and data exfiltration methods suggest the attacker has a practiced approach and is refining their techniques.
The targeting remains consistent, focusing on global regions where PayPal is widely used. In both aliases’ activity, the attacker aims at compromising systems of developers integrating financial services, thereby making this a software supply chain attack with broad implications. Attackers are embedding malicious scripts in legitimate- looking packages to steal sensitive data and enable further exploits or resale. The identical code and behaviour across different aliases suggest a coordinated, ongoing supply chain attack, underscoring the need for stronger security in open-source ecosystems.
ETLM Assessment:
The threat landscape surrounding the recent malicious npm package campaign highlights the increasing vulnerability of the open-source ecosystem to supply chain attacks. Attackers, such as the ones behind tommyboy_h1 and tommyboy_h2, are targeting developers by leveraging well-known and trusted platforms like PayPal to create malicious packages that appear legitimate. The preinstall hook is exploited as a primary vector to execute malicious scripts automatically, allowing attackers to steal sensitive data without detection. This type of attack bypasses traditional security mechanisms by obfuscating data and using dynamically generated URLs, making it harder to trace and block. Furthermore, as the open-source software supply chain becomes a more attractive target for cybercriminals, the rapid spread of malicious packages shows the increasing sophistication of threat actors who can abuse package management systems like npm to distribute malware and exfiltrate data. Emerging trends suggest a broader attack surface targeting developer tools and software dependencies, further highlighting the need for enhanced security in open-source package repositories.
The targeted geography in this campaign includes regions where PayPal is heavily used, making global markets the primary focus. The targeted industry is primarily the technology, fintech, and e-commerce sectors, where developers rely on third-party packages for software integration. As attackers increasingly use social engineering tactics to manipulate developers into installing seemingly legitimate packages, the scope of potential victims expands. This trend signifies the growing importance of securing software supply chains and maintaining vigilance in dependency management. Industries relying on online payment platforms, especially those using or integrating PayPal, are particularly vulnerable. To defend against such threats, it is critical for companies to scrutinize package sources and employ security tools that can detect suspicious activities across their networks and codebases.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
RE ATT&CK Tactics and Techniques
| Tactics | ID | Technique |
| Initial Access | T1195 | Supply Chain Compromise |
| Execution | T1059 | Command and Scripting Interpreter |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1119 | Automated Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
China reportedly accepted a hand in Volt Typhoon attacks
According to fresh media reports, in a closed-door meeting last December in Switzerland, Chinese officials privately acknowledged that Beijing was behind a series of aggressive cyberattacks targeting U.S. critical infrastructure.
Chinese representatives supposedly connected years of cyber intrusions into U.S. ports, water systems, airports, and other key sectors to Washington’s growing support for Taiwan. These intrusions, previously denied by Beijing, have been linked by security researchers to a group known as Volt Typhoon. The admission, albeit indirect and veiled in diplomatic language, came as a surprise to the American delegation.
Chinese officials had long denied involvement, often blaming criminal groups or accusing the U.S. of exaggerating. However, during this meeting, American officials interpreted the comments as a tacit acknowledgment of responsibility—along with an implicit warning over Taiwan.
ETLM Assessment:
Last year, the U.S. publicly warned about the Volt Typhoon’s infiltration of civilian infrastructure, attributing it to a Chinese military strategy aimed at embedding in U.S. networks in preparation for possible future conflict. Since the Geneva meeting, U.S.- China relations have further deteriorated amid an escalating trade war. Top Trump administration officials have vowed to step up offensive cyber operations against China, while Beijing continues to exploit access to U.S. telecommunications systems gained through a separate breach tied to another hacking group, dubbed Salt Typhoon.
Compounding concerns, the administration recently announced sweeping layoffs of cybersecurity personnel and dismissed both the director and deputy director of the National Security Agency. These moves have raised alarms among intelligence officials and lawmakers about weakening national defenses at a critical time. China’s targeting of civilian infrastructure represents one of the most serious threats currently facing the Trump administration.
Russian hackers target Western military missions in Ukraine
Researchers observed the Russian threat actor Gamaredon (also known as “Shuckworm”) using an infected removable drive to compromise the military mission of a Western country, based in Ukraine. The attackers deployed a new version of their GammaSteel infostealer.
The campaign began in February and extended into March, with the initial compromise likely stemming from an infected removable drive. The campaign highlights a shift in the group’s tactics, moving away from reliance on VBS scripts in favor of more PowerShell-based tools, especially in the later stages of the attack. PowerShell not only enables obfuscation but also allows scripts to be embedded in the Windows registry, adding persistence and stealth. GammaSteel was delivered through a multi- stage, heavily obfuscated attack chain, aimed at reducing the likelihood of discovery.
ETLM Assessment:
Gamaredon is a Russian state-linked espionage group active since 2013. Believed to operate under the direction of Russia’s Federal Security Service (FSB), the group has remained almost entirely focused on the Ukrainian government, law enforcement, and defense entities. Its ongoing activity underscores how the war in Ukraine has evolved into the central organizing principle of the Russian state, shaping the priorities of its intelligence and cyber operations.
This latest attack signals a modest increase in Gamaredon’s technical sophistication. Though considered less capable than other Russian cyber actors, the group makes up for it through relentless focus on Ukrainian targets. By continuously tweaking its code, adding obfuscation, and using legitimate web services, Gamaredon aims to evade detection despite its limited toolkit.
The operation underscores the group’s ongoing, singular focus on Ukraine—highlighting how the war has become not just a military campaign but the central organizing principle of the Russian state, driving long-term intelligence and cyber efforts.
The Qilin Ransomware Impacts Bangkok Electronics Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; Bangkok Electronics Co., Ltd (www[.]bangkokelectronics[.]com), was compromised by Qilin Ransomware.
Bangkok Electronics Co., Ltd. is a Thai company specializing in the distribution and installation of electronic security and access control systems. The compromised data consists of confidential and sensitive information related to the organization. The compromised data totals approximately 400 GB.
The following screenshot was observed published on the dark web:
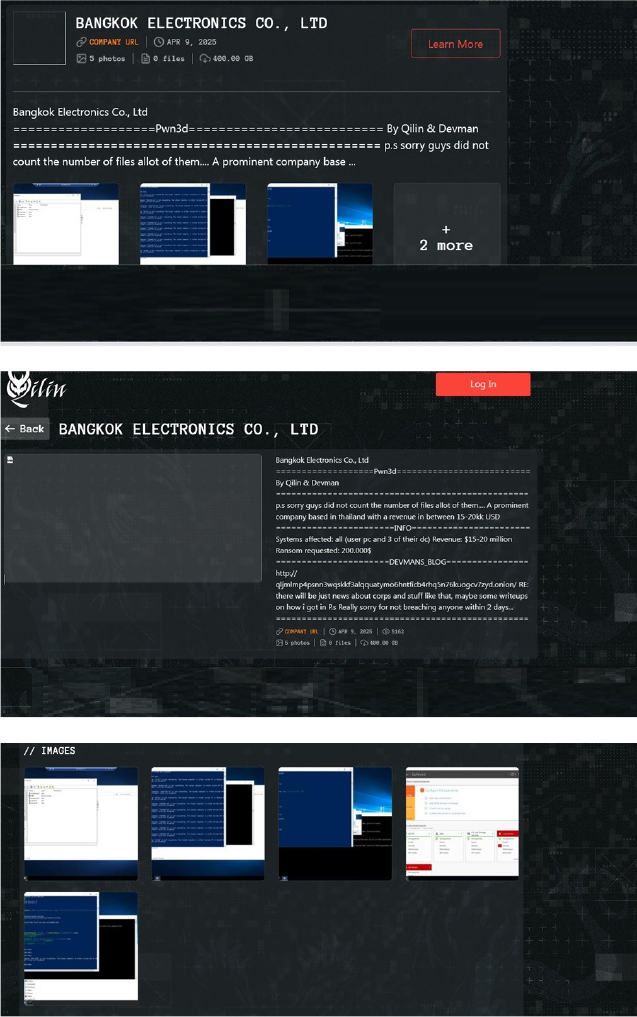
Relevancy & Insights:
The Sarcoma Ransomware Impacts FKS Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, FKS Group (https[:]//www[.]fksgroup[.]com/), was compromised by Sarcoma Ransomware. FKS Group is a Southeast Asian holding company focused on food and agriculture, infrastructure, and property. Its companies combine a strong commitment to logistics and infrastructure with deep domestic and international understanding to realize the potential of businesses and people across the region. The compromised data includes confidential and sensitive information belonging to the organization. The compromised data totals approximately 177 GB.
The following screenshot was observed published on the dark web:


Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Sarcoma ransomware is rapidly becoming a significant threat due to its aggressive tactics and increasing victim count. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate risks associated with this evolving threat landscape.
Vulnerability in Joomla!
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data in the quoteNameStr method of the Database package. A remote attacker can send a specially crafted requests to the affected application and execute arbitrary SQL commands within the application database.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to read, delete, and modify data in the database and gain complete control over the affected application.
Affected Products:
https://developer[.]joomla[.]org/security-centre/963-20250401- framework-sql-injection-vulnerability-in-quotenamestr-method-of-database-package.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
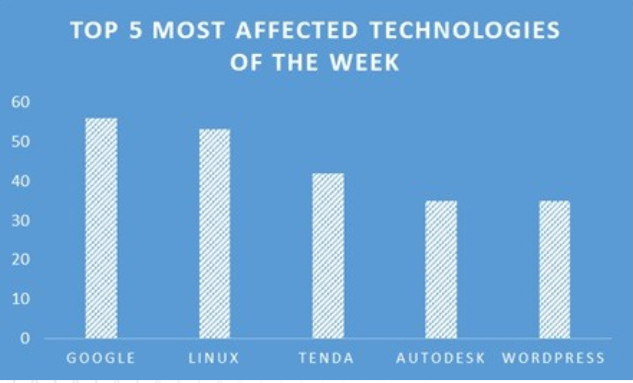
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Joomla! can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Joomla! is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding content management operations, including website creation, user interaction, and extension integration, across different geographic regions and sectors.
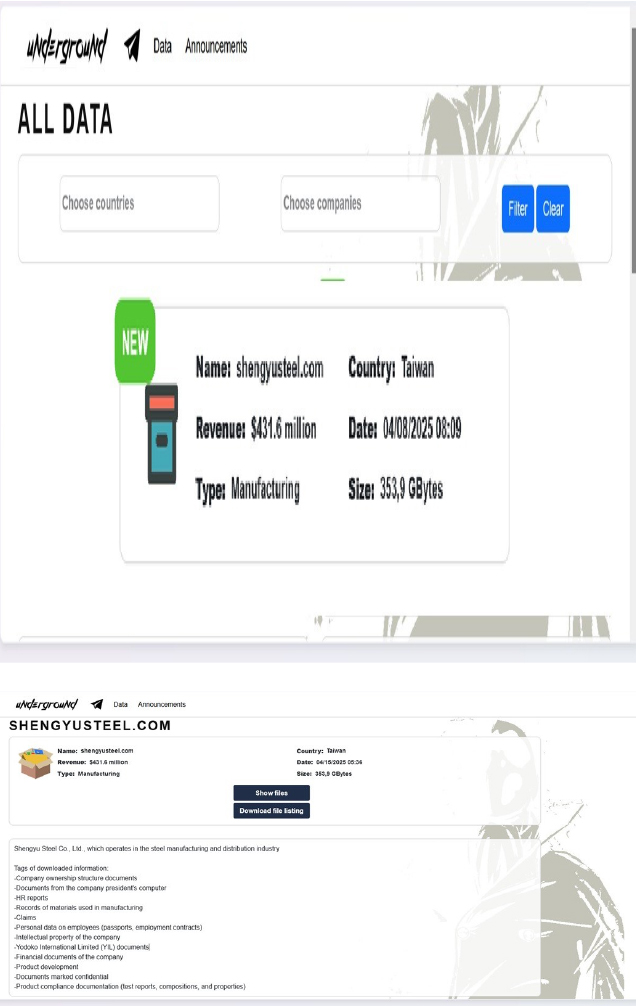
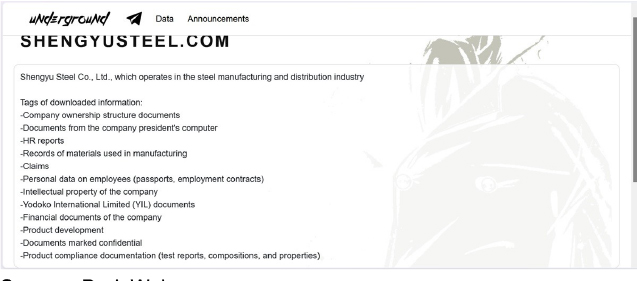
Underground Ransomware attacked and published the data of Shengyu Steel Co., Ltd.
Summary:
Recently, we observed that Underground Ransomware attacked and published the data of Shengyu Steel Co., Ltd.(https[:]//www[.]shengyusteel[.]com/) on its dark web website. Shengyu Steel Co., Ltd., operates in the steel manufacturing and distribution industry. The company exports its products to markets across Asia, Europe, and the United States. The data leak, following the ransomware attack, encompasses the following:
❍ -Documents from the company president’s computer
❍ -HR reports
❍ -Records of materials used in manufacturing
❍ -Claims
❍ -Personal data on employees (passports, employment contracts)
❍ -Intellectual property of the company
❍ -Yodoko International Limited (YIL) documents
❍ -Financial documents of the company
❍ -Product development
❍ -Documents marked confidential
❍ -Product compliance documentation (test reports, compositions, and properties)
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Underground ransomware continues to evolve as a major threat in the cybercrime ecosystem, driven by well-organized RaaS operations and sophisticated techniques. Organizations must adopt a multi-layered cybersecurity strategy to defend against these persistent threats and minimize impact.
Department of Transportation Philippines Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Department of Transportation of the Philippines (https[:]//www[.]dotr[.]gov[.]ph/) in an underground forum. The Department of Transportation (DOTr) in the Philippines serves as the government’s central authority for all matters related to transportation. Its primary function is to ensure the development and efficient operation of the country’s transportation networks, encompassing land, air, and sea travel. The compromised data includes confidential and sensitive information pertaining to the Department of Transportation of the Philippines. The breach has been linked to a threat actor identified as “LuxurySp1d3r.”

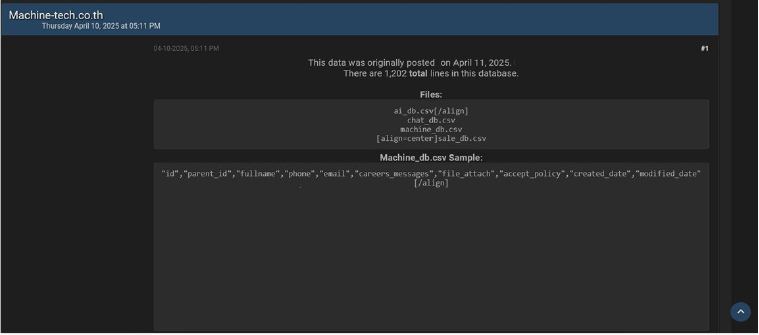
Machine Tech Co., Ltd Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Machine Tech Co., Ltd (https[:]//www[.]machine-tech[.]co[.]th/) in an underground forum. Machine Tech Co., Ltd is a leading supplier of industrial machinery and automation solutions in Thailand. The company specializes in importing and distributing CNC machines, waterjet cutting systems, 3D printers, and related equipment, serving various industries, including automotive, aerospace, electronics, medical, and mold manufacturing. The compromised data includes ID, parent ID, full name, phone number, email address, messages, file attachments, creation and modification dates, along with other confidential and sensitive information. The breach has been linked to a threat actor identified as ” Sythe.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The rise of the threat actor known as ‘Sythe’ marks a significant development in the cyber threat landscape, especially given their claims of responsibility for multiple breaches. This incident underscores the fact that even individual or seemingly isolated actors can cause substantial harm. It highlights the ongoing importance of implementing strong, layered security measures. Staying vigilant and maintaining a proactive defense posture is essential to countering the risks posed by emerging threats like Sythe.
Recommendations: Enhance the cybersecurity posture by
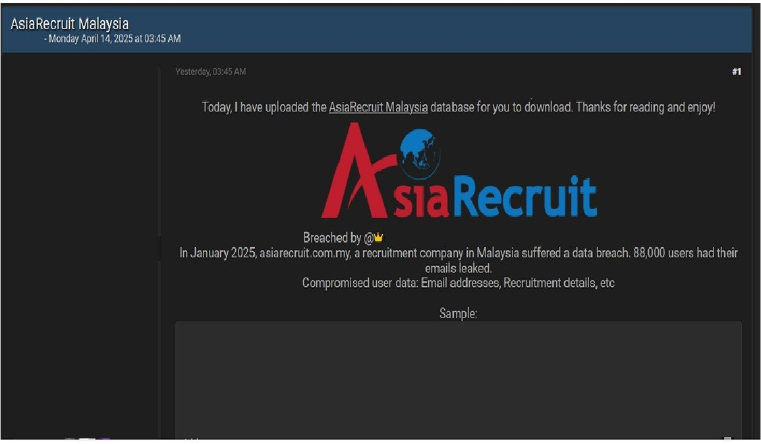
The CYFIRMA Research team observed a data leak related to AsiaRecruit Malaysia (https[:]//www[.]asiarecruit[.]com[.]my/) in an underground forum. Asia Recruit is a leading recruitment and human resource consultancy firm based in Malaysia. The data leak involved information of 88,000 users, including email addresses, recruitment details, and other related data.
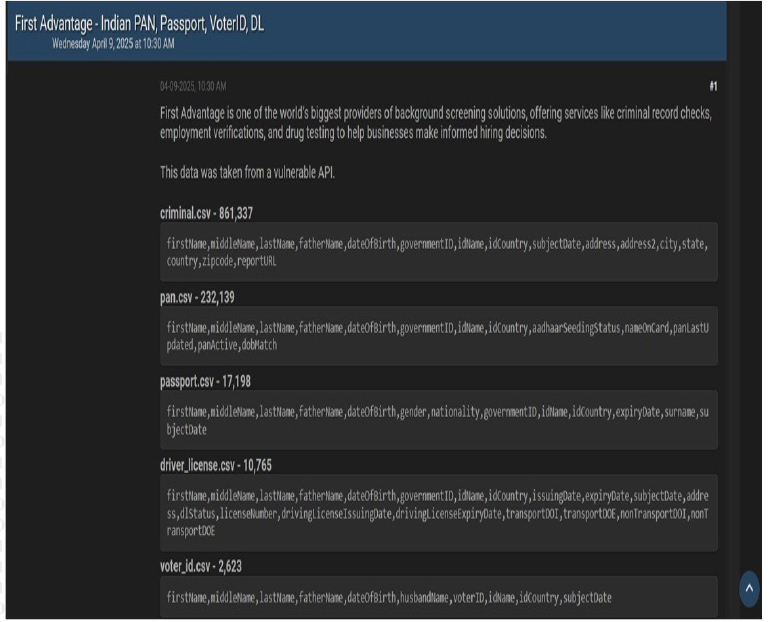
The CYFIRMA Research team observed a data leak related to First Advantage (https[:]//fadv[.]com/solutions/employment-background-checks/) in an underground forum. First Advantage Corporation is a leading global provider of background screening, identity verification, and risk mitigation solutions. The company serves clients across various industries, including healthcare, retail, financial services, and transportation.
The data leak contains Indian PAN, Passport, voter ID, and DL, including:
criminal.csv – 861,337
first name, middle name, last name, father name, date of birth, government ID, ID name, ID country, subject date, address, address2, city, state, country, zip code, report URL
pan.csv – 232,139
first name, middle name, last name, father name, date of birth, government ID, ID name, ID country, Aadhaar seeding status, name on card, pan Last updated, pan active
passport.csv – 17,198
first name, middle name, last name, father name, date of birth, gender, nationality, government ID, ID name, ID country
driver_license.csv – 10,765
first name, middle name, last name, father name, date of birth, government ID, ID name, ID country, issuing date, expiry date, subject date
voter_id.csv – 2,623
first name, middle name, last name, father name, date of birth, husband name, voter ID, ID name, ID country, subject date
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
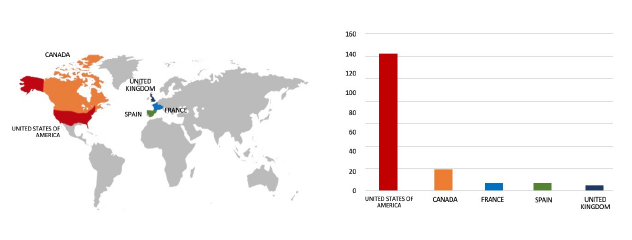
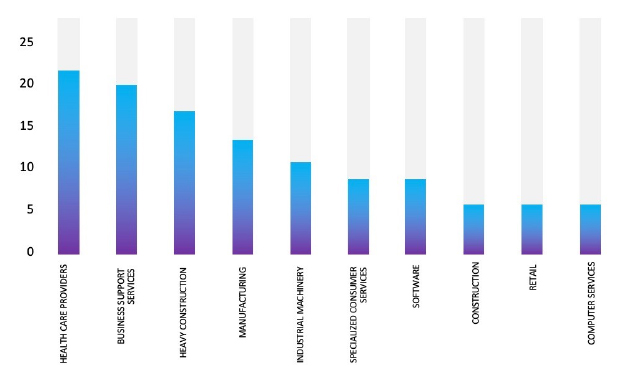
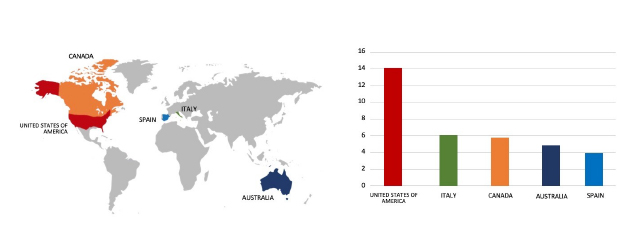
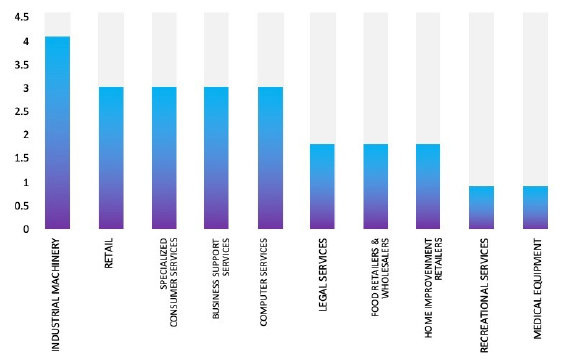
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
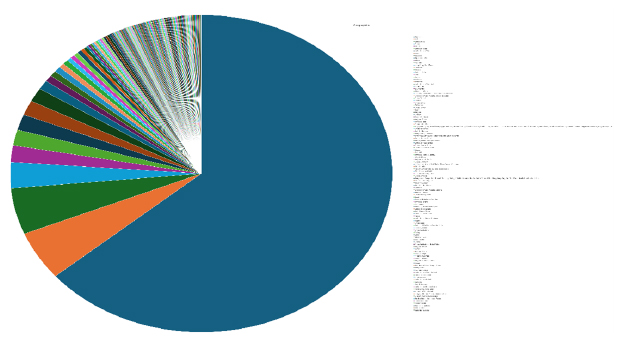
Industry-Wise Graph
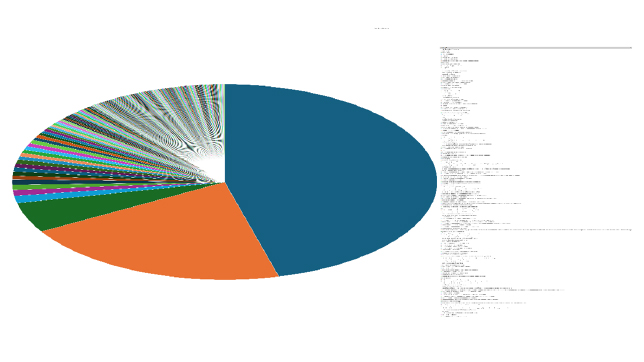
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.